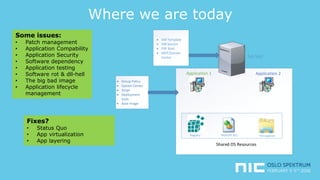
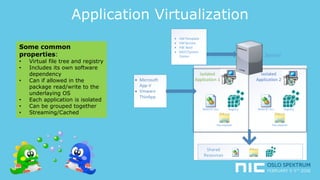
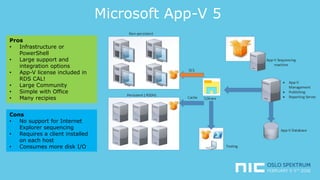
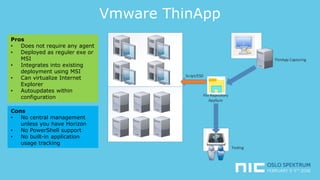
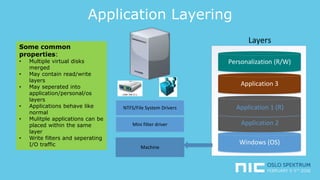
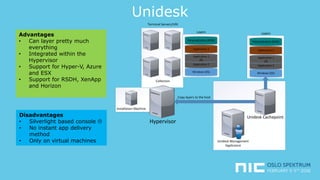
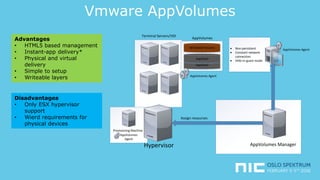
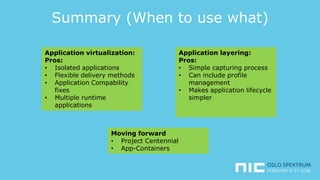
The document provides an overview of application virtualization and application layering, highlighting their respective advantages and disadvantages. It discusses key technologies like Microsoft App-V, VMware ThinApp, Unidesk, Citrix AppDisks, and VMware AppVols, outlining their features and suitability for different use cases. The presentation also covers current challenges in application management and concludes with guidelines on when to use each approach.