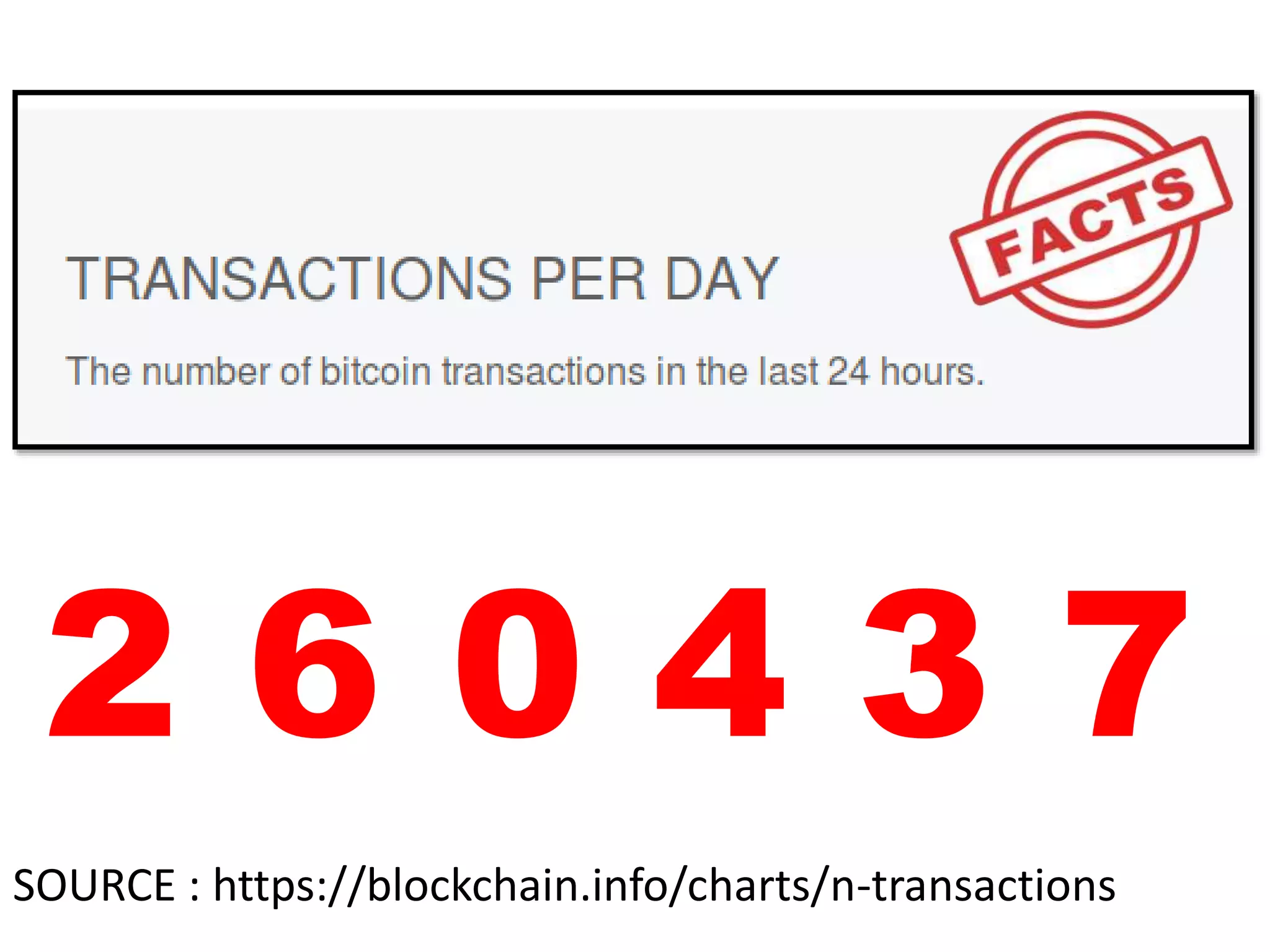
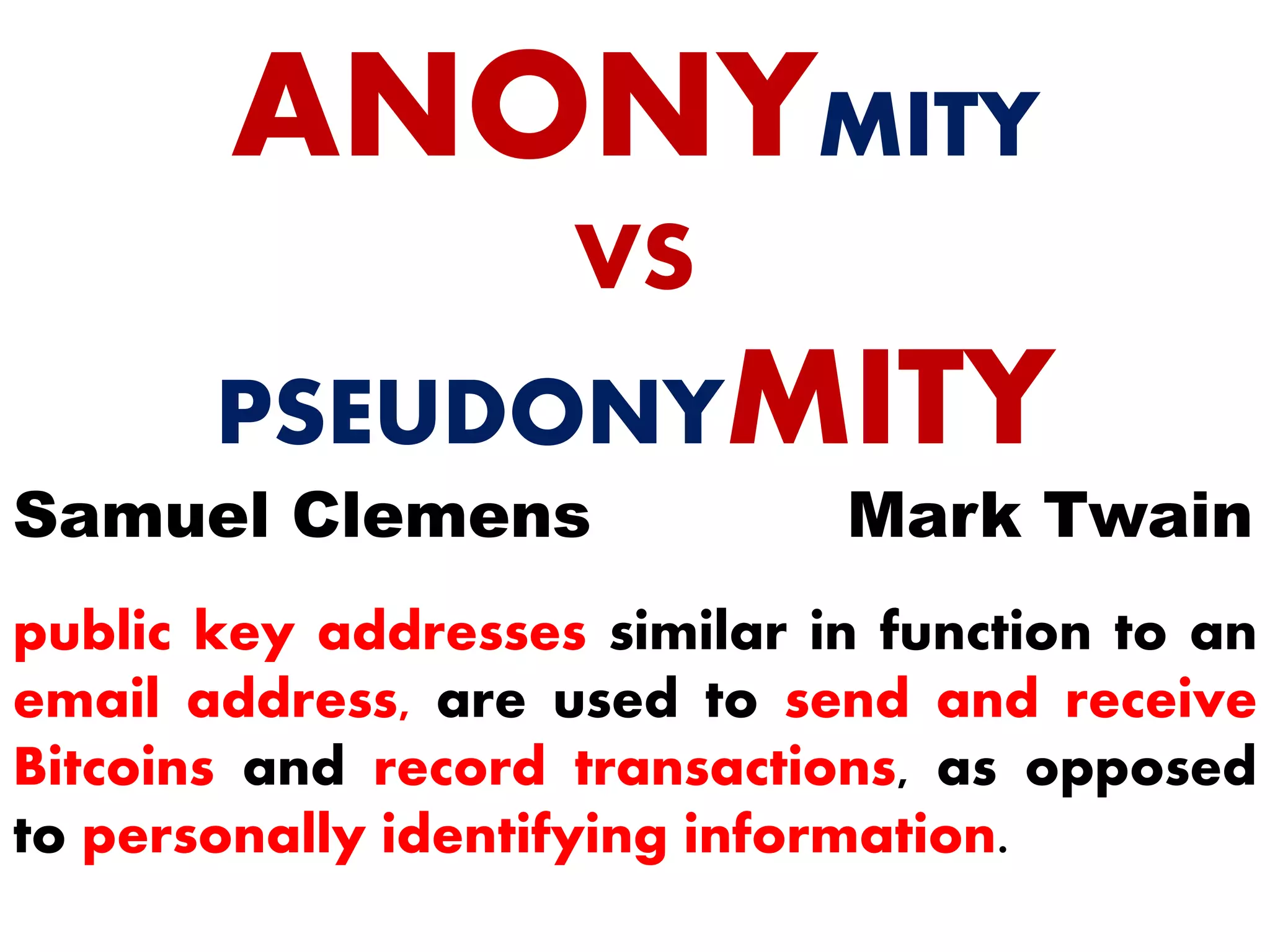
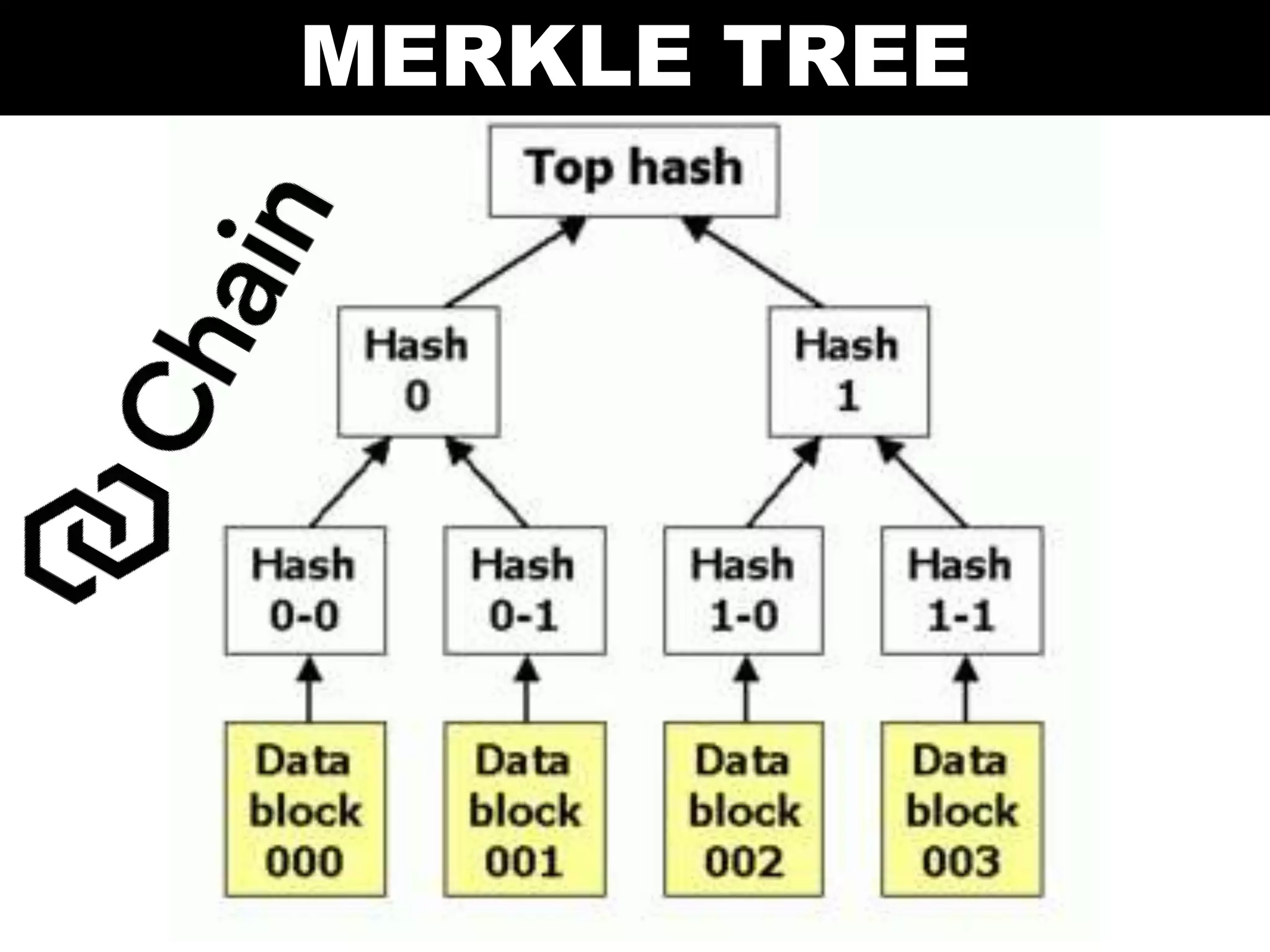
