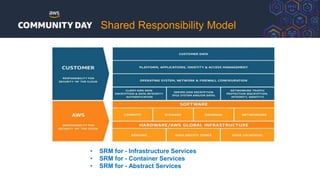
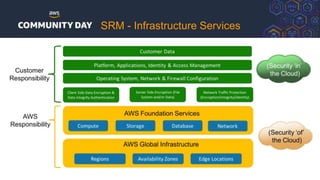
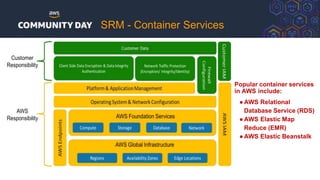
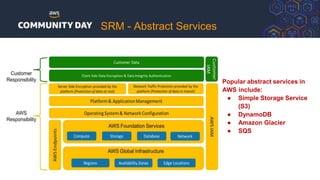
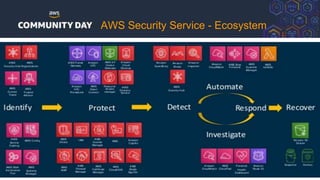
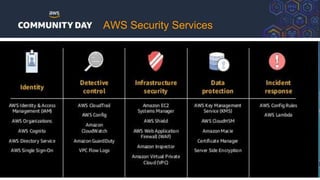
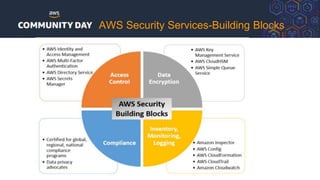
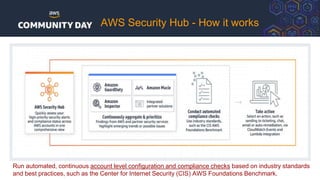
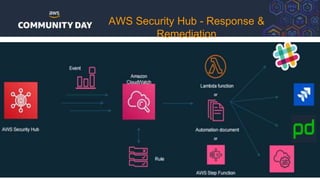
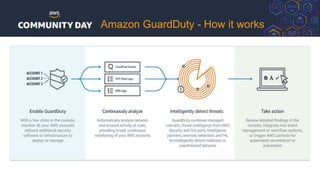
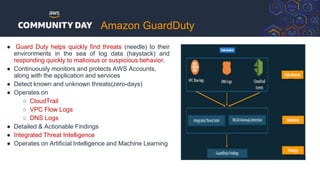
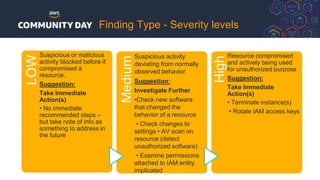
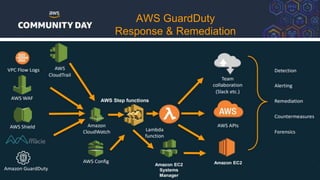
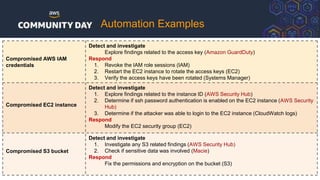
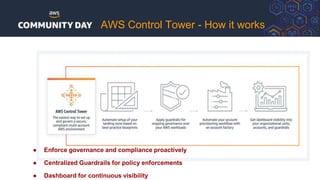
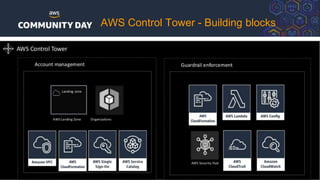
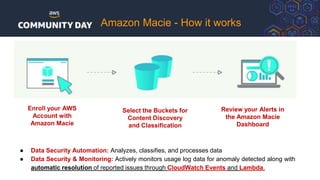
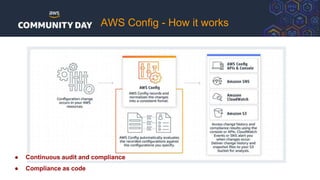
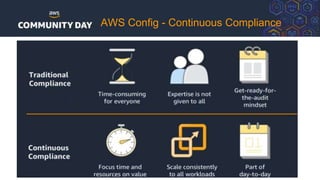
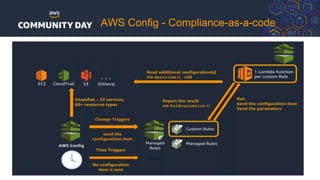
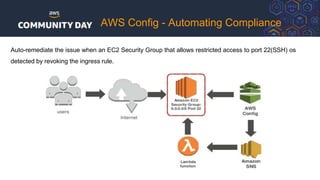
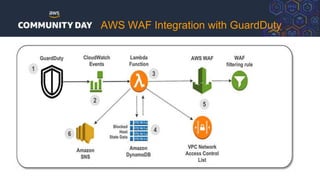
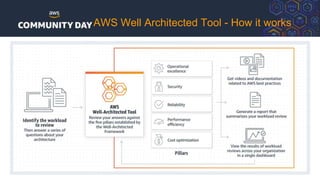
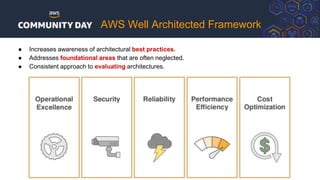
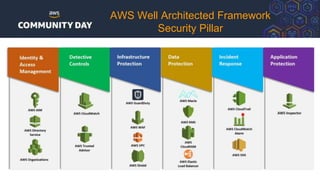
The document discusses automating security and compliance on AWS. It begins with an overview of common cloud security threats and why automating security is important. It then covers AWS' shared responsibility model and various AWS services that can help with automation, including Security Hub, GuardDuty, Control Tower, Macie, Config, and WAF. These services aid in tasks like continuous monitoring, detecting threats, and automating response. The document emphasizes that automation is faster, more effective, reliable, and scalable than manual security and compliance processes. It provides examples of how different threats could be automatically detected and remediated.