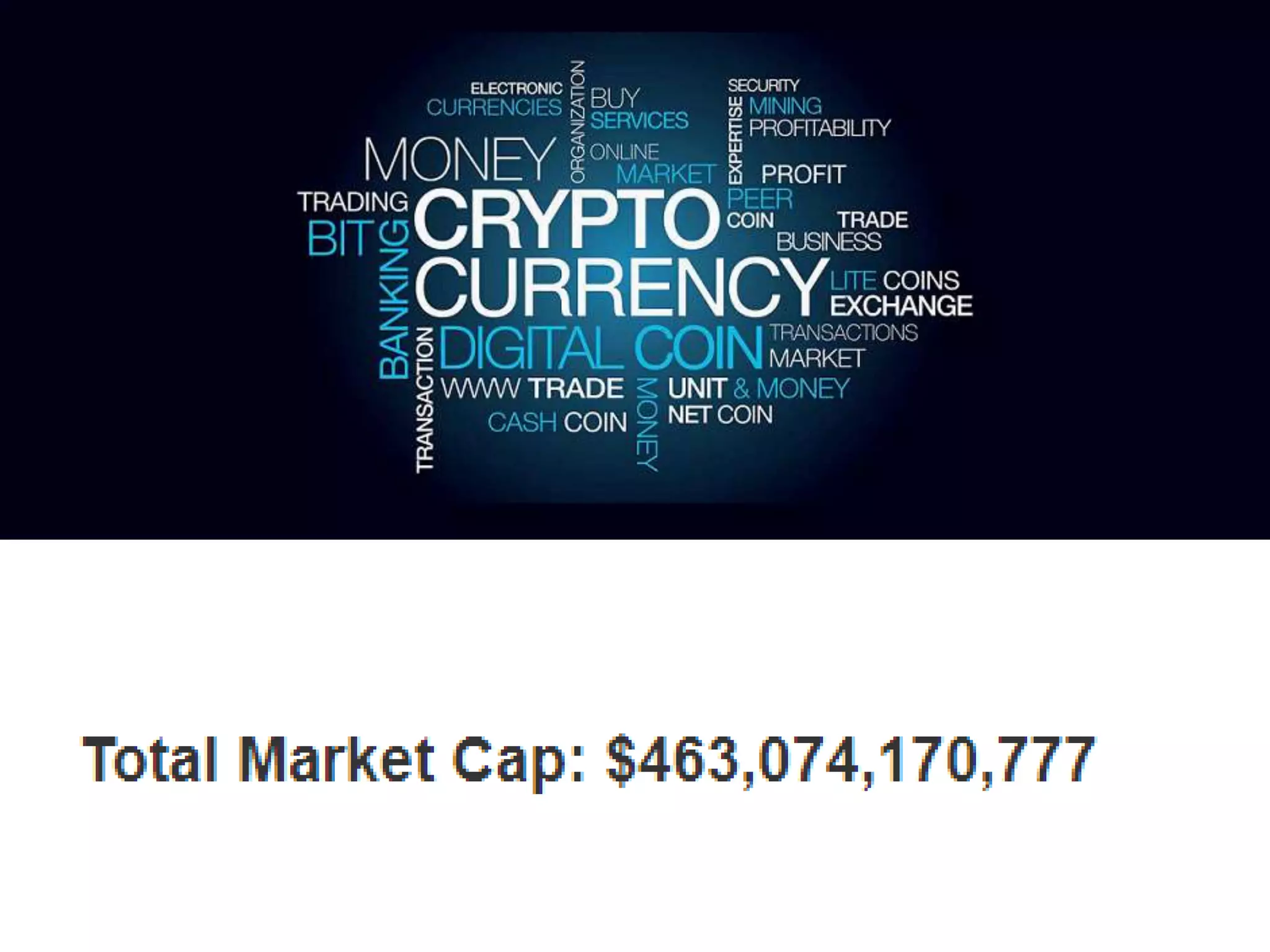
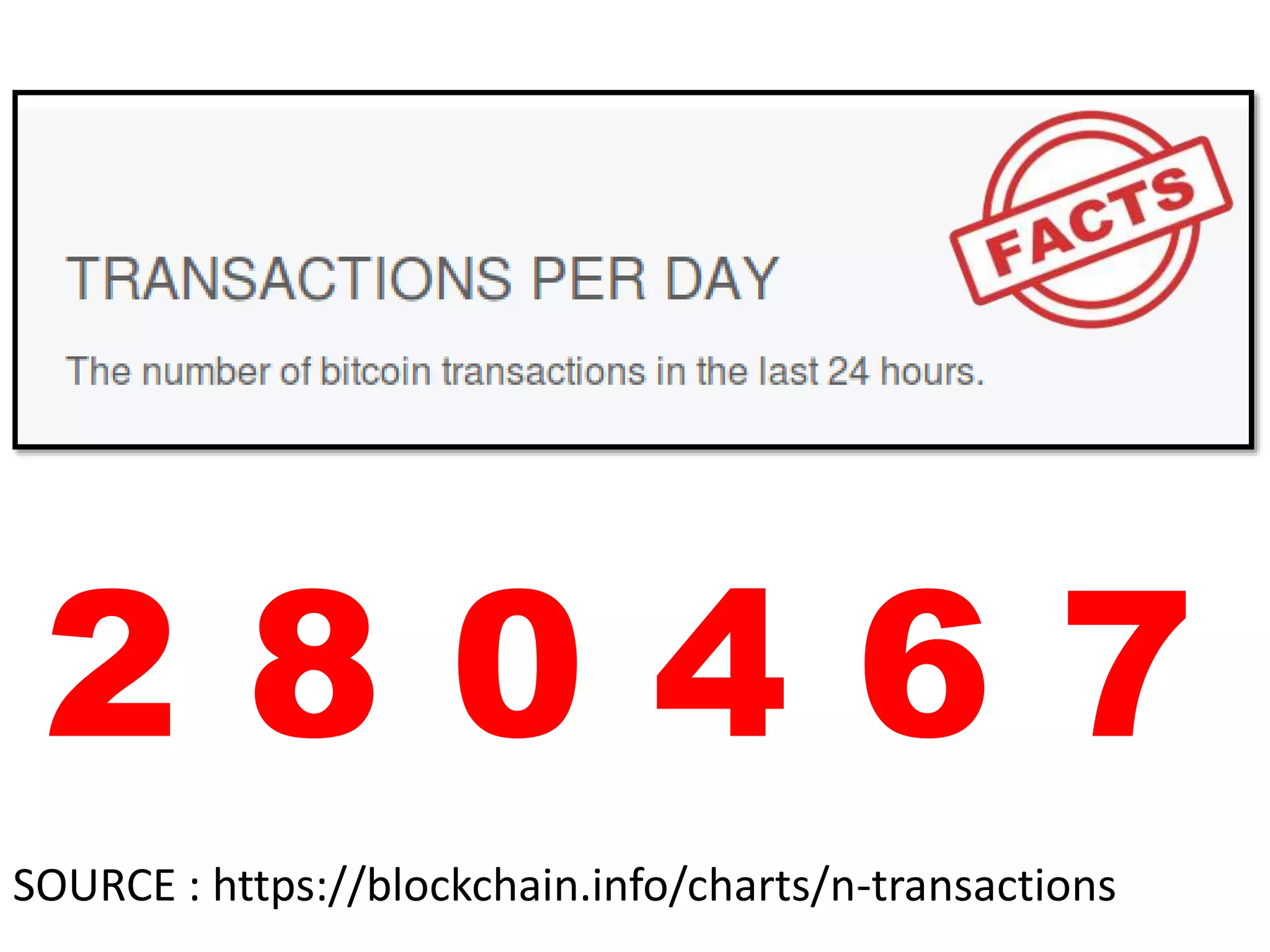
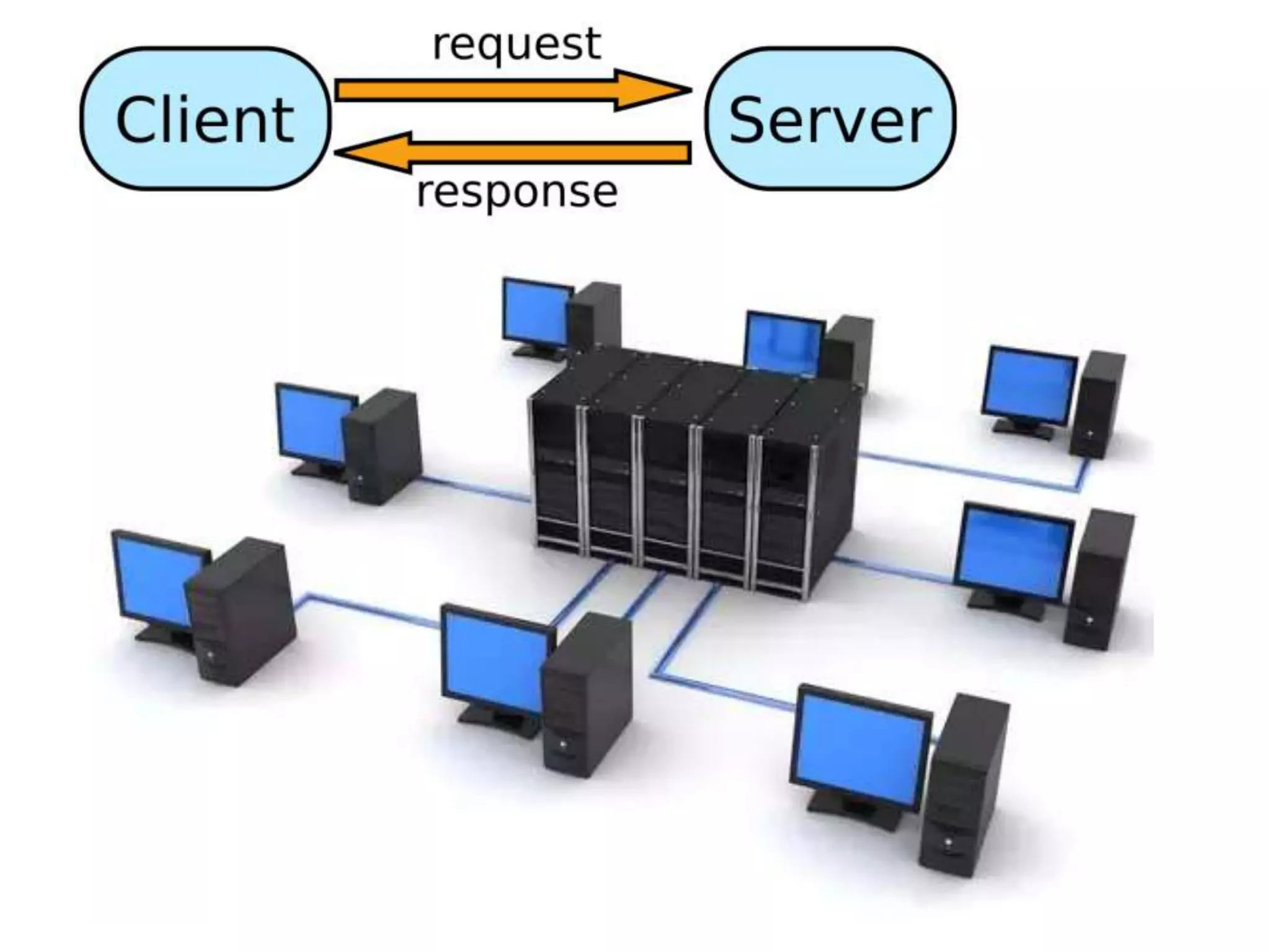
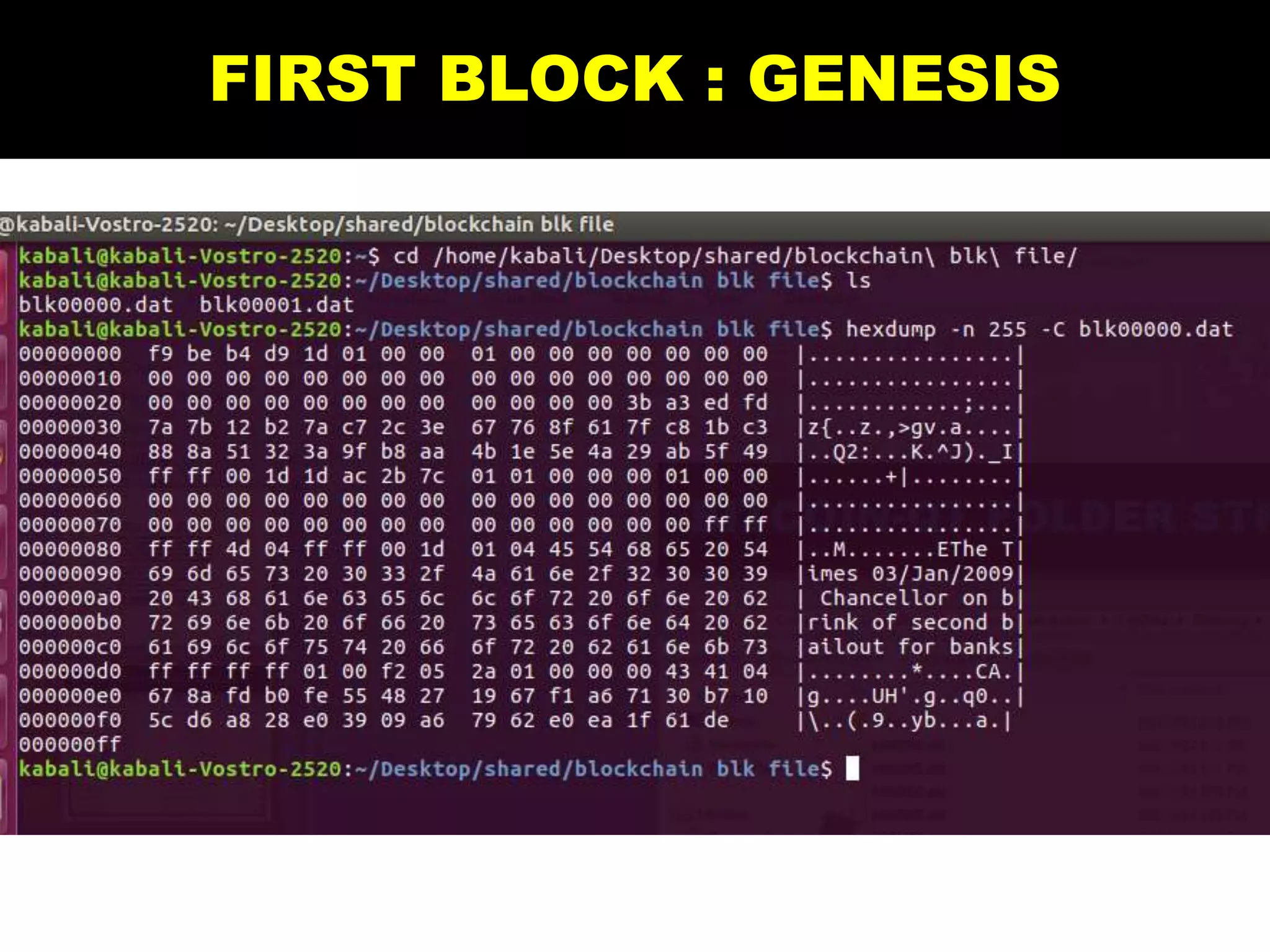