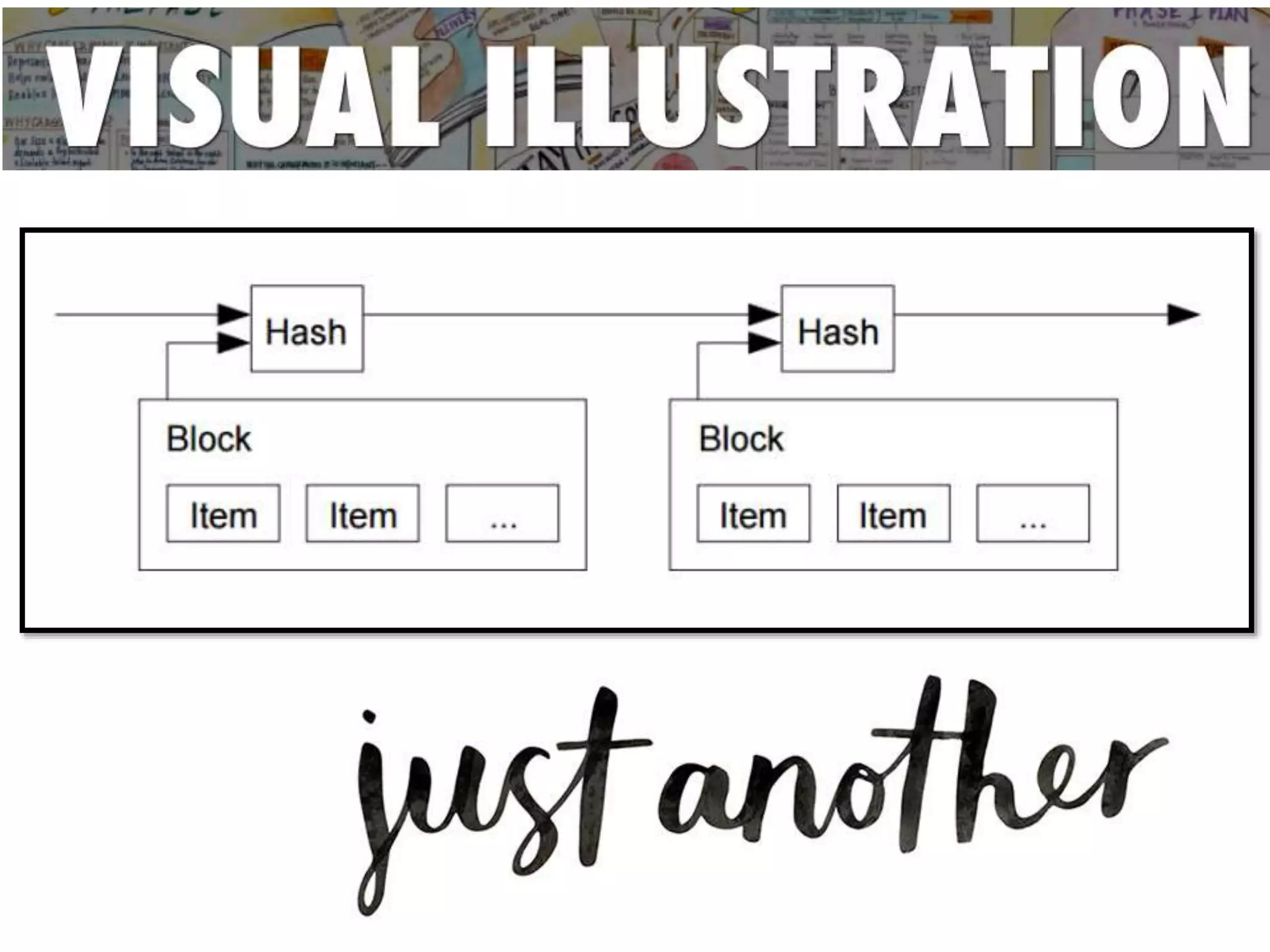
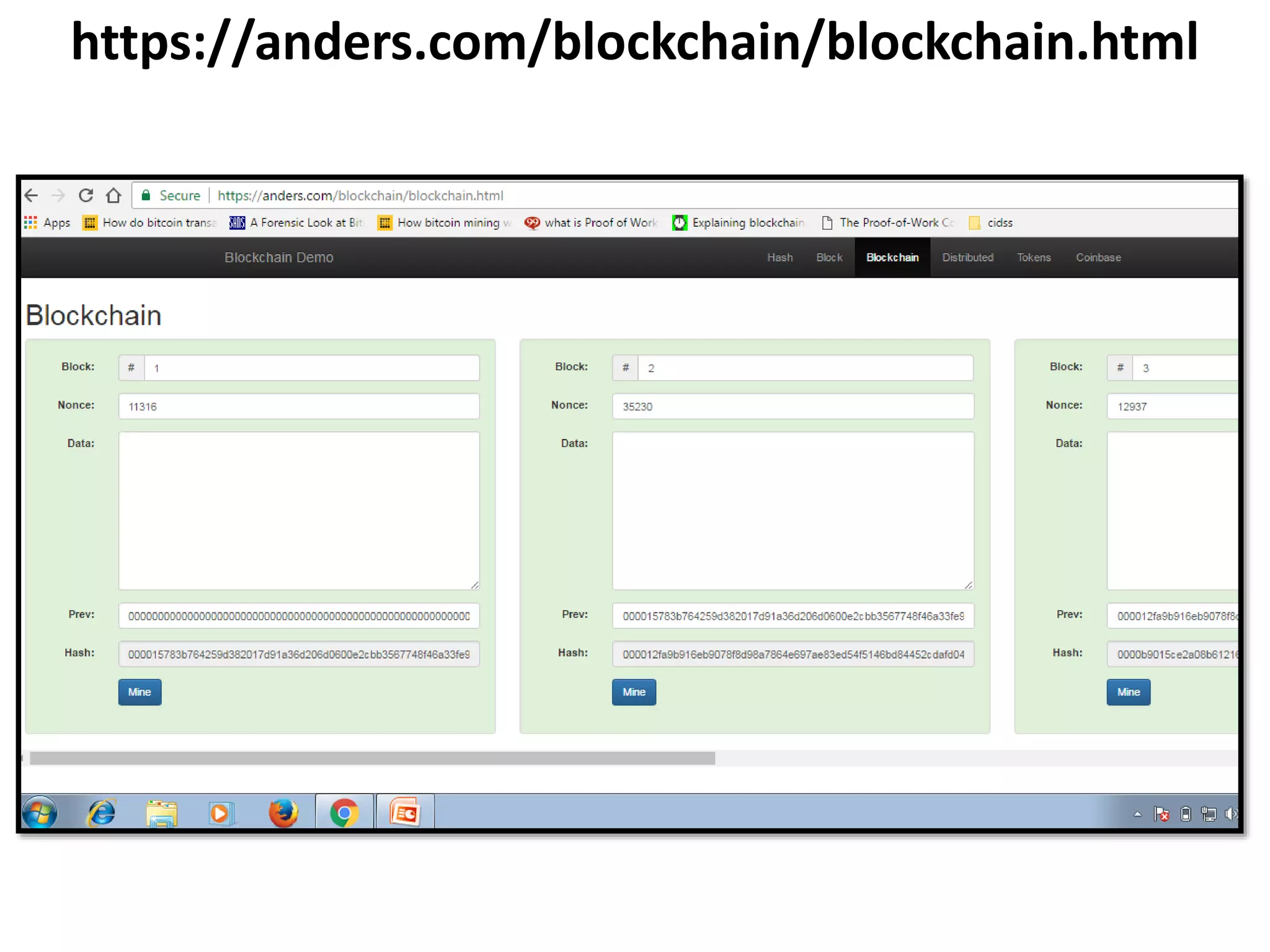
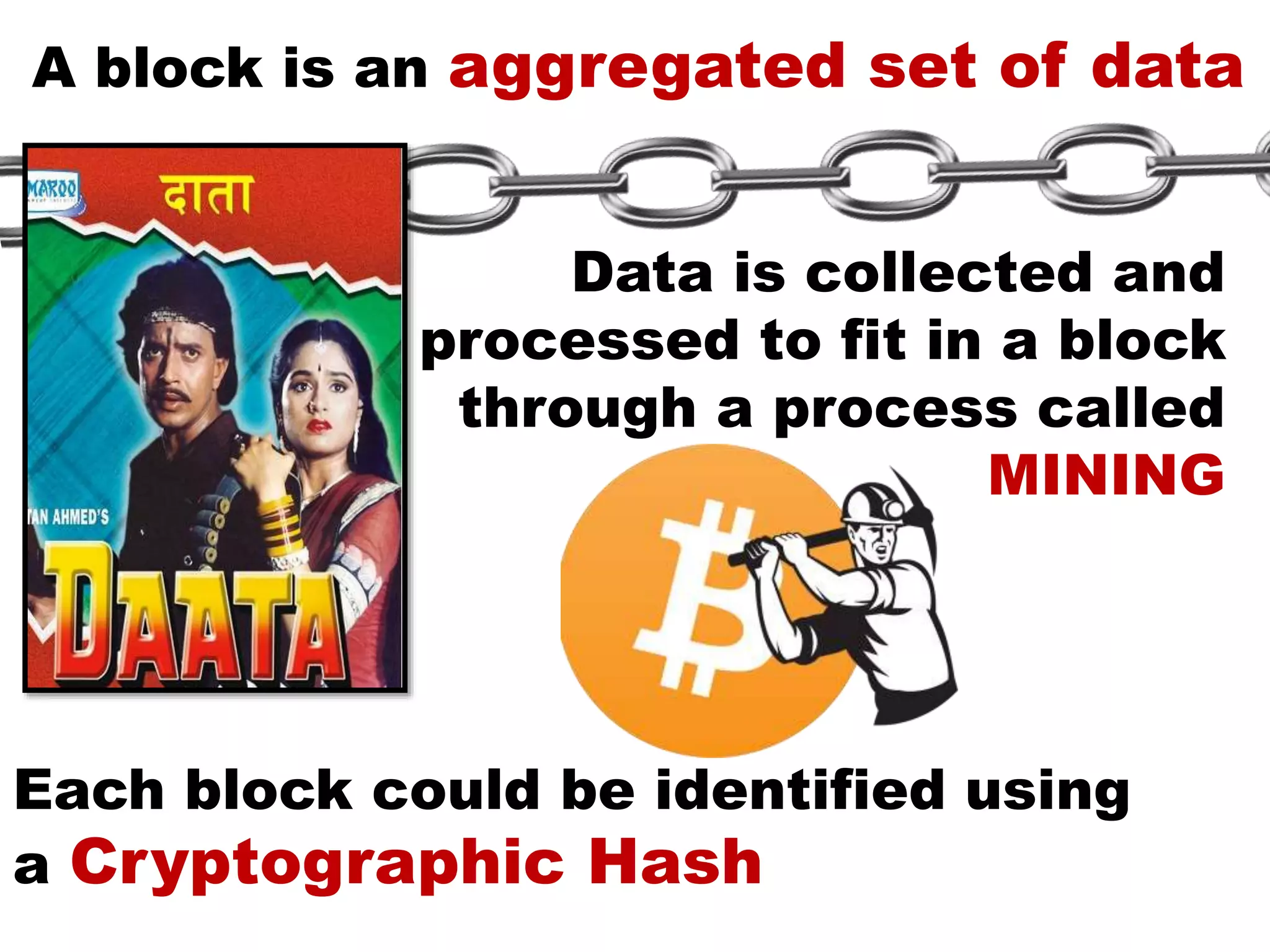
