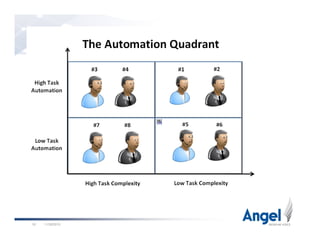
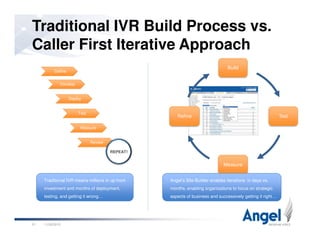
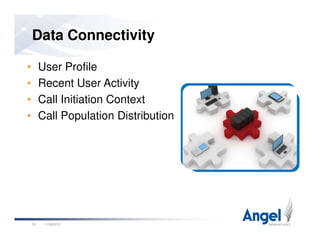
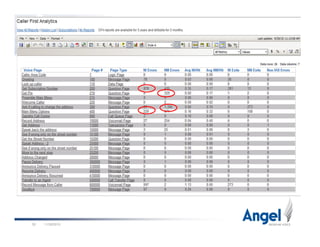
This document discusses best practices for building world-class voice applications (IVRs). It begins by explaining why people dislike IVRs and argues that people dislike bad automation, not self-service itself. It then outlines three key challenges with IVRs: they impose themselves on users, have a constrained voice interface, and must simulate human behavior. The document advocates for a "Caller First" philosophy of rapid development, leveraging caller and application data, and intelligent behavior. Examples of intelligent behavior include avoiding main menus, prioritizing options, and bypassing automation for unhappy callers. The presentation concludes by emphasizing the importance of data and putting the caller first.