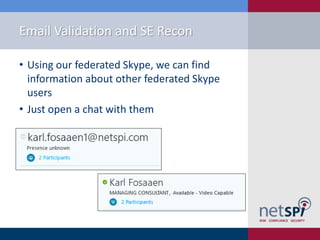
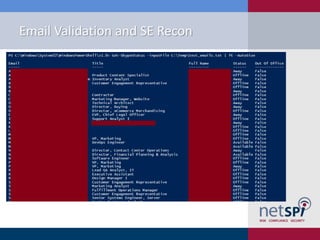
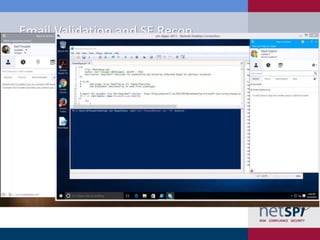
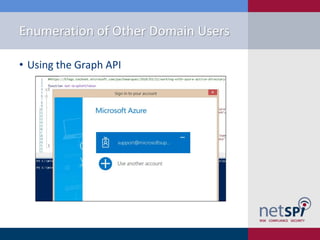
The document presents a detailed examination of attacks on Active Directory Federation Services (ADFS) using PowerShell, covering user enumeration, phishing, and dictionary attacks. It provides a comprehensive guide on setting up a test environment, identifying federated endpoints, and mitigation strategies to enhance security. Key insights include the importance of dual-factor authentication and monitoring of federated services to protect against common vulnerabilities.