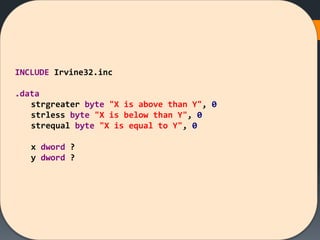
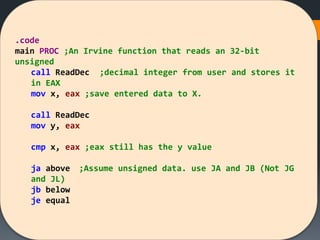
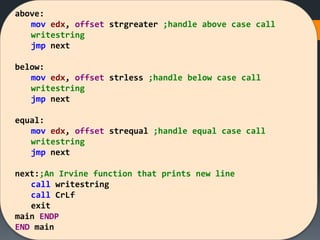
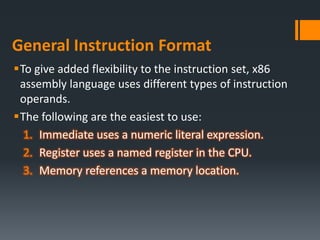
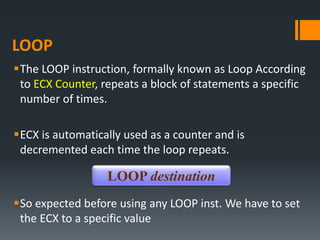
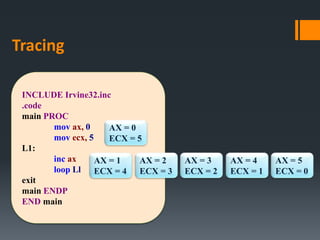
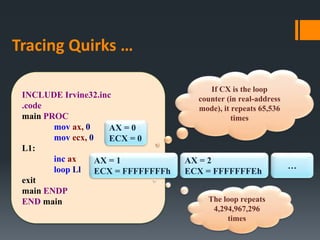
The document discusses assembly language instructions and concepts. It covers:
- Basic instruction formats and operand types like registers, memory, and immediates.
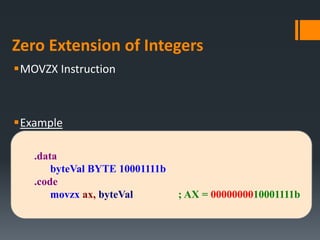
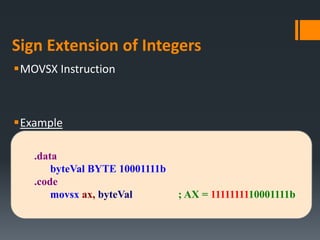
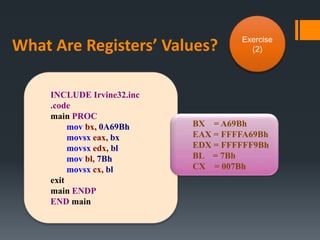
- Data transfer instructions like MOV, and addressing modes like direct offset addressing of arrays.
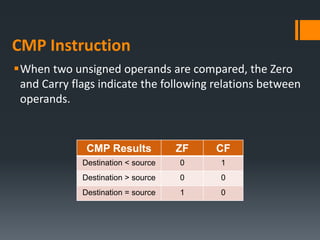
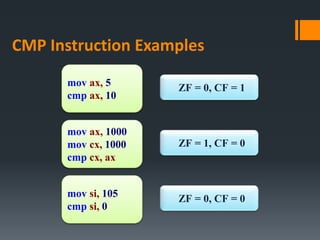
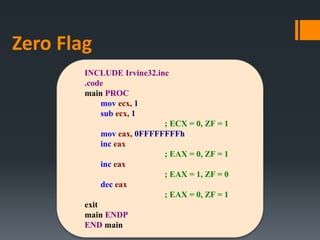
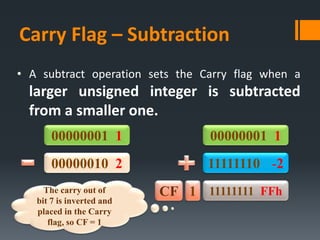
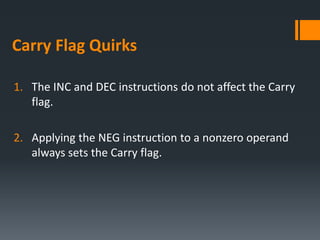
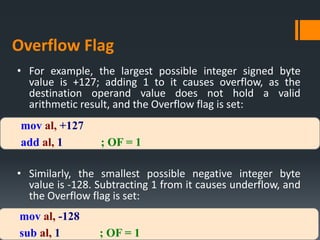
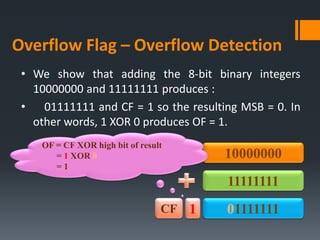
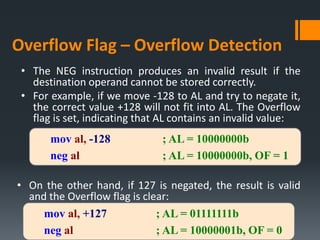
- Arithmetic instructions like ADD, SUB, INC, DEC, and NEG, and how they affect status flags.
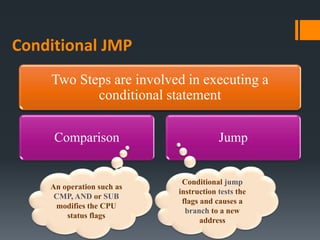
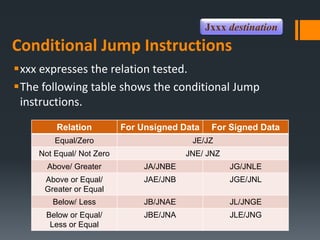
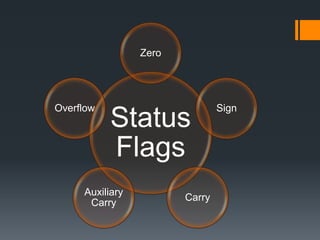
- Status flags like zero, carry, sign, auxiliary carry, parity, and overflow flags which provide information about instruction results.