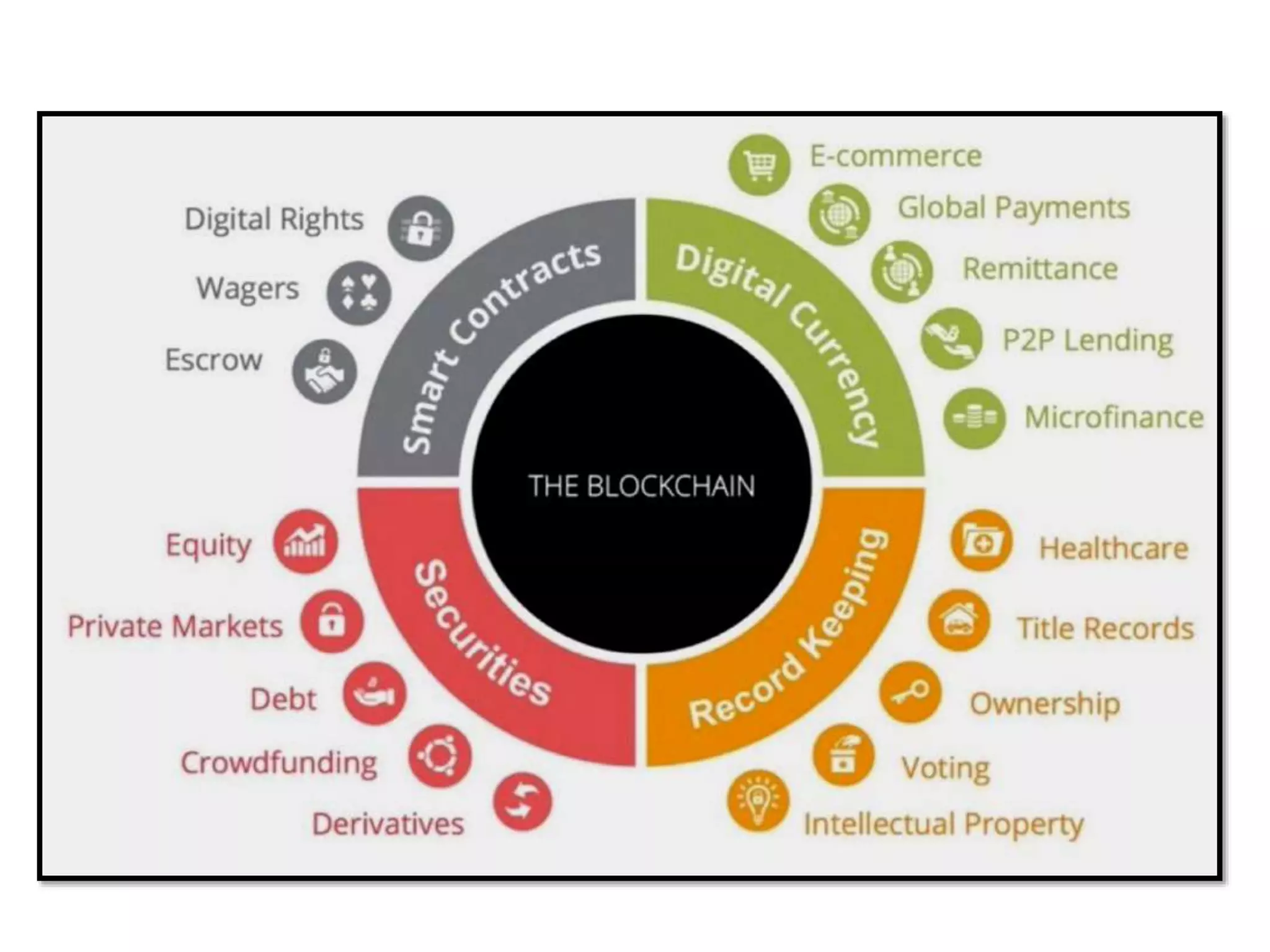
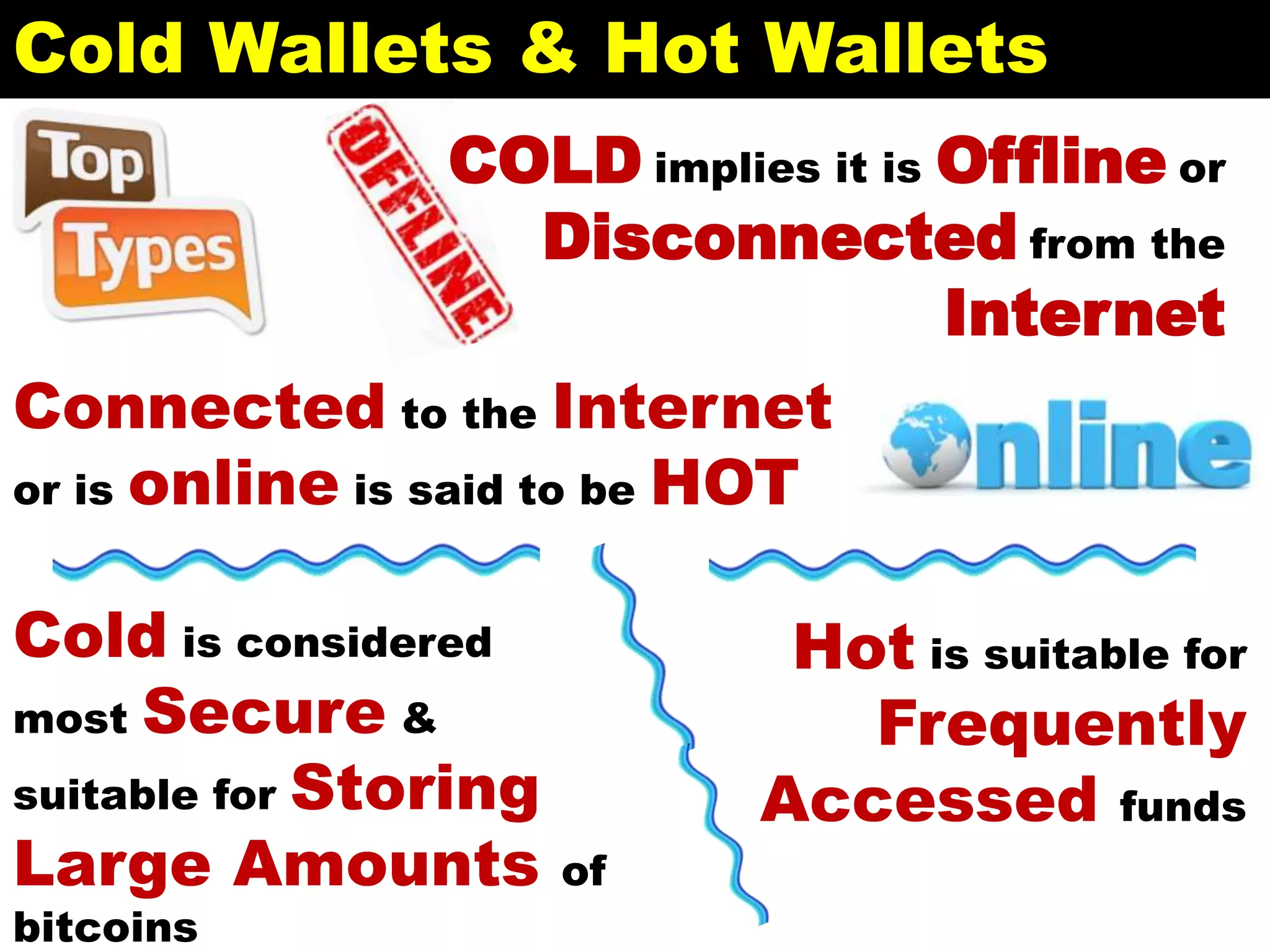
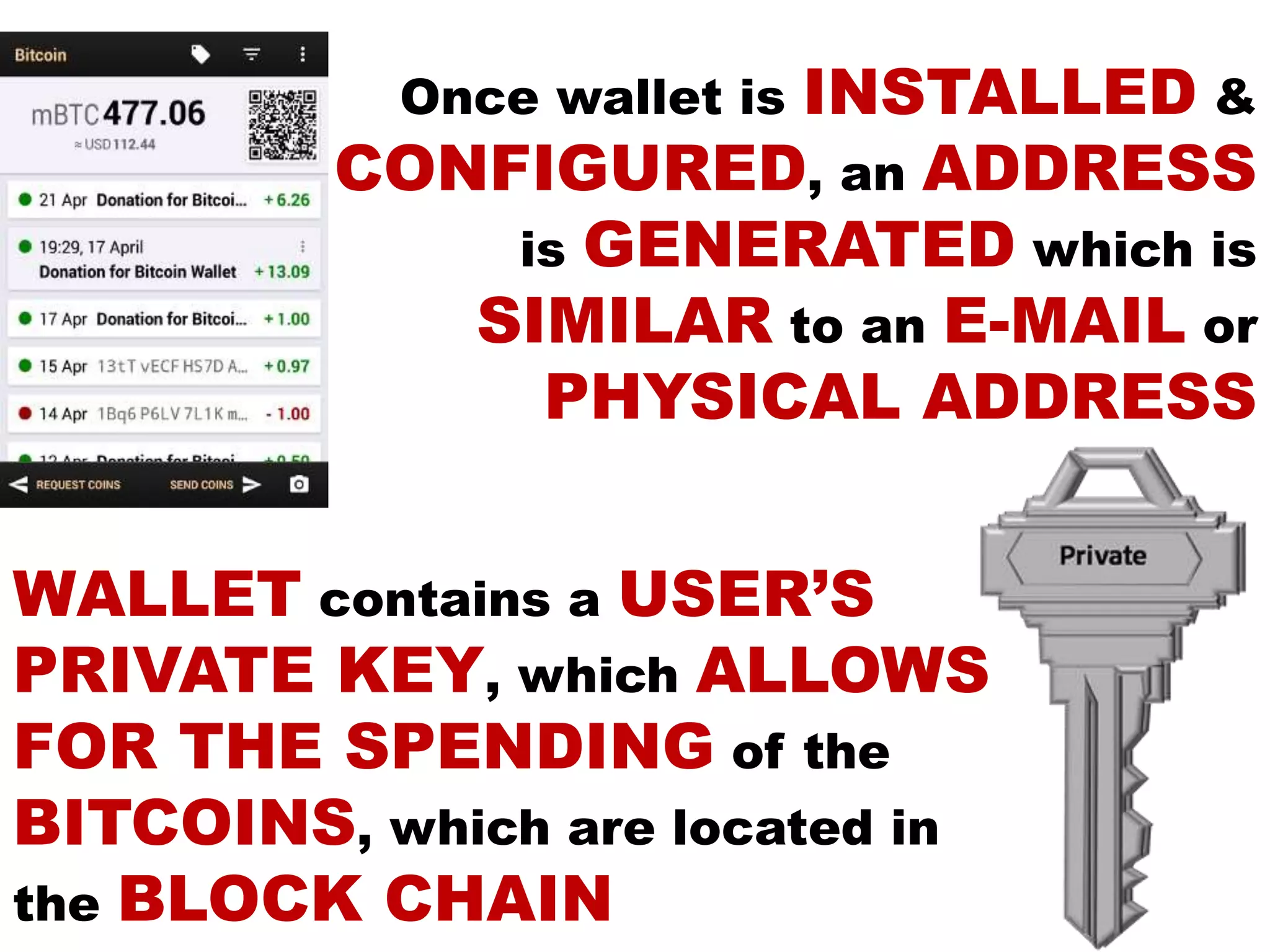
