This document discusses assembly language string primitives instructions including MOVSx, CMPSx, SCANSx, STOSx, LODSx. It explains how these instructions use registers like ESI, EDI to operate on strings and arrays. Examples are provided to copy arrays, compare strings, find characters in strings, fill arrays, and multiply array elements. Two-dimensional arrays are also discussed where rows are stored sequentially in memory. Hands-on exercises demonstrate using these instructions to work with strings and 2D arrays.


![String Primitives
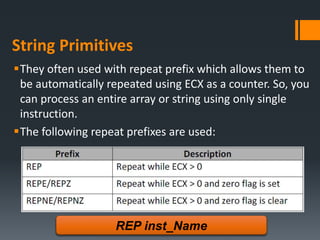
When repeat prefix is used, the sequence of its operation
is as follows:
1. Test repeat condition(s) [ECX > 0 and zero flag status
with REPE and REPNE]
2. If test success, perform the instruction (in addition to
incrementing or decrementing ESI or EDI or both).
Otherwise, skip the entire instruction.](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-6-320.jpg)

![MOVSB / MOVSW / MOVSD Instructions
These instructions copy data pointed by ESI to the
memory location pointed by EDI. They are used with
repeat prefixes to copy arrays and strings.
It’s Like:
T
H
E
T
H
E
ESIEDI
ESI
ESI
EDI
EDI
MOV [EDI], [ESI]](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-8-320.jpg)
![[Hands On] Copy an Array
Use string primitive instructions to copy items from
double word array to another, then display the output](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-9-320.jpg)
![.data
source dword 10,20,30,40,50
target dword 5 dup(?)
.code
main proc
cld ;clear direction flag. Move forward
mov ecx, lengthof source
mov esi, offset source
mov edi, offset target
rep movsd
; display the target array
mov edx, OFFSET target
mov ecx, lengthof target
L1:
MOV eax, [edx]
CALL WriteInt
CALL CRLF
ADD edx, TYPE target
LOOP L1
exit
main endp
end main](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-10-320.jpg)
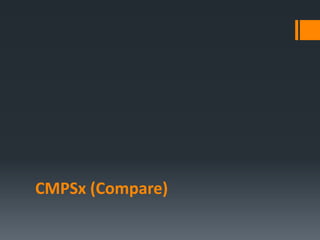
![CMPSB / CMPSW / CMPSD
These instructions compare a memory operand pointed
by ESI (source) with the memory operand pointed by EDI
(destination).
They actually subtract target from source and set flags
according to the result like CMP instruction.
It’s Like:
CMP [EDI], [ESI]](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-12-320.jpg)
![Example
.DATA
SOURCE DWORD 1234h
TARGET DWORD 5678h
.CODE
MOV ESI, OFFSET SOURCE
MOV EDI, OFFSET TARGET
CMPSD ;like cmp [EDI], [ESI]
JA l1
JMP l2](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-13-320.jpg)
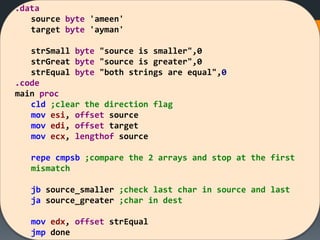
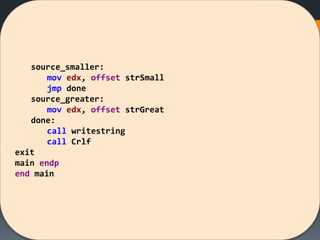
![[Solved Example] CMP 2 Strings
Compare two strings assuming that both strings have the
same size.](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-14-320.jpg)
![[Hands On] CMP 2 Strs with Diff Len
Implement the same previous example but assume the
strings have different length
Key Idea:
1.Loop for the length of the minimum
2.Handle case JB and JA like pervious
3.In case of having the same chars check the length of
each](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-17-320.jpg)
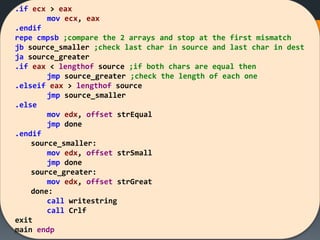

![[Hands On] Find ‘W’
Write an assembly program the search for letter ‘w’ in a
given string
It’s a sequential search…](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-21-320.jpg)