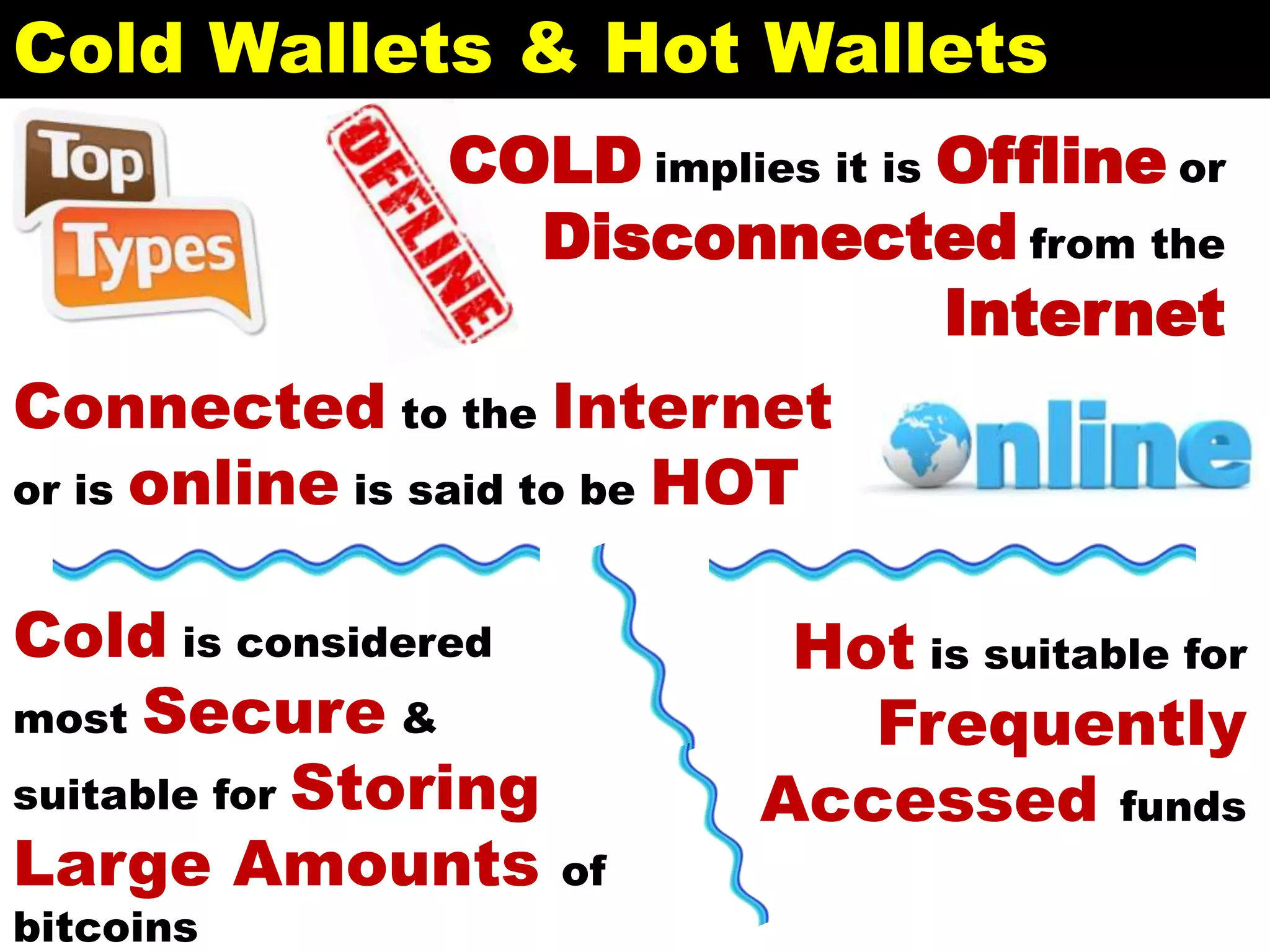
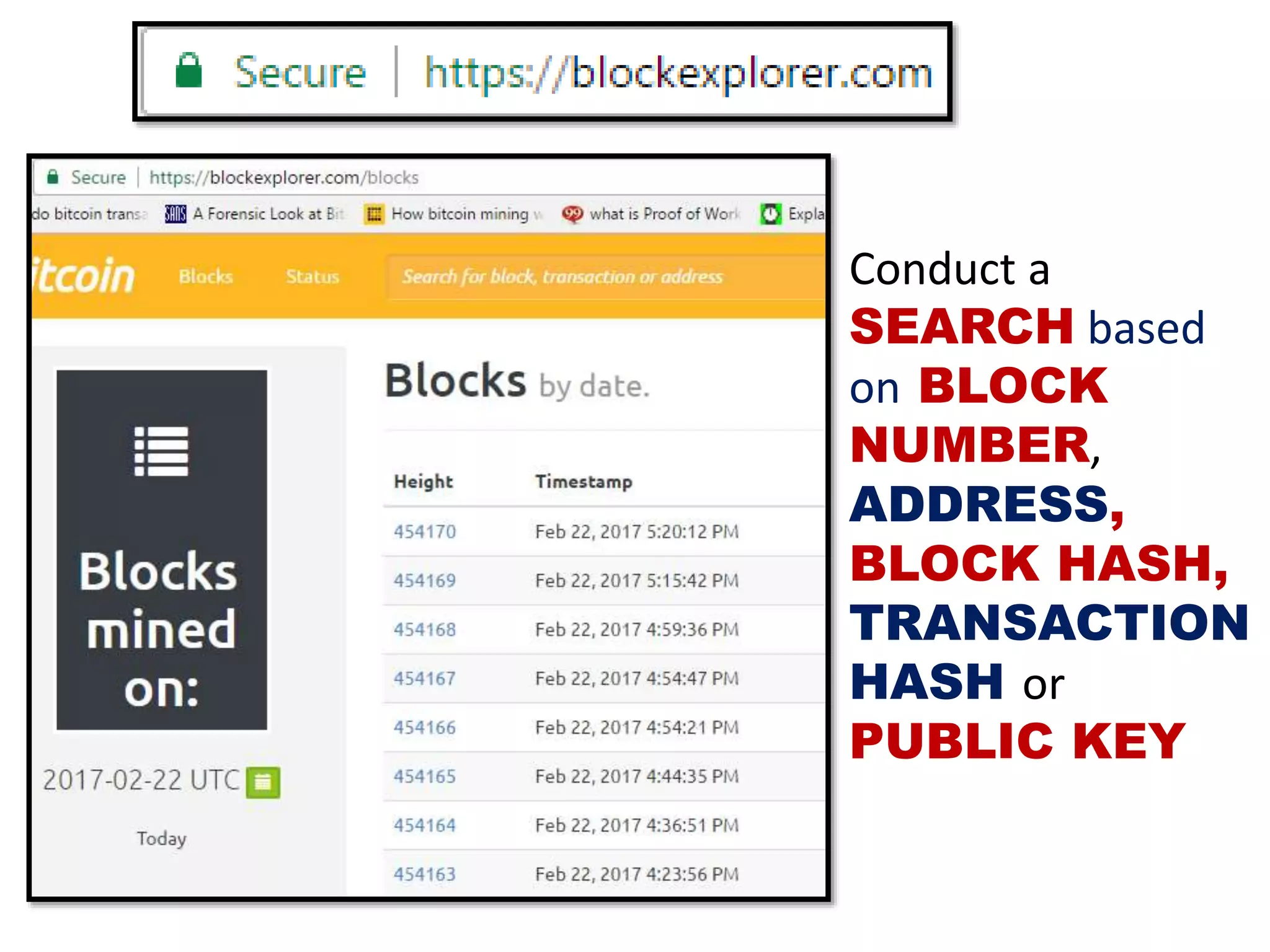
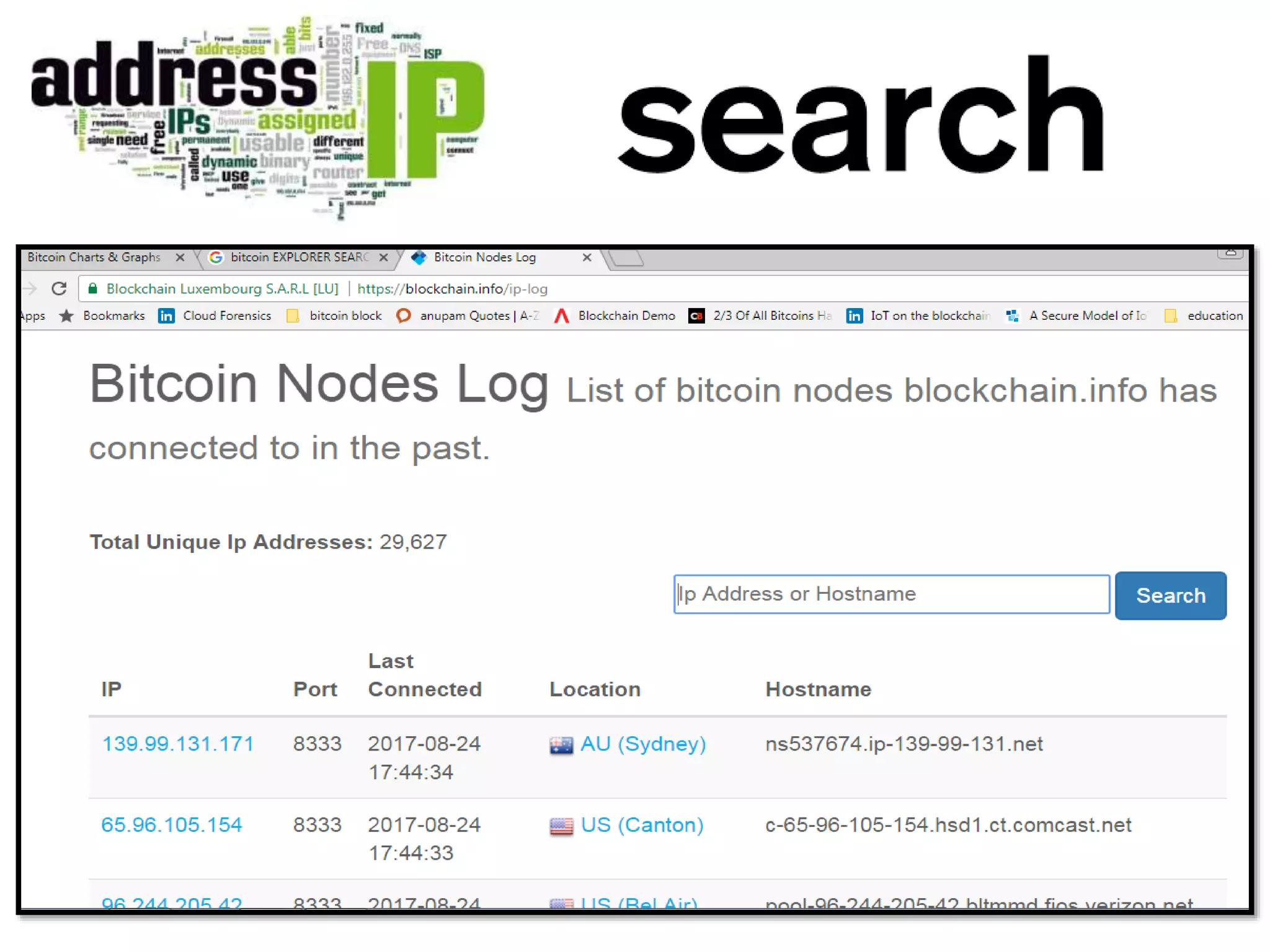