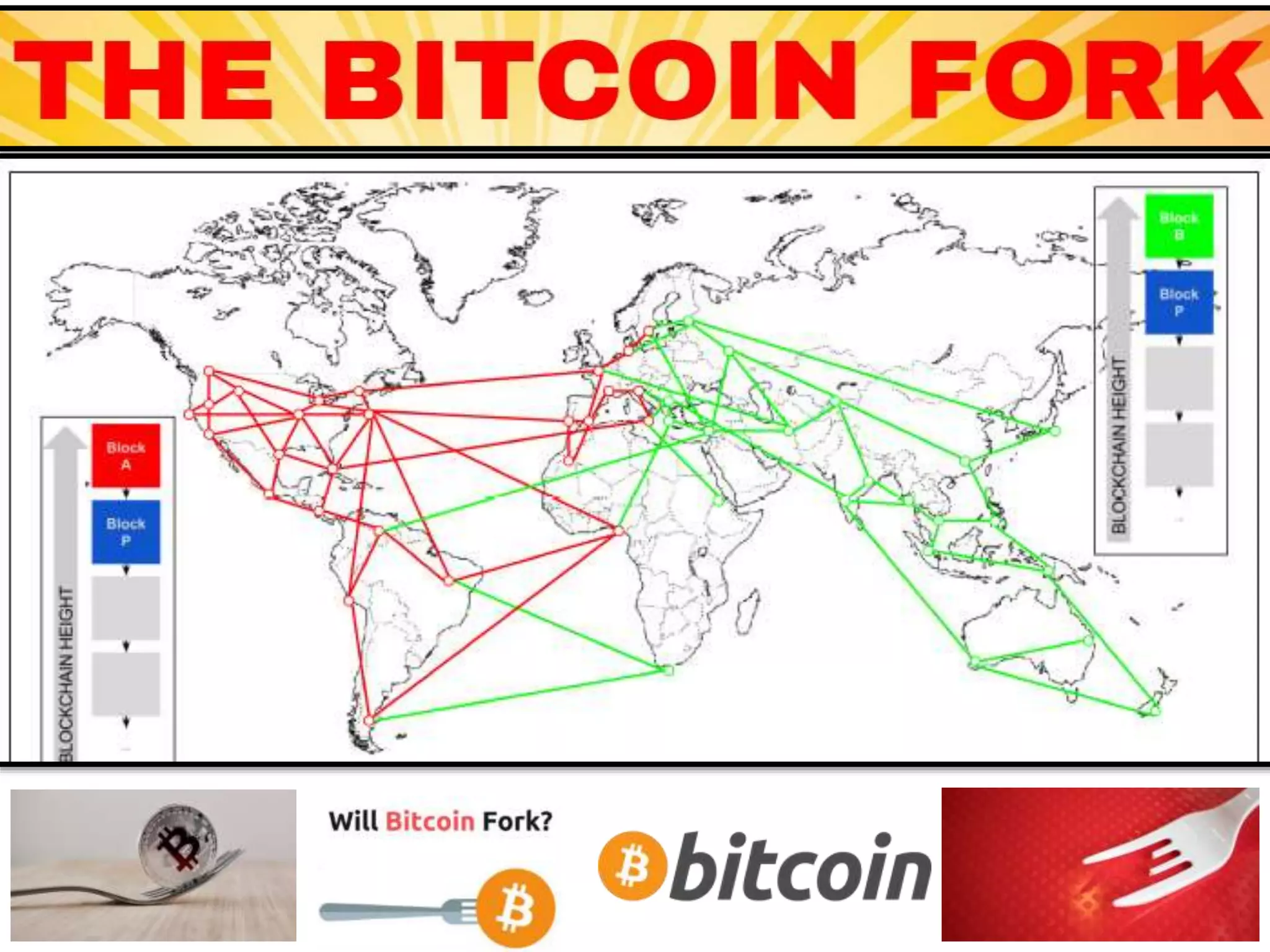
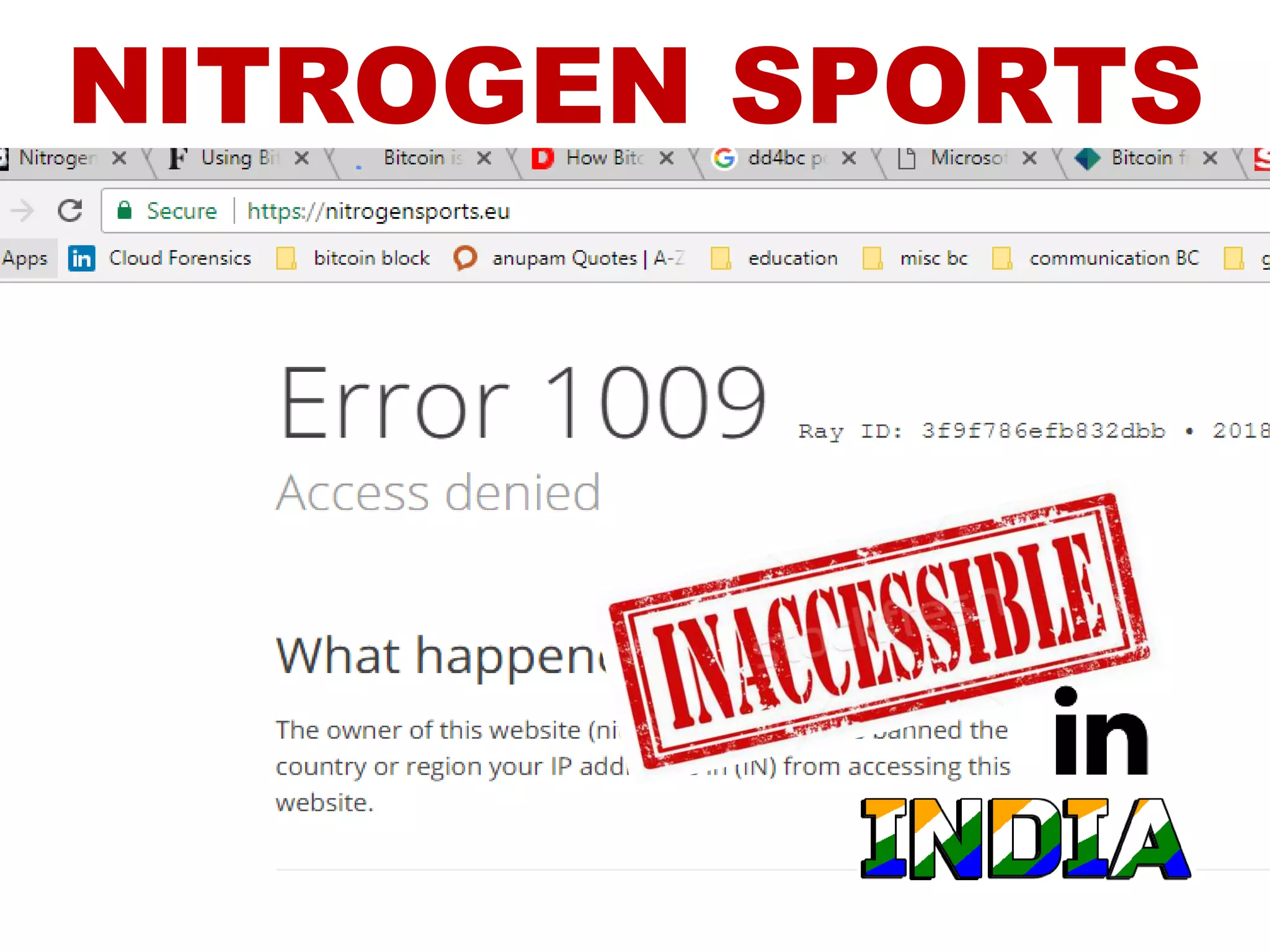
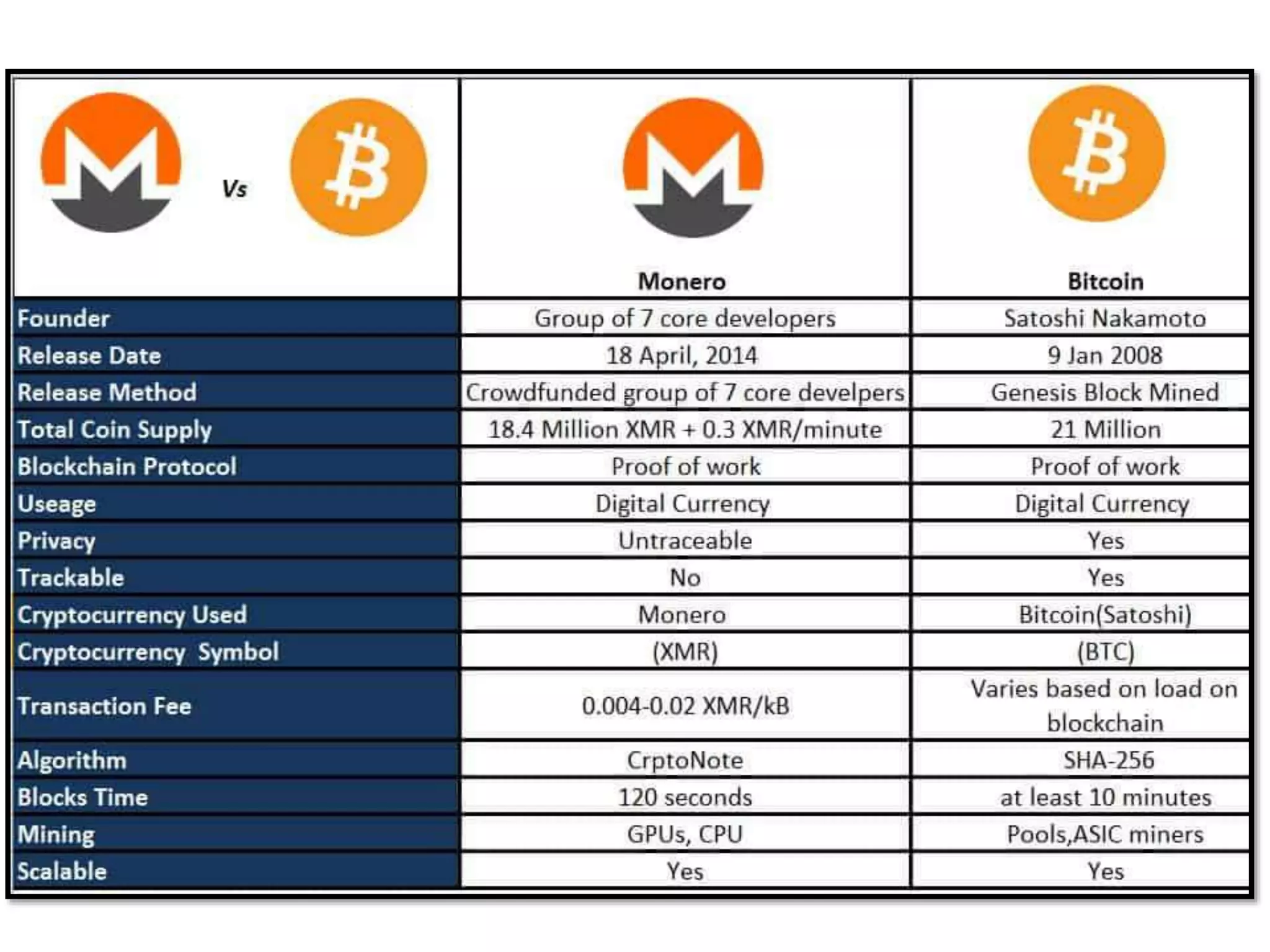
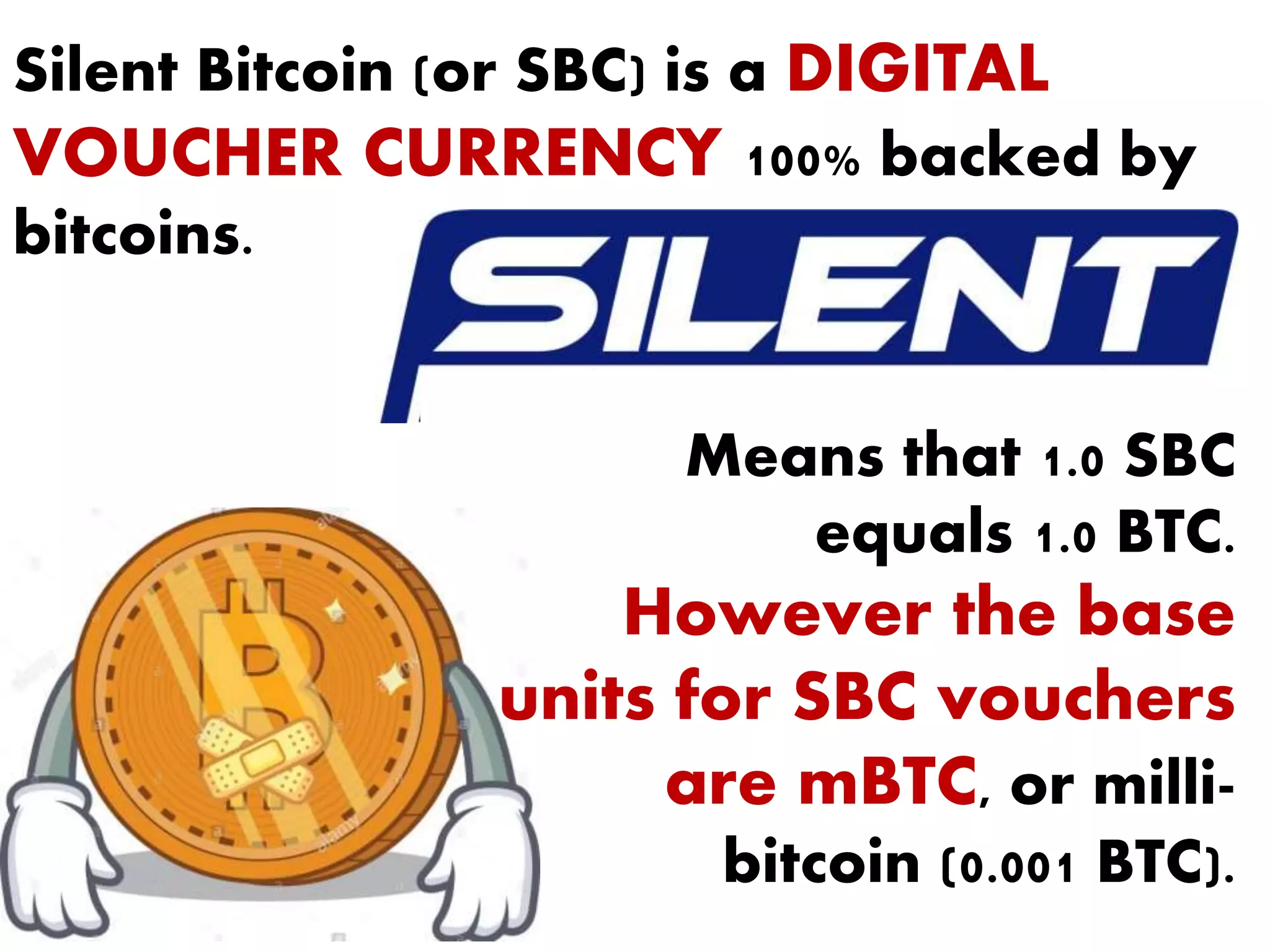
