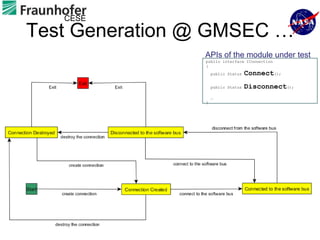
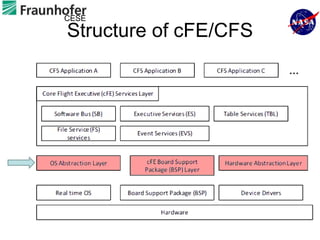
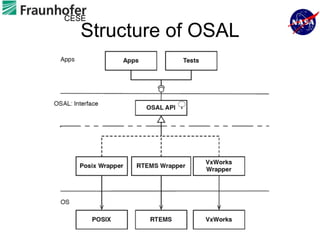
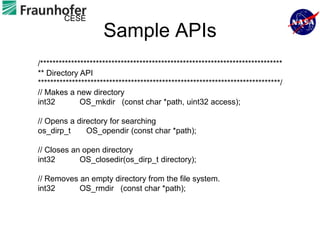
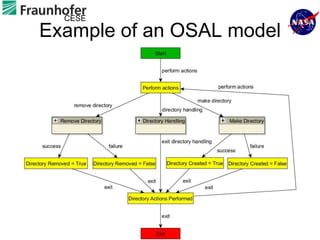
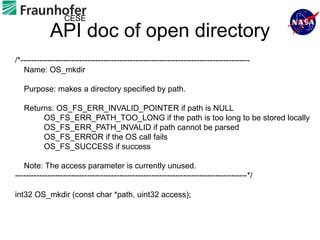
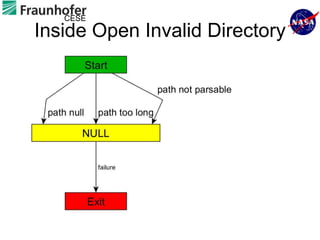
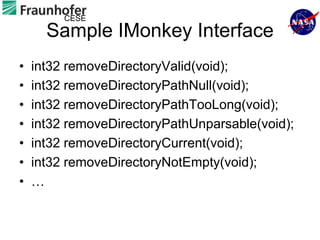
1) The document describes an approach for automated testing of large multi-language software systems using cloud computing.
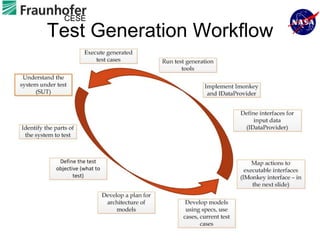
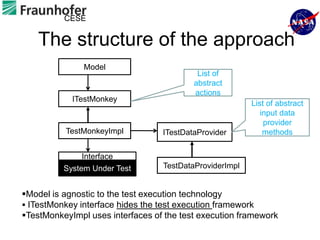
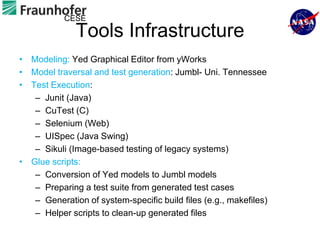
2) Key aspects of the approach include generating test cases from models of software APIs and interfaces and executing them using tools like JUnit and Selenium.
3) The approach was applied to test portions of NASA software like GMSEC and CFS, and was able to find bugs not discovered with manual testing.

![CESE
Hand-crafted test case (snippet)
public static void main( String args[] ) {
Status result = new Status();
Connection conn = new Connection();
ConnectionConfig cfg = new ConnectionConfig( args );
// Create the connection
result = ConnectionFactory.Create( cfg, conn );
checkError( false, result, "Creating the connection object" );
// Disconnect
result = conn.Disconnect();
checkError( true, result, "Disconnecting before connection is established" );
// Connect
result = conn.Connect();
checkError( false, result, "Establishing the connection to the middleware" );
} //..main()](https://image.slidesharecdn.com/automatedtestingsas2011techpresentation-121023141938-phpapp02/85/Automated-testing-of-NASA-Software-part-2-7-320.jpg)