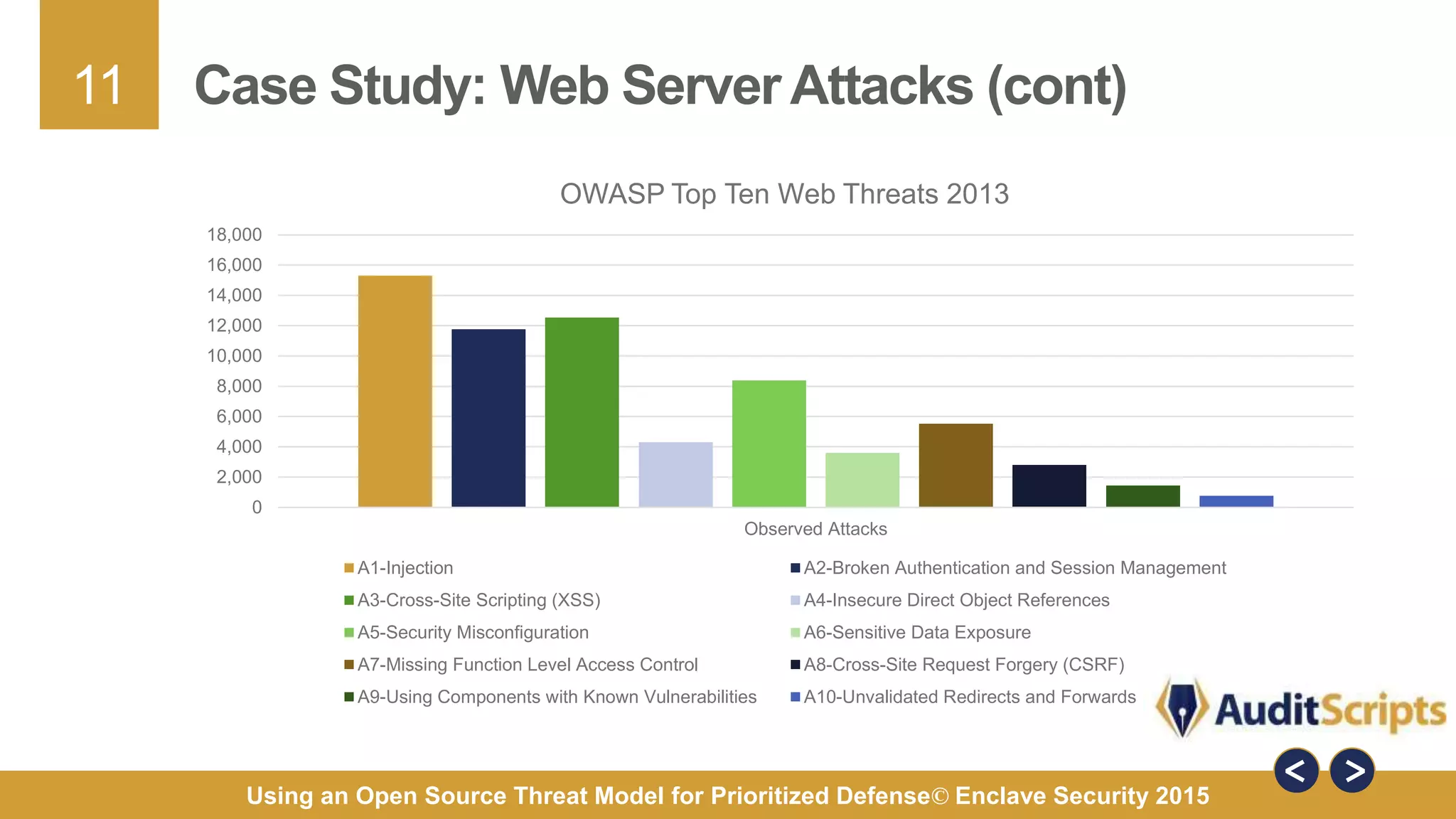
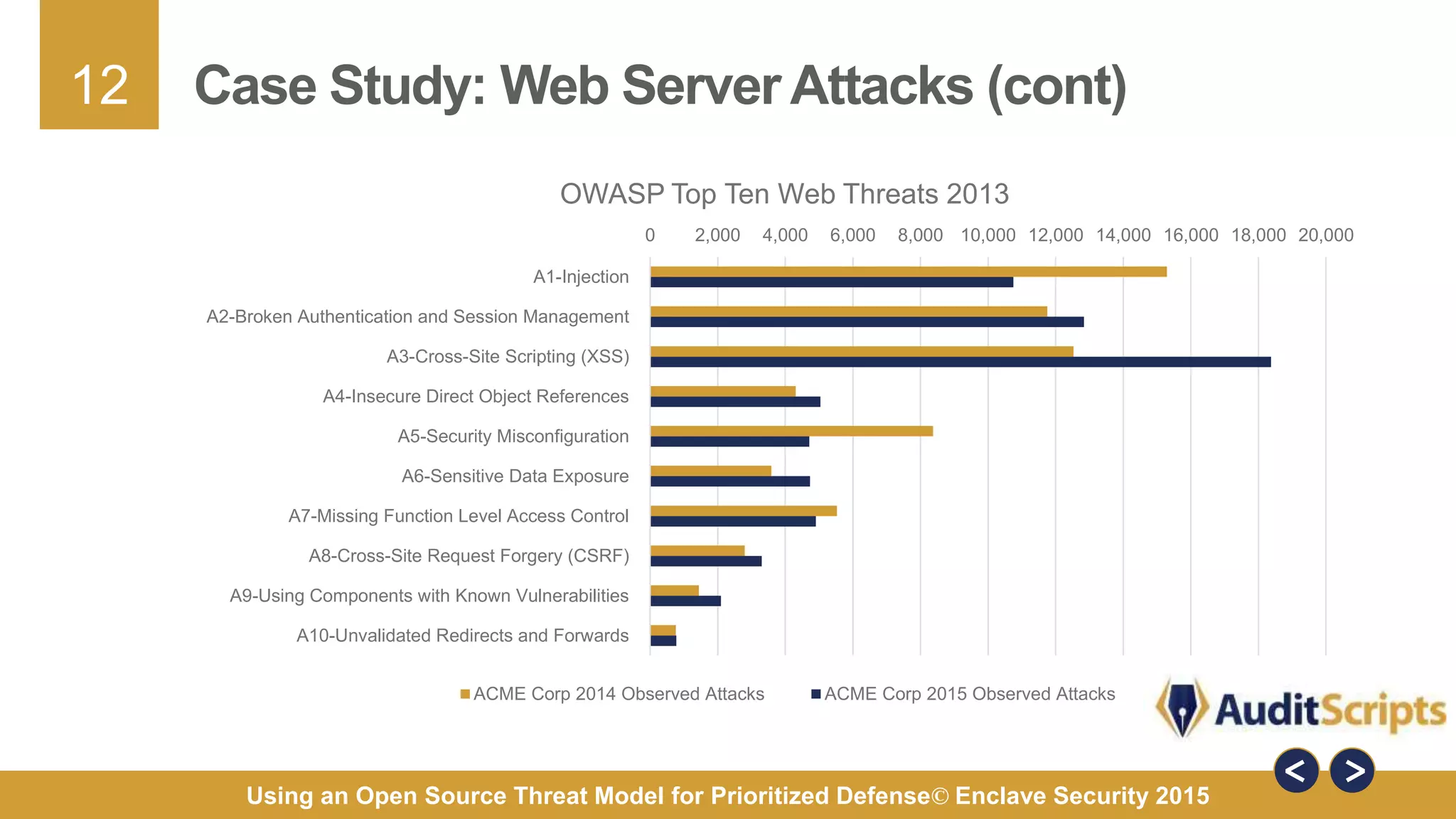
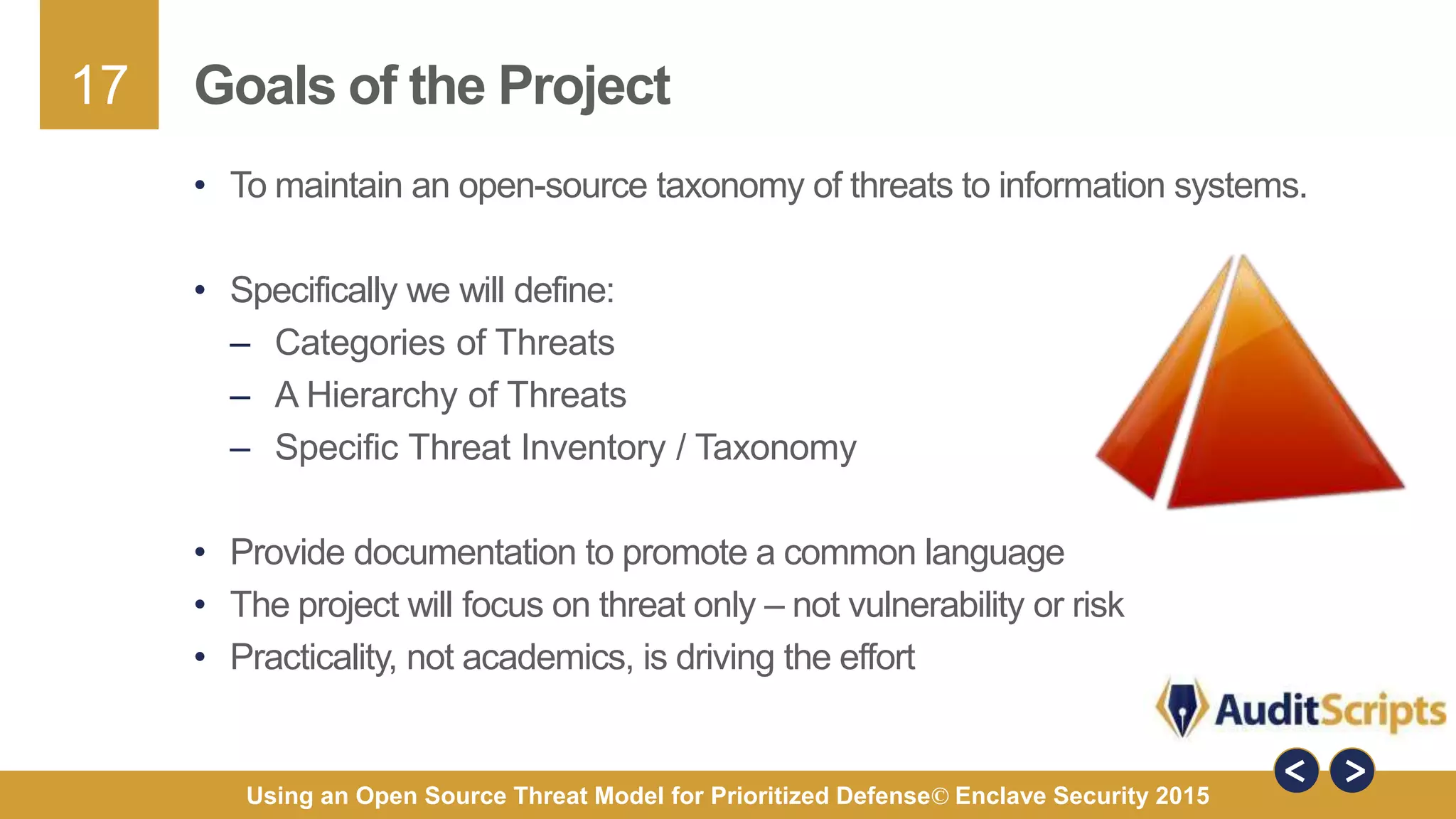
