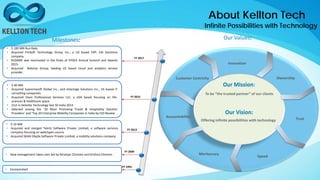
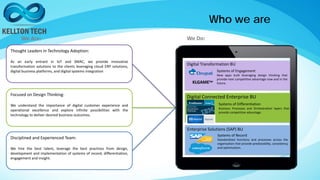
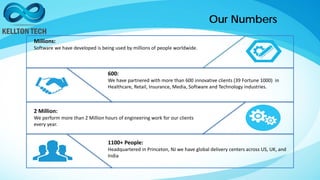
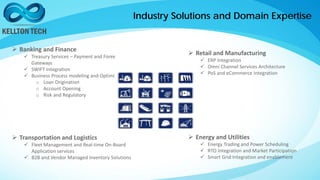
Kellton Tech Solutions, Inc. specializes in integrating API security using the OAuth2 framework and has a diverse portfolio of technology services, including digital transformation and enterprise solutions. The company has expanded significantly through acquisitions and partnerships, achieving a $100 million run rate and working with over 600 clients. They emphasize innovation and operational excellence, aiming to provide secure, scalable, and customer-centric solutions across various industries.