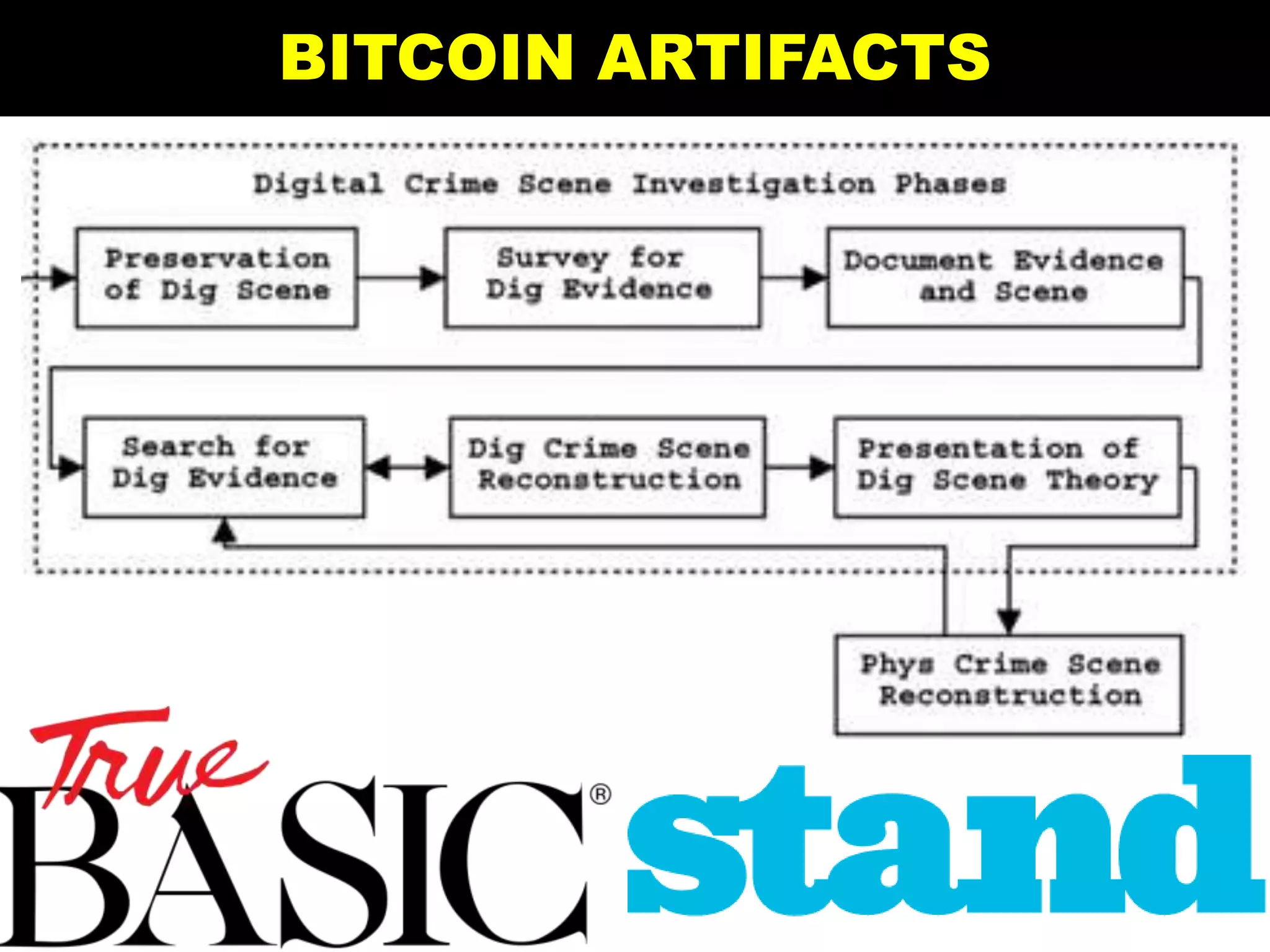
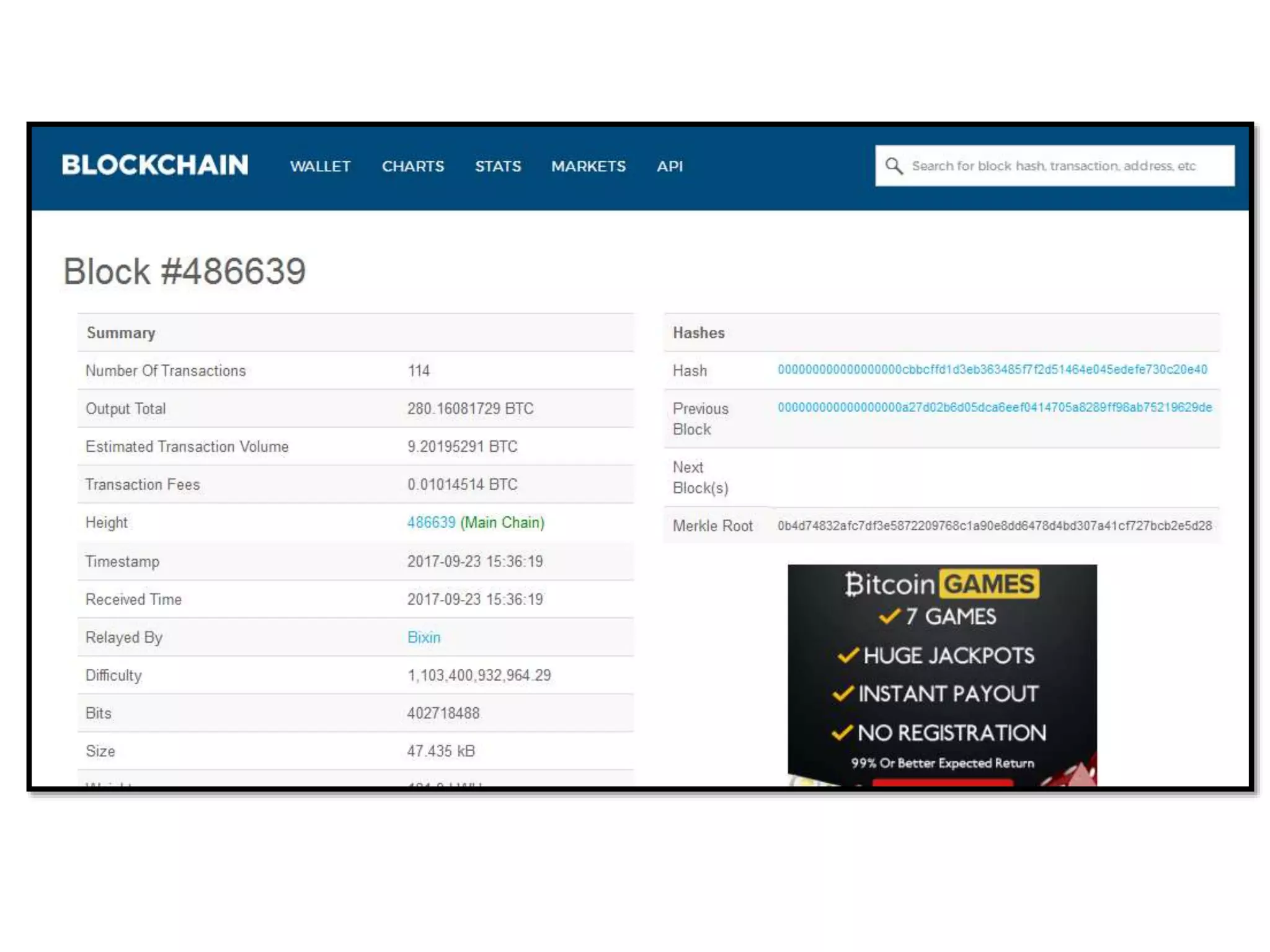
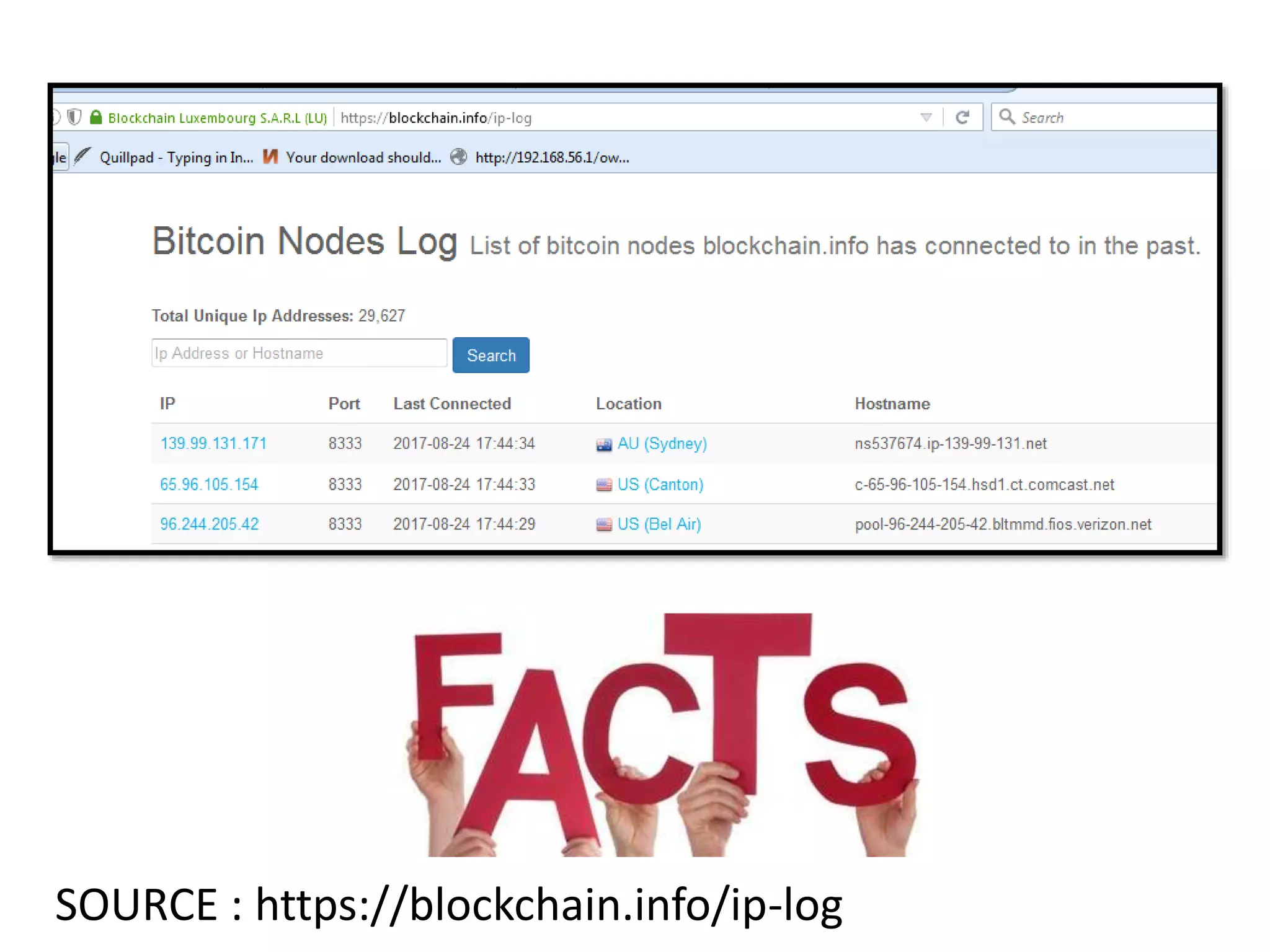
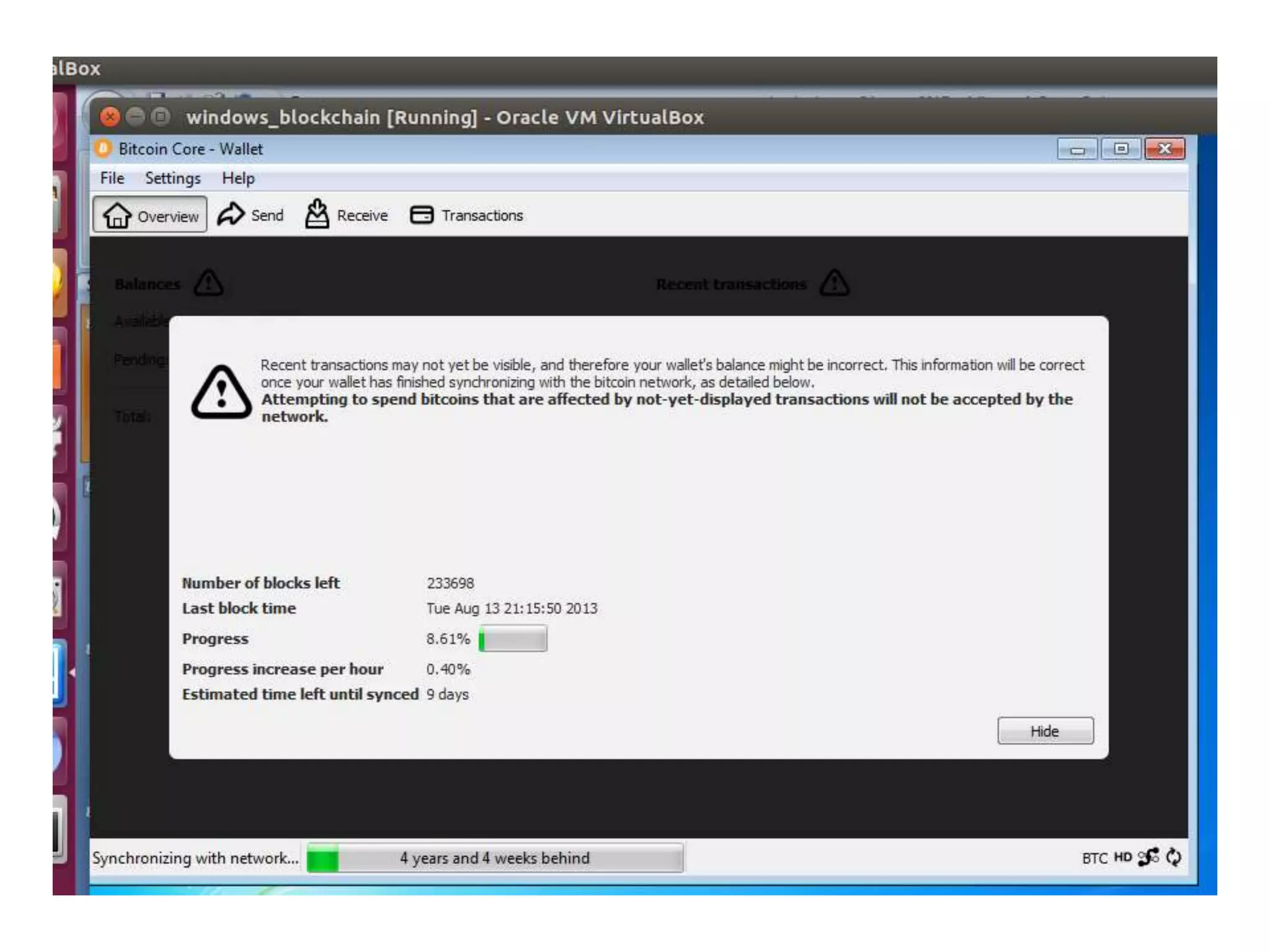
