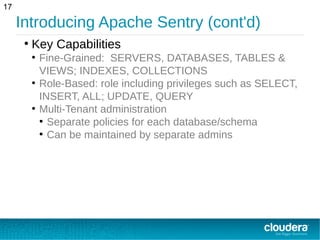
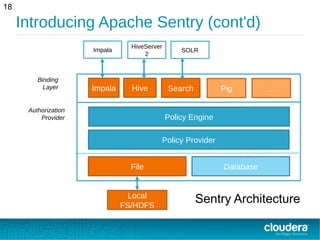
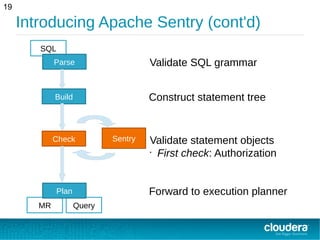
This document provides an overview of Apache Sentry, an open source authorization module for Hadoop. It discusses how Sentry provides fine-grained, role-based authorization across Hadoop components like Hive, Impala and Solr to address the fragmented authorization in Hadoop. Sentry stores authorization policies that map users and groups to roles with privileges for resources like databases, tables and collections. It evaluates rules to determine access for a user based on their group memberships and role privileges.













![Introducing Apache Sentry (cont'd)
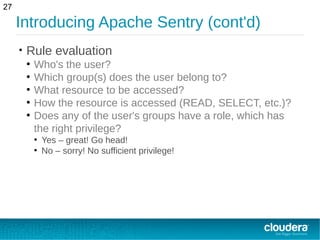
• Roles
●
A collection of privileges
●
Defined in Sentry policy
●
Example
[roles]
ana_query_role = collection=sentryColl->action=query
ana_update_role = collection=sentryColl->action=update
test_role = collection=testColl->action=update
full_admin_role = collection=*
25](https://image.slidesharecdn.com/bigdatagurus-june2014-apachesentry-final-140814124744-phpapp02-151112231543-lva1-app6892/85/Apache-Sentry-for-Hadoop-security-25-320.jpg)
![Introducing Apache Sentry (cont'd)
• (Group, Role) mapping
●
Defined in policy
●
One-to-Many
●
Example
[groups]
analyts = ana_query_role, ana_update_role
admins = full_admin_role
testgroup = test_role
hbase = full_admin_role
26](https://image.slidesharecdn.com/bigdatagurus-june2014-apachesentry-final-140814124744-phpapp02-151112231543-lva1-app6892/85/Apache-Sentry-for-Hadoop-security-26-320.jpg)