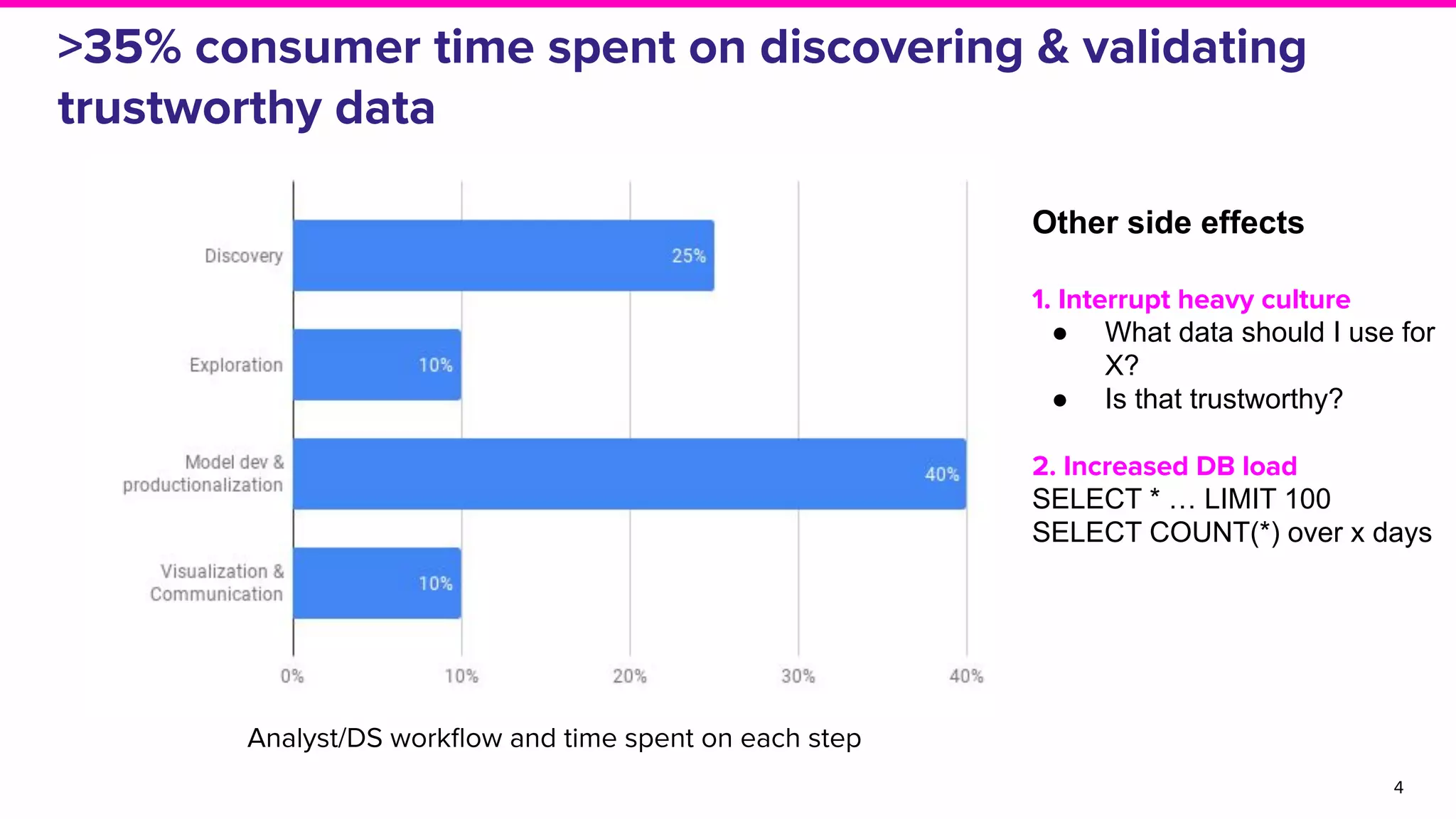
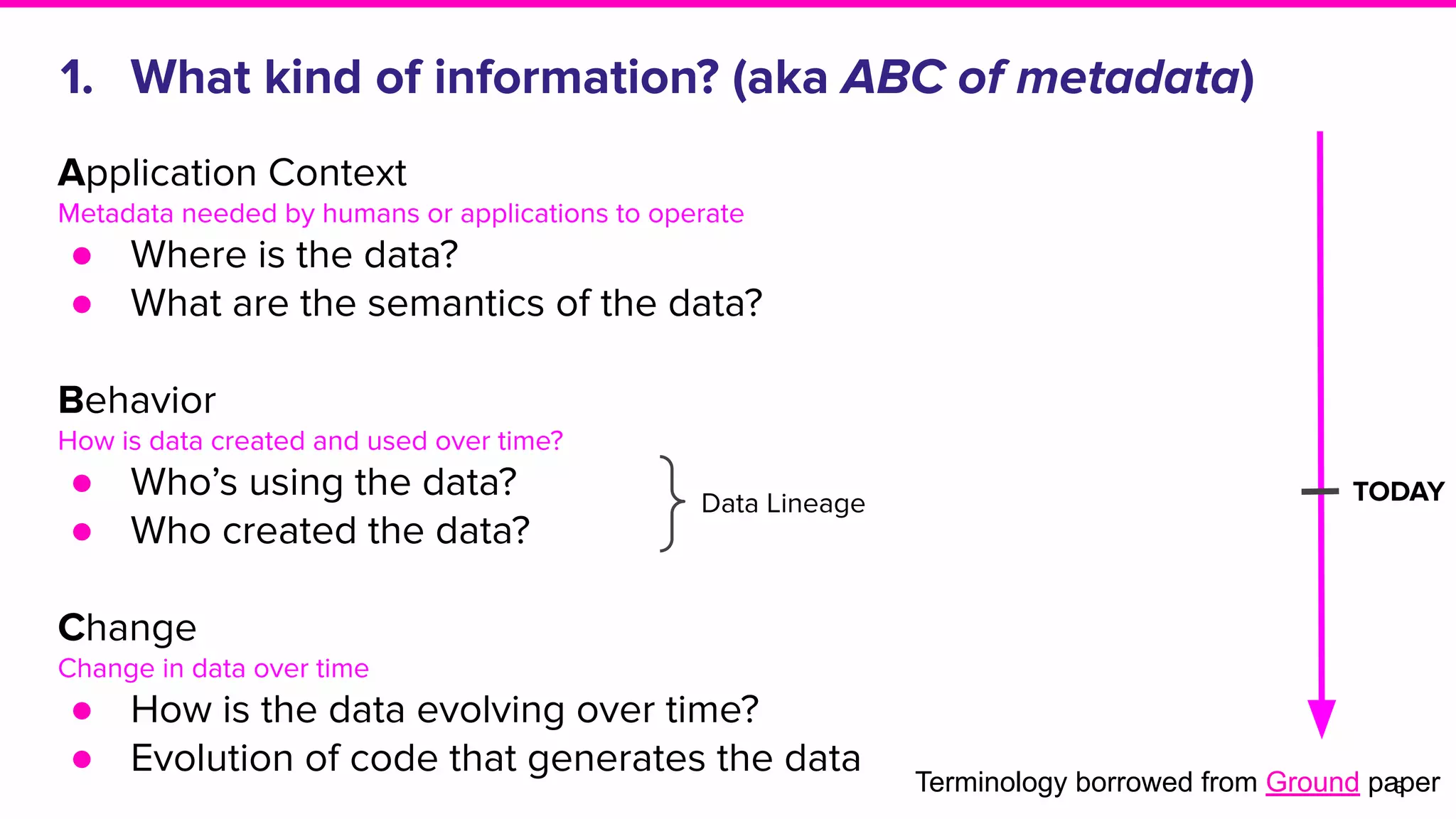
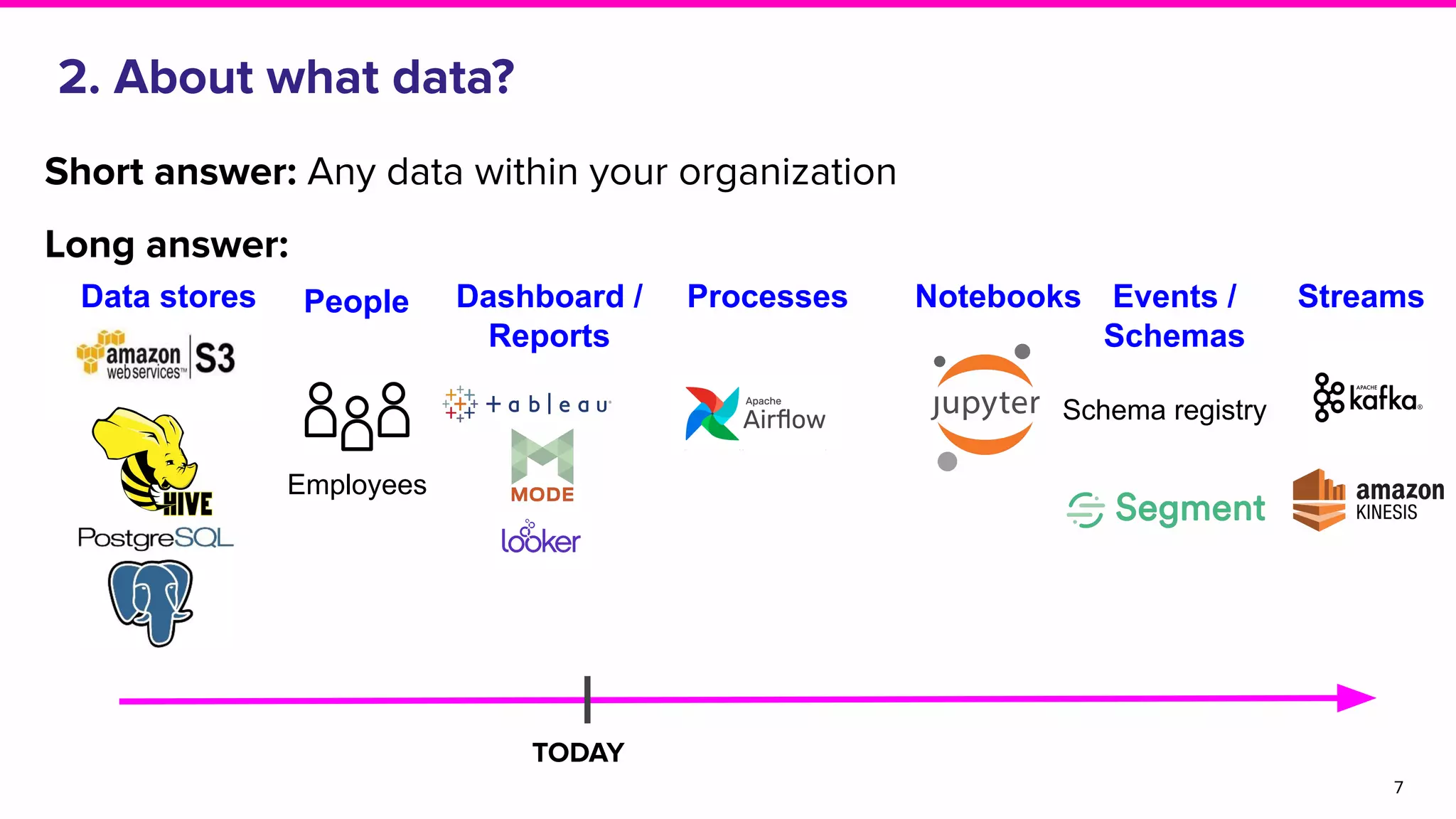
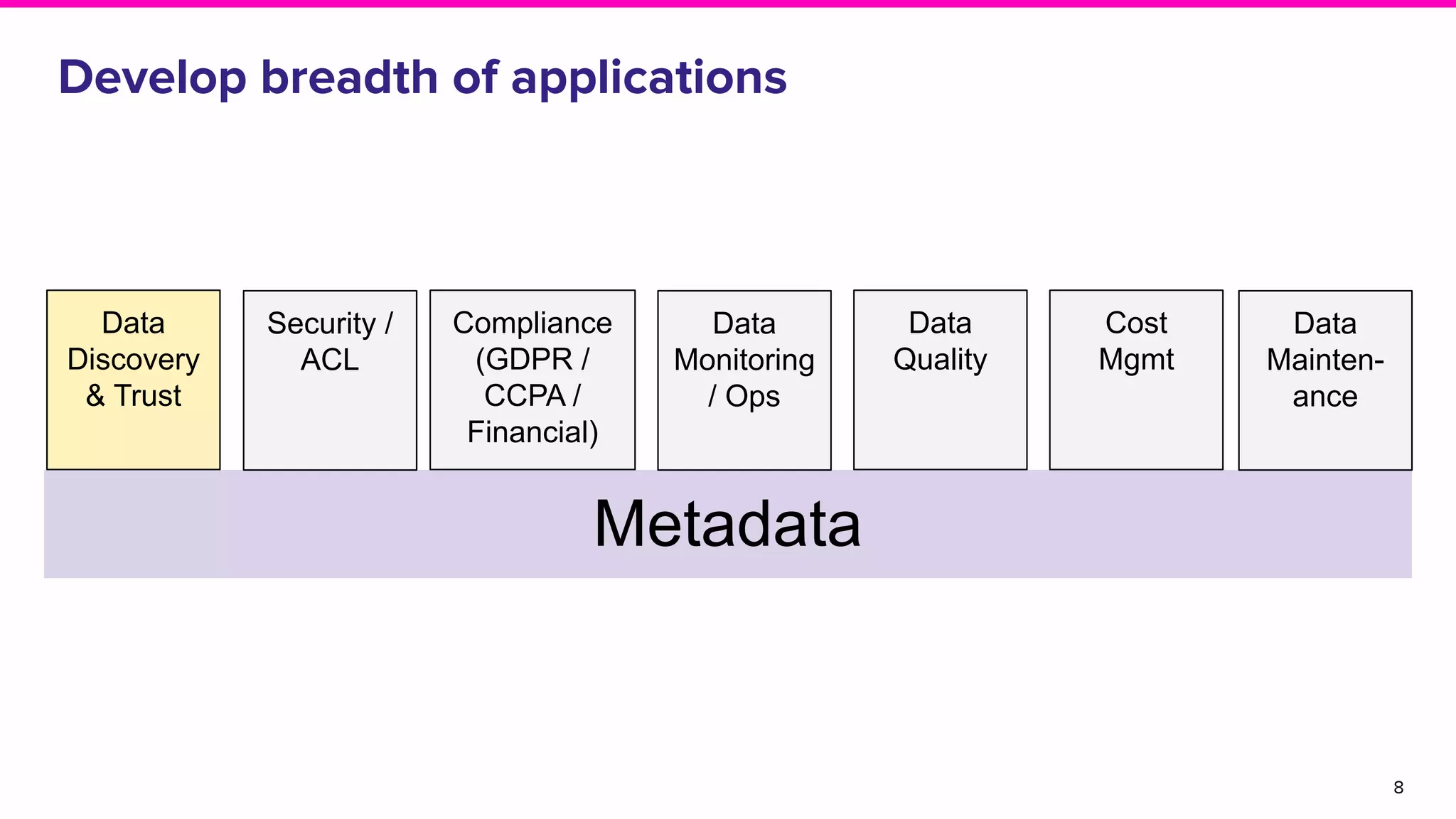
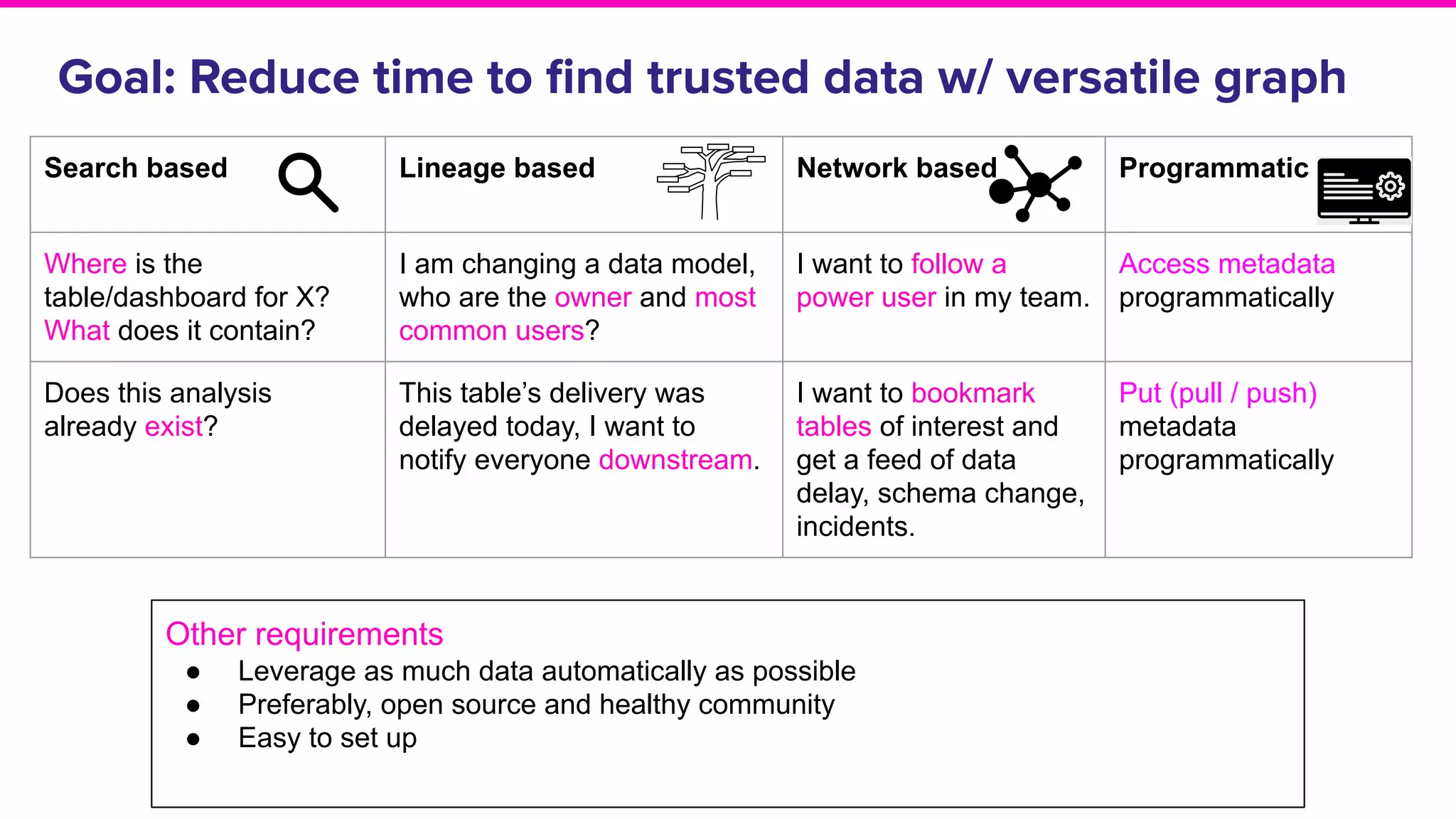
