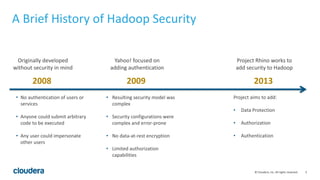
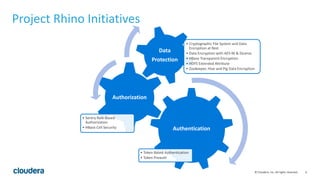
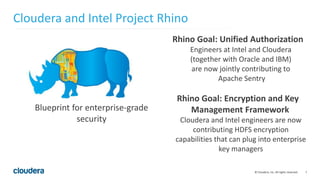
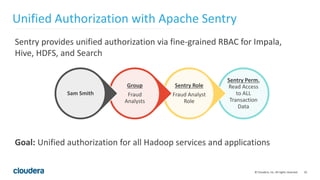
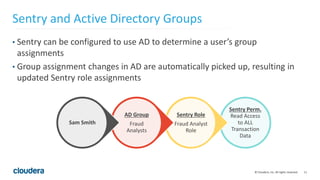
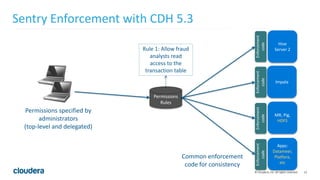
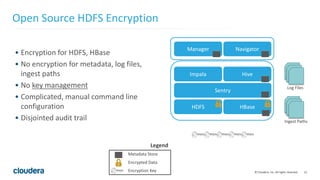
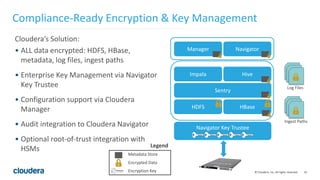
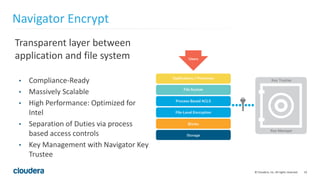
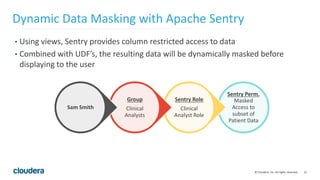
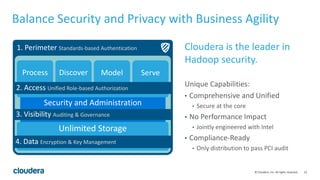
The document discusses Project Rhino, an initiative aimed at enhancing data protection and security for Hadoop by addressing its vulnerabilities such as lack of authentication and encryption. It outlines features like unified authorization through Apache Sentry, encryption for HDFS and HBase, and key management via Navigator Key Trustee, which together address compliance needs and improve security. Cloudera and Intel emphasize the importance of these security measures in safeguarding sensitive data within Hadoop ecosystems.