![STOSB / STOSW / STOSD Instructions
These instructions store the content of AL/AX/EAX into
memory at the offset pointed to by EDI.
They are useful for filling all elements of a string or array
with a single value.
It’s Like
MOV BYTE PTR [EDI], AL
MOV WORD PTR [EDI], AX
MOV DWORD PTR [EDI], EAX](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-24-320.jpg)
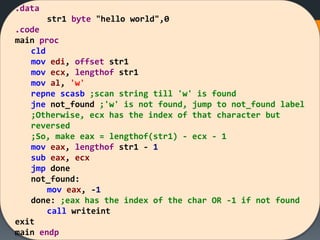
![[Solved Example] Fill an Array
Uses string primitive instructions to initialize an array by a
specific value.
It reminds me with DUP API ;)
Use an already defined word array with length 20
Init. it with 5](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-25-320.jpg)
![.data
arr1 word 20 dup (?)
.code
main proc
cld
mov edi, offset arr1
mov ecx, lengthof arr1
mov ax, 5 ;save number you want to initialize with in
the AX
rep stosw ;set all items in arr1 by AX value
;display the array elements
mov ecx , lengthof arr1
mov esi, offset arr1
L1:
movzx eax, WORD PTR[esi]
call writeInt
Call CRLF
LOOP L1
exit
main endp
end main](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-26-320.jpg)
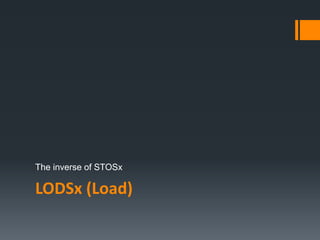
![LODSB / LODSW / LODSD Instructions
These instructions load a byte, word, or double word
from memory at ESI into AL/AX/EAX respectively.
REP prefix is rarely used with them as each new value
loaded into accumulator overwrites its previous
contents.
MOV AL, BYTE PTR [ESI]
MOV AX, WORD PTR [ESI]
MOV EAX, DWORD PTR [ESI]](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-28-320.jpg)
![[Hands On] Array Multiplier
Write an assembly program the multiply a Dword array with
10
Example
You have a fixed array 1, 2, 3, 4, 5
Print 10, 20, 30, 40, 50
Key Idea
1. Load array element by element
2. Multiply loaded element by 10
3. Store element](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-29-320.jpg)
![.data
arr1 dword 1, 2, 3, 4, 5
multiplier dword 10
.code
main proc
cld
mov esi, offset arr1 ;initialize ESI for LODSD
instruction
mov edi, esi ;initialize EDI for STOSD instruction
mov ecx, lengthof arr1
l1:
lodsd ;mov eax, [esi]
mul multiplier ;edx:eax = eax * multiplier
stosd ;mov [edi], eax
loop l1](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-30-320.jpg)
![;display array elements…
mov ecx, lengthof arr1
mov esi, offset arr1
L2:
mov eax, [esi] ;Or use LODSB instruction…
call writeInt
call crlf
add esi, type arr1
Loop L2
exit
main endp
end main](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-31-320.jpg)
![Two Dimensional Arrays
Multi-dimensional arrays in assembly are defined as
single dimensional arrays… WHY??
For example, a 2D array can be defined as 1D array where
rows are concatenated in a single row.
Accessing items in 2D arrays can be done by indirect
memory addressing mode using a base register and an
index register like [ebx+esi].
In such addressing mode, a base register (i.e. ebx) should contain
the row offset while an index register (i.e. esi) should contain the
column offset.](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-33-320.jpg)
![[Solved Example] Sum 2D Arr
Given 2D array
Calculate it’s sum in the EAX
Then display it
Questions?
1. 2D Array how to declare?
2. How to parse/navigate from row to row? key idea](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-34-320.jpg)
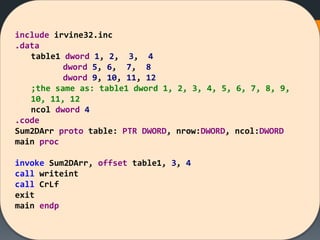
![Sum2DArr proc USES esi ecx ebx edx,
table: PTR DWORD, nrows:DWORD, ncols:DWORD
mov esi, table ;ESI = start of 1st row
mov ecx, nrows ;ECX: # of rows
; will be used as a row index
mov edx, ncols
shl edx, 2 ;EDX: # of bytes in each row (ncols*4)
mov ebx, 0 ;col index
mov eax, 0 ;EAX: accumulator for the result
l1:
.while ebx < ncols
add eax, [esi+4*ebx]
inc ebx
.endw
mov ebx,0 ;Reset col. Index for each row
add esi, edx ;ESI: points to the next row
loop l1
ret
Sum2DArr endp](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-36-320.jpg)
![[Hands On] Sum i Col. In 2D Arr
Calculate the sum of a given column in a 2D array
USING PROC
Given in .data
table1 dword 1, 2, 3, 4
dword 5, 6, 7, 8
dword 9, 10, 11, 12
Col to be summed = 3
Sum = 24](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-37-320.jpg)
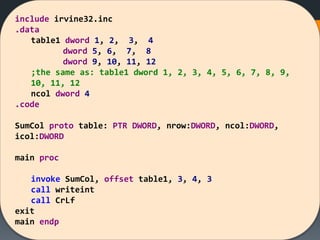
![SumCol proc USES esi ecx ebx edx,
table: PTR DWORD, nrows:DWORD, ncols:DWORD, icol:DWORD
mov esi, table ;ESI: points to the beginning of array
(1st row) base reg
mov ecx, nrows ;ECX: # of rows
; will be used as a row index
mov edx, ncols
shl edx, 2 ;EDX: # of bytes in each row (ncols*4)
mov ebx, icol ;EBX: index of target column
mov eax, 0 ;EAX: accmulator for the result
l1:
add eax, [esi+4*ebx]
add esi, edx ;ESI: points to the next row
loop l1
ret
SumCol endp
end main](https://image.slidesharecdn.com/asmlab8-151121102357-lva1-app6892/85/ASM-Lab8-39-320.jpg)