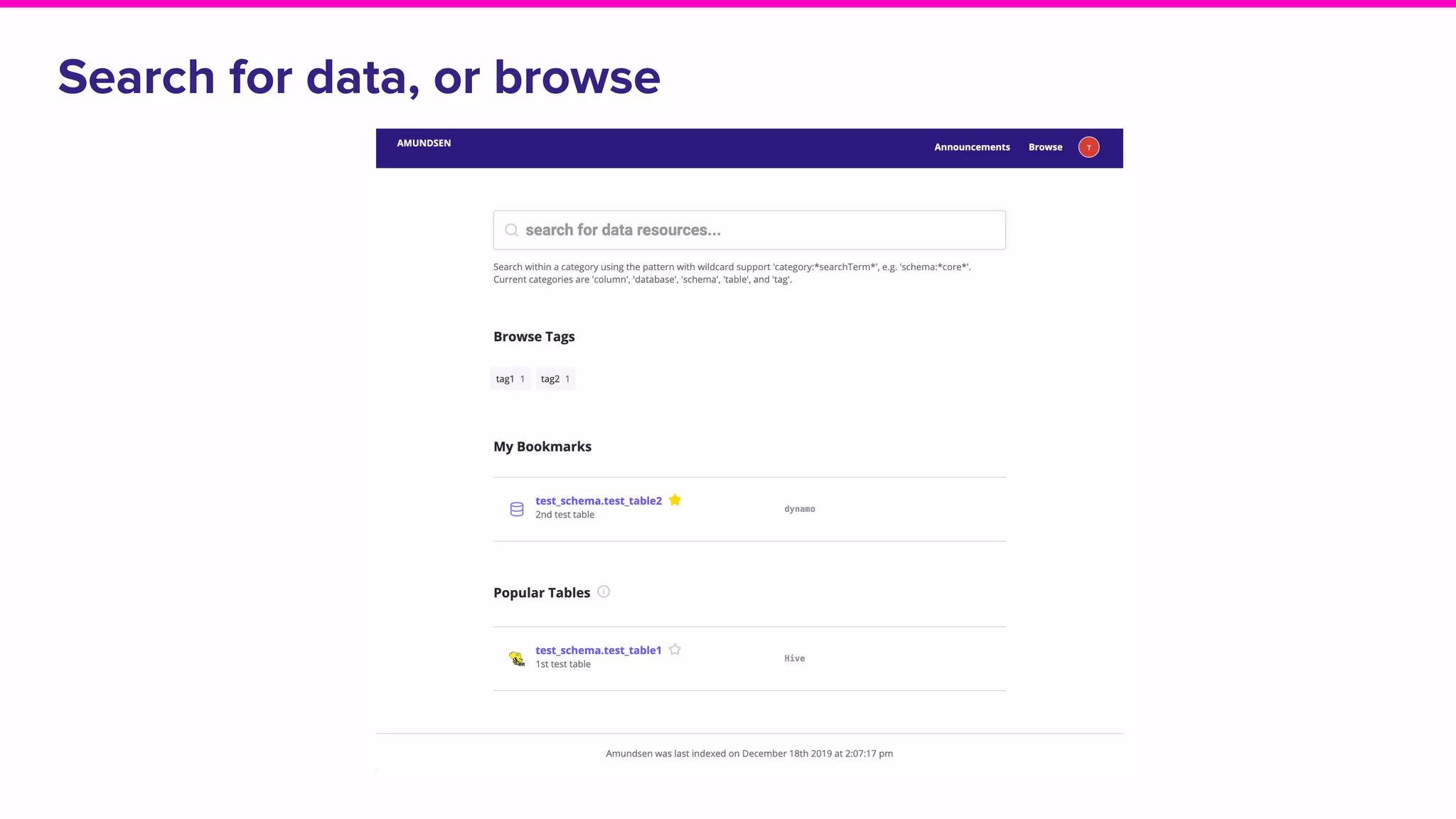
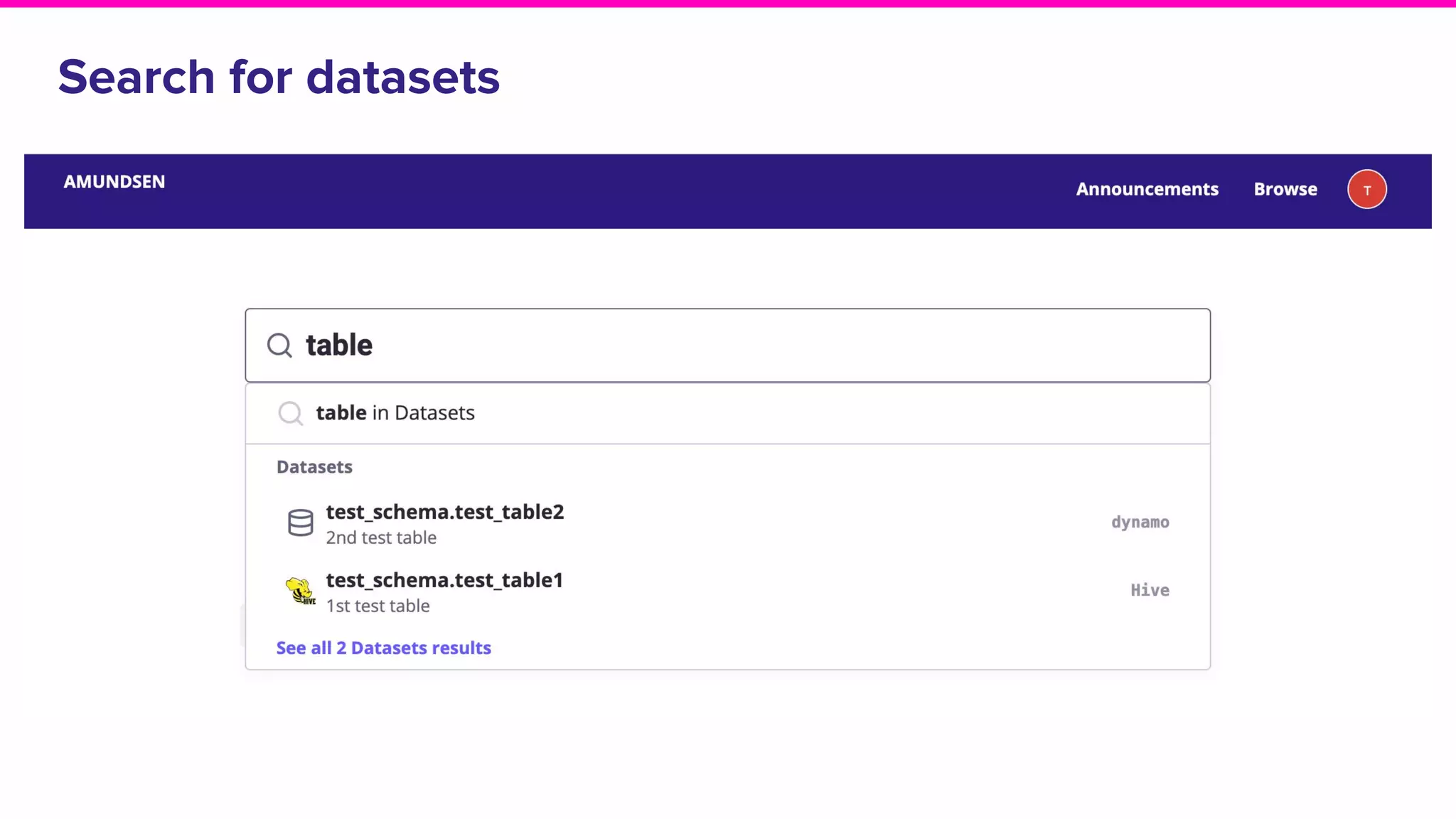
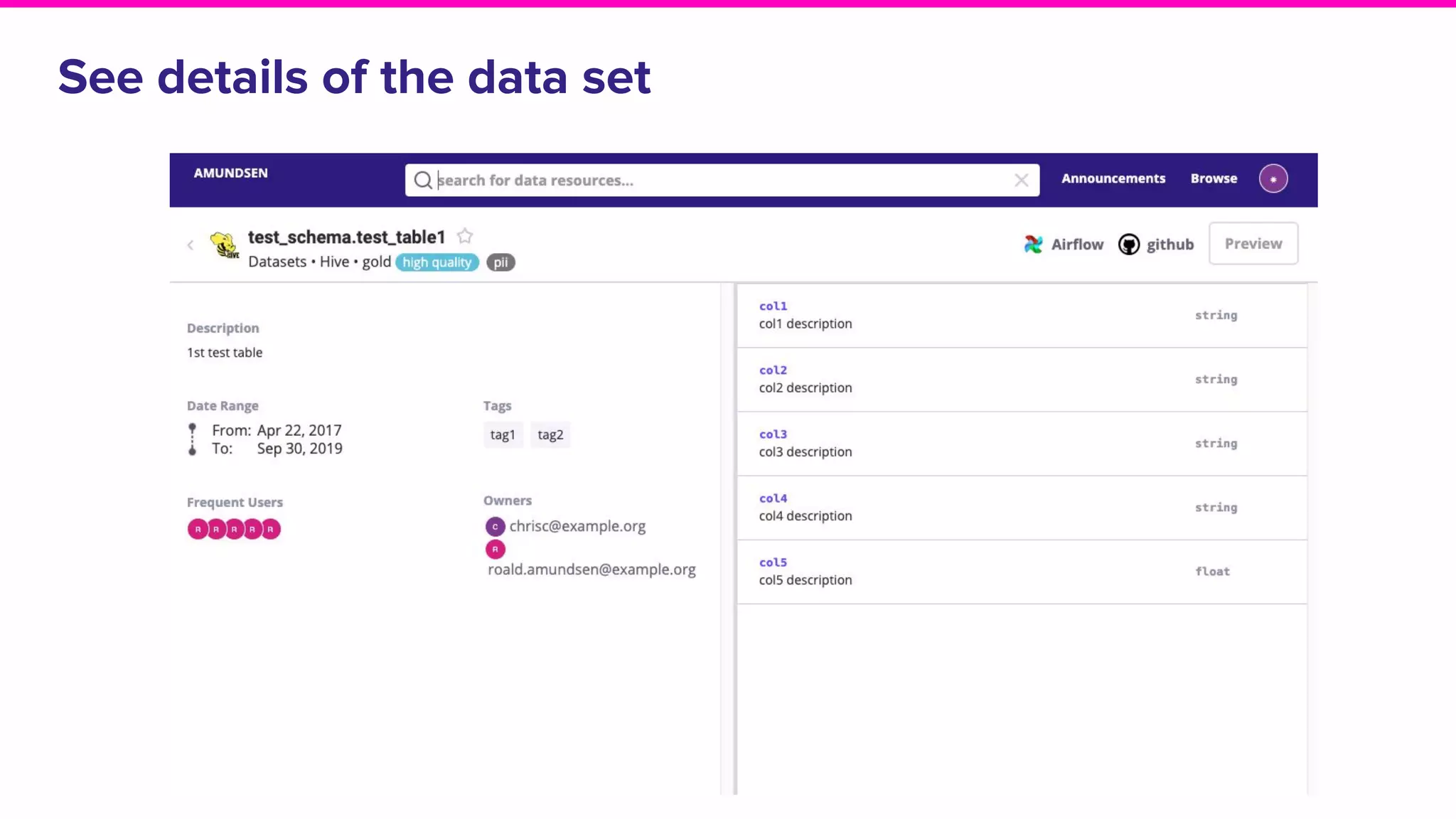
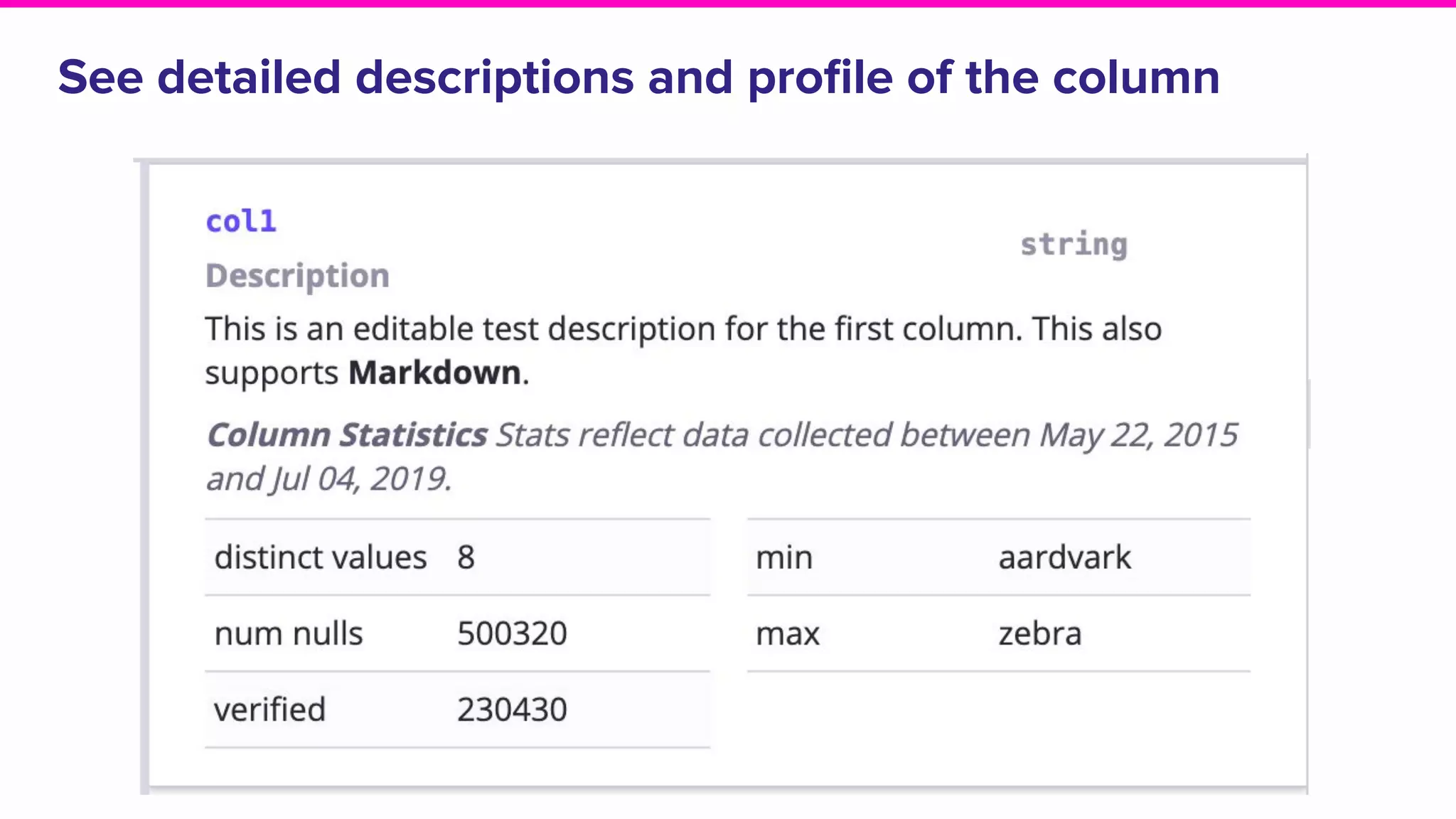
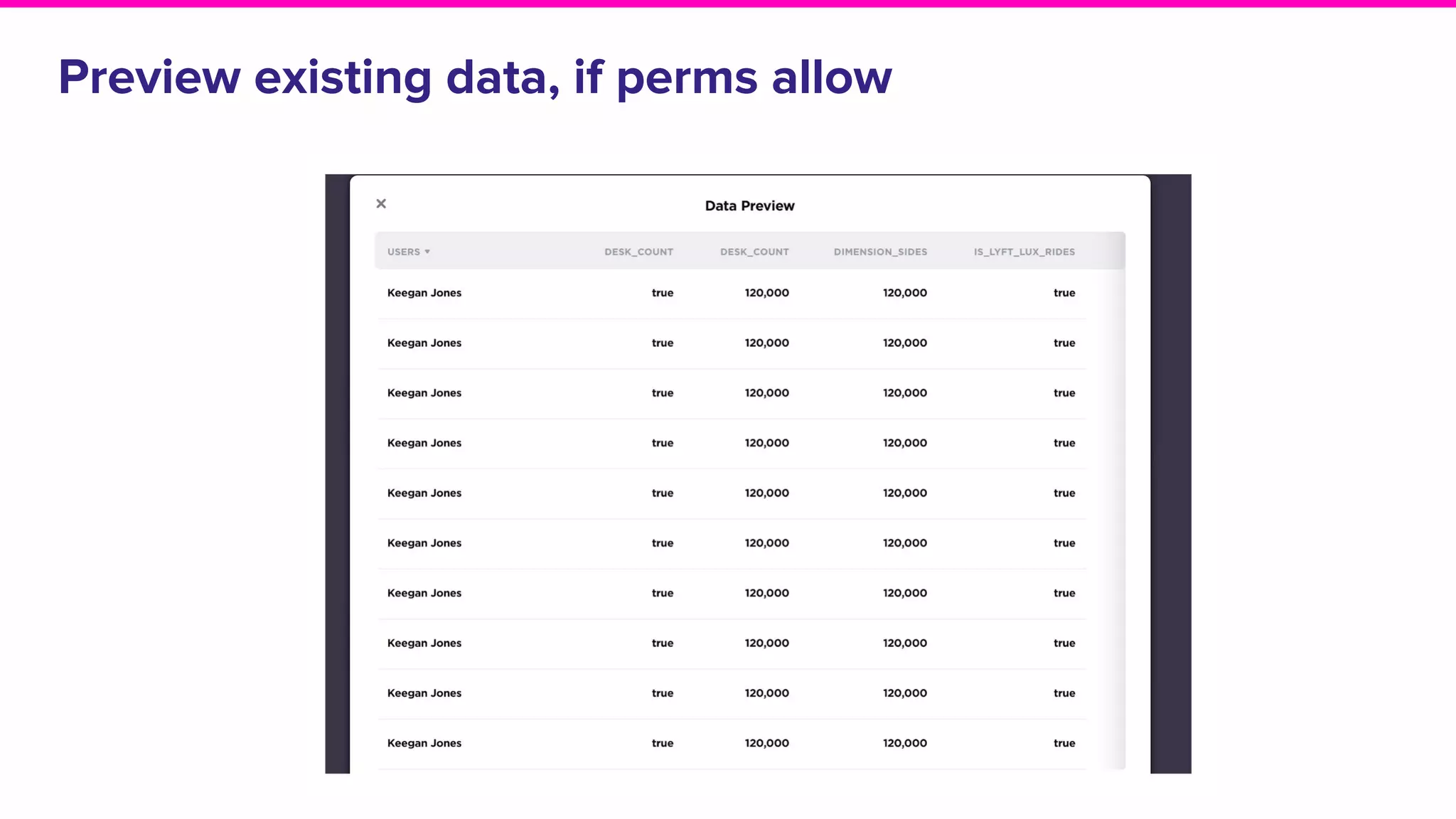