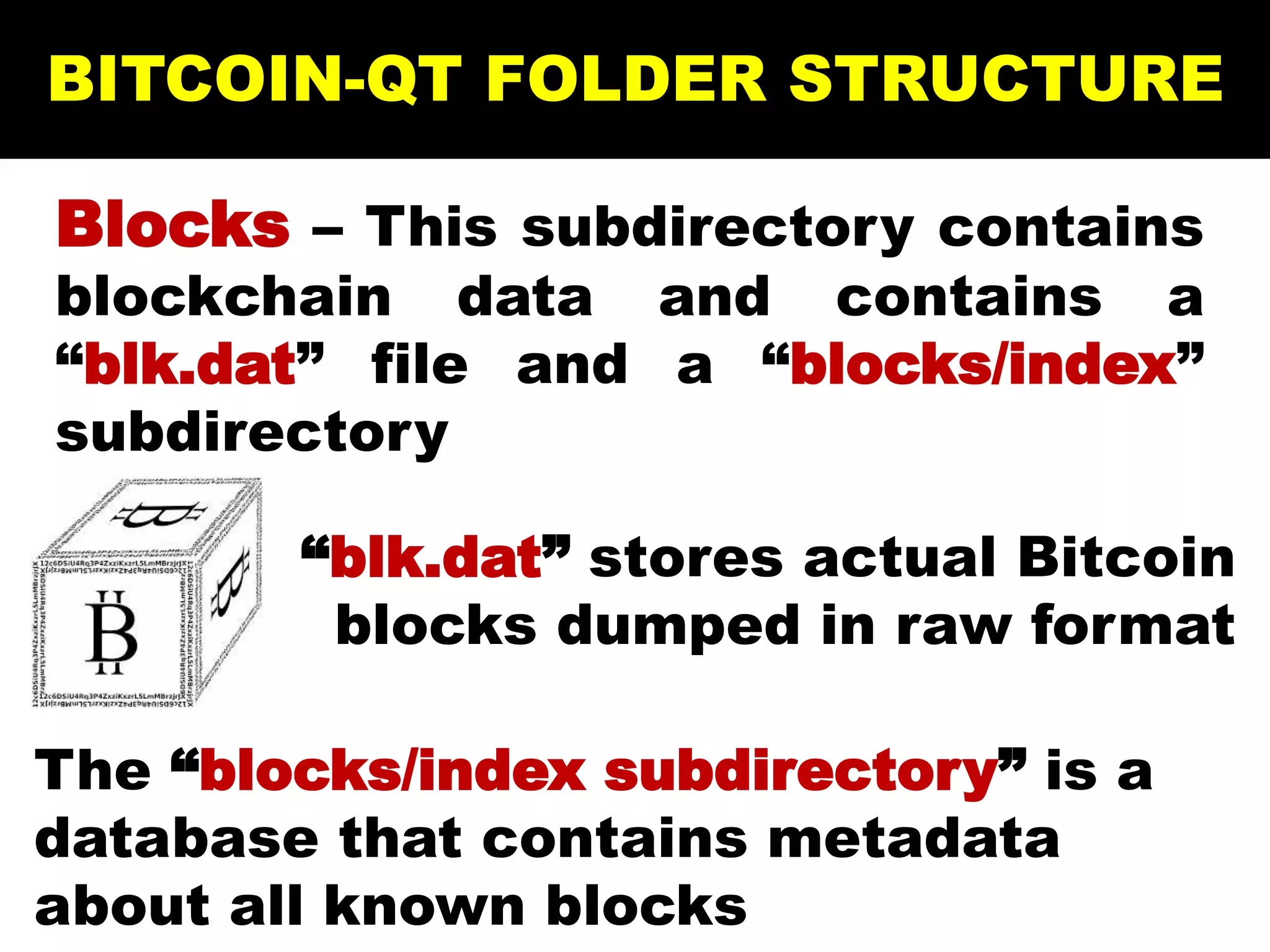
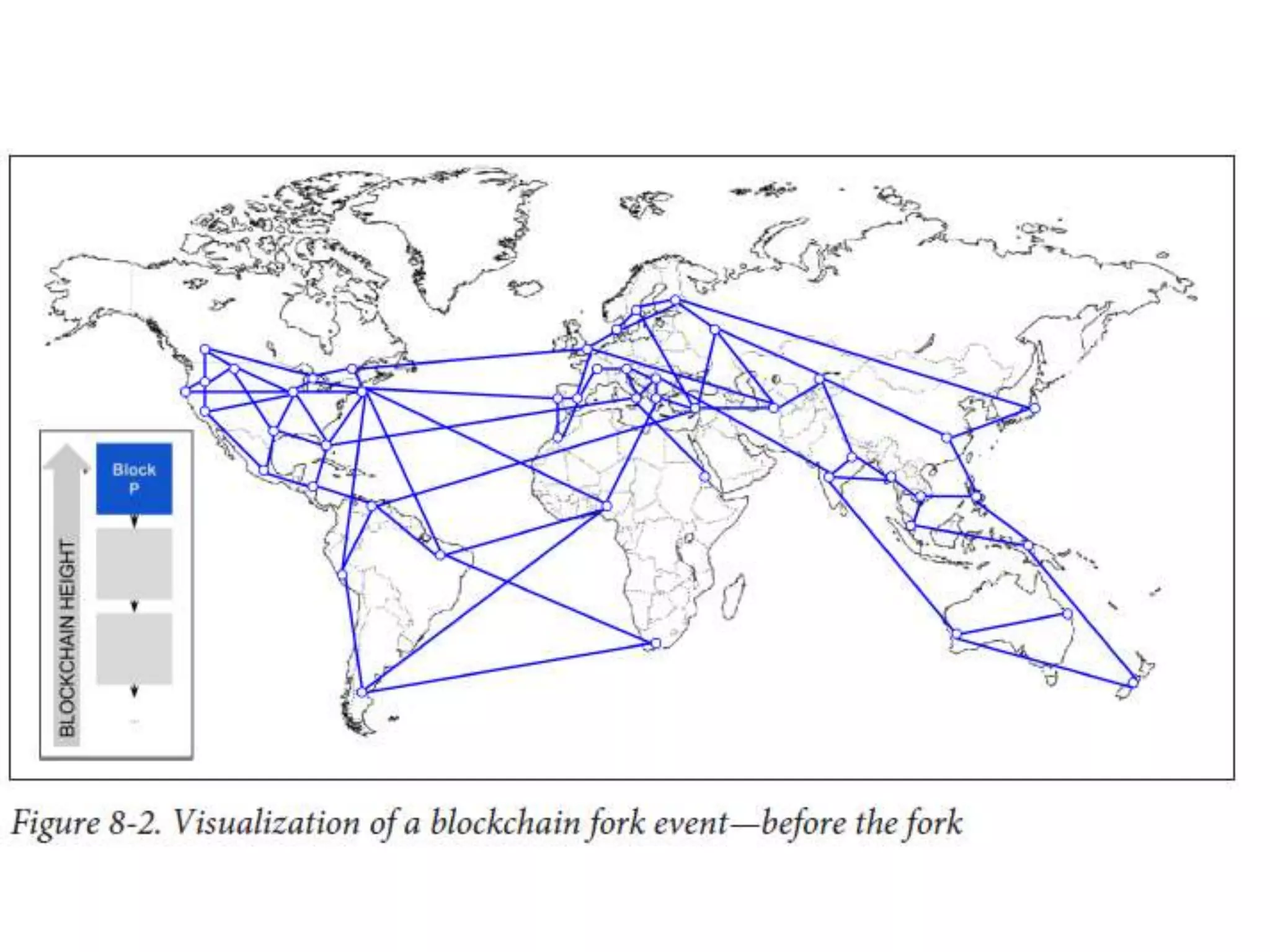
