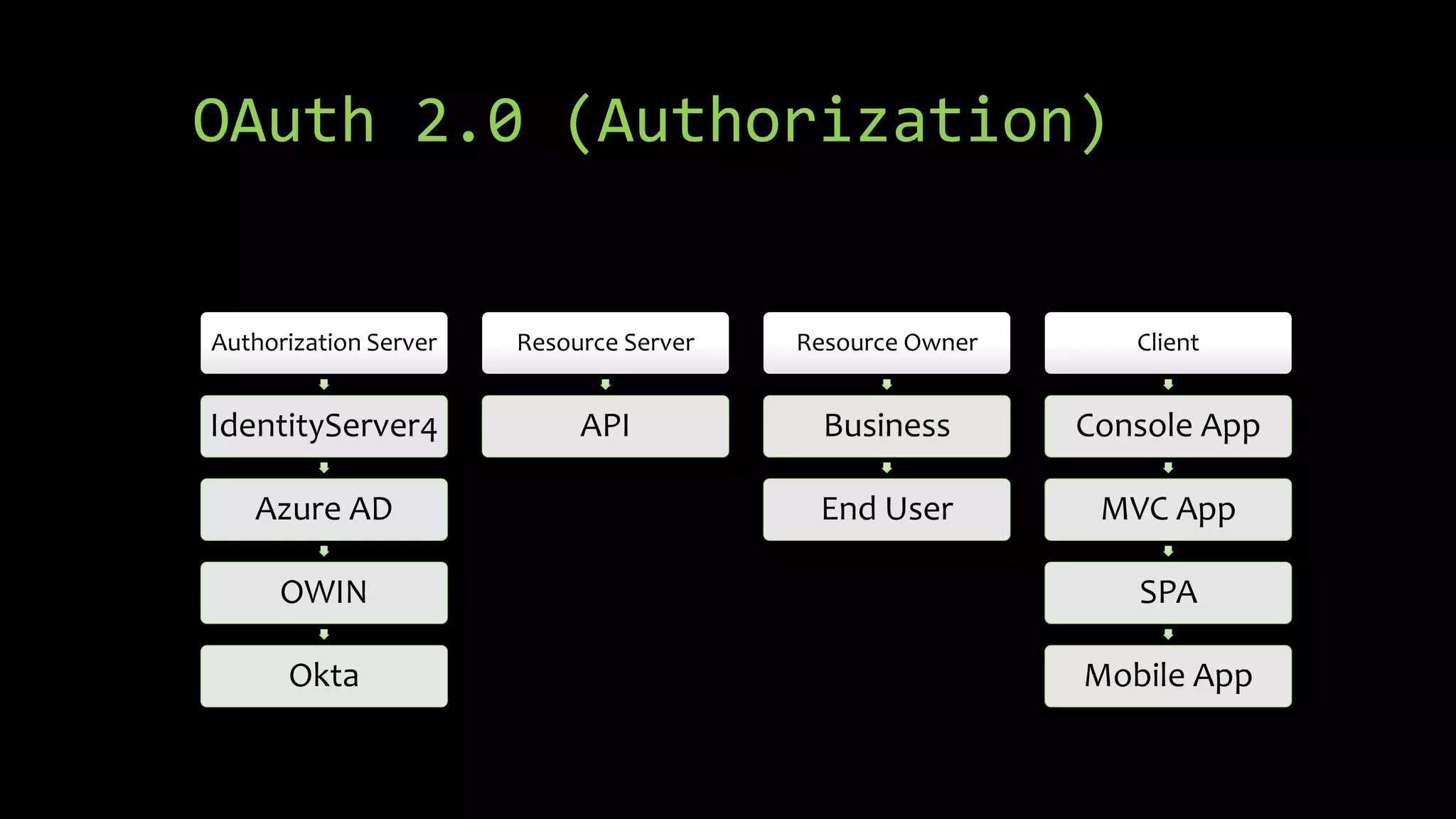
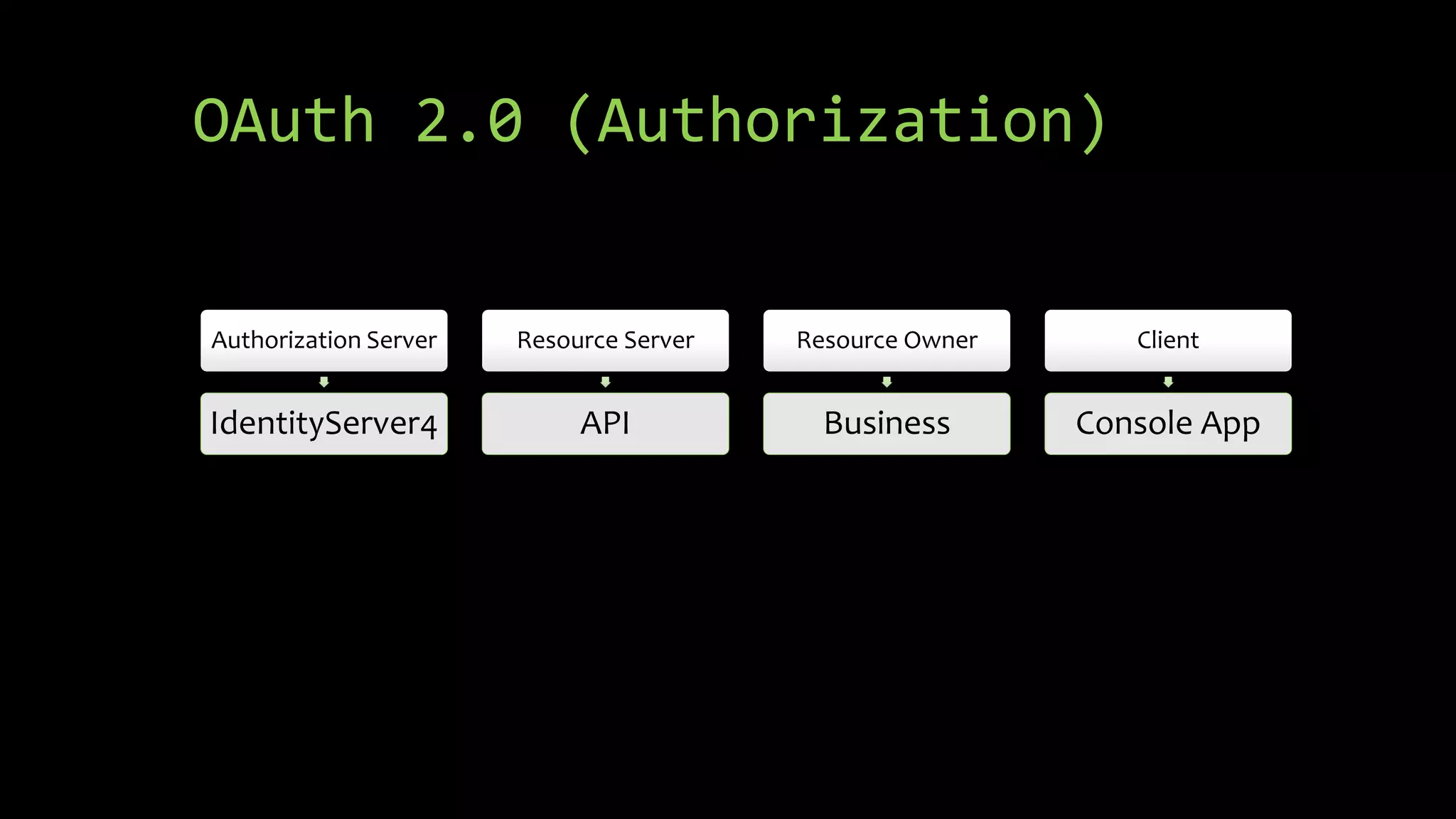
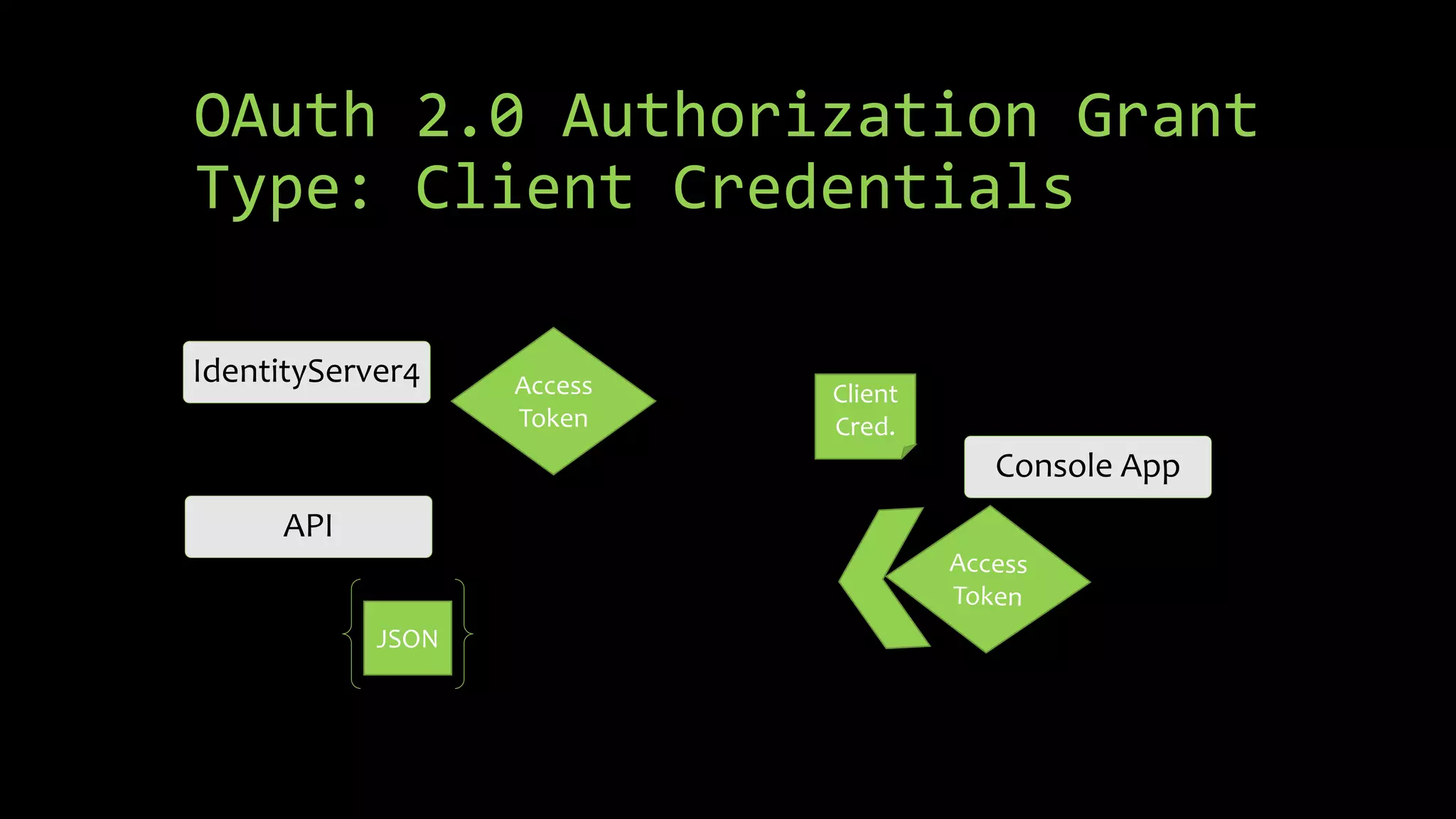