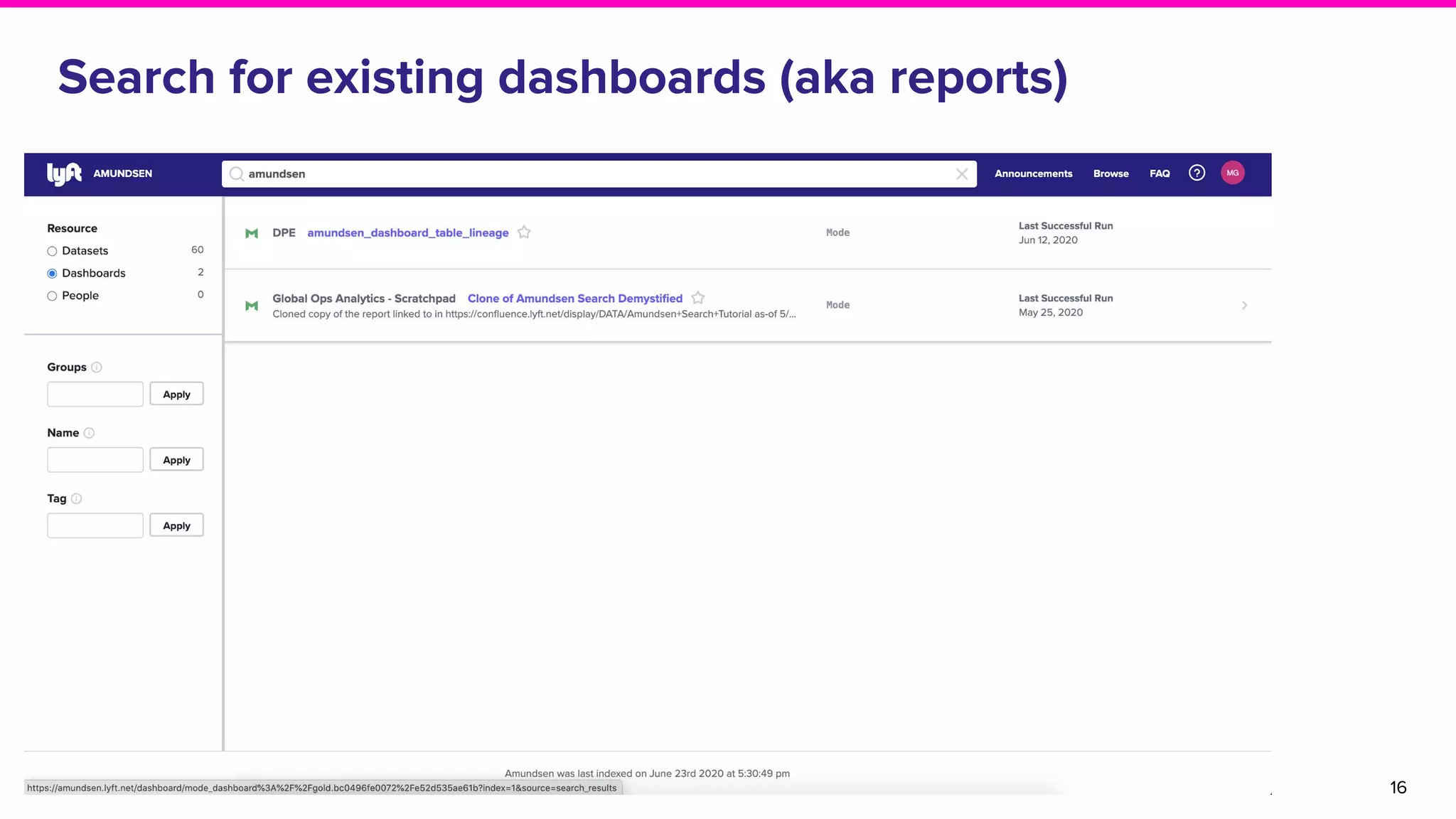
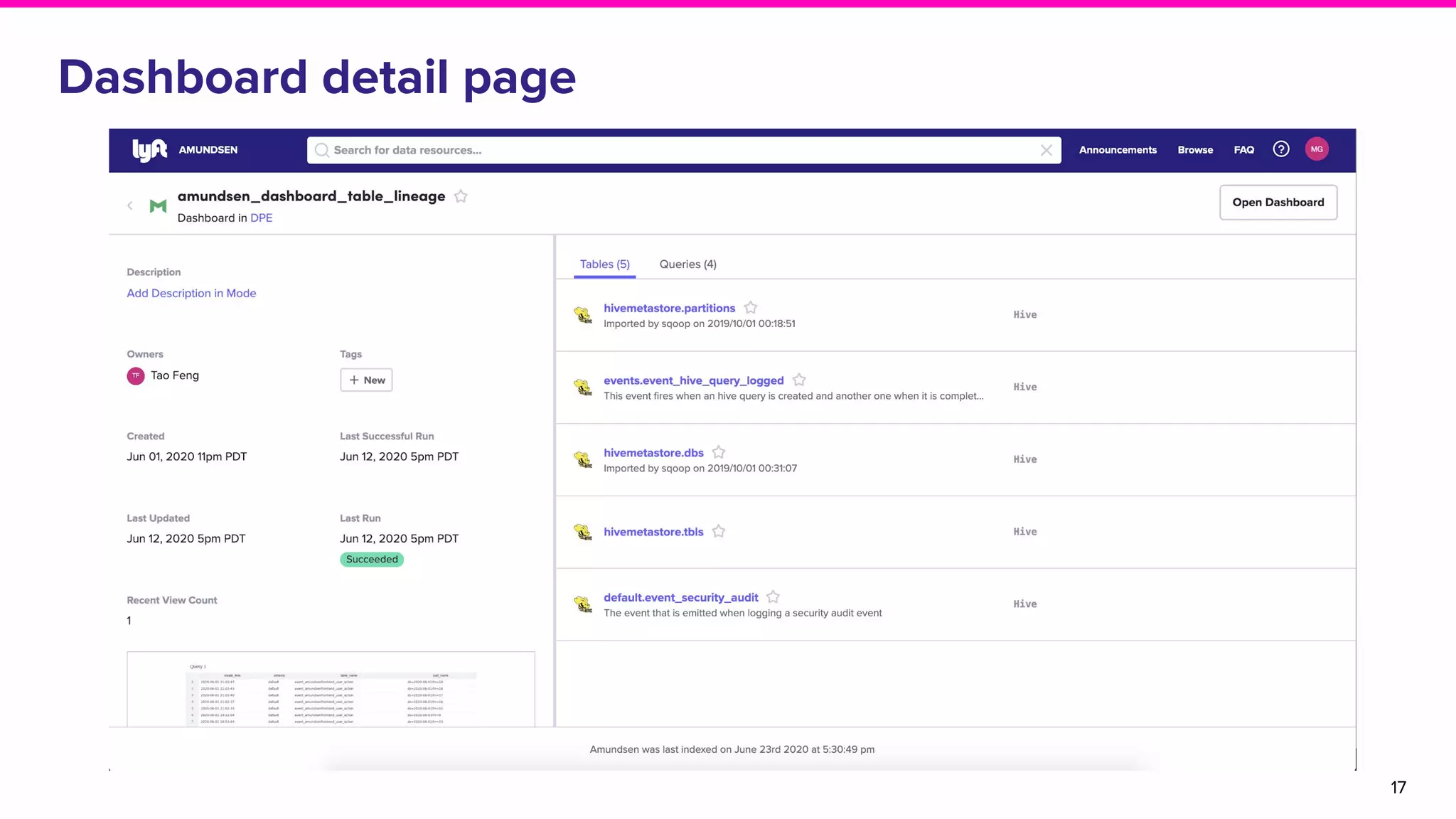
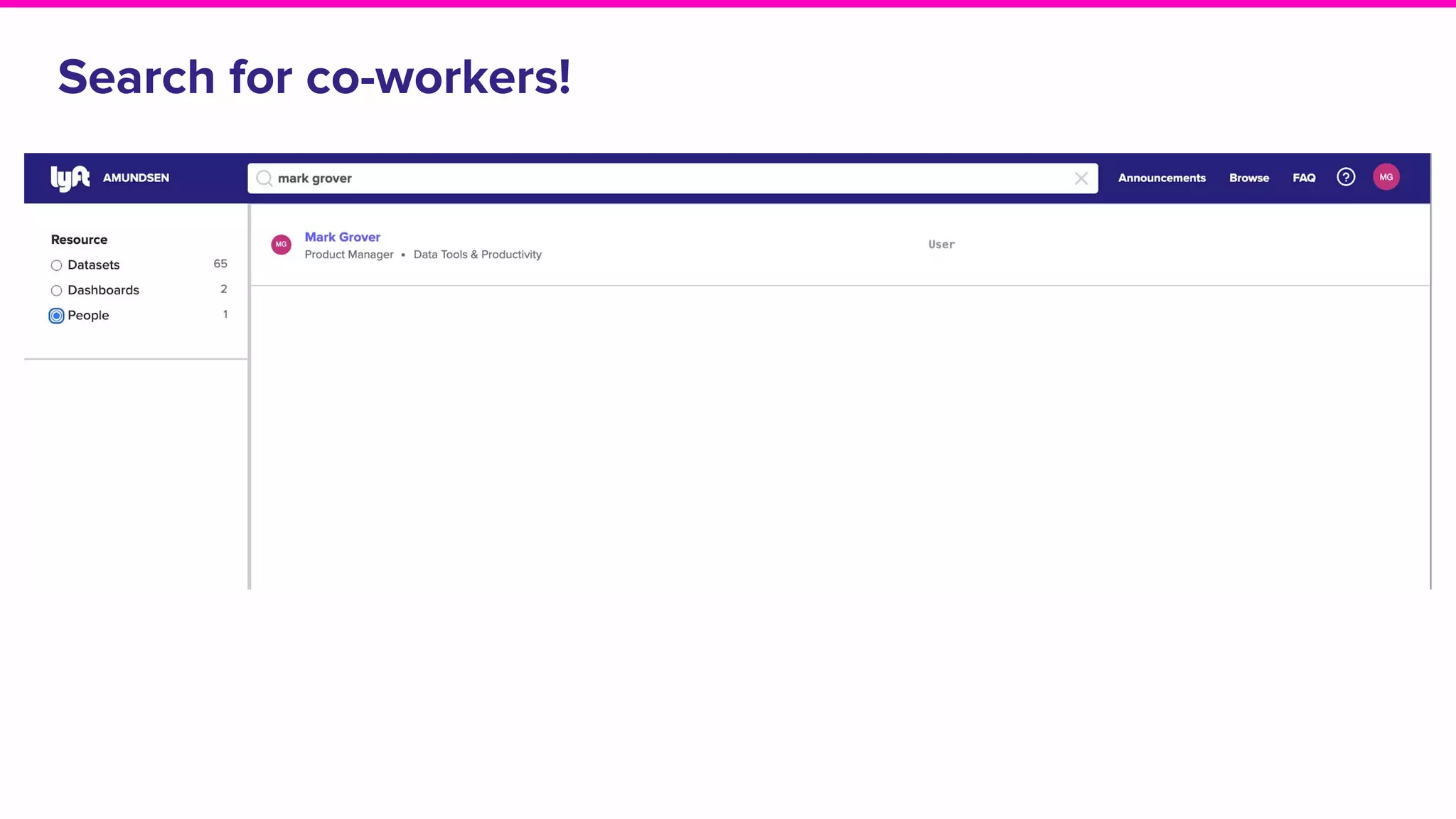
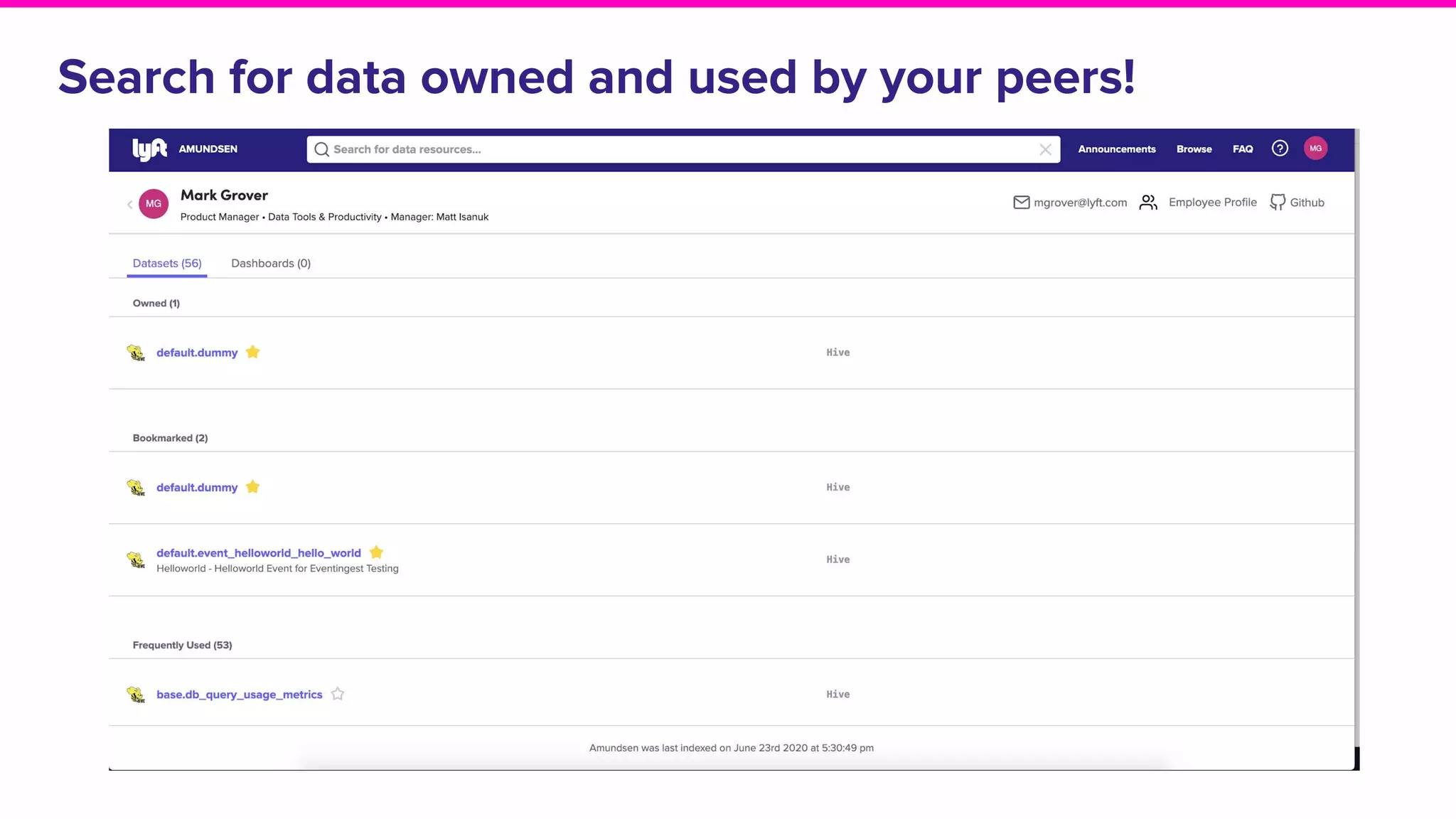
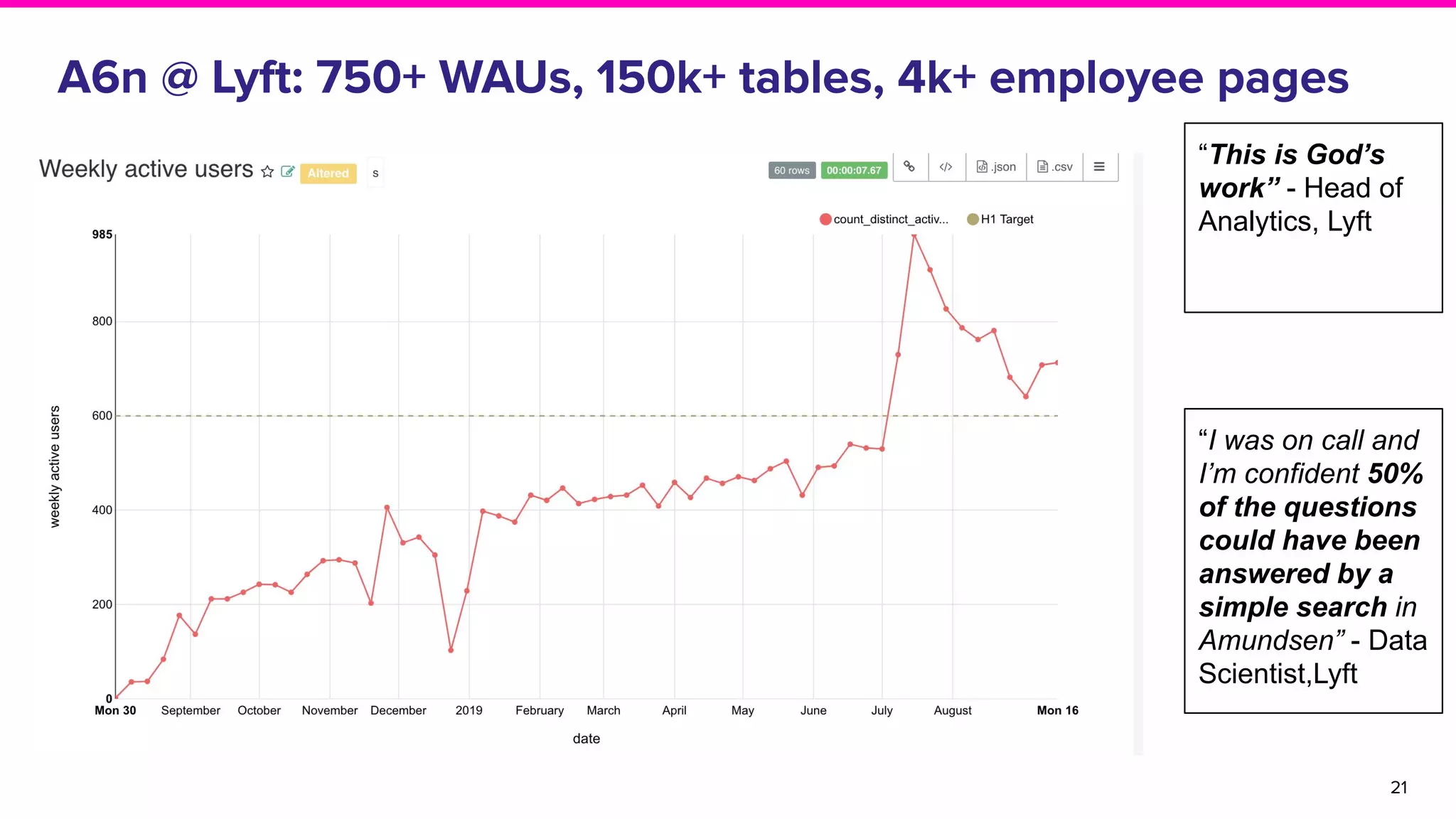