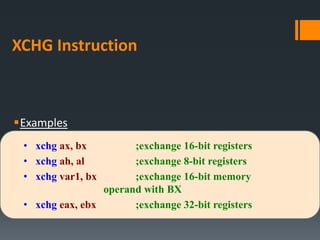
![General Instruction Format
Because the number of operands may vary, we can
further subdivide the formats to have zero, one, two, or
three operands. Here, we omit the label and comment
fields for clarity:
mnemonic
mnemonic [destination]
mnemonic [destination], [source]
mnemonic [destination], [source-1], [source-2]
[label:] mnemonic [operands][ ; comment ]](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-4-320.jpg)








![Direct-Offset Operands
Adding a displacement to the name of a variable
(creating a direct-offset operand) is useful when it is
needed to access memory locations that may not have
explicit label. (ARRAYS!!)
.data
arrayB BYTE 10h, 20h , 30h, 40h, 50h
.code
mov al, arrayB ;AL = 10h
mov al, [arrayB + 1] ;AL = 20h
mov al, [arrayB + 2] ;AL = 30h
Adding 1 to
the off`set
of arrayB
Adding 2 to
the offset of
arrayB](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-19-320.jpg)
![Direct-Offset Operands
arrayB + 1
Effective
Address
[arrayB + 1]
Dereferencing the
expression to obtain
the contents of
memory at the
address
mov al, arrayB + 1
mov al, [arrayB + 1]
The brackets are not
required by MASM,
so these statements
are equivalent](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-20-320.jpg)
![Direct-Offset Operands
Range Checking
MASM has no built-in range checking for effective
addresses.
If we execute the following statement, the assembler just
retrieves a byte of memory outside the array.
mov al, [arrayB + 20]
In other words
there is no
index out of
range exception
:D](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-21-320.jpg)
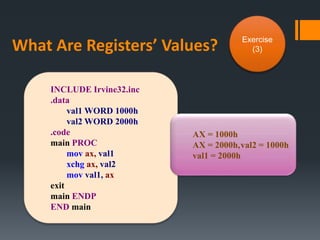
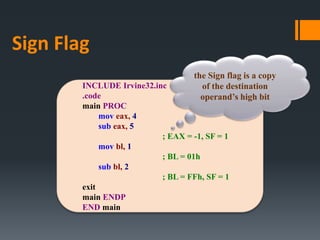
![What Are AL’ Values? Exercise
(4)
INCLUDE Irvine32.inc
.data
arrayB BYTE 10h, 20h, 30h, 40h, 50h
.code
main PROC
mov al, arrayB
mov al, [arrayB + 1]
mov al, arrayB + 2
exit
main ENDP
END main
AL = 10h
AL = 20h
AL = 30h](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-22-320.jpg)

