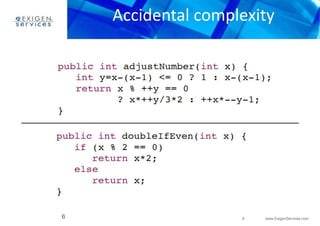
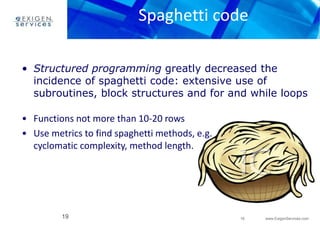
This document discusses various programming anti-patterns organized into three sections: programming anti-patterns, methodological anti-patterns, and configuration management anti-patterns. Some of the programming anti-patterns discussed include accidental complexity, blind faith, boat anchor, cargo cult programming, coding by exception, error hiding, hard coding, magic numbers, spaghetti code, and incorrect exceptions usage. Some methodological anti-patterns discussed include copy and paste programming, golden hammer, improbability factor, premature optimization, and premature pessimization.


























![Golden hammer
– look at the problem from different points of view
– choose technology (concept, framework or tool) that better suits
– previous means you have o know at least on more solution to
– There are 191 fundamental software patterns (23 Gamma
Patterns + 17 Buschmann Patterns + 72 Analysis Patterns + 38
CORBA Design Patterns + 42 AntiPatterns)
32 www.ExigenServices.com
• Solution:
to solve the problem
problem (learn it if needed)
– [4] describes 140 antipatterns
32](https://image.slidesharecdn.com/anti-patternspart2-141212045527-conversion-gate02/85/Anti-patterns-part-2-32-320.jpg)












![46 www.ExigenServices.com
Links
Nr. Document Author, Date, Location
[1] Anti-patterns wiki •http://en.wikipedia.org/wiki/Anti-patterns
[2] AnemicDomainModel •http://www.martinfowler.com/bliki/AnemicDomainModel.html
[3] AntiPatterns •http://www.antipatterns.com/briefing/sld001.htm
[4] AntiPatterns catalog •http://c2.com/cgi-bin/wiki?AntiPatternsCatalog
[5] Supported by the Antipattern template •http://c2.com/cgi-bin/wiki?AntiPatternTemplate
[6] AntiPatterns: Refactoring Software,
Architectures, and
Projects in Crisis by William J. Brown
et.al. (Wiley)
[7] AntiPatterns •http://sourcemaking.com/antipatterns
46](https://image.slidesharecdn.com/anti-patternspart2-141212045527-conversion-gate02/85/Anti-patterns-part-2-46-320.jpg)