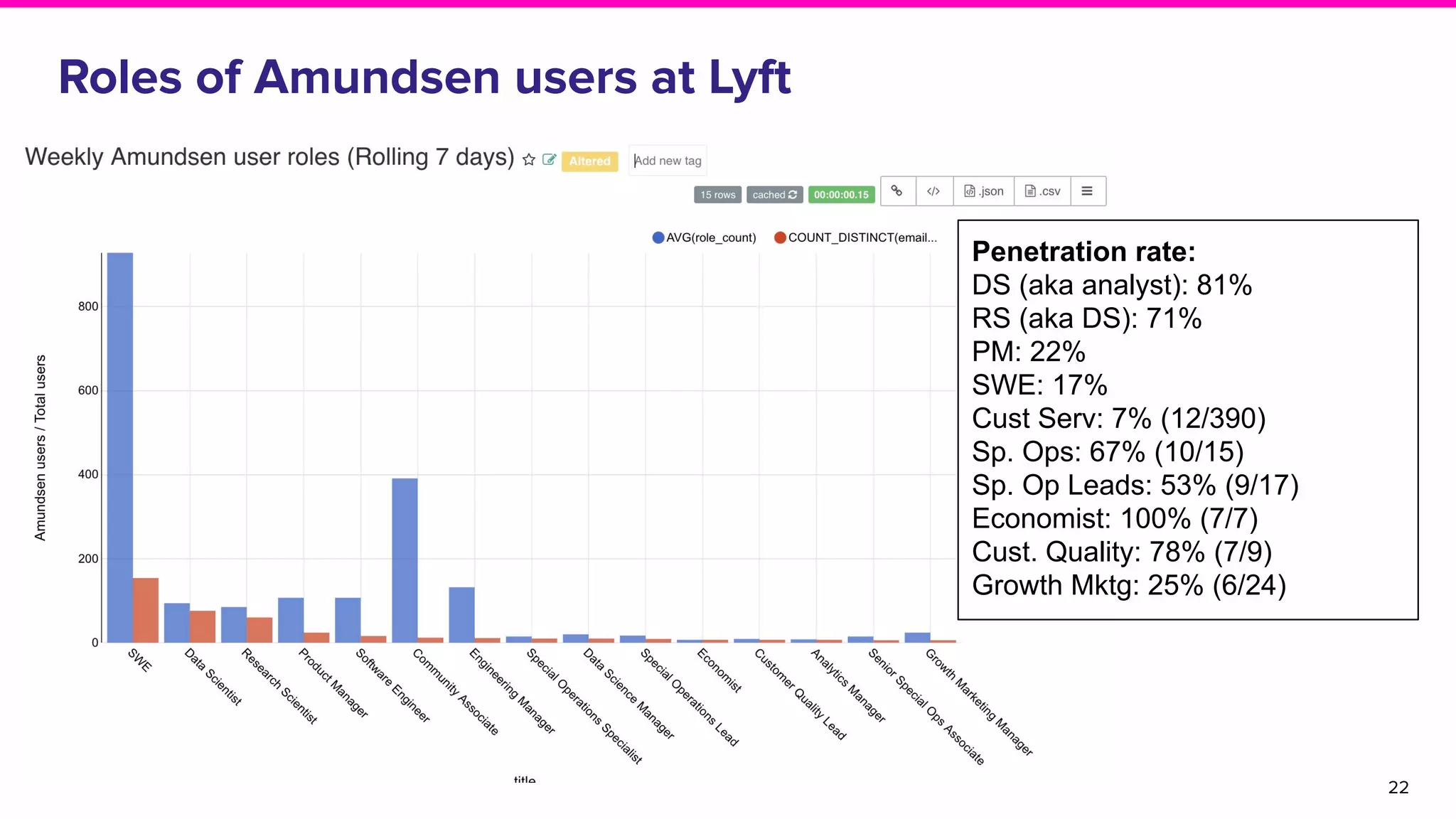
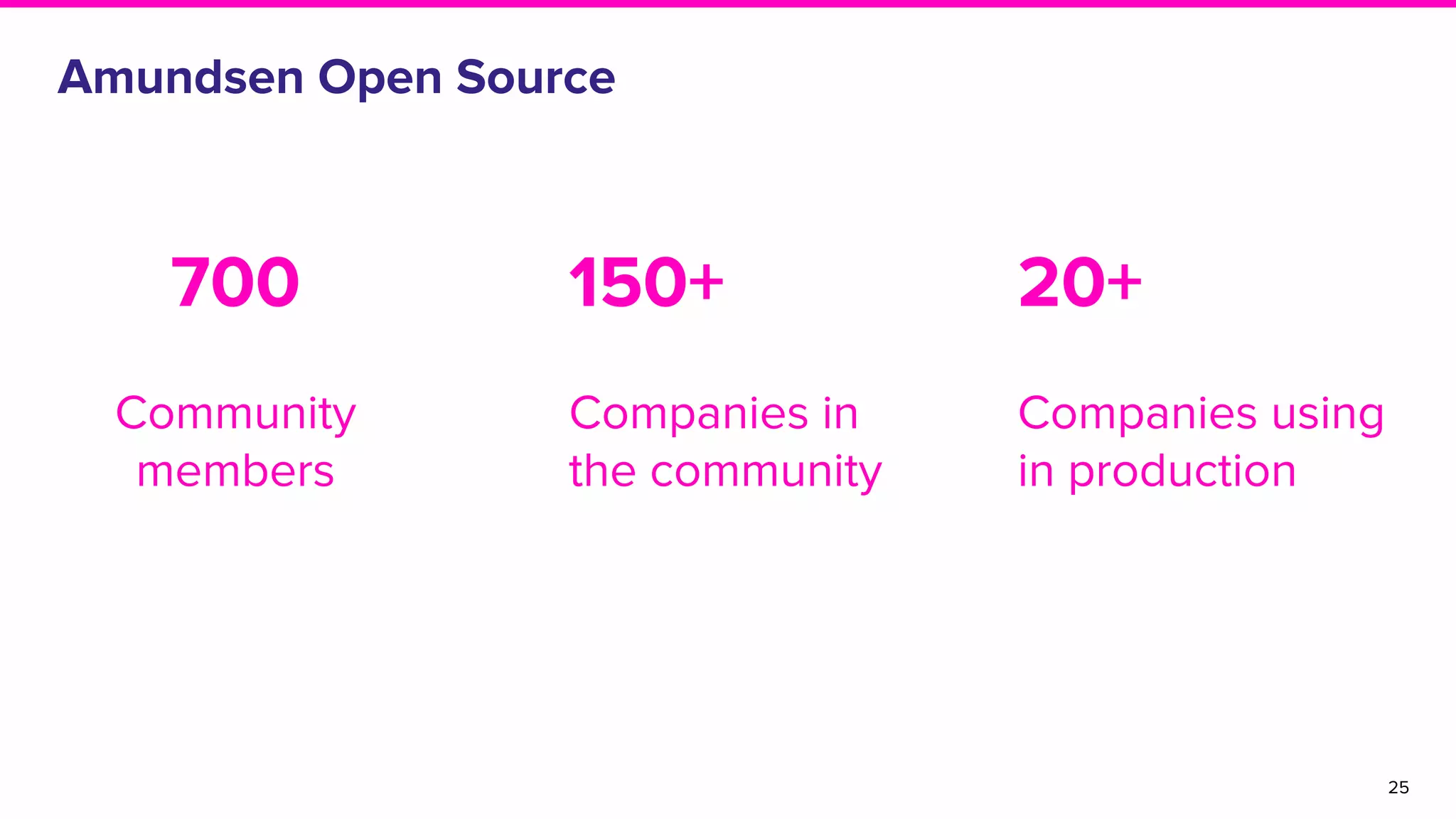
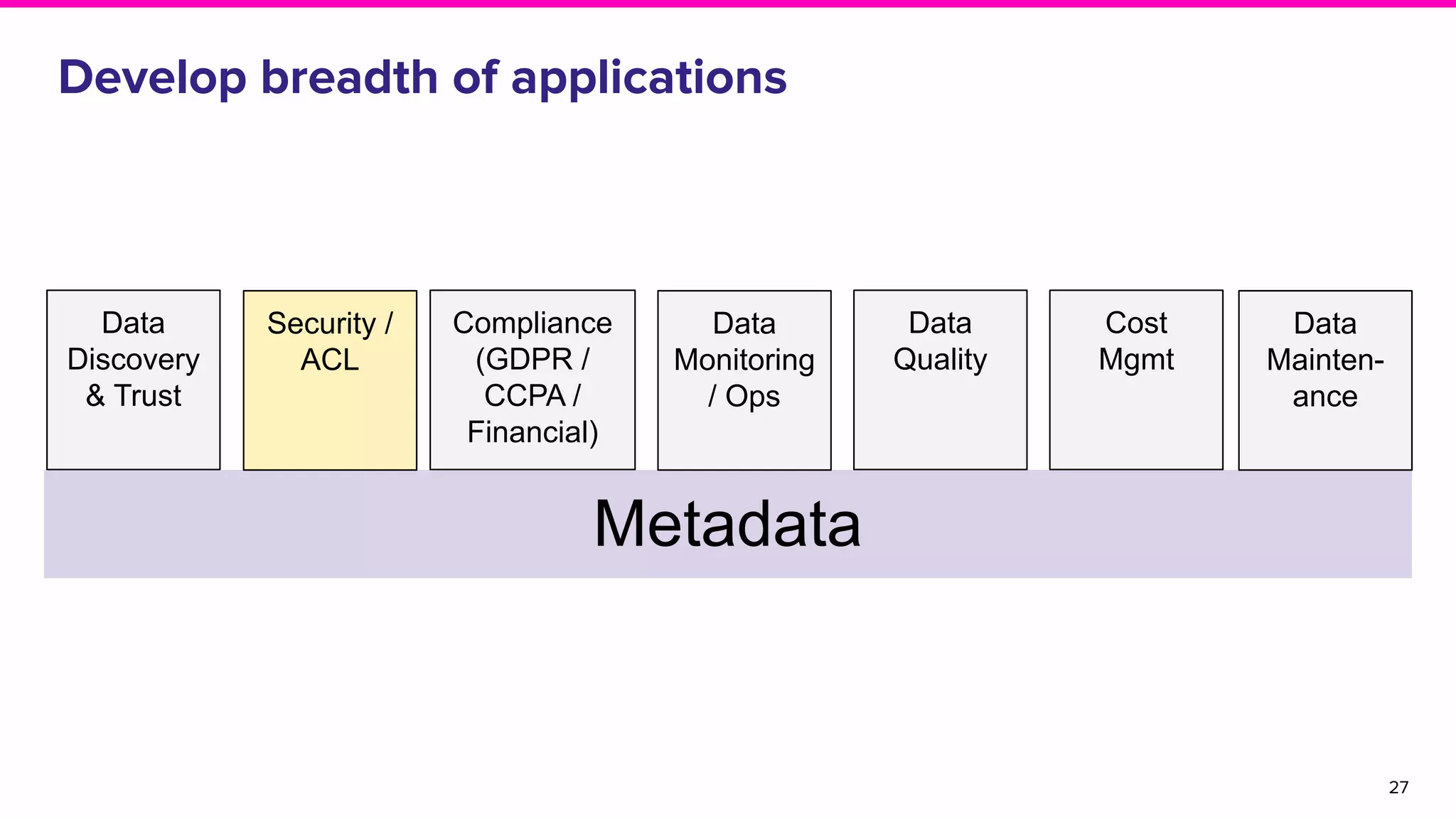
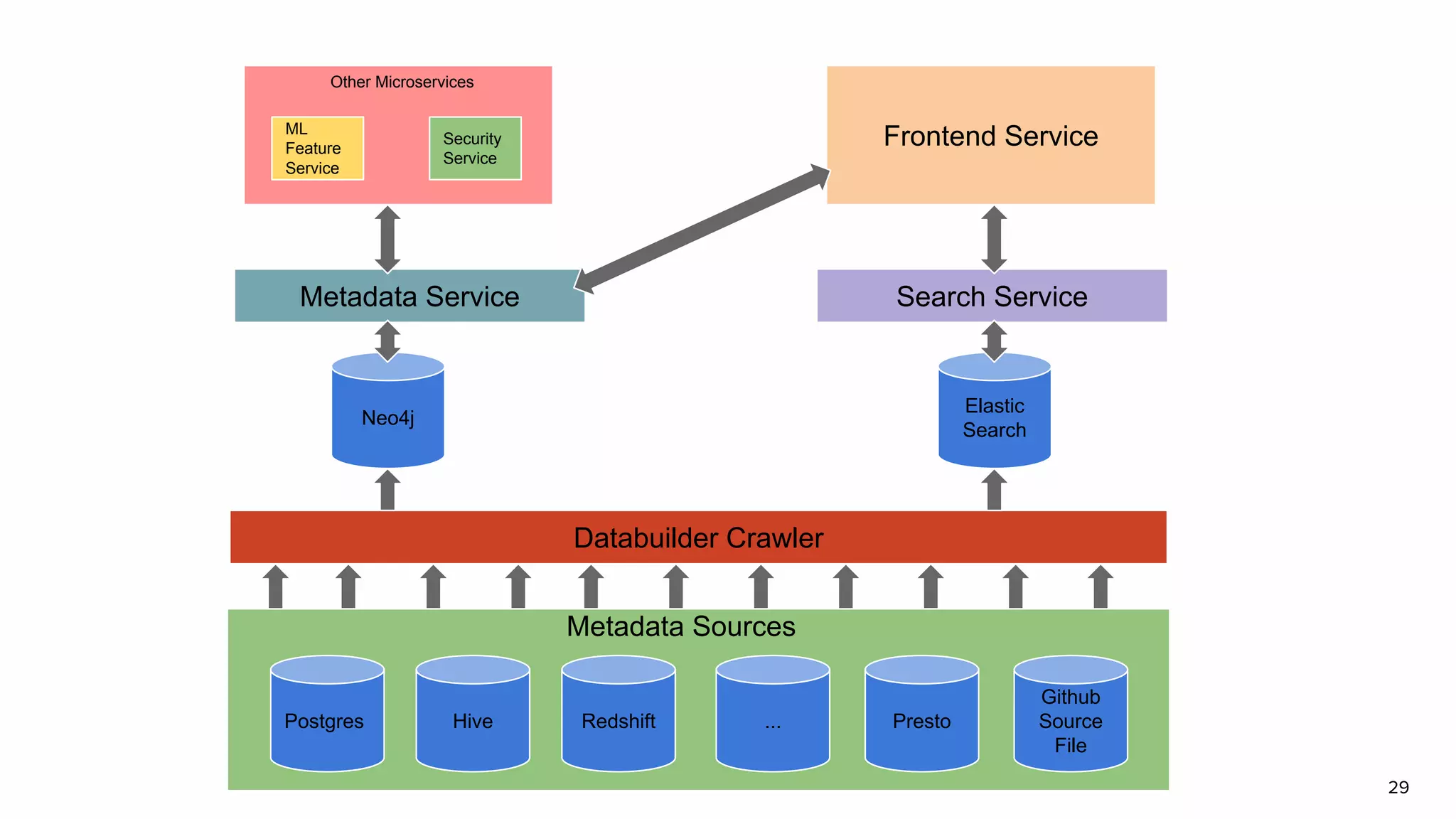