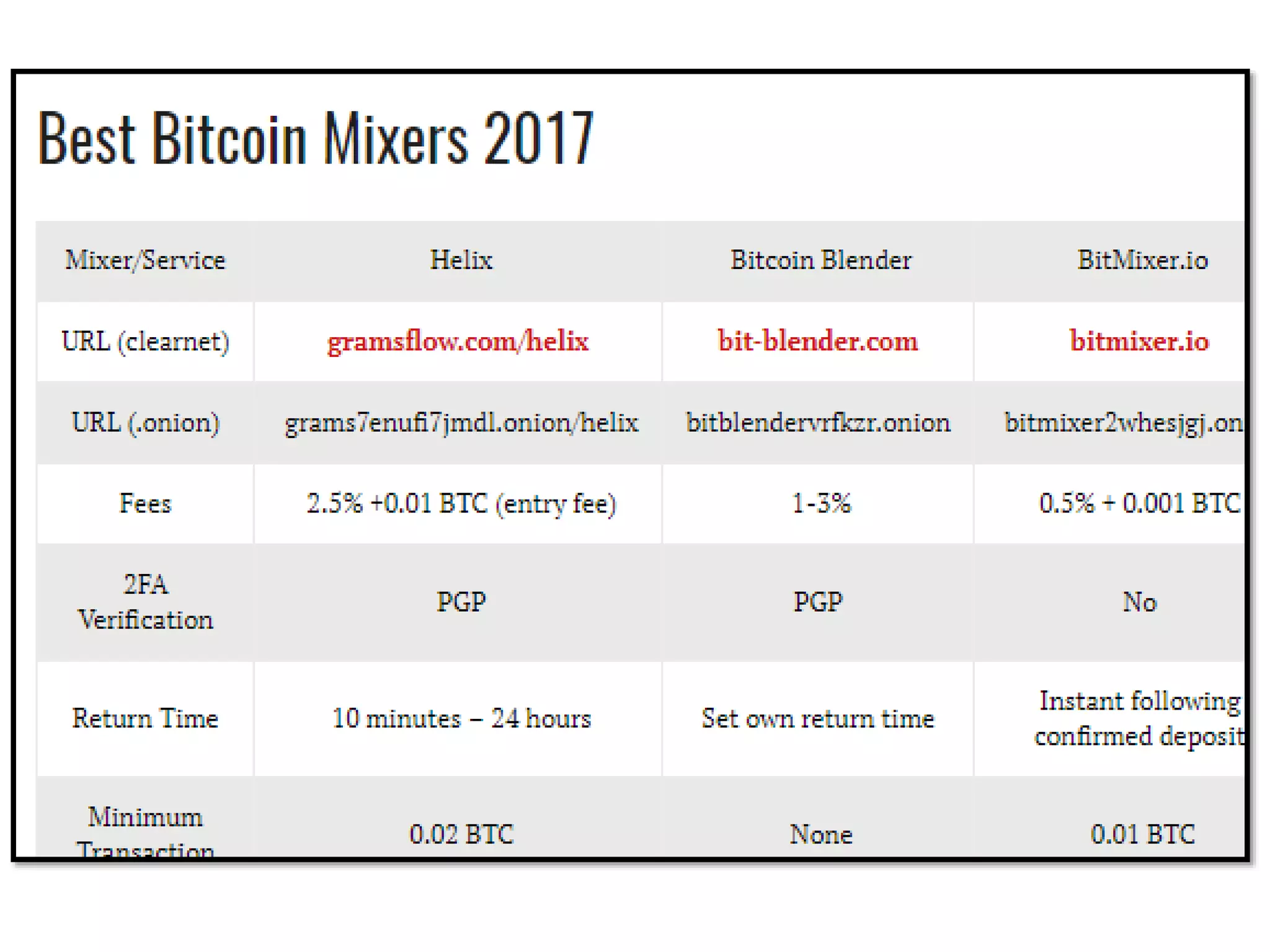
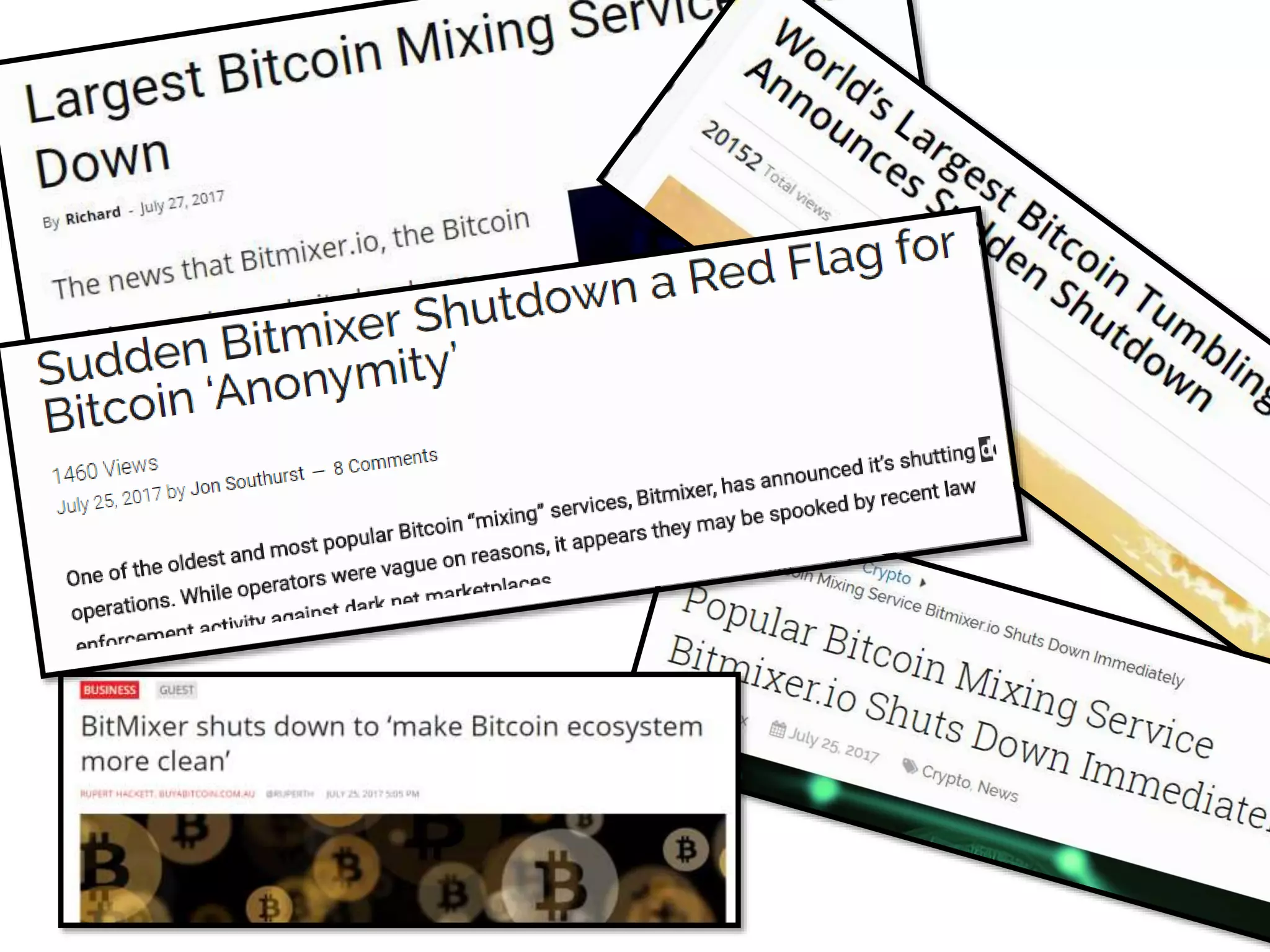
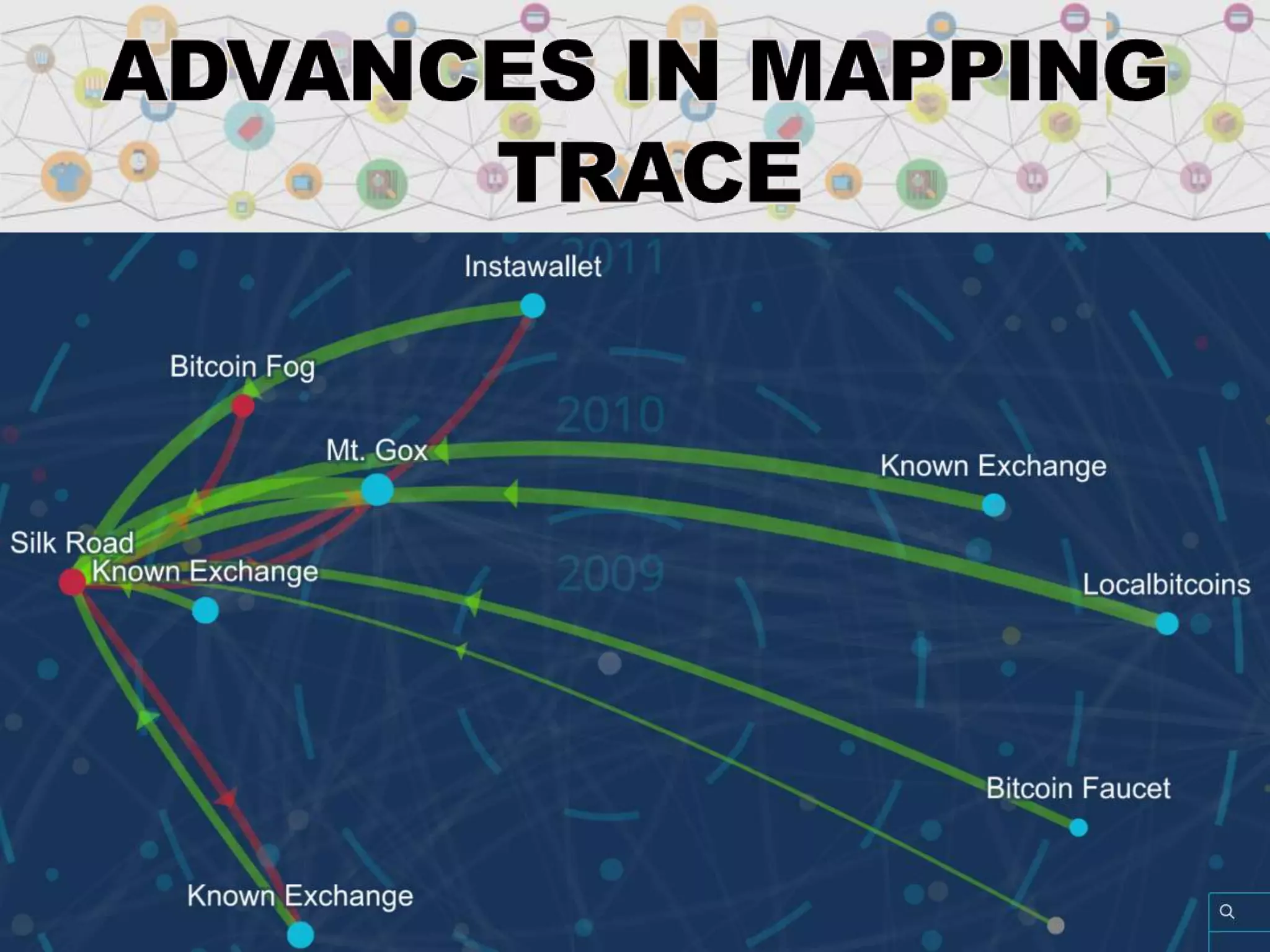
The document is a presentation discussing the technical aspects of Bitcoin and blockchain technology, including its decentralized nature, mining processes, and wallet types. It highlights important concepts like proof of work, transaction anonymity, and the implications of cryptocurrency on financial systems and investigations. The content is presented by Anupam Tiwari and emphasizes the significance of understanding blockchain for both users and investigators.