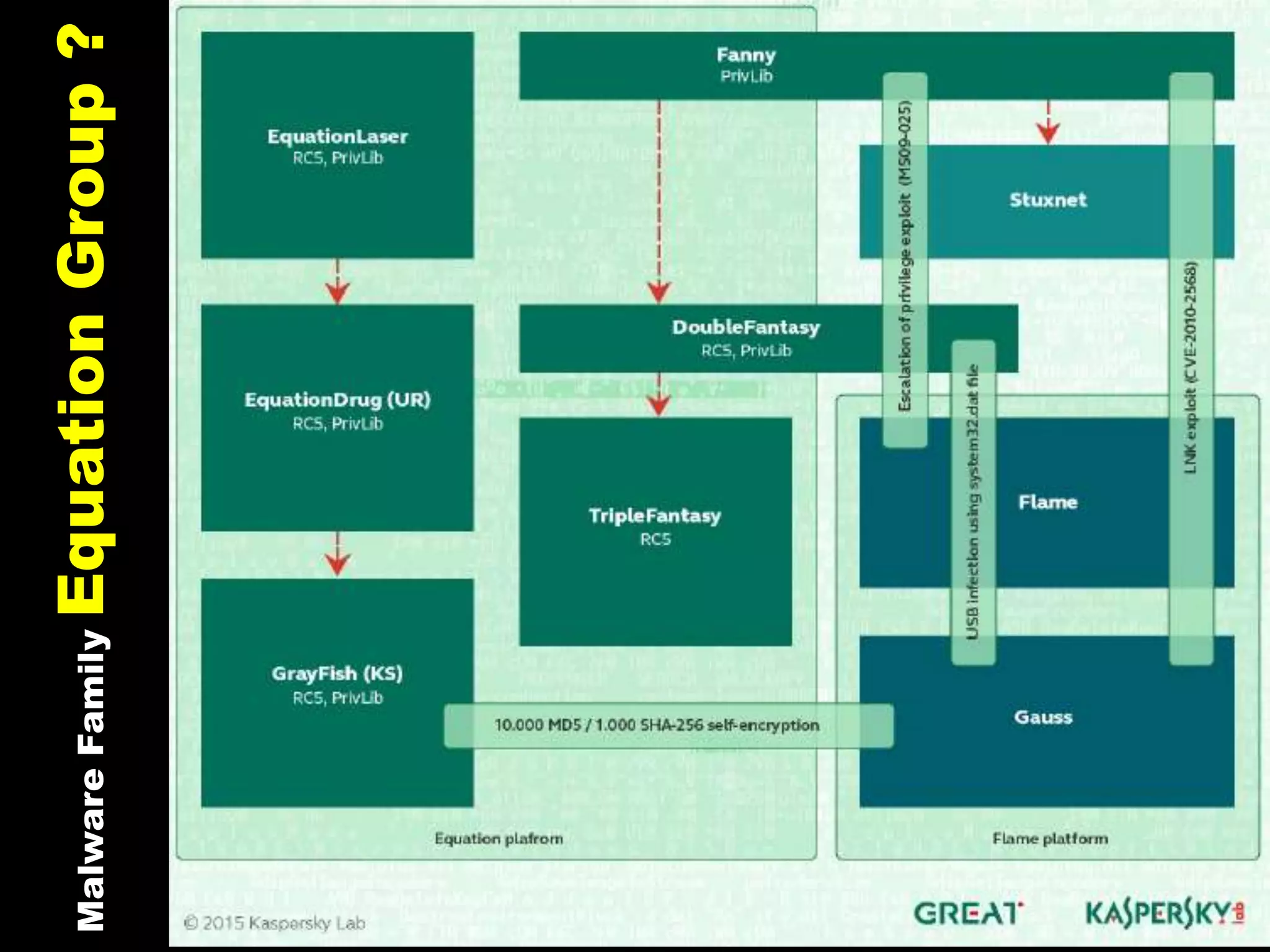
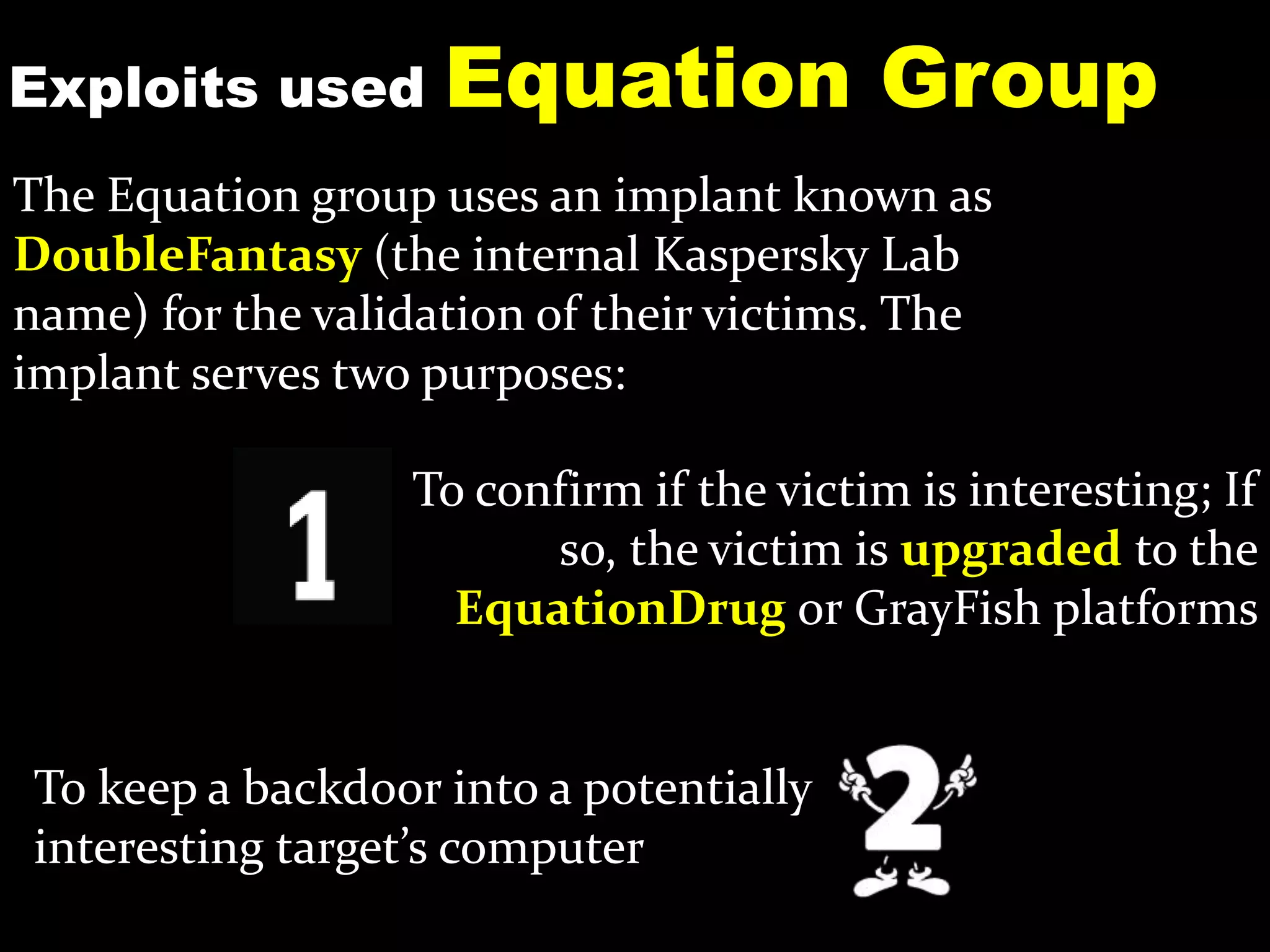
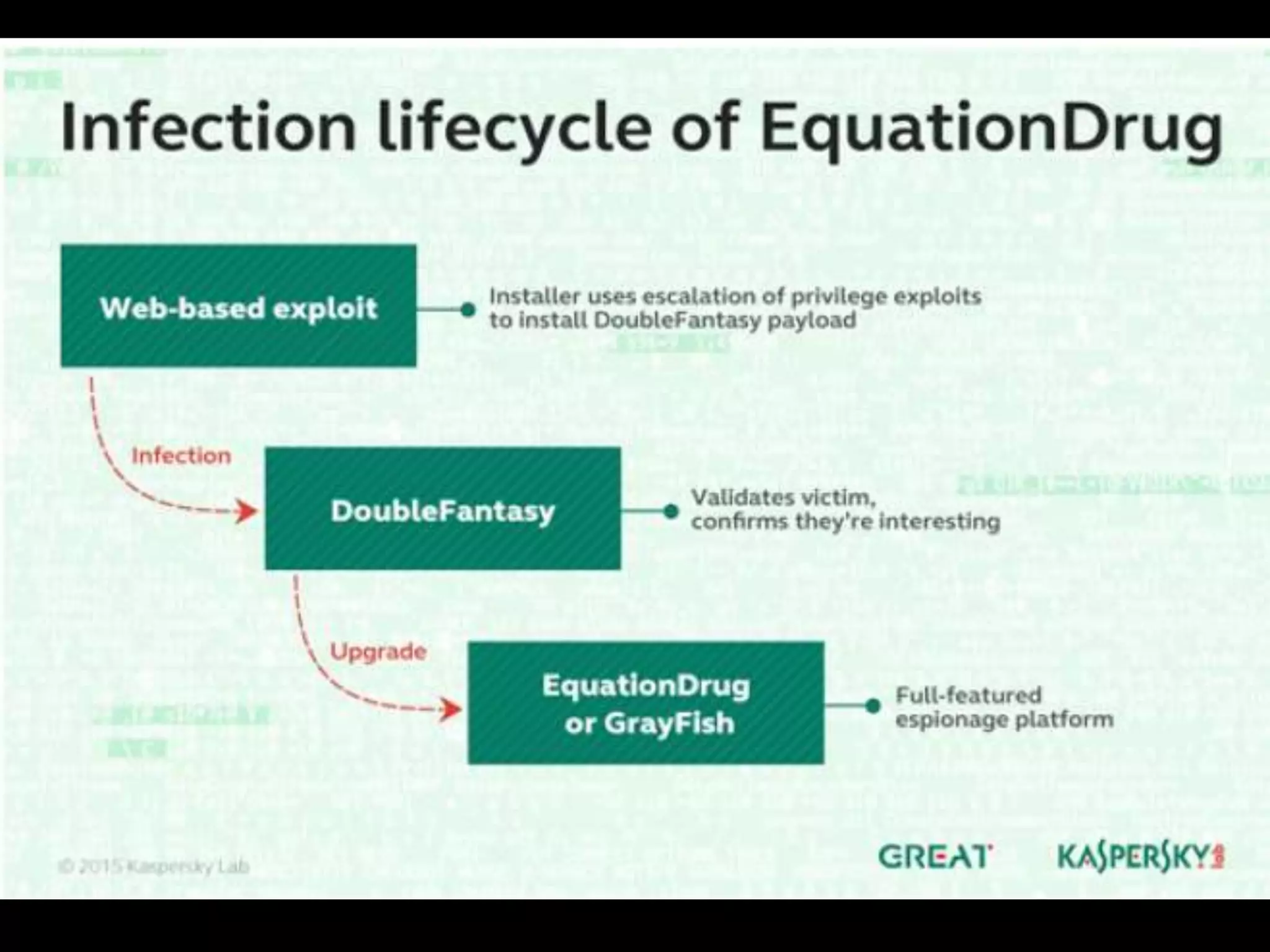
