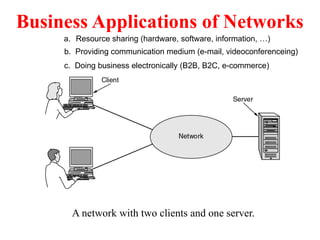
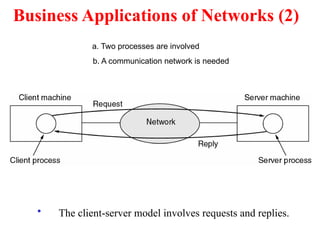
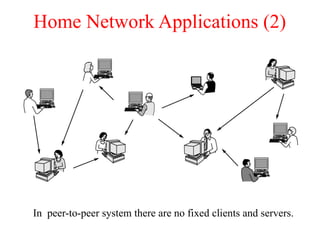
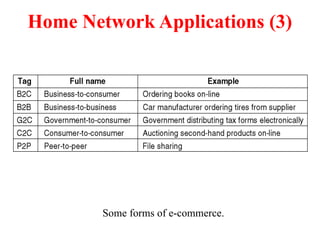
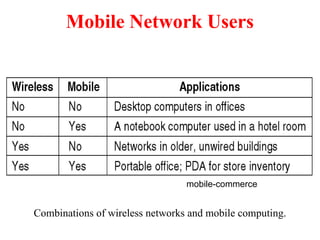
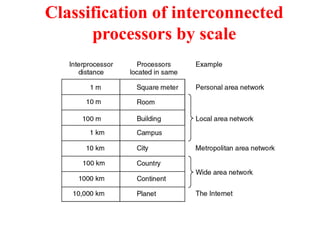
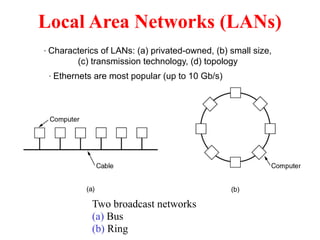
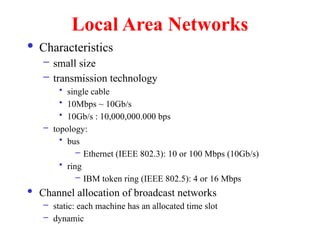
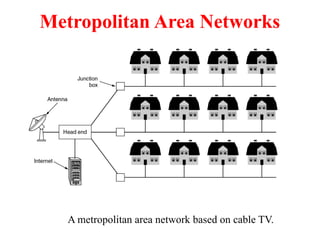
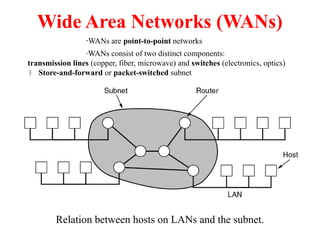
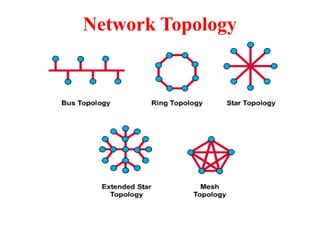
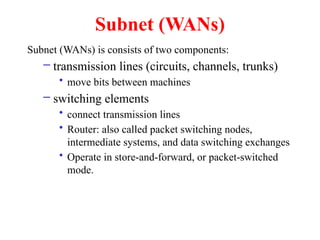
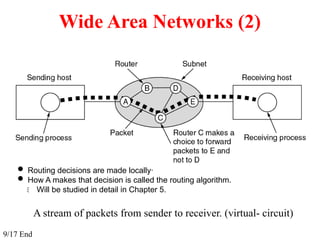
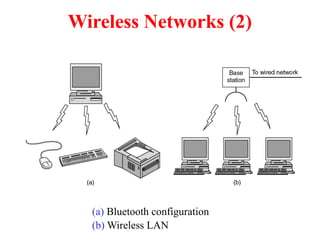
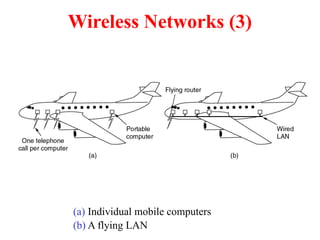
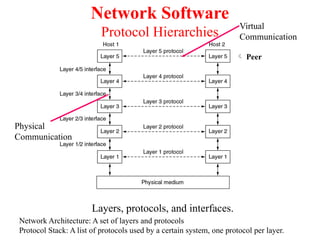
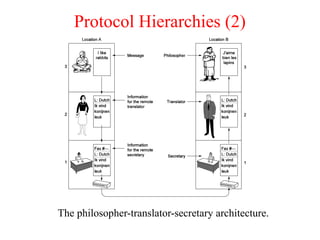
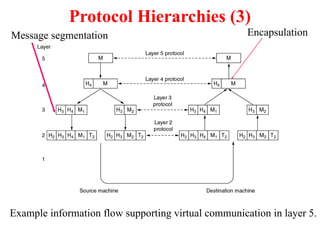
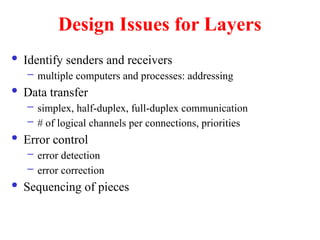
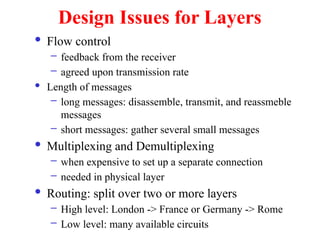
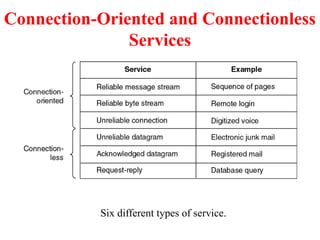
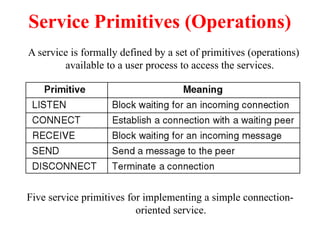
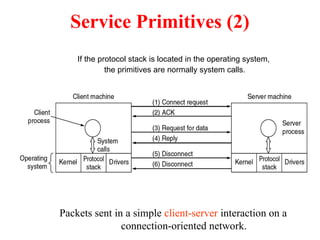
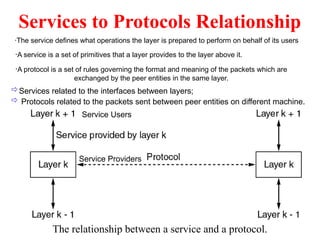
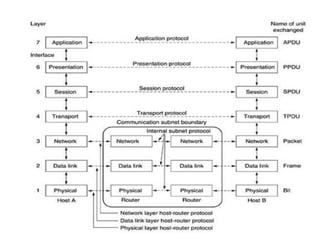
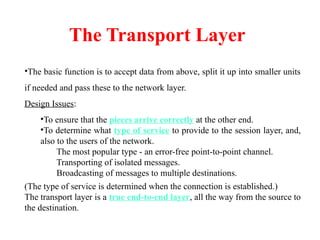
