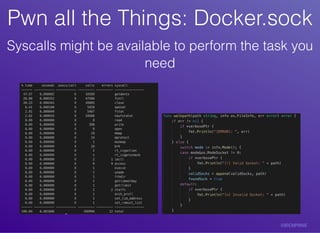
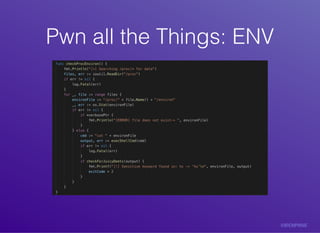
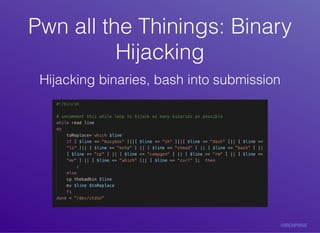
The document discusses container vulnerabilities and their exploitation within modern cloud environments. It introduces a tool called 'botb' that aids both pentesters and engineers in identifying and exploiting these vulnerabilities through various methods, including accessing Docker sockets and hijacking binaries. The conclusion emphasizes the importance of using 'botb' for testing and feedback within the software development lifecycle.