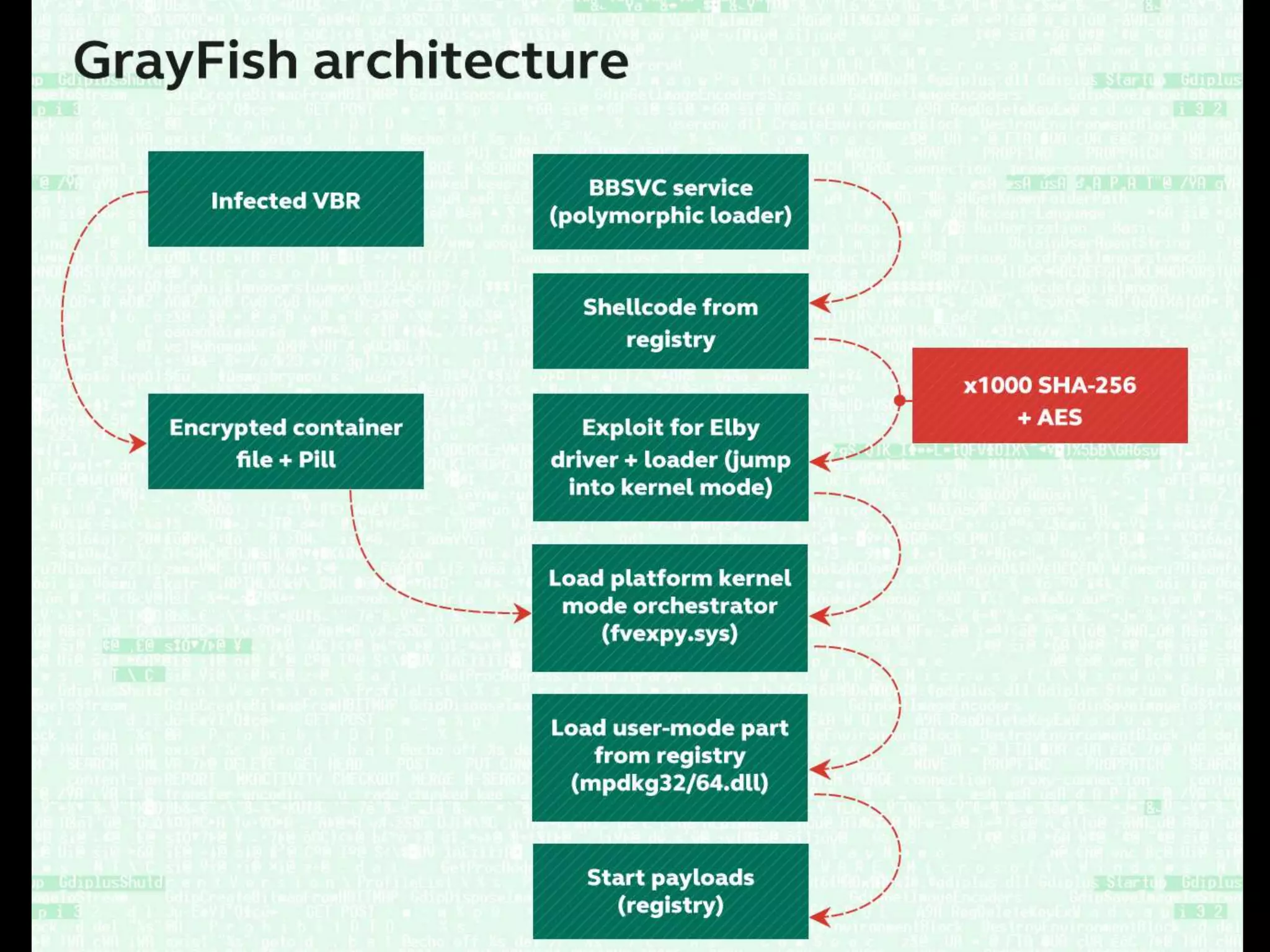
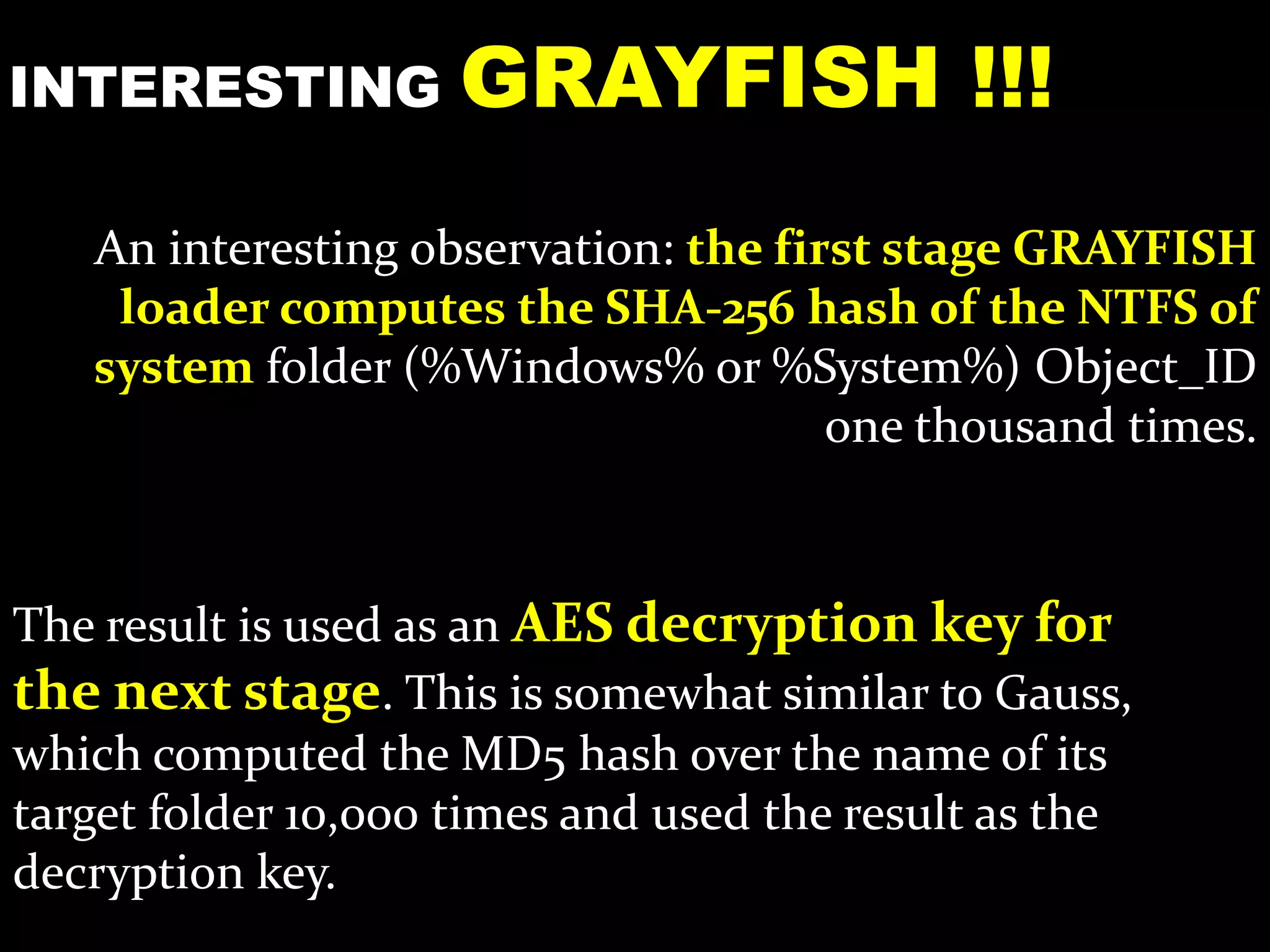
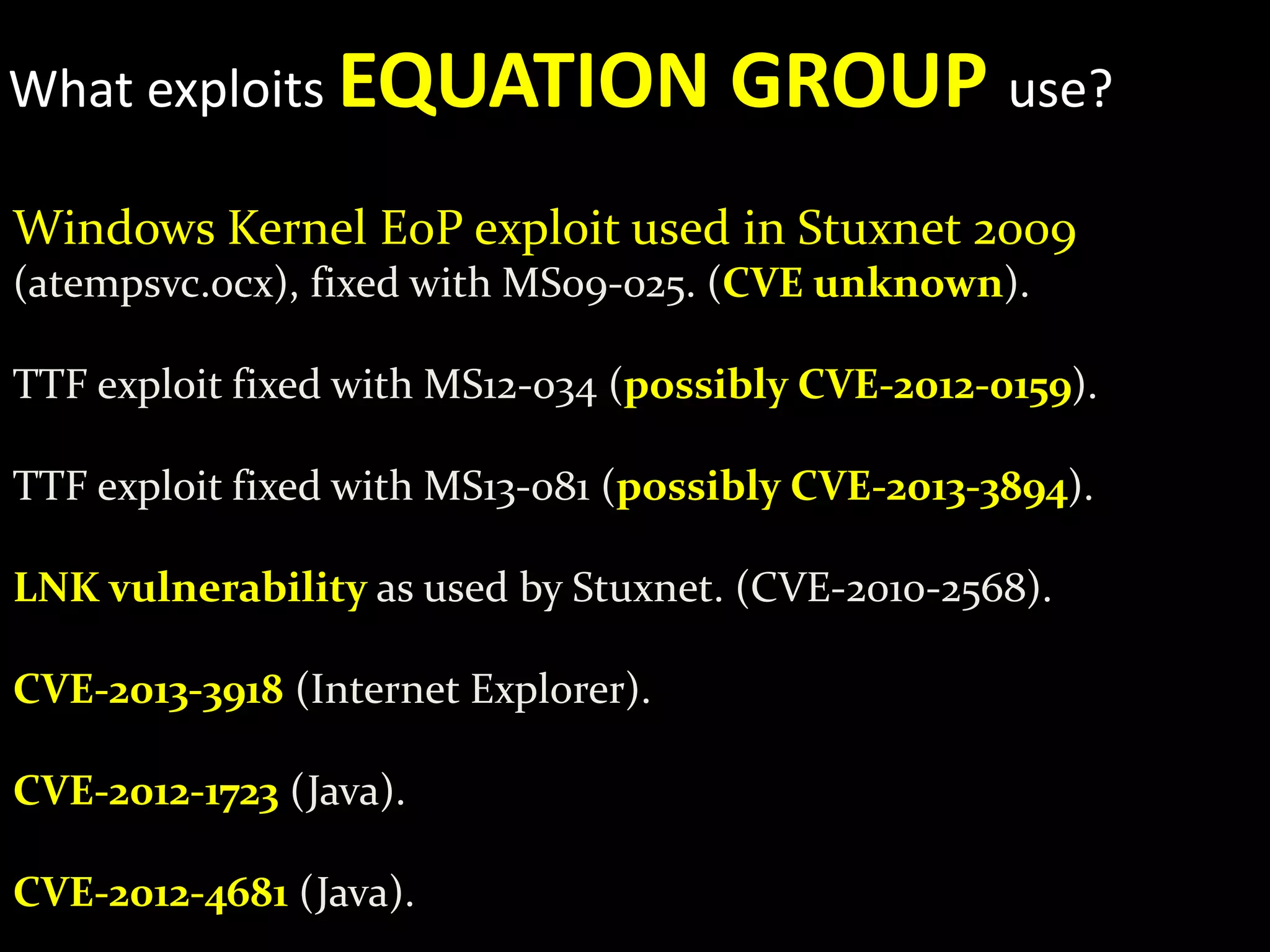
