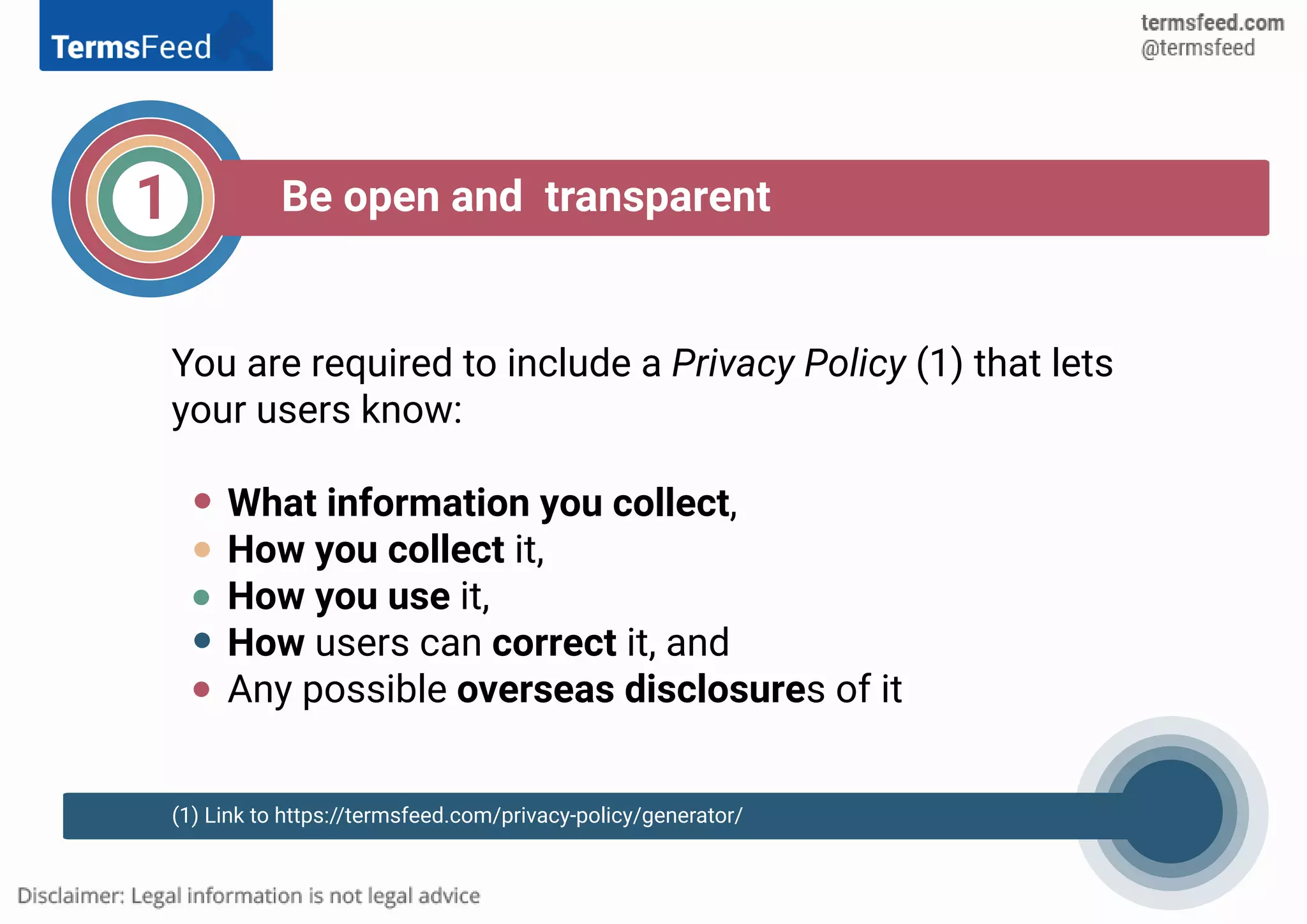
The Australia Privacy Act of 1988 mandates compliance for businesses meeting certain criteria, including income threshold and personal information handling. It establishes 11 Information Privacy Principles (IPPs) governing the collection, use, and security of personal data, alongside a 13-principle compliance checklist for best practices. Key requirements include transparency, user consent, data protection measures, and processes for correcting personal information.