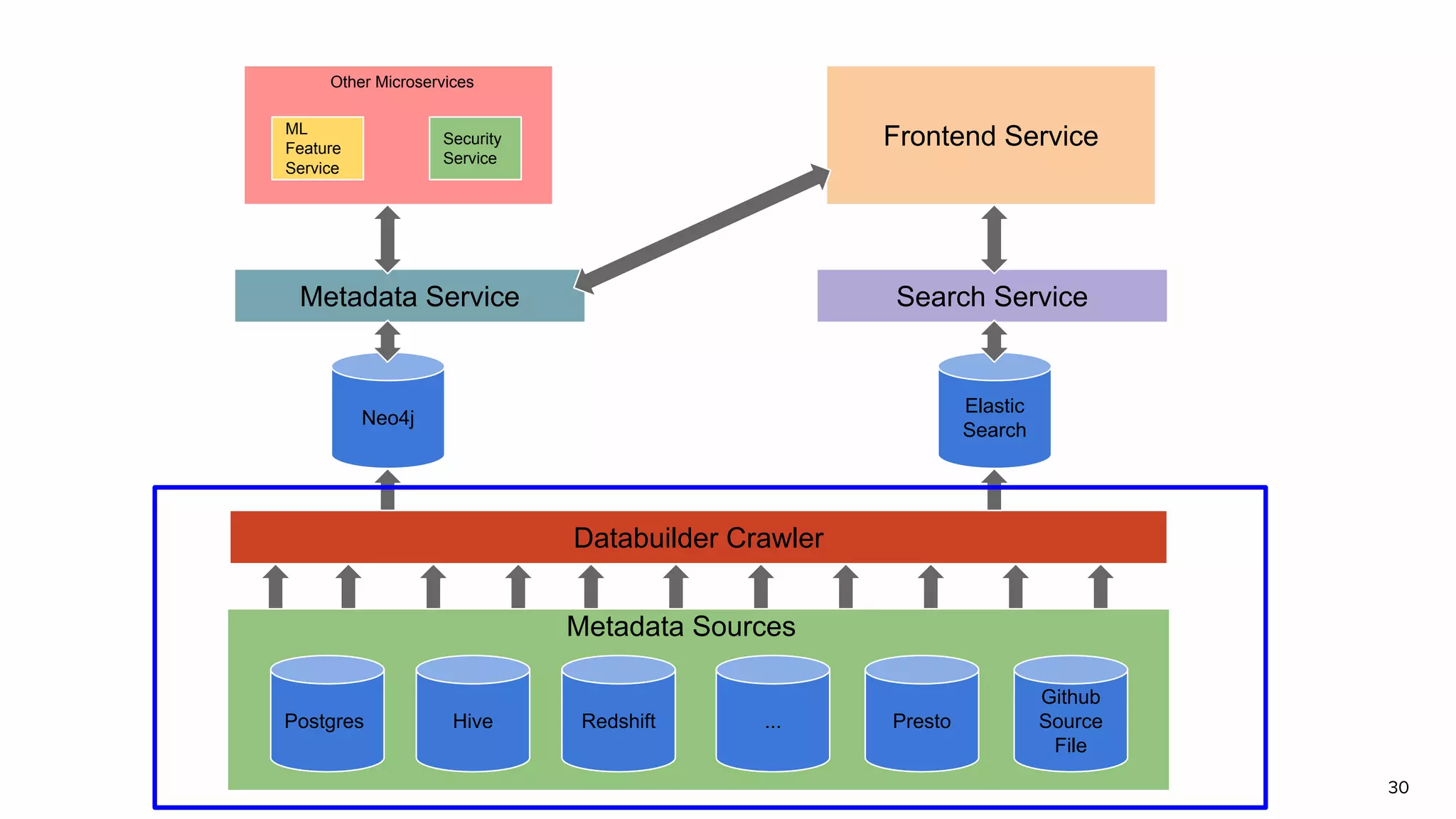
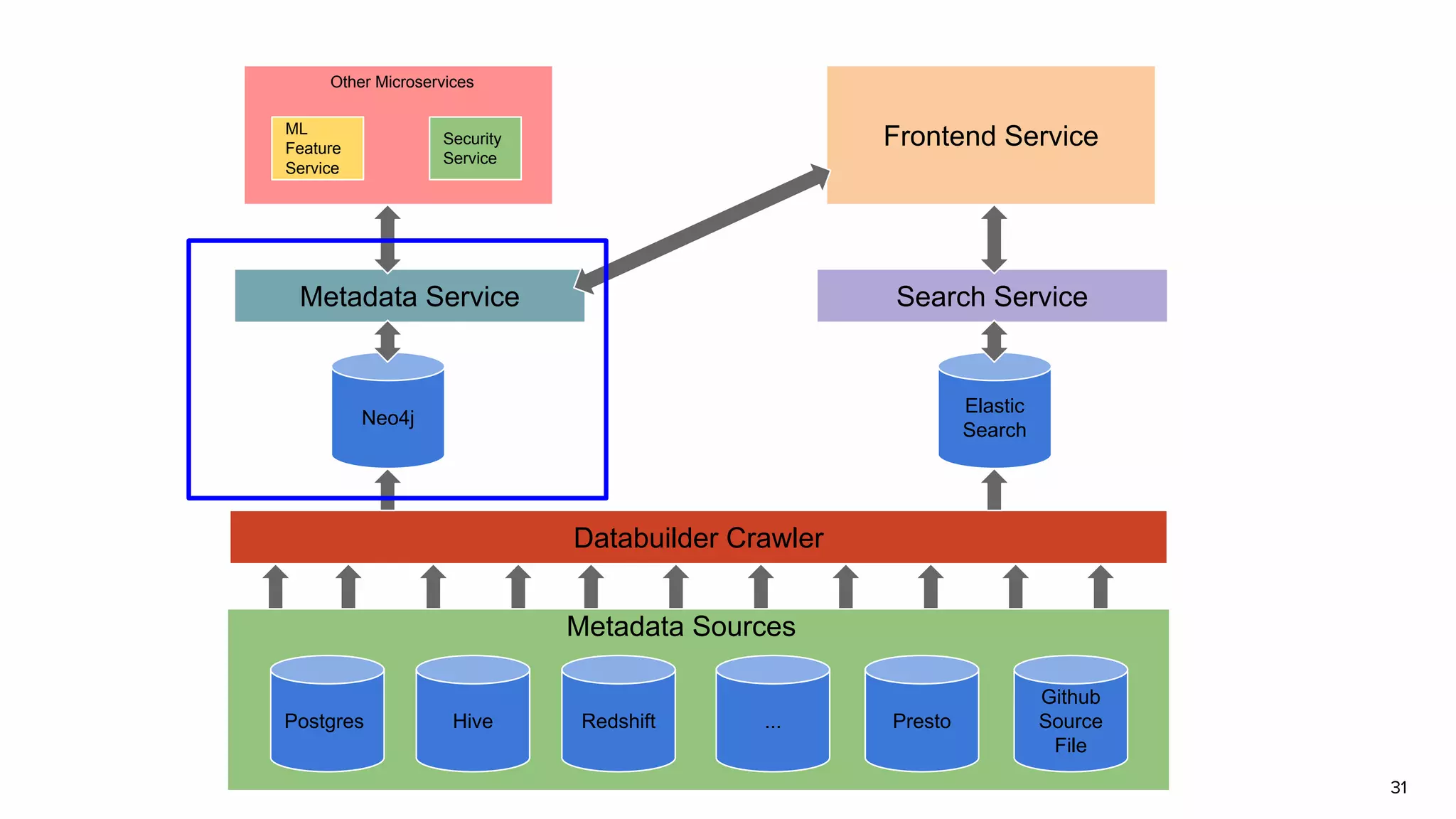
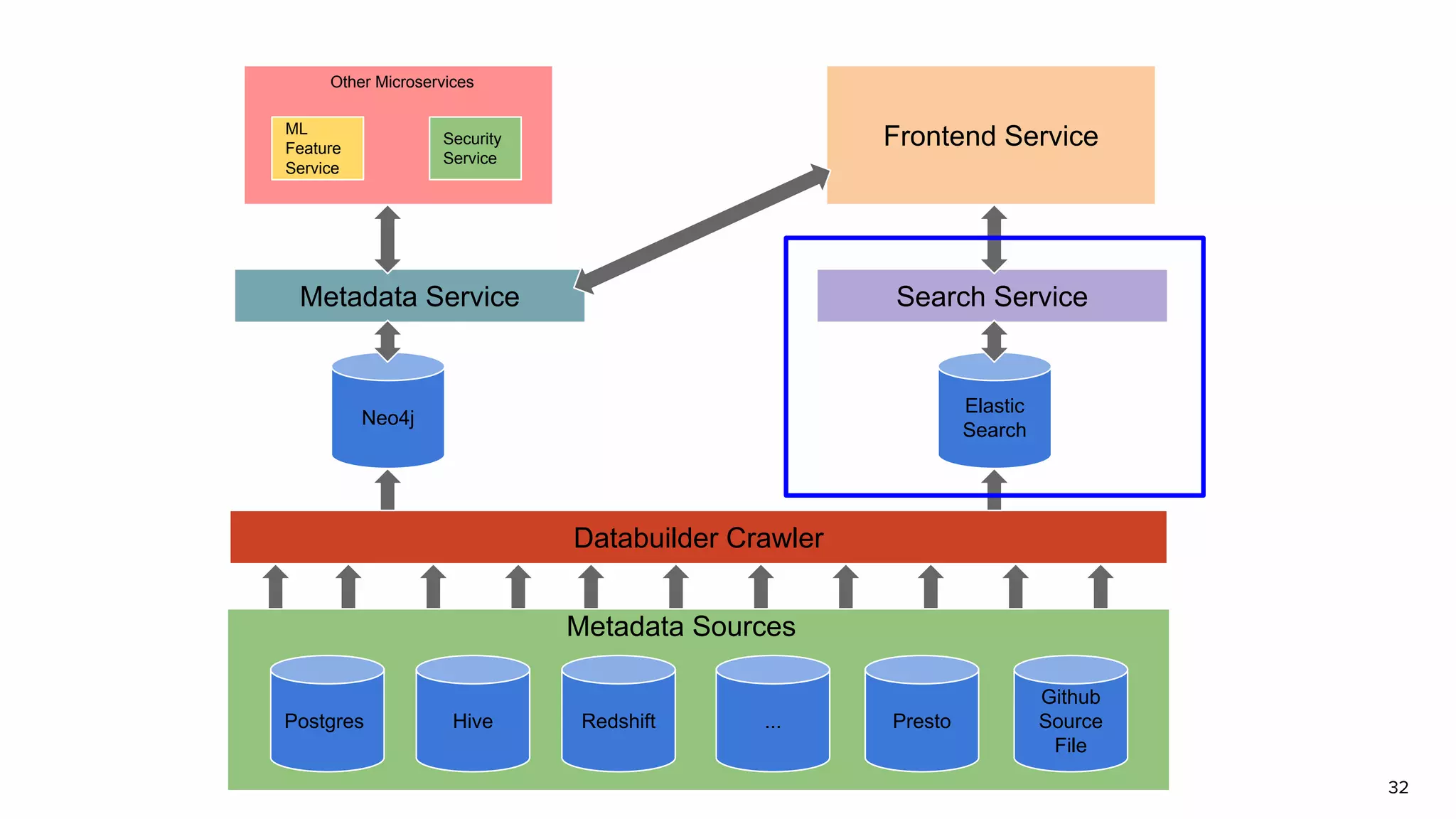
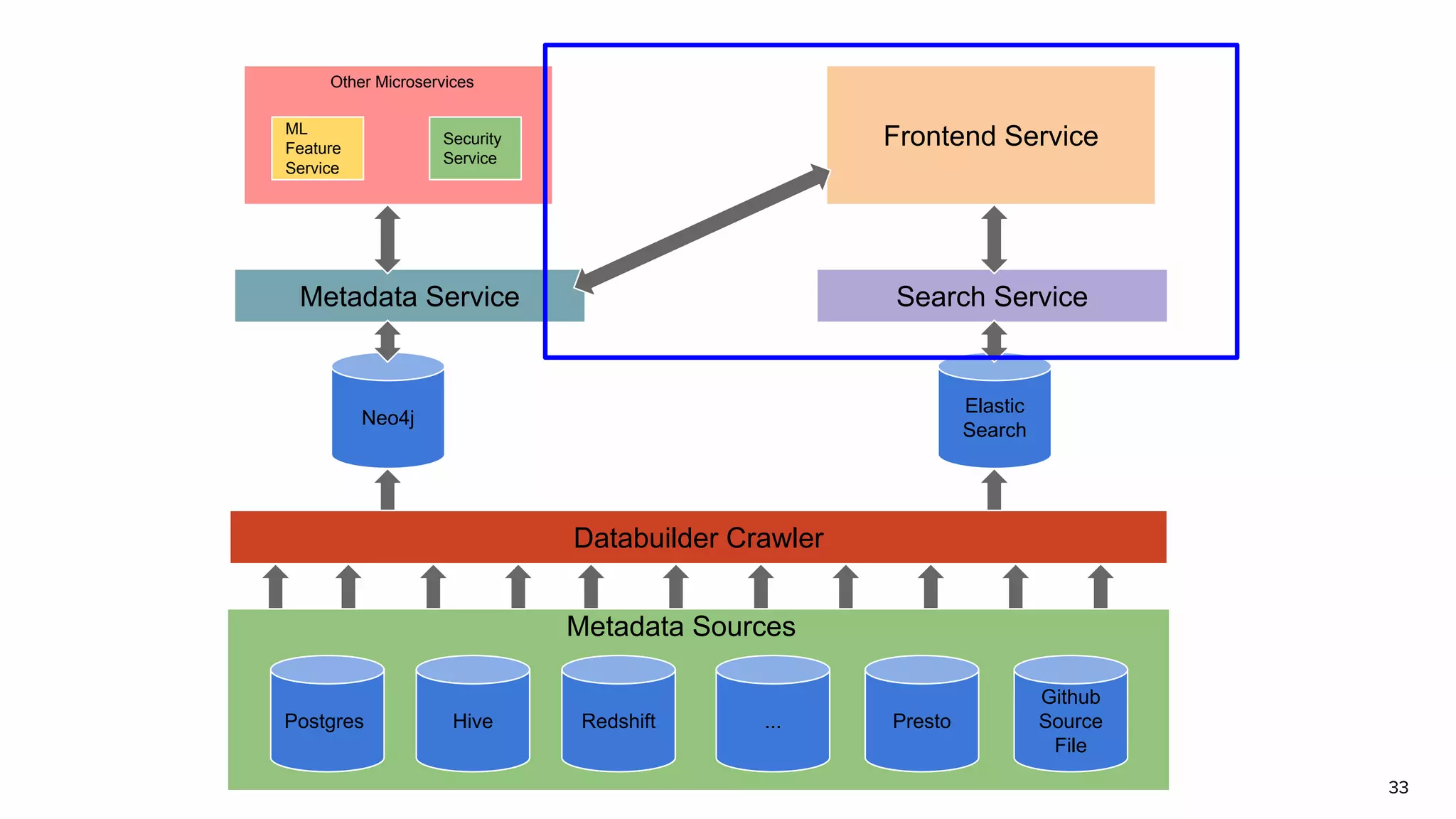
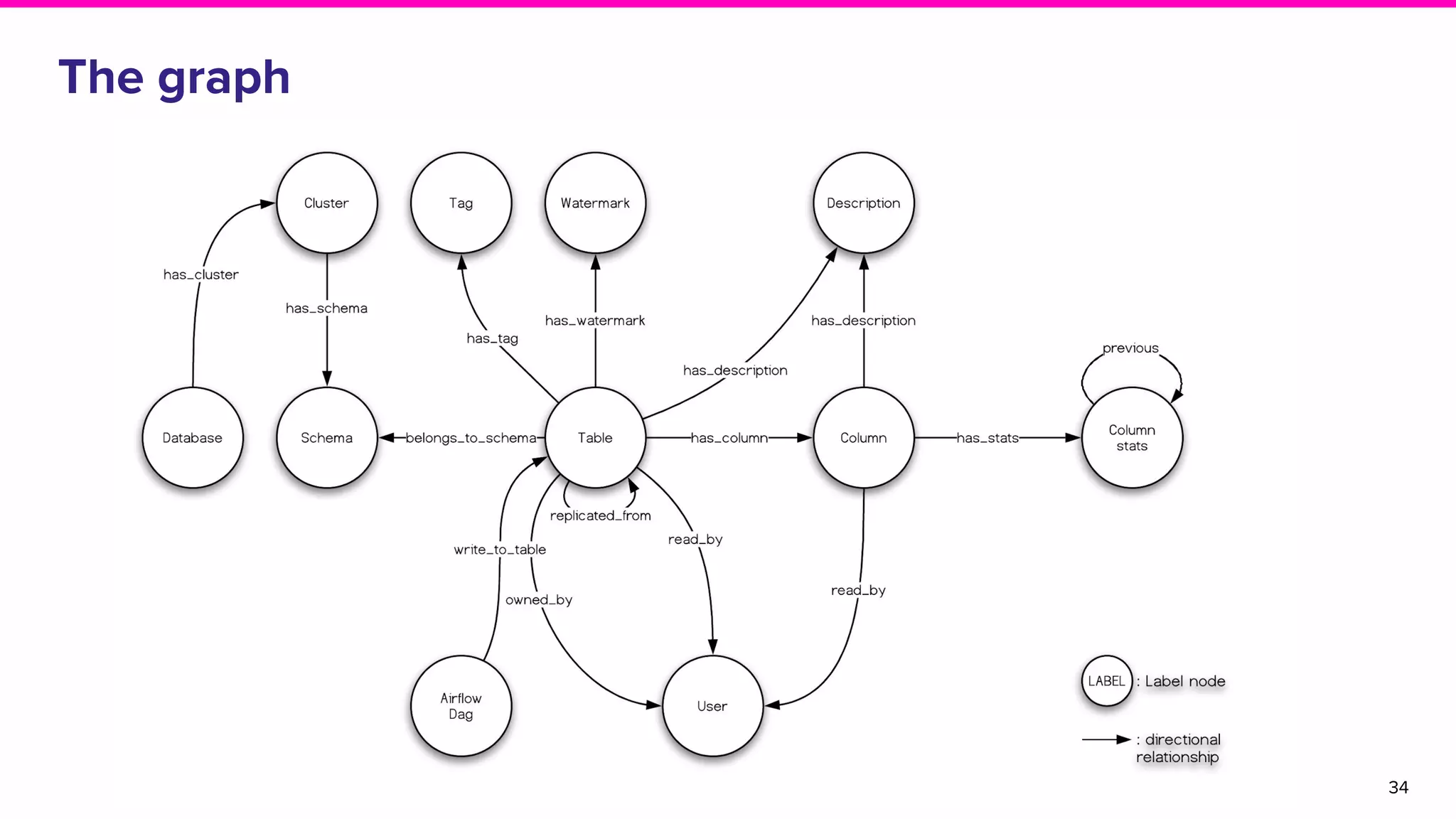
