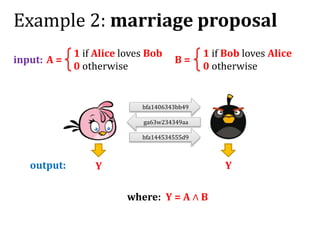
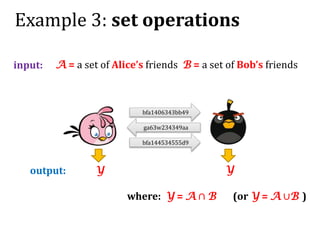
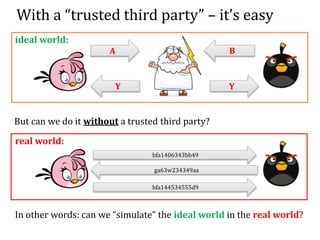
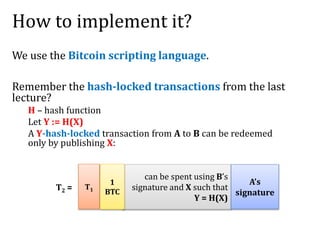
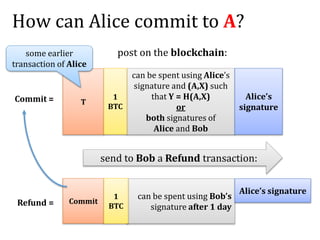
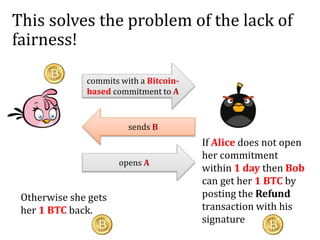
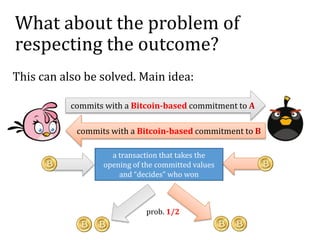
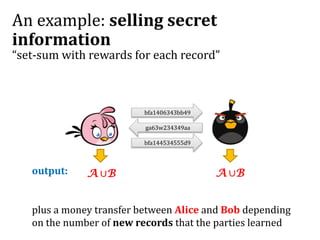
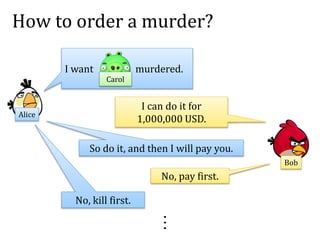
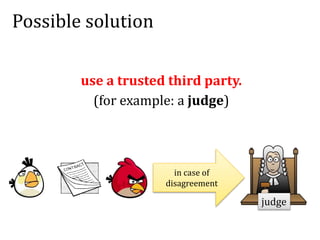
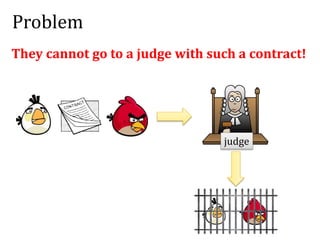
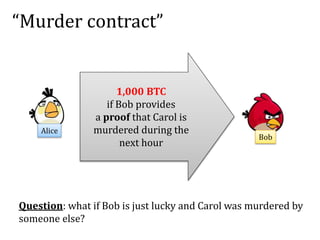
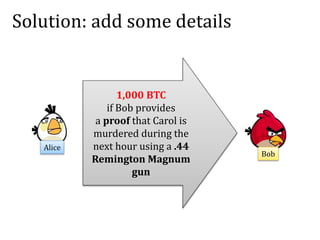
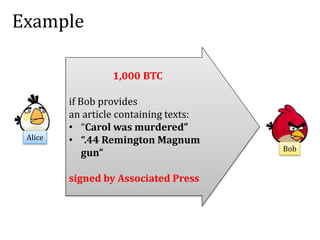
This document discusses smart contracts and applications, focusing on secure multiparty computations using Bitcoin contracts. It describes how Bitcoin contracts can be used to simulate coin tossing and other multiparty computations without requiring a trusted third party. Criminal uses of smart contracts, such as ordering a murder, are also discussed, along with potential solutions like authenticated data feeds. Formal modeling of contracts using timed automata is presented as a way to analyze complicated contracts.





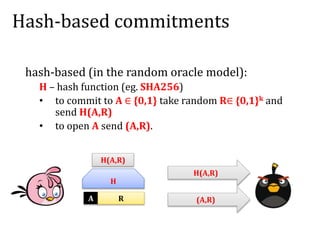
![Commitment schemes – an intuition
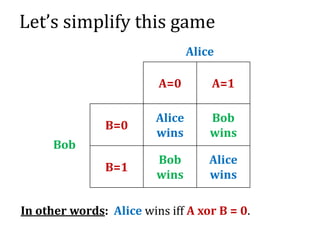
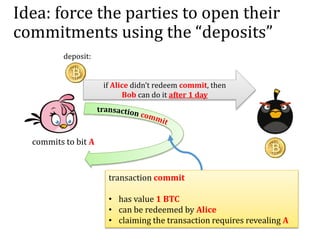
Alice sends a locked box to Bob
a bit A
A
Alice can later send the key to Bob
A
[binding] from now Alice cannot change A,
[hiding] but Bob doesn’t know A
Alice “commits
herself to A”
Alice “opens the
commitment”](https://image.slidesharecdn.com/4-160609174408/85/Smart-contracts-and-applications-part-II-21-320.jpg)
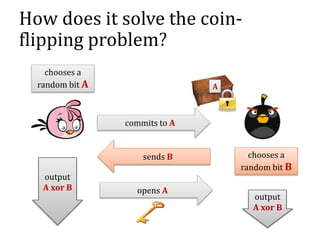

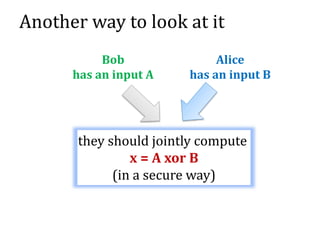
![The results of [Andrychowicz
et al]
Any two-party non-reactive functionality can be
“simulated” in this way.
The simulation can enforce the financial
consequences.
Generalized to multiparty reactive functionalities
in [Kumaresan, Moran, Bentov].](https://image.slidesharecdn.com/4-160609174408/85/Smart-contracts-and-applications-part-II-32-320.jpg)









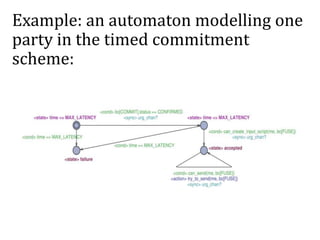
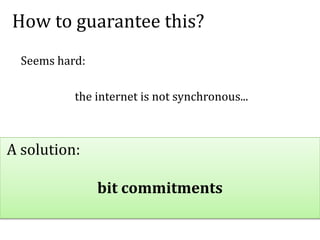
![Can we do it automatically?
[Andrychowicz, D., Malinowski, Mazurek, Modeling
Bitcoin Contracts by Timed Automata, 2014]:
Yes! (to a certain extent)
The general idea:
model a contract as a
timed automaton
use the UPPAAL tool
to verify its properties
yes/no](https://image.slidesharecdn.com/4-160609174408/85/Smart-contracts-and-applications-part-II-51-320.jpg)