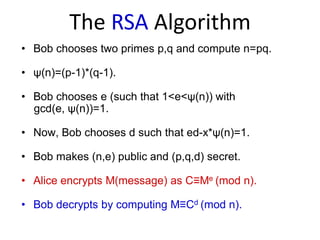
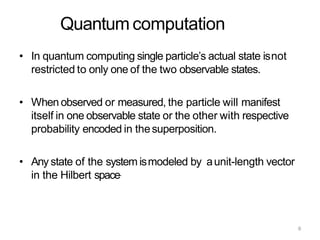
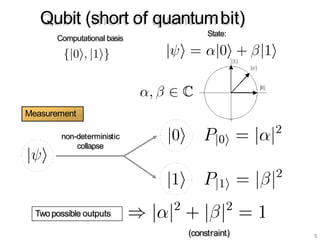
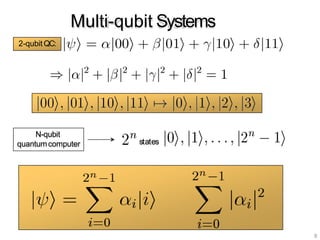
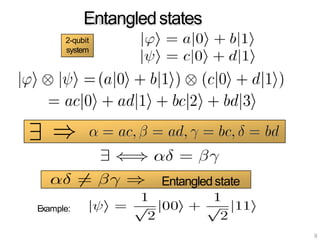
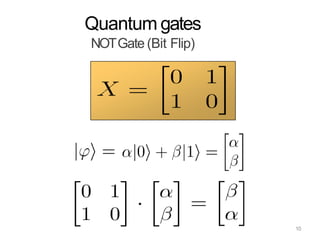
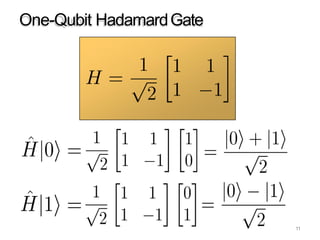
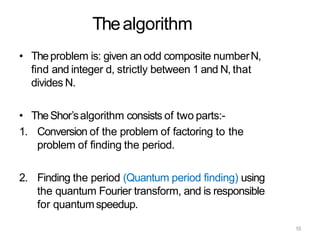
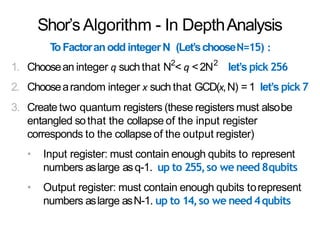
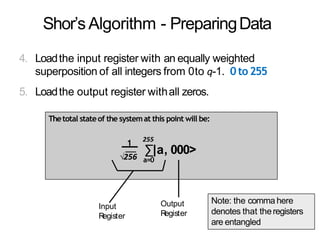
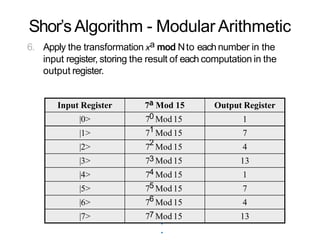
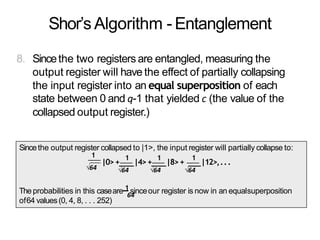
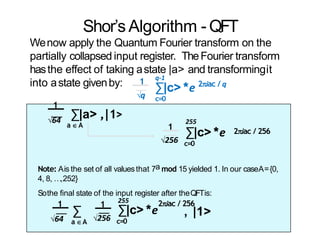
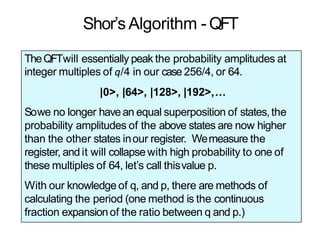
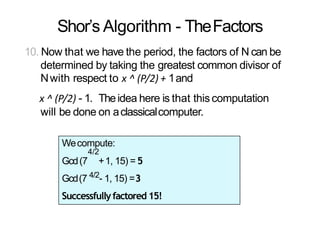
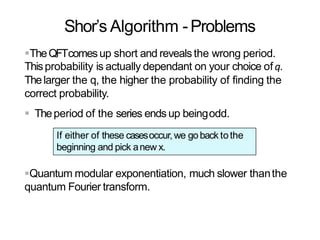
The document discusses the fundamentals of quantum computing, focusing on the historical development of quantum algorithms, particularly Shor's algorithm for factoring large integers, which poses a potential threat to current internet encryption methods like RSA. It explains how quantum mechanics principles such as superposition and entanglement enable quantum computers to factor numbers more efficiently than classical algorithms. Recent advancements in quantum computing applications are also highlighted, showcasing significant achievements in factorization using quantum machines.

![Introduction
▪“I think I can safely saythat nobody
understands quantum mechanics” - Feynman
▪1982 - Feynman proposed the idea ofcreating
machines based on the laws of quantum
mechanics instead of the laws of classical
physics.
▪1985 - David Deutsch developed the quantum Turingmachine,
showing that quantum circuits areuniversal[1].
▪1994 - Peter Shorcame up with aquantum algorithm tofactor
very large numbers in polynomialtime.
▪1997 - LovGrover develops aquantum searchalgorithm with
O(√N) complexity.](https://image.slidesharecdn.com/shorsalgorithm-240715142905-8f8a6c50/85/A-basic-overview-to-the-Shor-s-algorithm-2-320.jpg)