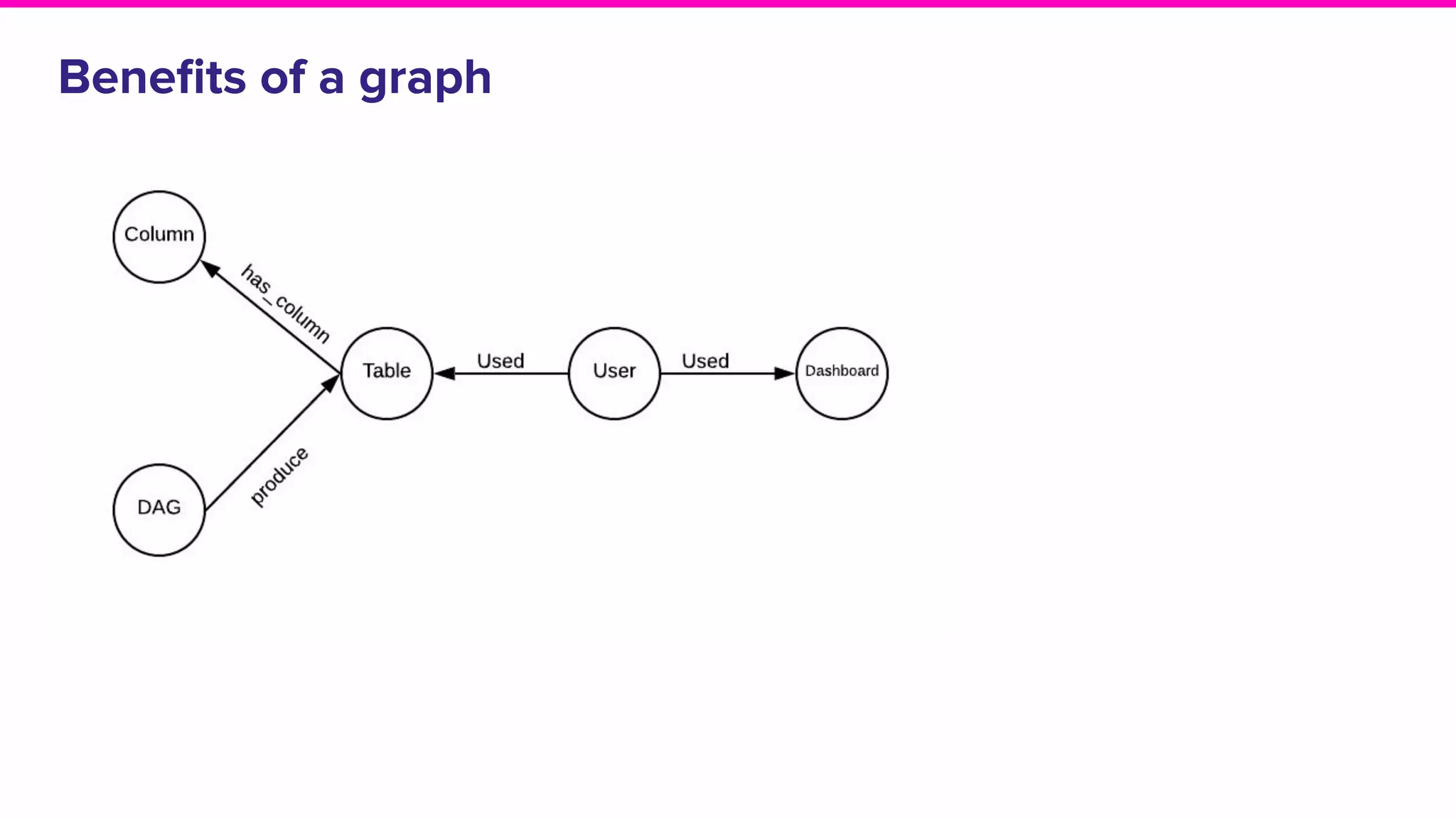
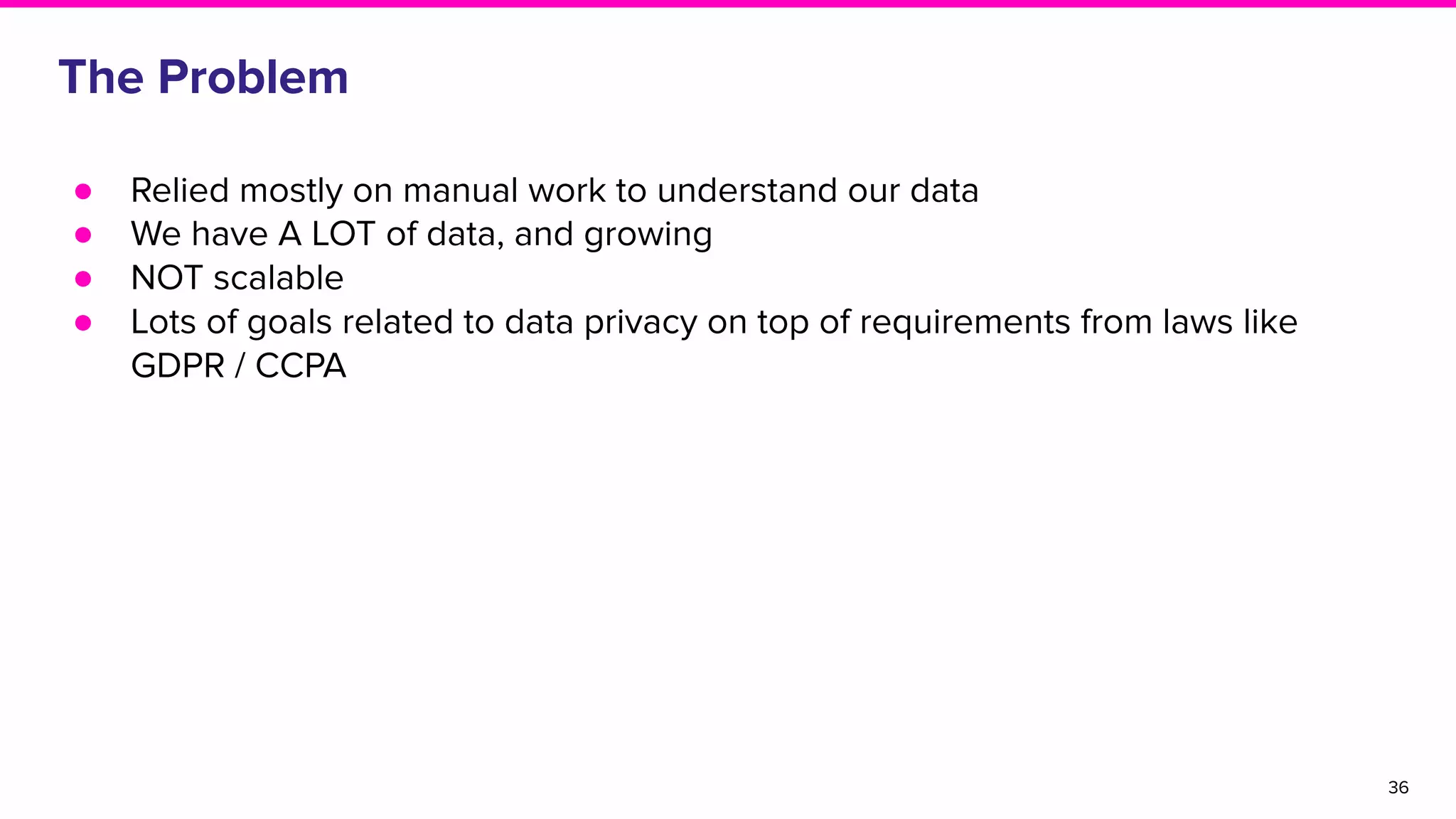
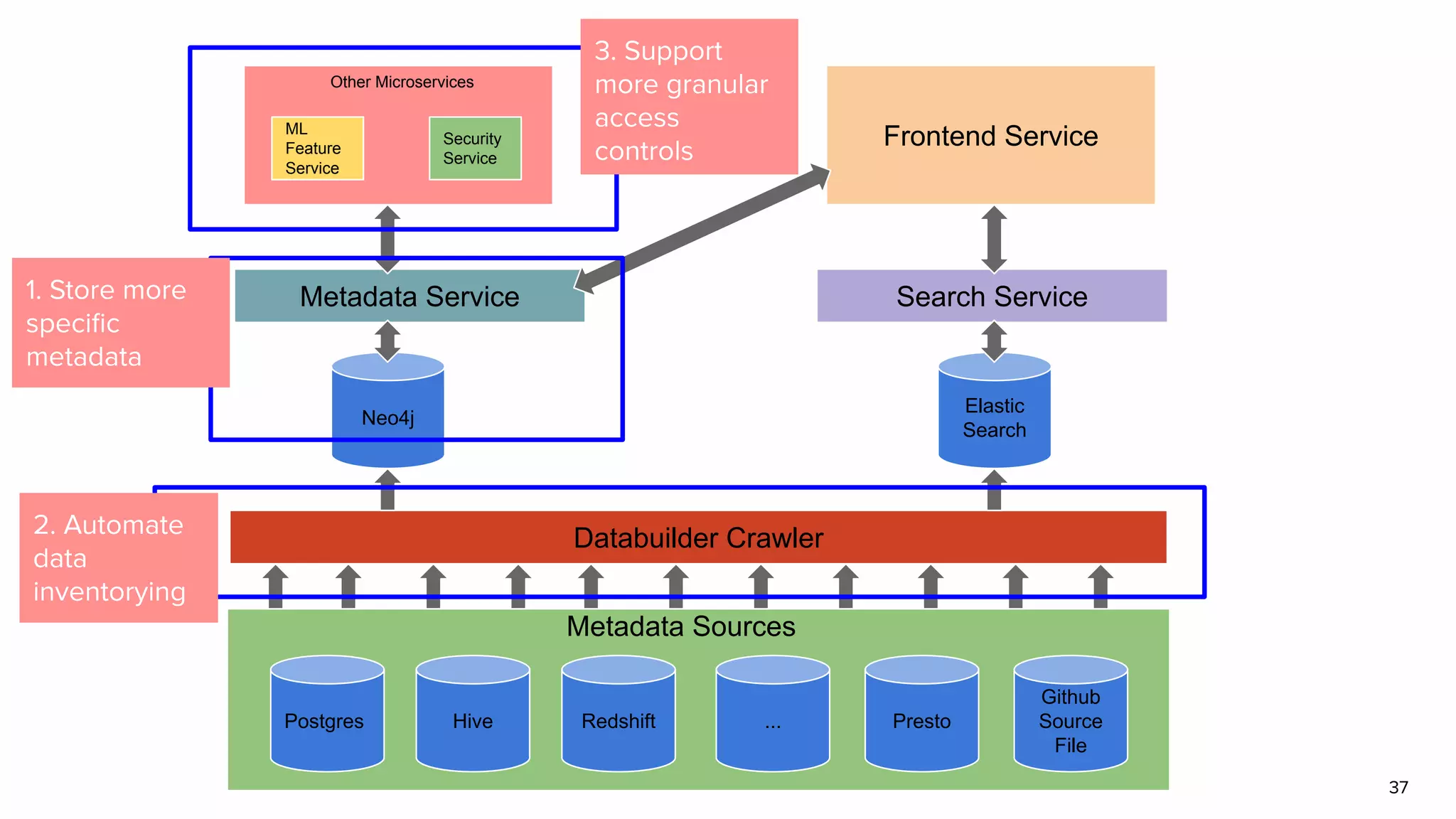
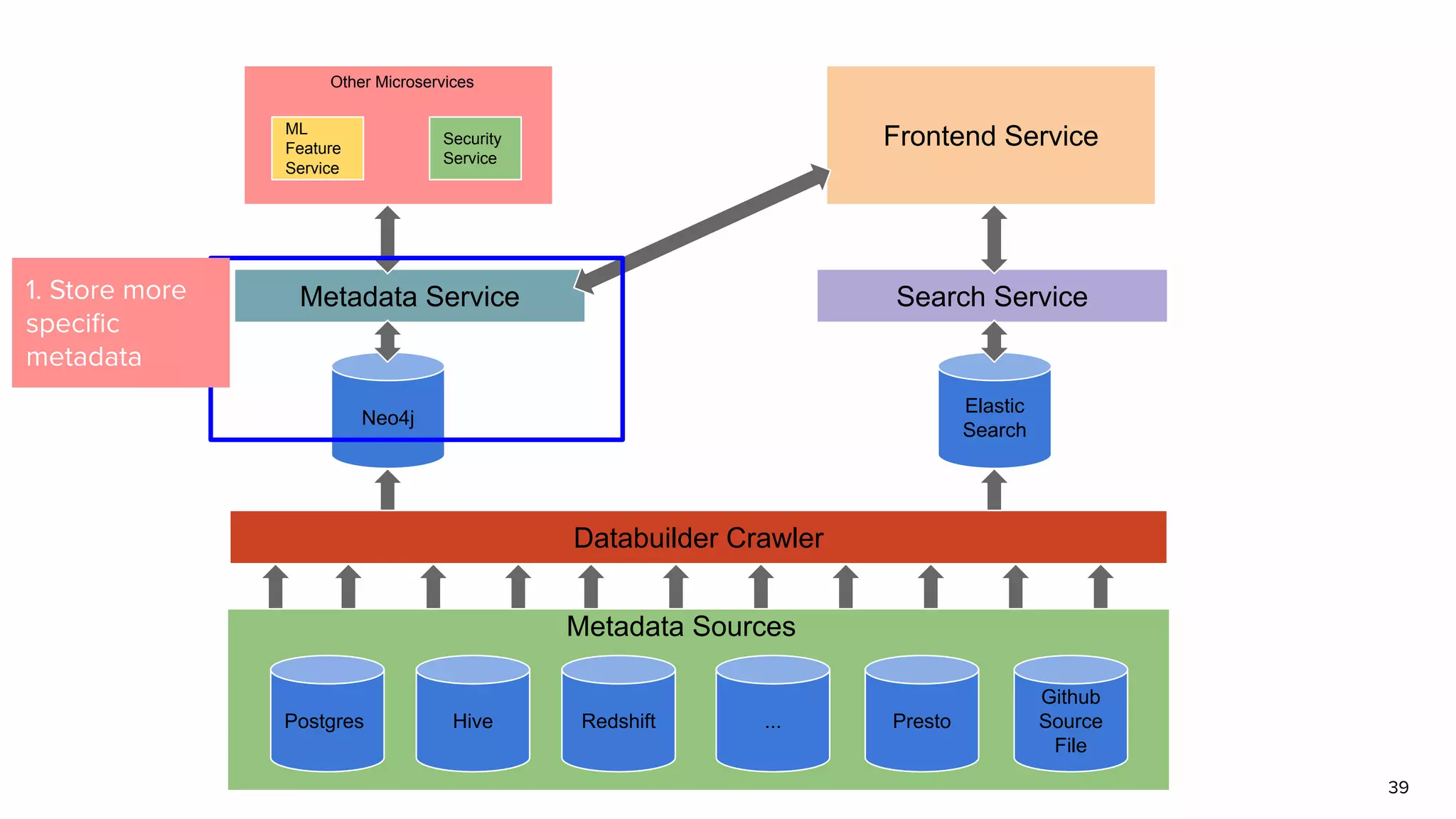
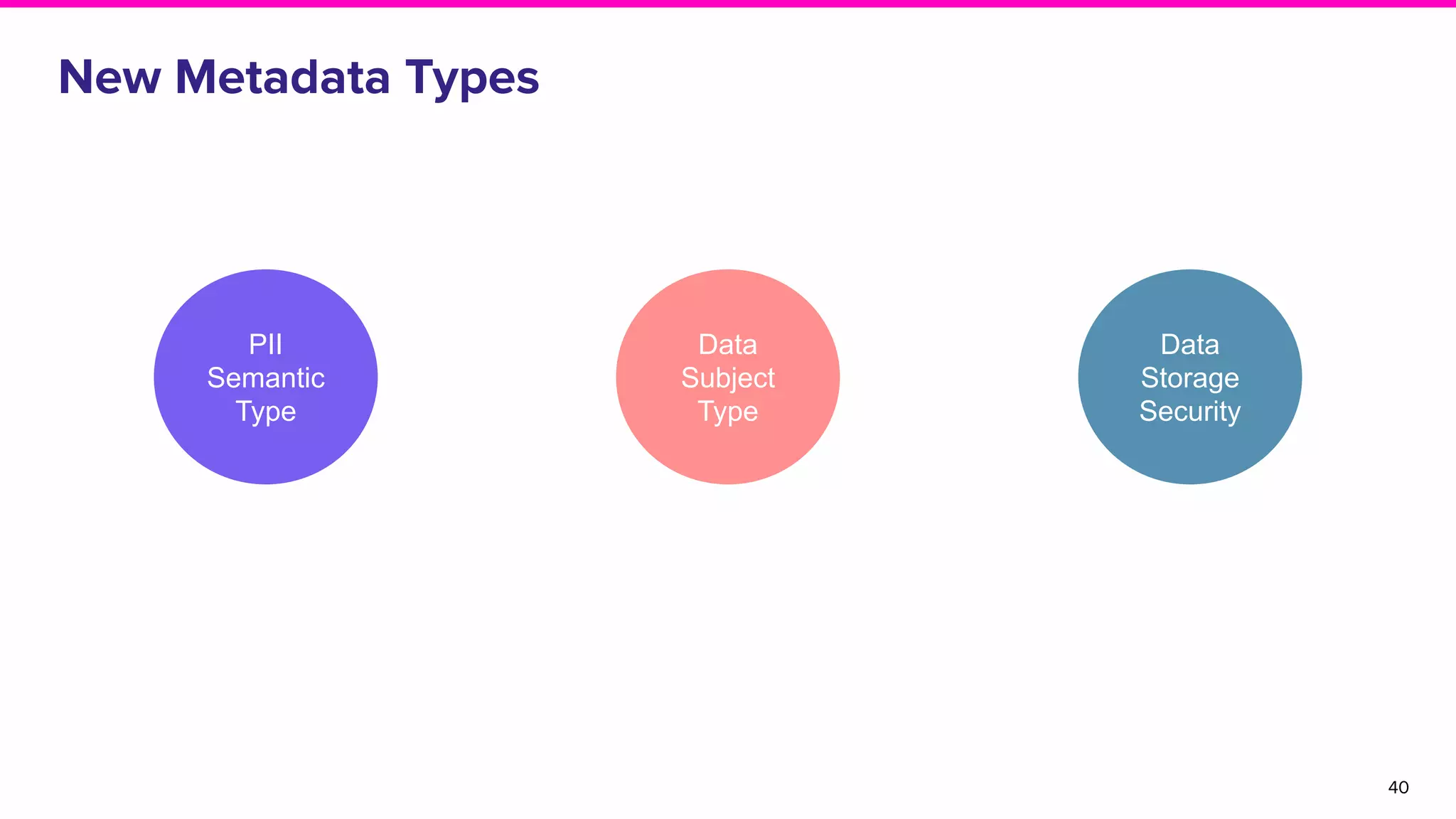