![What are the AX’s values?
INCLUDE Irvine32.inc
.data
arrayW WORD 1000h, 2000h, 3000h
.code
main PROC
mov ax, arrayW
mov ax, [arrayW + 2]
exit
main ENDP
END main
AX = 1000h
AX = 2000h
Adding 2 to the
offset of arrayW
to access the
second element
Exercise
(5)](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-24-320.jpg)

![What are the EAX’s values?
INCLUDE Irvine32.inc
.data
arrayD DWORD 10000000h, 20000000h
.code
main PROC
mov eax, arrayD
mov eax, [arrayD + 4]
exit
main ENDP
END main
EAX = 10000000h
EAX = 20000000h
Adding 4 to the
offset of arrayD
to access the
second element
Exercise
(6)](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-26-320.jpg)
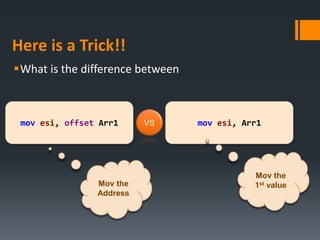
![Here is a trick !!
What about this?
INCLUDE Irvine32.inc
.data
arrayD WORD 1011h, 2022h
.code
main PROC
movzx eax, arrayD
movzx eax, [arrayD + 1]
exit
main ENDP
END main
100 • 11
102 • 10
103 • 22
104 • 20
Little
Indian
AX = 1011h
AX = 2210h](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-27-320.jpg)

























![4. Indirect Memory Addressing
100 Main
Memory
EBX
MOV EAX, [EBX]](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-66-320.jpg)
![4. Indirect Memory Addressing
100 Main
Memory
EBX
103MOV ECX, [EBX + 3]
Base Displacement
Addressing](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-67-320.jpg)
![4. Indirect Memory Addressing
100 Main
Memory
EBX
150MOV ECX, [EBX + ESI]
Base‐Index
Addressing
50ESI](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-68-320.jpg)
![4. Indirect Memory Addressing
100 Main
Memory
EBX
154MOV ECX, [EBX + ESI + 4]
Base‐Index with
Displacement
Addressing
50ESI](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-69-320.jpg)
![5. Direct Offset Addressing
It is similar to accessing items in an array, but the number
used represents the number of bytes, not the index of
the items.
MOV CL, byteArr[2]
MOV CL, [byteArr + 2]
MOV CL, byteArr + 2
The instruction
copies the byte that
is distanced two
bytes from byteArr
to CL](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-70-320.jpg)






![.data
Arr1DWORD10, 20, 30, 40, 50
sum_val DWORD?
.code
main PROC
mov esi, offset Arr1;put array address in esi
mov eax, 0;initialize eax by zero for temp sum
mov ecx, 5;initialize ecx (loop counter)
;by array size
sum_loop:
add eax, DWORD PTR [esi]
add esi, 4;increment esi pointer by 4
;(size of array element)
loop sum_loop ;ECX decremented implicitly by LOOP
instruction
call writeint ;output the sum (which already stored
in EAX)
mov sum_val, eax
call CrLf](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-81-320.jpg)
![Notes
PTR is an operator that overrides the size of an operand. It is always
preceded by a Type (BYTE, WORD, DWORD…etc). In the instruction add
eax, DWORD PTR [esi], you can remove DWORD PTR as the assembler
will assume a default size equals to the size of the second operand which
in this case DWORD. If ax is used instead of eax, WORD size will be
assumed and so on.
Writeint function is a function defined in Irvine library. It prints a signed
integer stored in EAX on the screen.
LENGTHOF operator retrieves the length of an array. For example, the
instruction mov ECX, LENGTHOF Arr1 gets the length of Arr1 array and
stores it in ECX.
TYPE operator retrieves the number of bytes allocated for each item in
the given array. For example, the instruction add esi, TYPE Arr1 adds 4 to
esi if Arr1 is DWORD array, adds 2 if Arr1 is WORD array and adds 1 if
Arr1 is BYTE array](https://image.slidesharecdn.com/asmlab4-151121101809-lva1-app6891/85/ASM-Lab4-83-320.jpg)