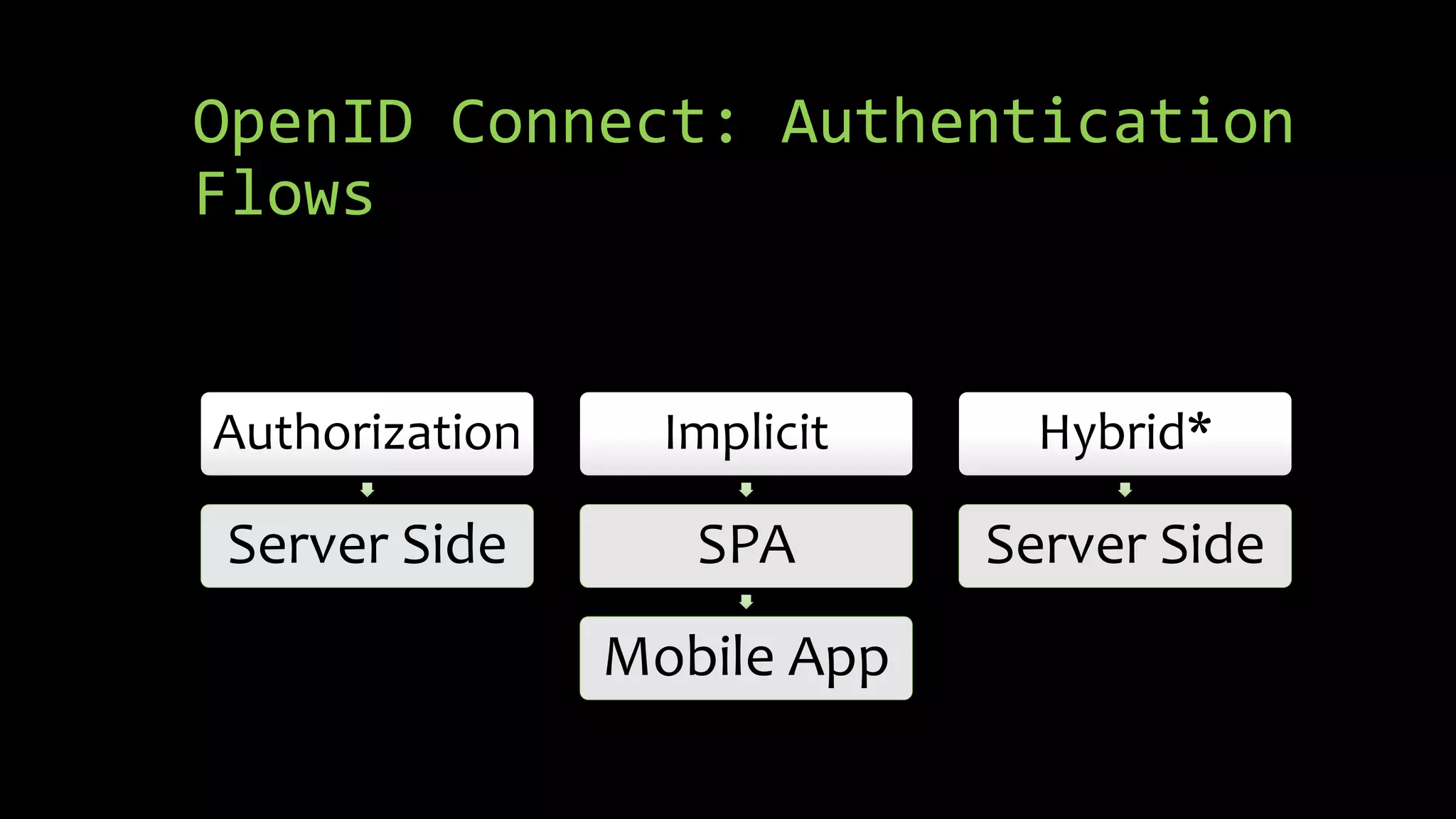
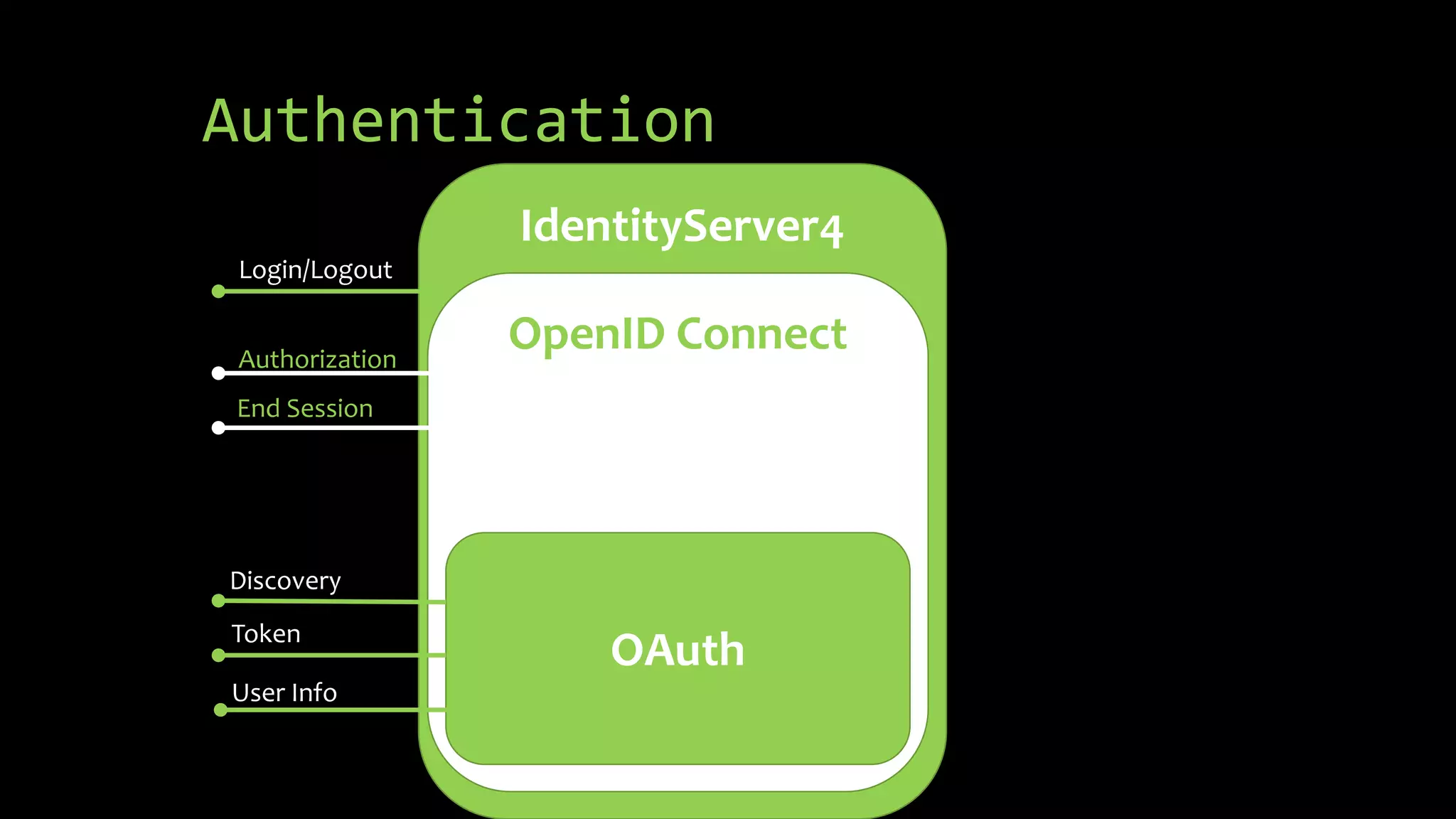
This document summarizes a presentation about OAuth 2.0, OpenID Connect, and single sign-on (SSO) using IdentityServer4. It discusses the differences between authorization and authentication, provides an overview of OAuth 2.0 authorization grant types and how IdentityServer4 can implement OAuth 2.0 and OpenID Connect protocols to secure APIs, web, and mobile applications. It also lists some demos and helpful links related to implementing OAuth 2.0 and OpenID Connect with IdentityServer4.