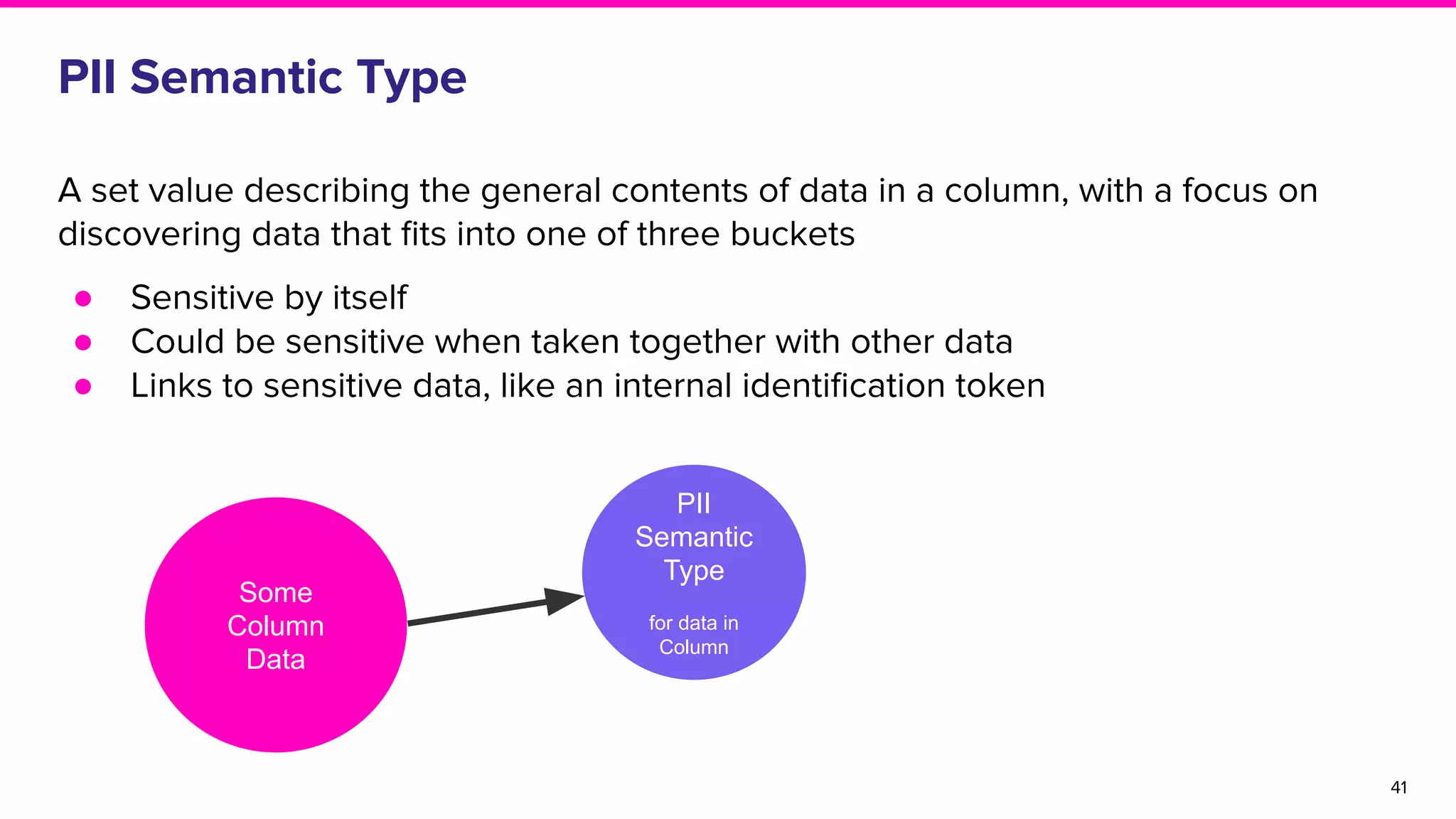
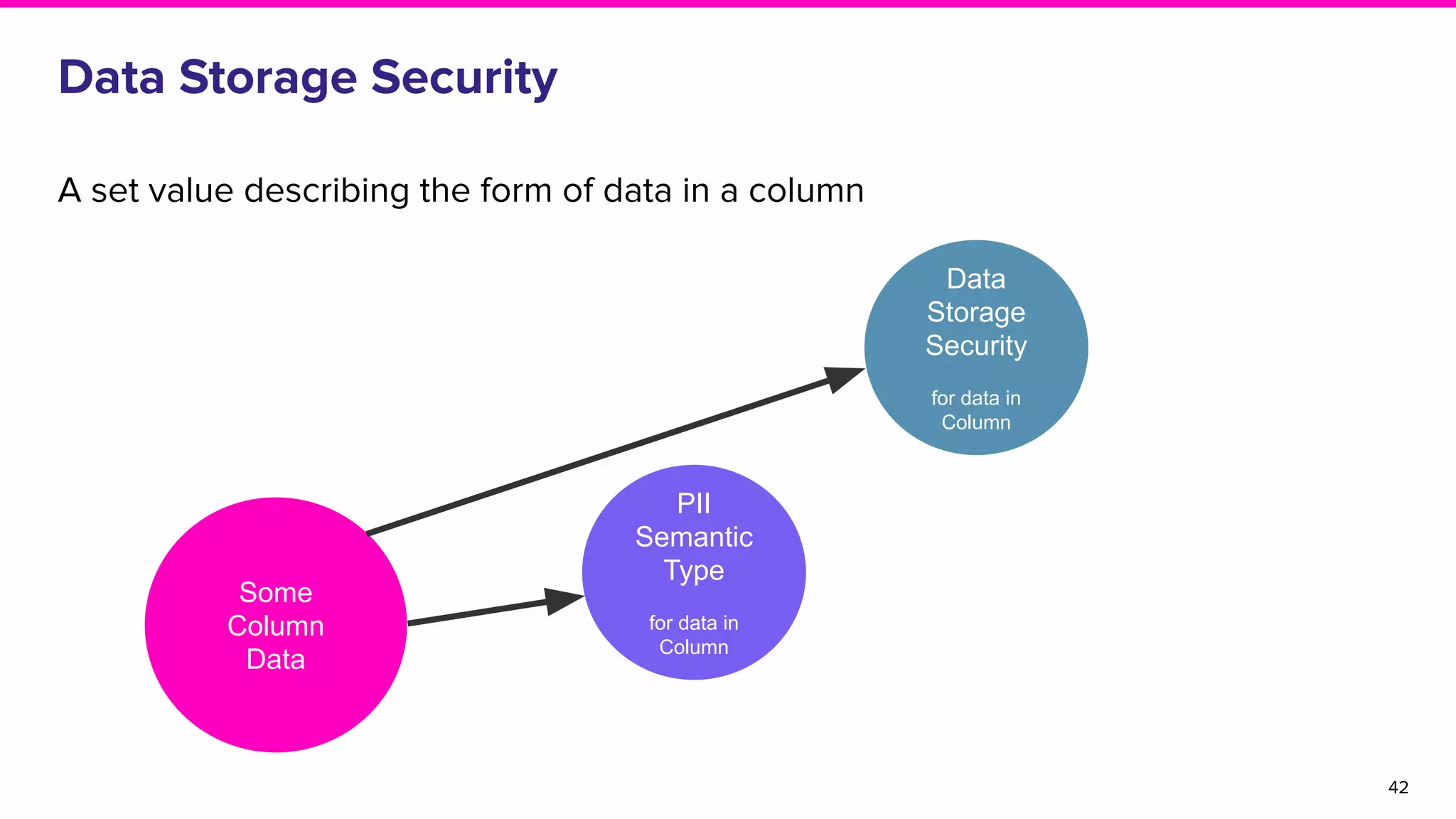
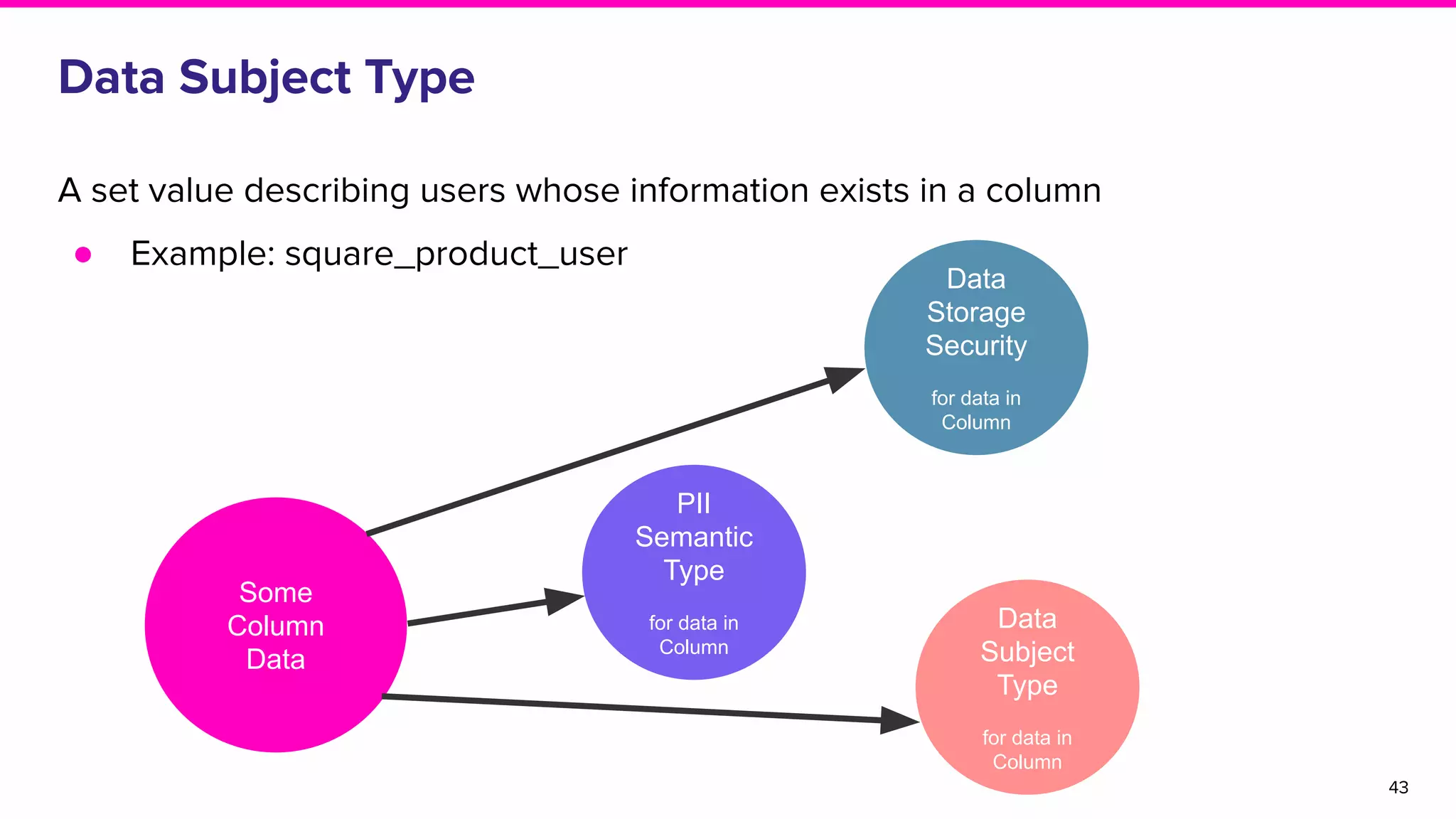
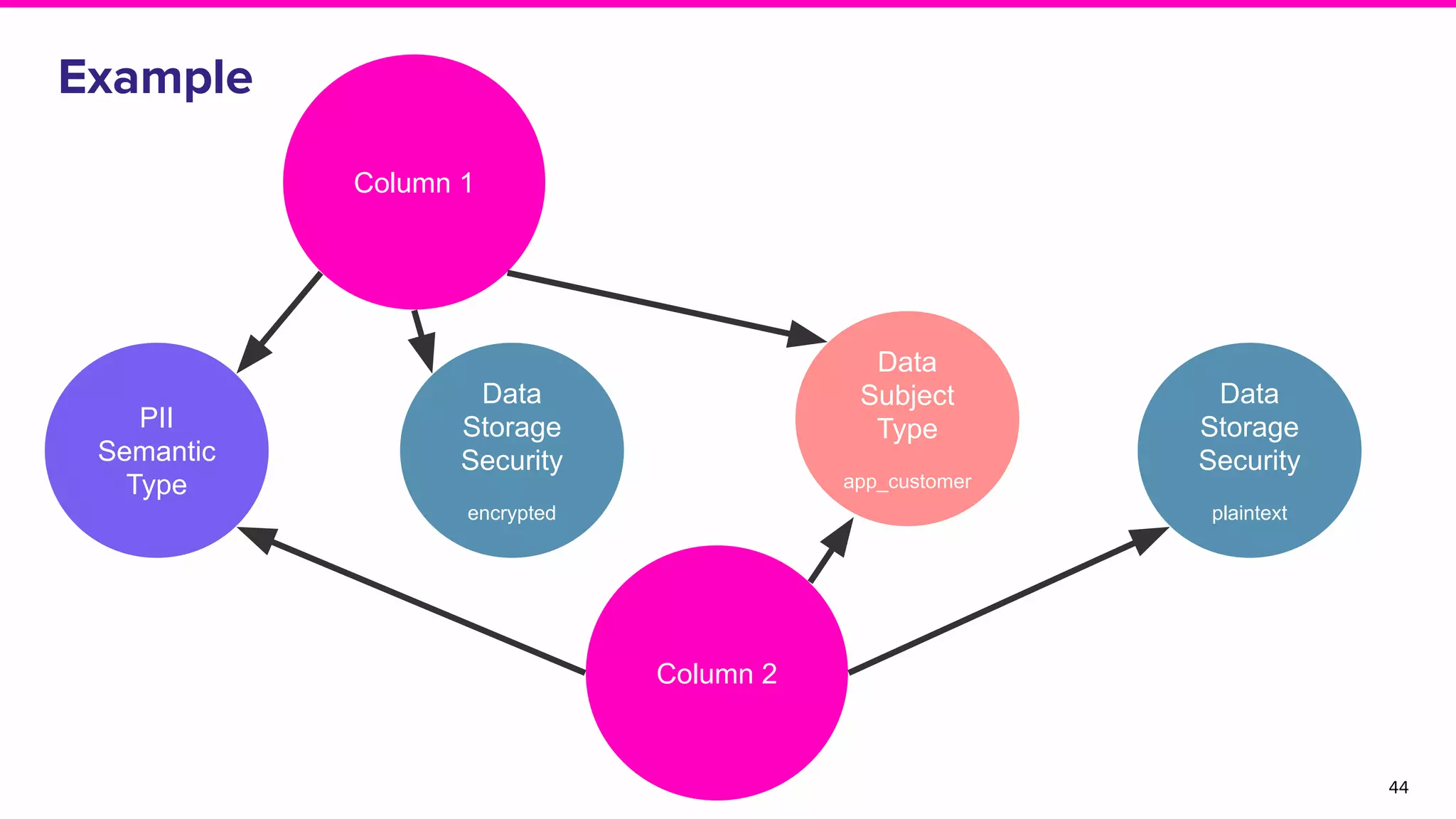
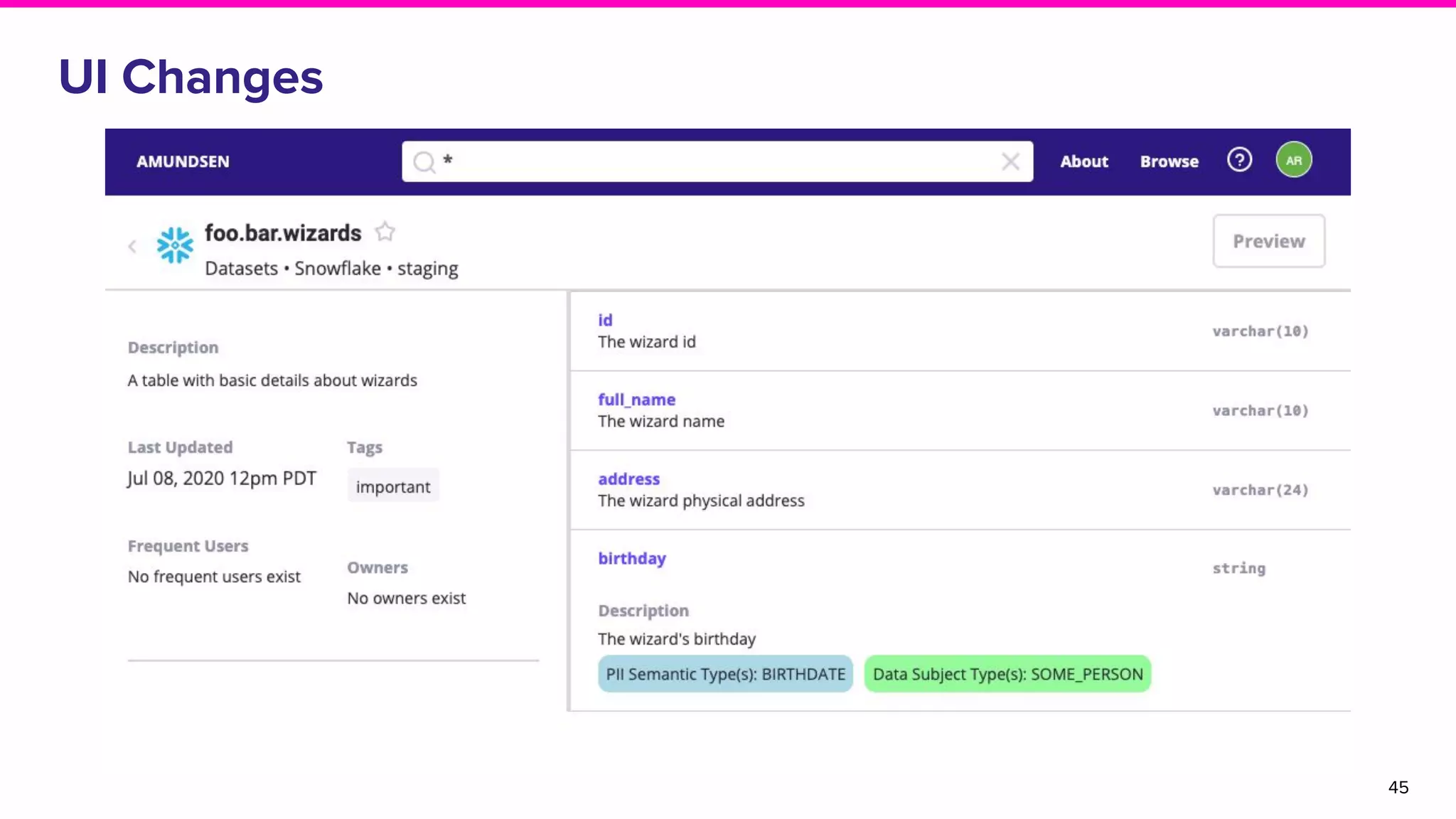