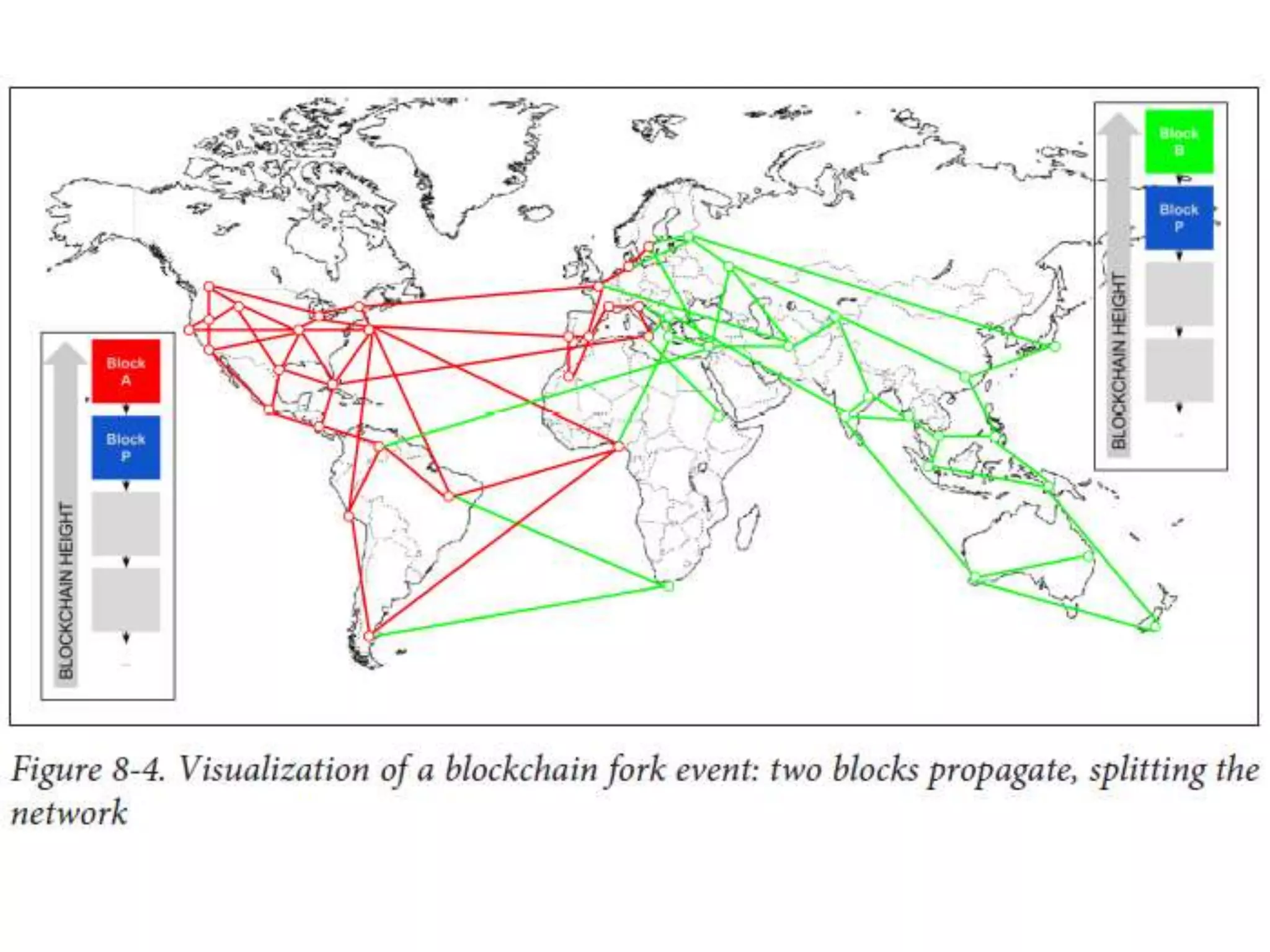
The document discusses Bitcoin and its underlying technology, blockchain, emphasizing its decentralized nature and implications for anonymity and forensic investigation. It outlines the functionality of Bitcoin wallets, mining processes, and the importance of consensus in adding blocks to the blockchain. Additionally, it touches on the emergence of smart contracts and the challenges in tracing digital transactions for investigative purposes.