Embed presentation
Download as PDF, PPTX





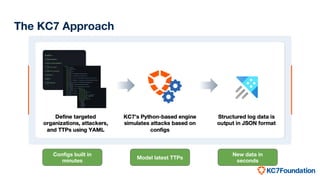


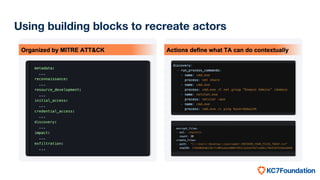





The document discusses the use of MITRE ATT&CK framework to create realistic cyber adversaries for training and skill development in cybersecurity. It highlights the limitations of traditional simulated intrusion data and presents the KC7 Foundation's approach to quickly generate updated attack configurations and enhance analytical skills. The end goal is to provide practical insights into real-world techniques and their effectiveness.