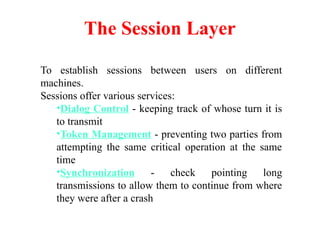
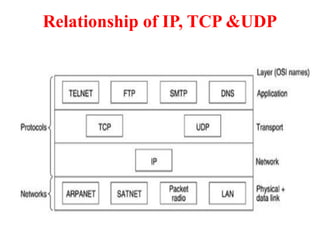
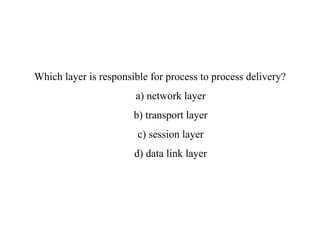
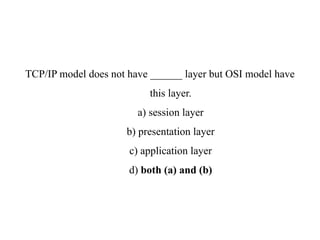
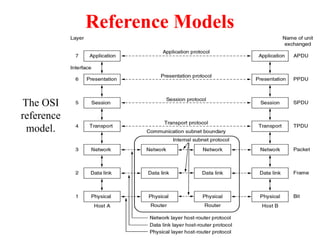
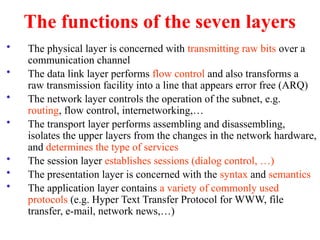
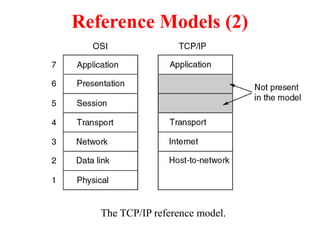
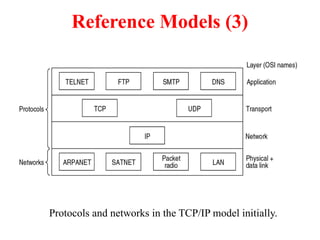
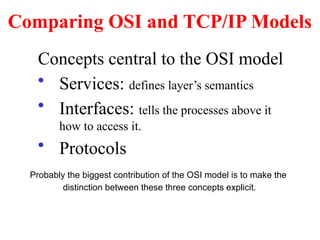
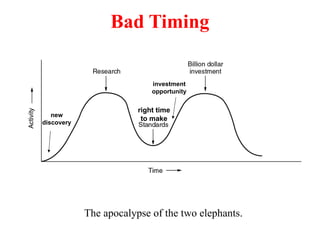
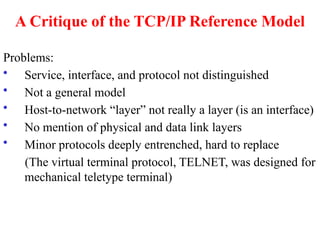
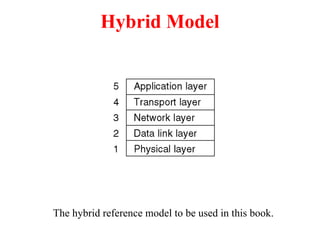
The document provides an overview of computer networks and information security, detailing the evolution of network technology from centralized computing to interconnected systems. It defines computer networks, their components, and various applications in business and home settings while discussing different types of networks, transmission technologies, and protocols, including OSI and TCP/IP models. Additionally, it covers the functionalities and design issues related to various network layers, emphasizing resource sharing, communication, and the role of software in network architecture.