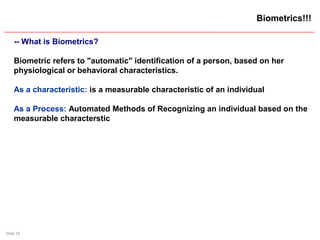
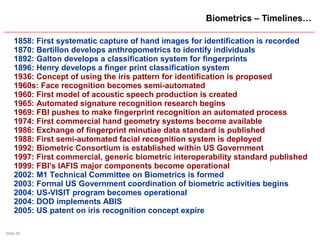
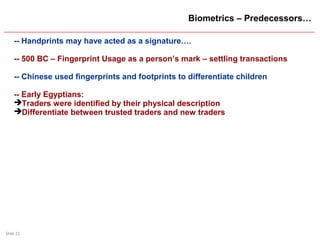
The document presents a session on user authentication trends, focusing on the significance of authentication methods including biometrics. It discusses the importance of understanding user behaviors regarding password security and highlights various biometric technologies and their historical development. The session concludes by emphasizing the critical need for secure authentication mechanisms to prevent unauthorized access.









![Slide 14
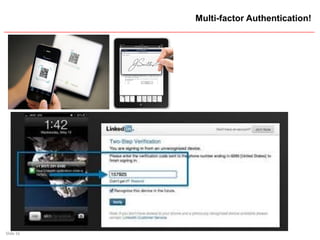
Multi-factor Authentication!
-- Knowledge factors – Something you know
[Passphrase, PIN, Challenge/Response]
-- Possession factors – Something you have
[ID Card, Token, Phone]
-- Inherence factors – Something you are
[Fingerprint, Retina, Iris, Voice, Face]
-- Dynamic factors – Something you do - Question 6
-- Hybrid [Private Keys Encrypted by a Fingerprint Device Inside a USB
Token]
-- So… How many? Who will decide? Criterion?
More Reading: https://twofactorauth.org/](https://image.slidesharecdn.com/userauthentication-trends-151224131000/85/User-authentication-trends-14-320.jpg)
![Slide 15
Multi-factor Authentication!
-- Tokens – Connected, Disconnected, H/W, S/W, USB
Based, Audio Port Based
-- Cards – Magnetic Strip Cards, Grid Cards, Patterns
-- Wireless Tokens [RF Id, Bluetooth]
-- Software: Capcha, SSO
-- Onetime pads, iButtons These are OLD….
-- Mobile Phone Based Tokens – Soft token, SMS, QR
Code, Call, smart phone Push, Mobile Signatures, Apps](https://image.slidesharecdn.com/userauthentication-trends-151224131000/85/User-authentication-trends-15-320.jpg)
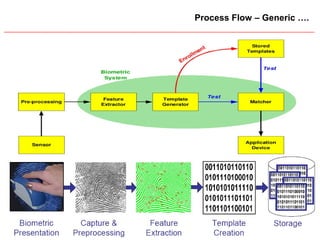
![Slide 23
Biometrics – Broad Classification
-- Behavioral
[Keystroke, Signature: Static, Dynamic]
-- Physical
[Fingerprint, Voice, Hand/Finger/Face Geometry, Facial Recognition,
Signature, Voice, Iris]
-- Still In Progress
[Smell, Ear Shape, Finger Nail Bed, Face-3D, Gait, Lip Movement, Vein Scan]
-- Traits: Collectability, Uniqueness, Performance, Acceptability, Expected
Number of Users
-- Components: Server, Signal Processing, Data Storage, Matching
Algorithm, Decision Process
-- Capturing Technology: RF, Optical, Capacitive, Pressure Tracking](https://image.slidesharecdn.com/userauthentication-trends-151224131000/85/User-authentication-trends-23-320.jpg)
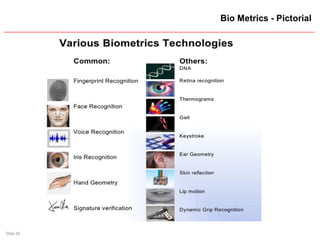


![Slide 27
Other Biometrics…
-- Voice Scan: Measures sound waves of a human
speech; Voice print compared to a previous one.
-- Signature Scan: Measures speed, pressure, stroke
order of a signature
-- Retina Scan: Measures Unique characterestics of a
retina; Blood vessel patterns, Vein Patterns
-- Facial Scan: camera measures the following facial
features: Distance between eyes, eyes and nose
ridge, angles of cheek, slope of the nose, Facial
Temperatures
-- Hand Scan: Measures Top and Side of a hand – Not
the palm [Hand Geometry]](https://image.slidesharecdn.com/userauthentication-trends-151224131000/85/User-authentication-trends-27-320.jpg)
![Slide 28
Biometrics – Metrics
-- FAR : False Acceptance Rate [Wrong Identification]
-- FRR : False Recognition Rate [Access Denial]
-- FTE: Failure to Enrol Rate
-- AVT : Ability To Verify
[AVT = (1 – FTE)(1-FRR)
-- IRIS: FAR – 1/1,000,000; FRR : 2%
-- Fingerprint: FAR – 1/100,000; FRR: 1%
-- Algorithmic; Matching Scores
-- Standards: BioAPI, BAPI](https://image.slidesharecdn.com/userauthentication-trends-151224131000/85/User-authentication-trends-28-320.jpg)
![Slide 29
Biometrics – Areas
-- Identification Systems: Who am I ?
[Determine Identity]
-- Verification Systems: Am I who I claim to be ?
[Authenticate Identity]
-- In short, Determine or Authenticate Authority!
--Verification Systems:
More Accurate
Less Expensive
Faster
Limited in Functionality
More Efforts by User than Computer](https://image.slidesharecdn.com/userauthentication-trends-151224131000/85/User-authentication-trends-29-320.jpg)

![Slide 34
Question 6: Biometrics – Cons
-- Can be faded with time : Fingerprint, Voice [Answer]
-- Not still matured – For example Fingerprint
-- Standards are not in place yet – Replacement, if Lost
-- Not easy to introduce variability
-- Still Expensive
-- Replacement, if Lost
-- Cultural/Religious Issues
-- Privacy Concerns of misuse](https://image.slidesharecdn.com/userauthentication-trends-151224131000/85/User-authentication-trends-34-320.jpg)
![Slide 36
So, What are we guarding against ?
Question
Simple – “Unauthorized Access”
And what are the threats ? [Question]
--- Stealing
--- Confidence Tricks
--- Technical Tricks [Local, Remote]
--- Victim Mistakes
--- Implementation Oversights
--- DoS Attacks
--- Enrollment Attacks
https://www.owasp.org/index.php/Comprehensive_list_of_Threats_to_Authe
ntication_Procedures_and_Data](https://image.slidesharecdn.com/userauthentication-trends-151224131000/85/User-authentication-trends-36-320.jpg)


