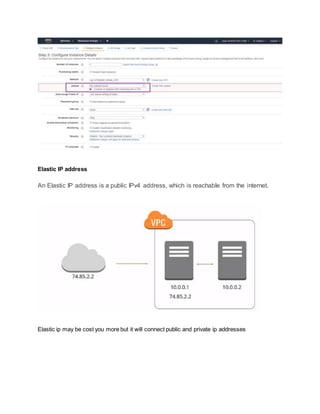
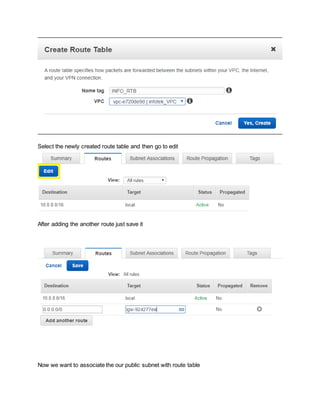
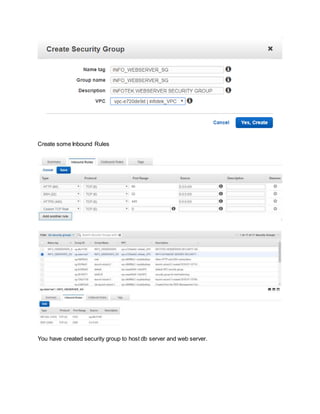
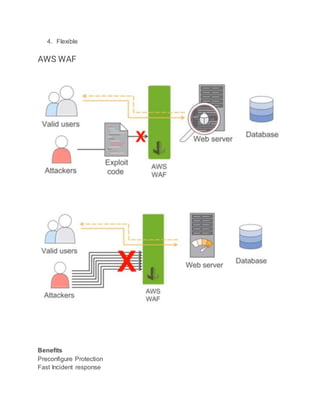
To secure AWS infrastructure, implement multiple layers of security including VPCs, subnets, security groups, network ACLs, firewalls, and IAM roles and policies. Create a custom VPC with public and private subnets, attach an internet gateway to the VPC and route tables to allow access. Use security groups to control traffic, network ACLs as an additional firewall layer, and a NAT gateway to allow private instances internet access. Implement AWS WAF, Shield, and IAM best practices like MFA and least privilege policies.