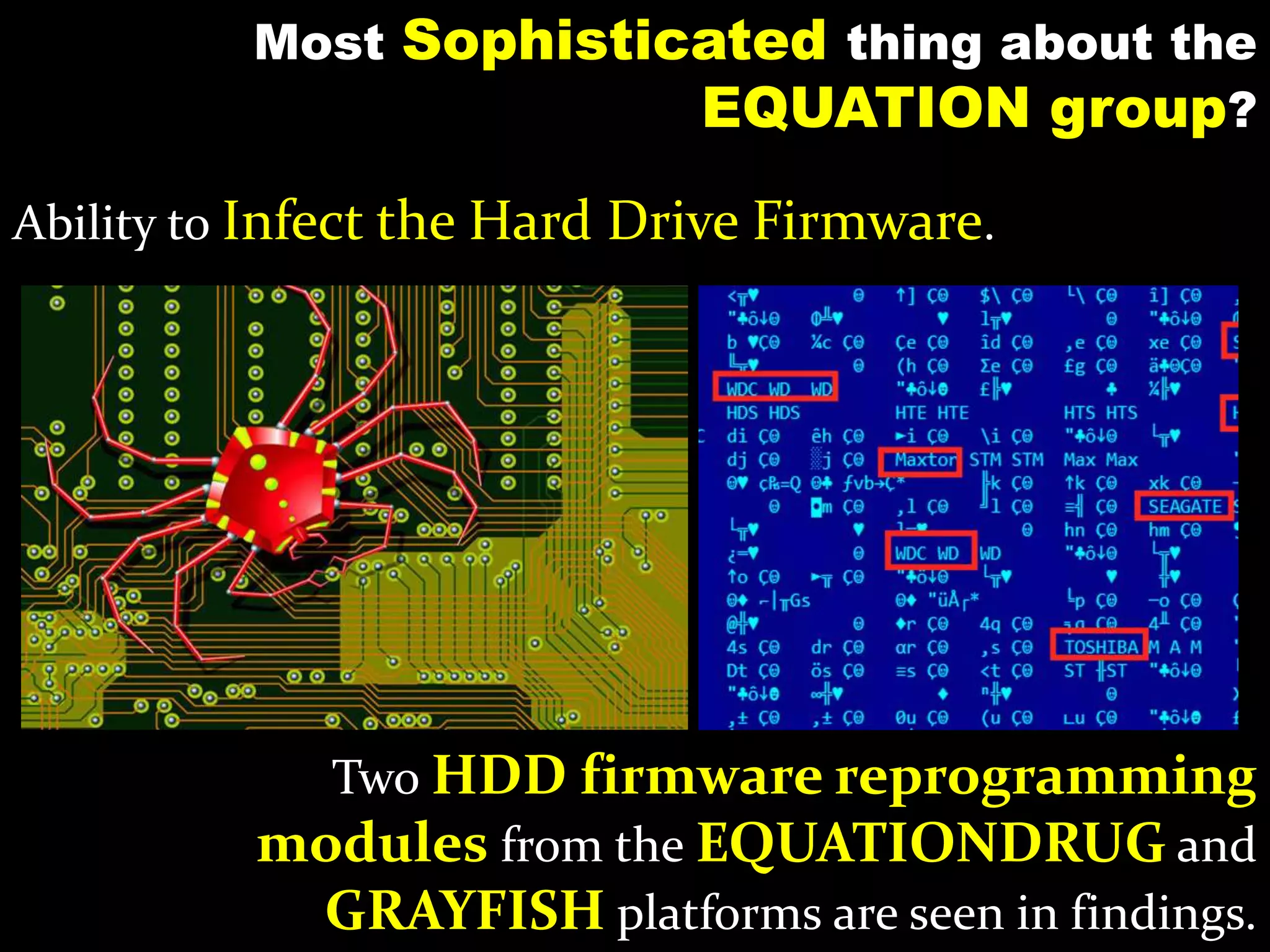
The document discusses the Equation Group, a sophisticated threat actor involved in computer network exploitation since the late 1990s, known for their advanced malware platforms utilizing complex encryption methods. Key malware includes DoubleFantasy, used to validate victims, and EquationDrug and Grayfish, which offer advanced espionage capabilities and persistence mechanisms. The Group employs various methods for infection and has a vast command and control infrastructure across multiple countries.