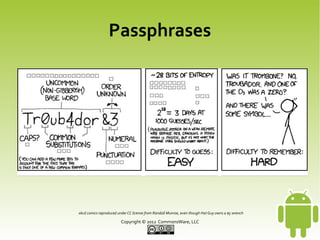
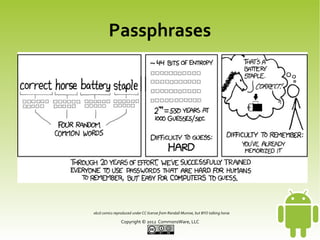
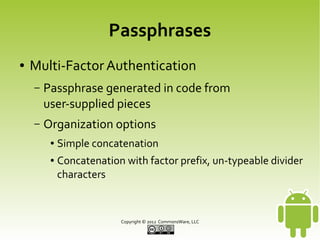
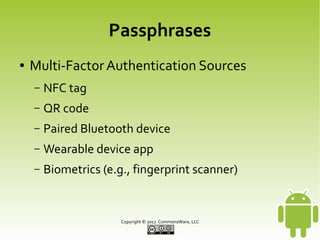
This document discusses securing Android applications by encrypting data. It recommends encrypting data stored locally using SQLCipher, which provides encryption of SQLite databases with AES-256. The document outlines how to integrate SQLCipher by replacing import statements, supplying passphrases, and testing. It also discusses challenges with passphrases and suggests multi-factor authentication by combining user-supplied pieces from different sources like NFC tags or biometrics.