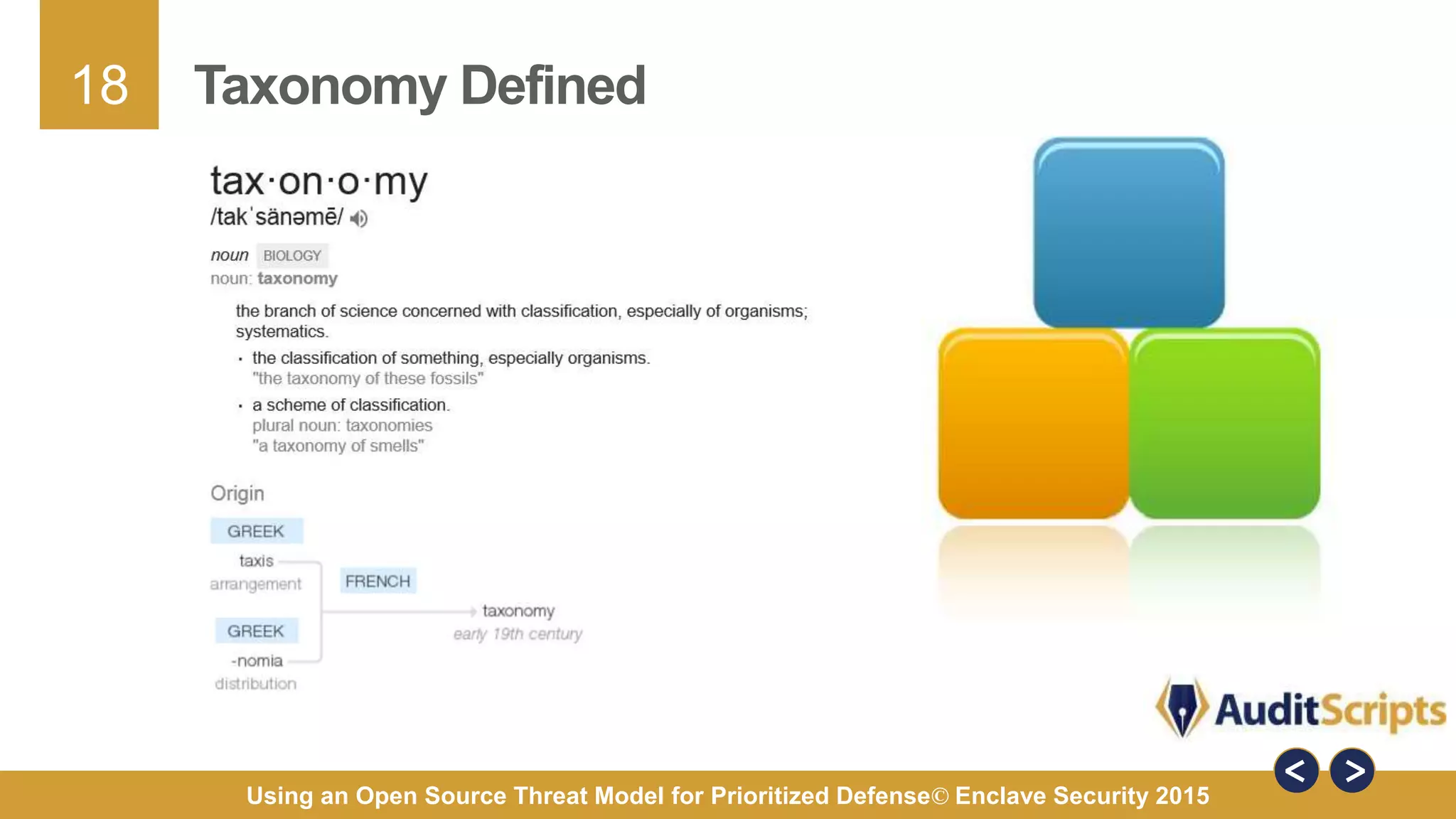
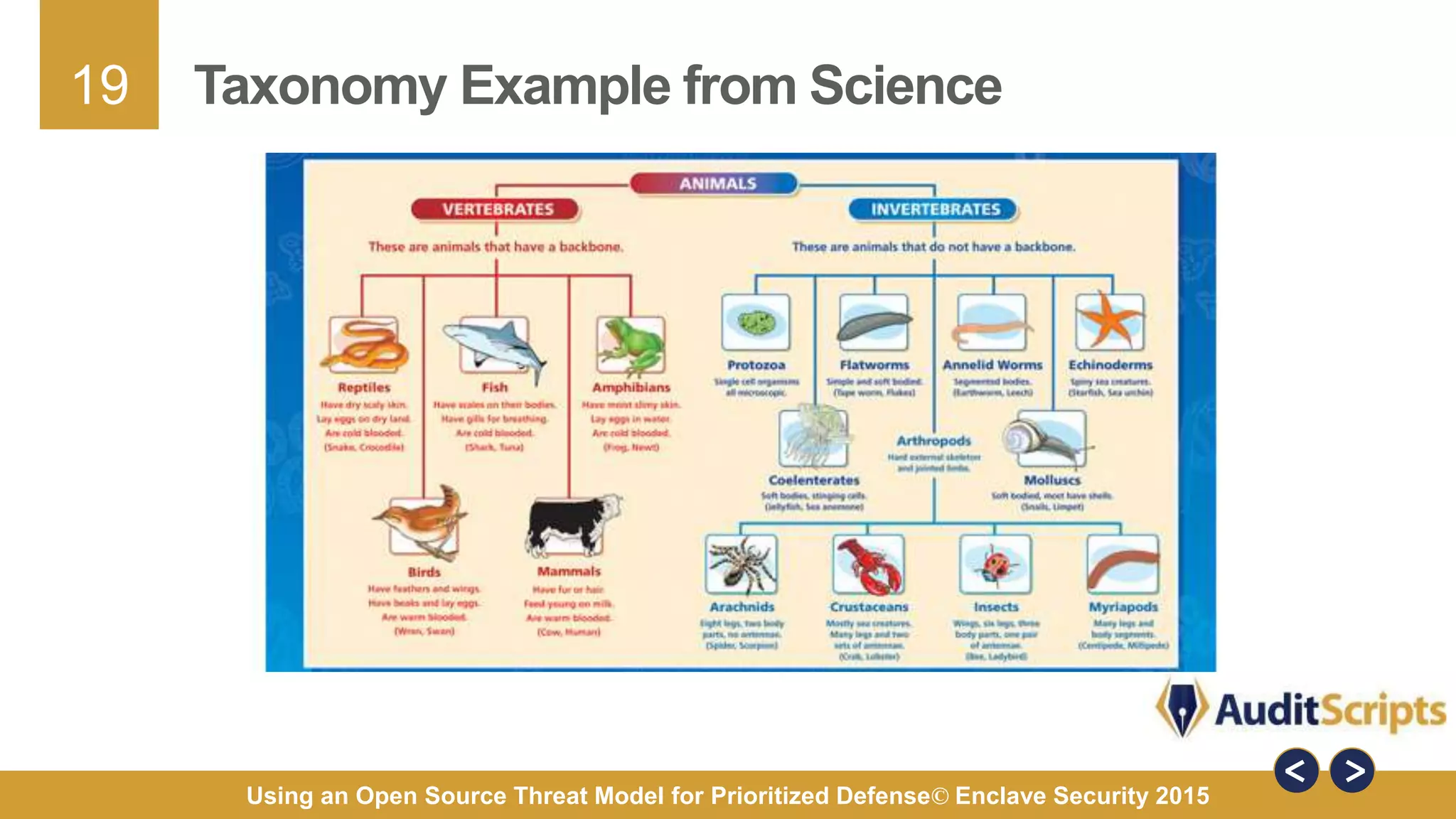
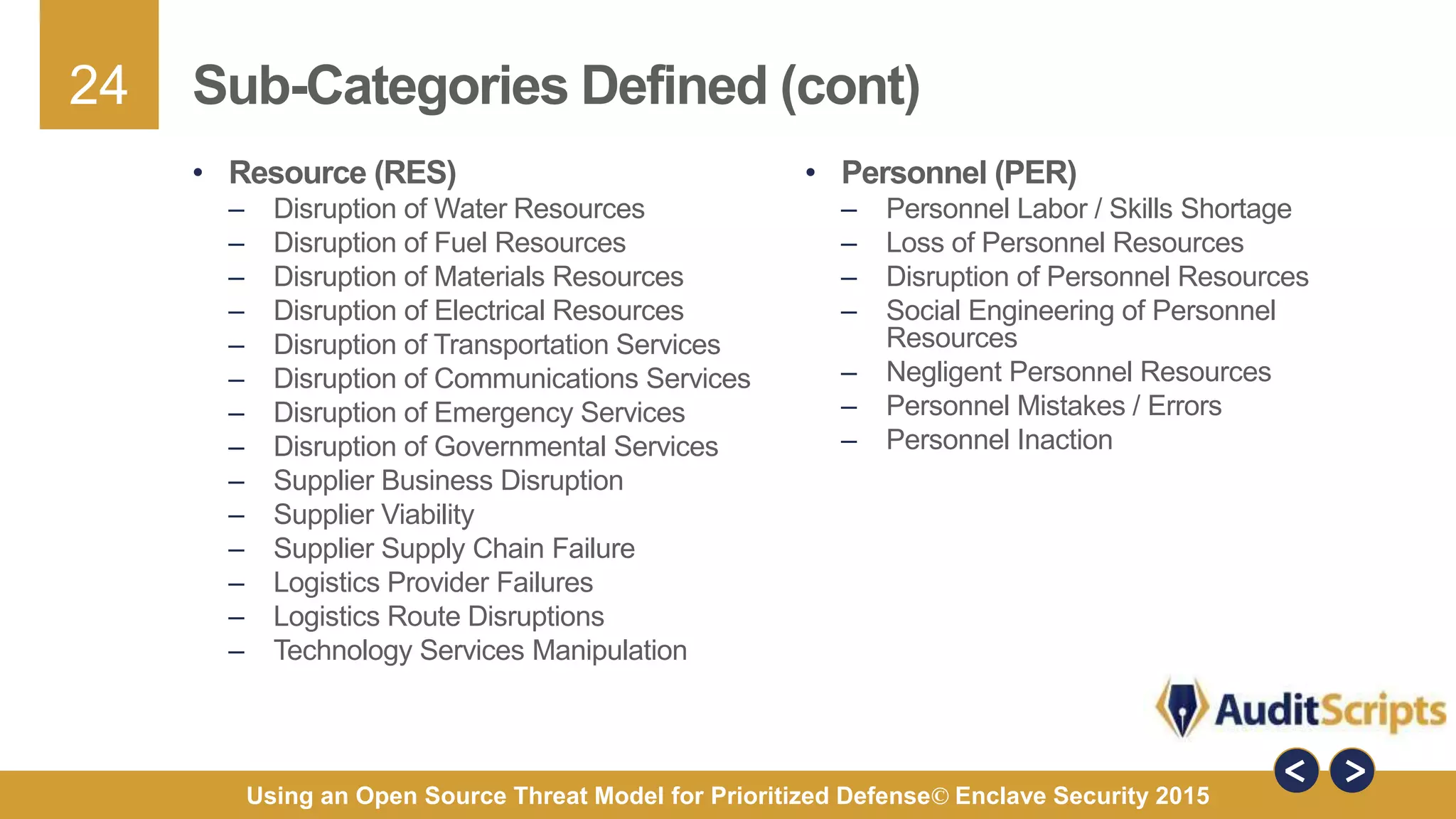
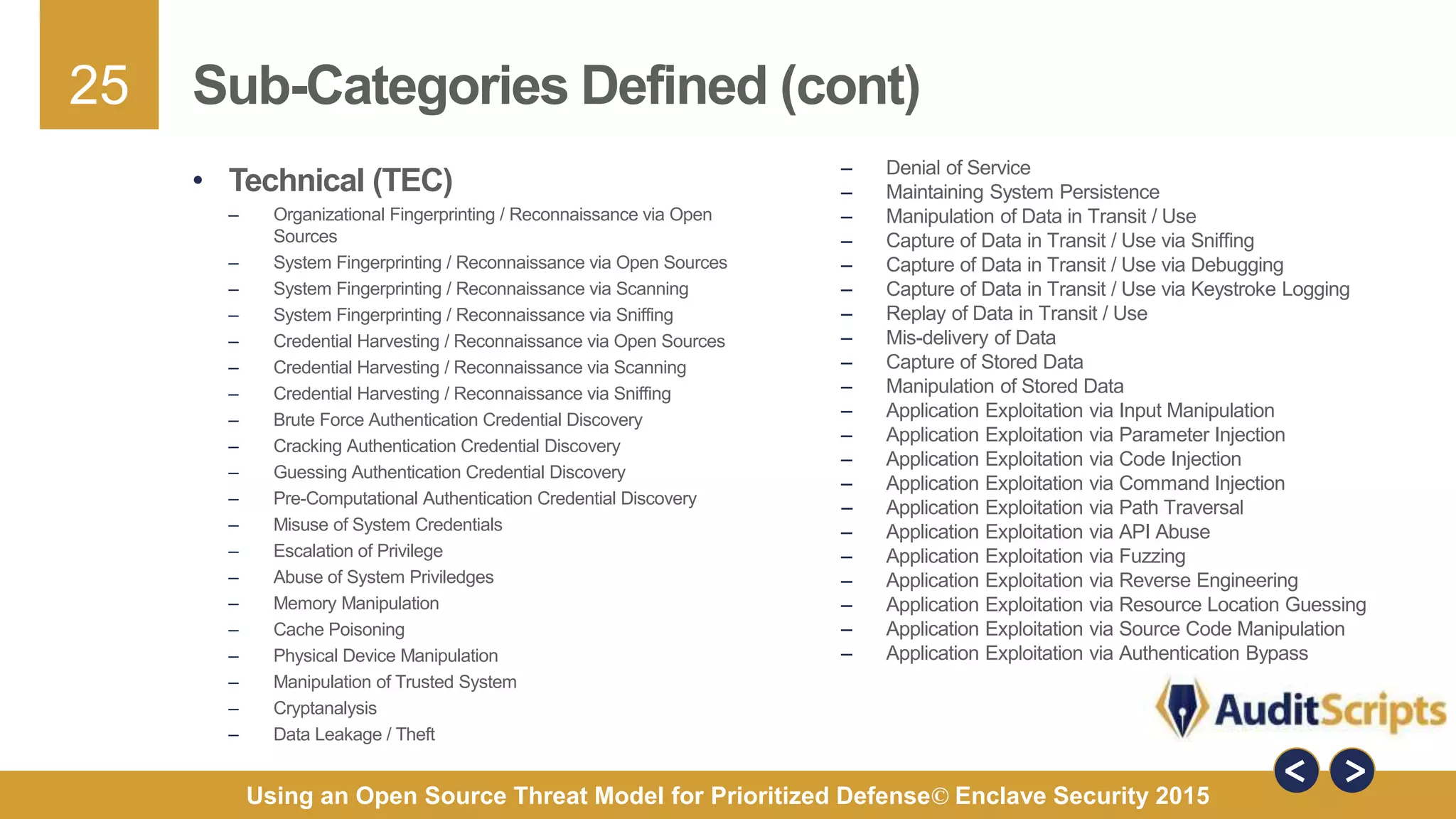
The document discusses using an open source threat model for prioritized defense. It proposes creating a common taxonomy of threats to information systems that defines categories, a hierarchy, and specific threats. This would provide organizations a common language and understanding of threats to help them determine appropriate defenses. The taxonomy would be based on research from industry reports and categorize high-level threats as physical, resource, personnel, or technical, with subcategories defined. The goal is a practical taxonomy maintained by a committee that organizations can reference to identify relevant threats and prioritize controls without having to define threats themselves.