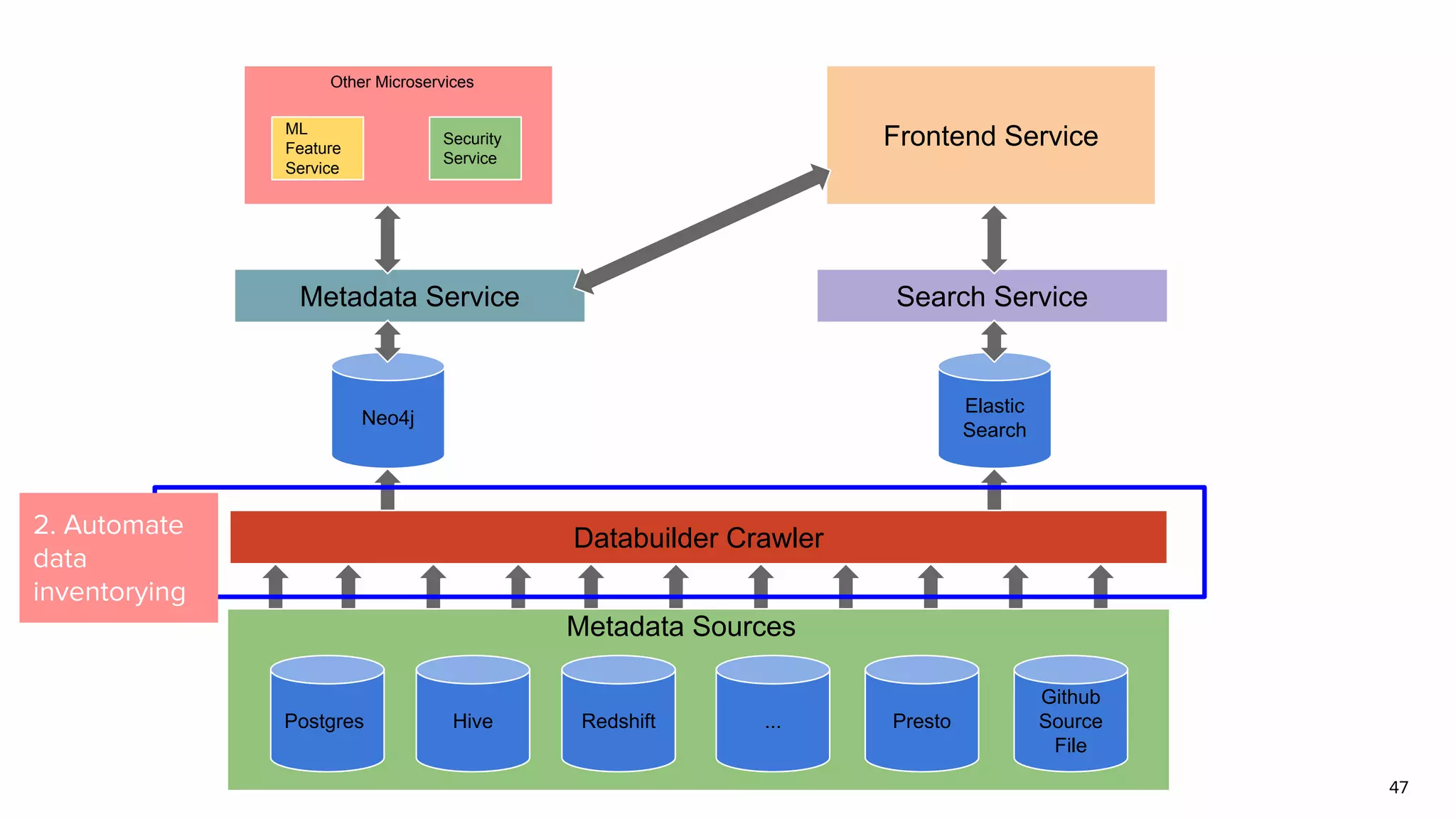
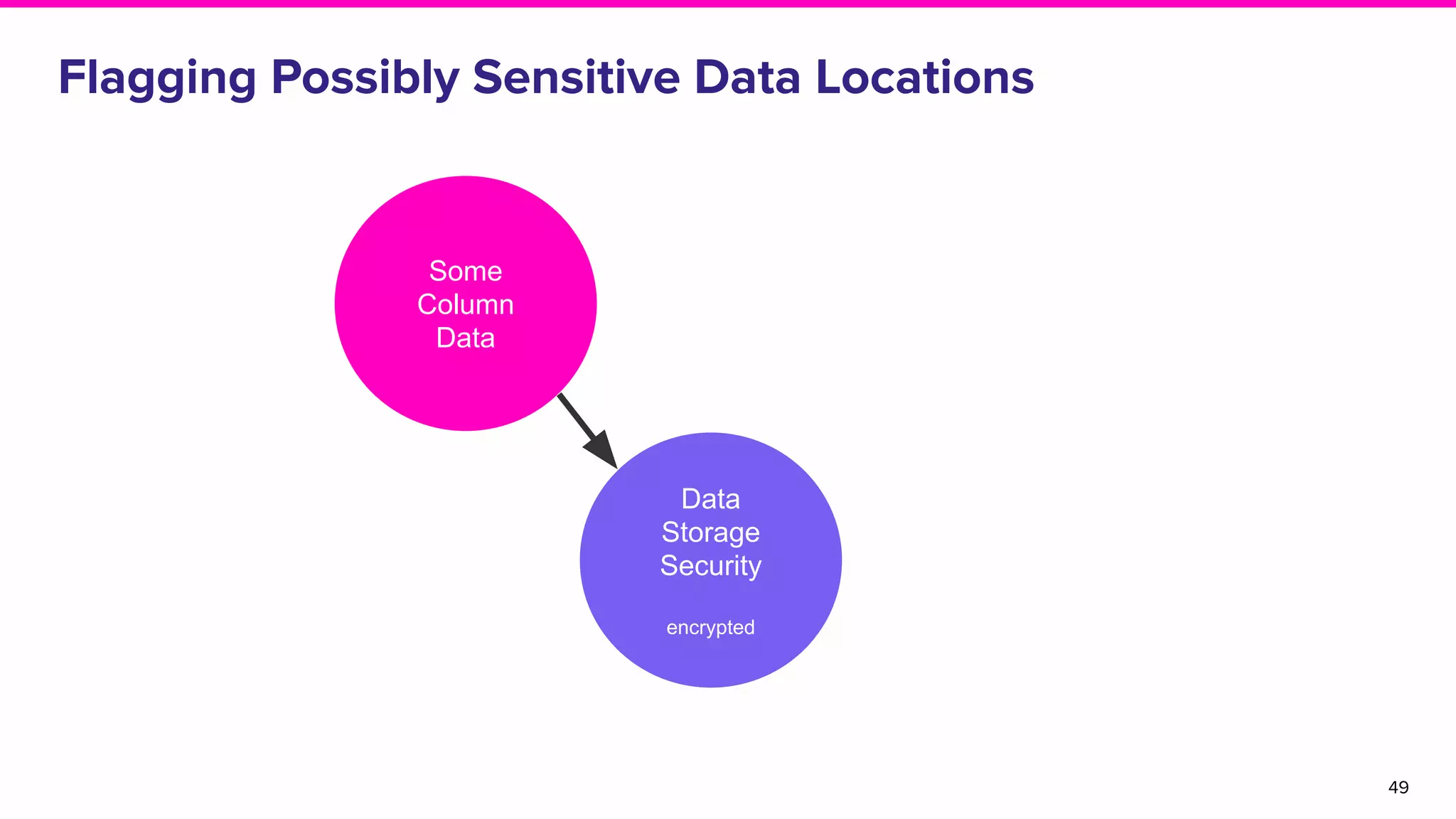
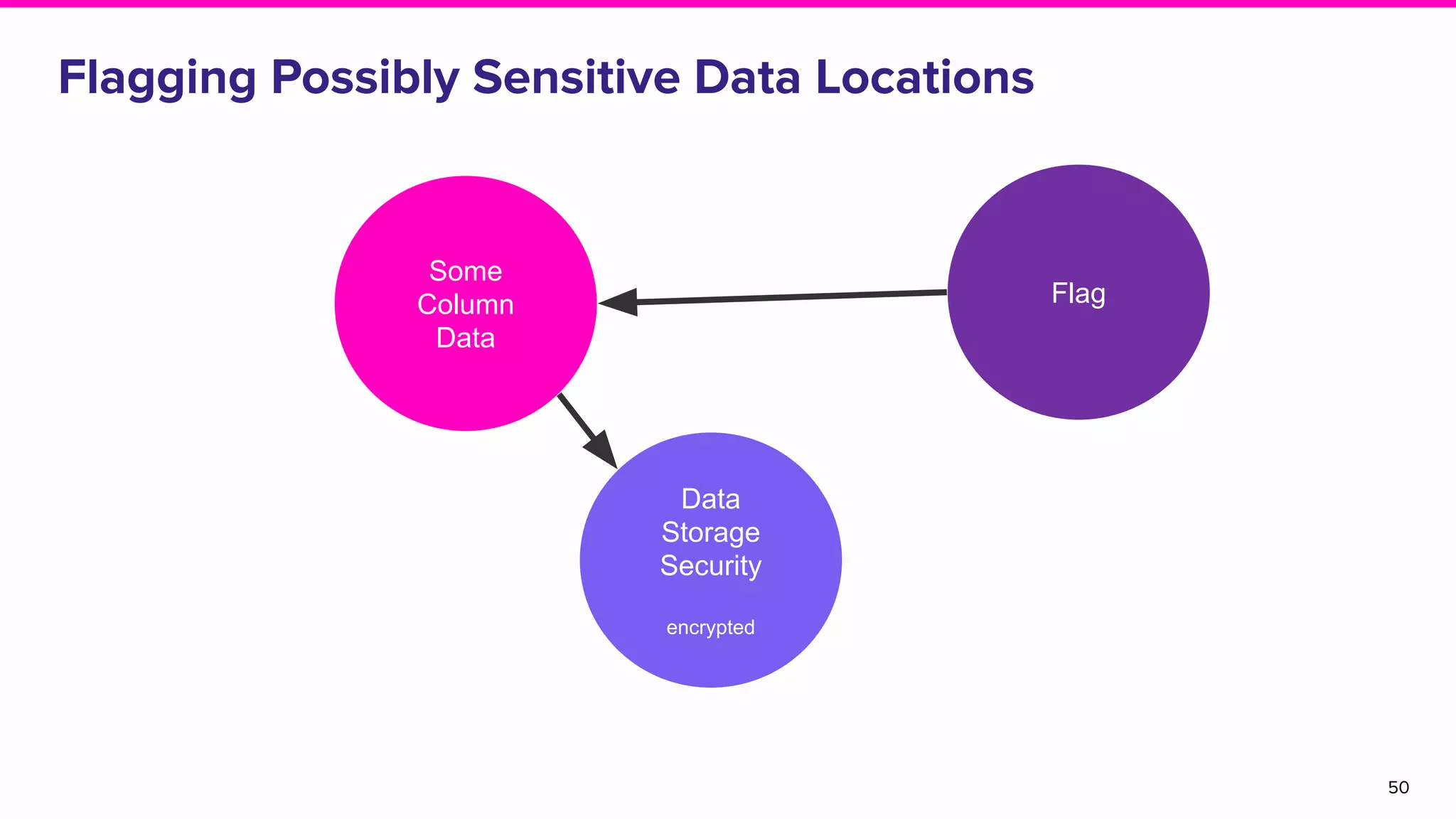
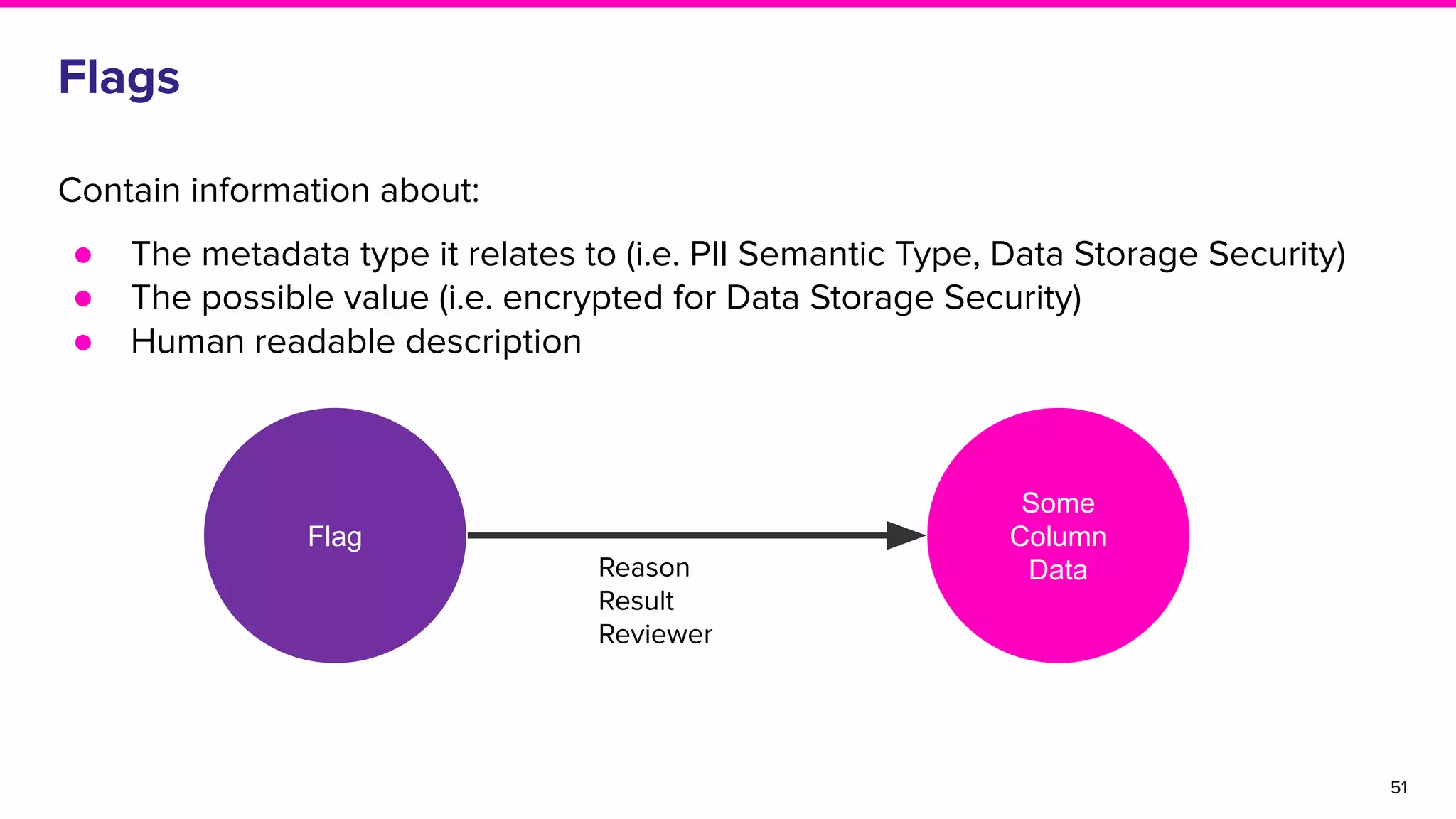
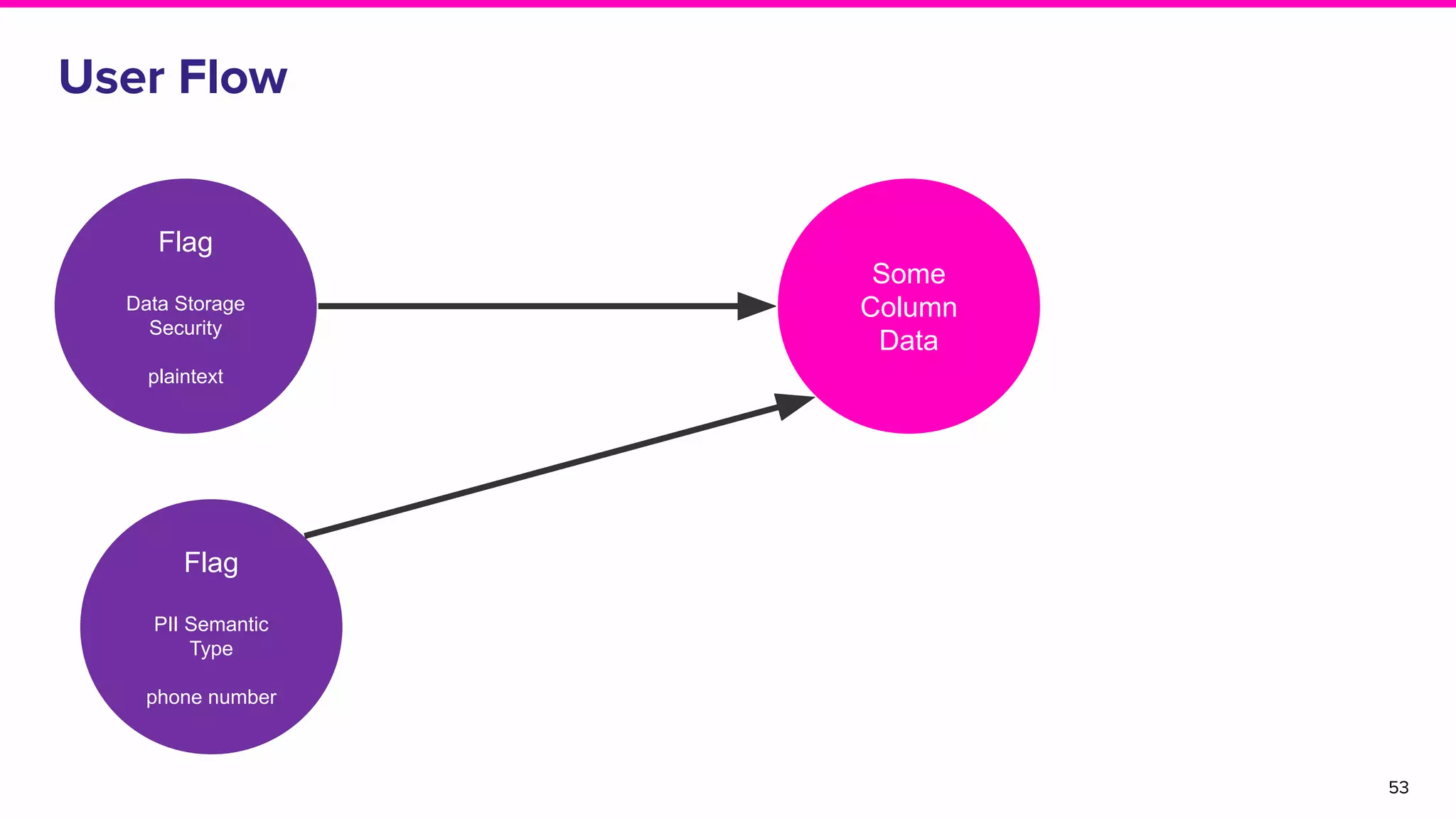
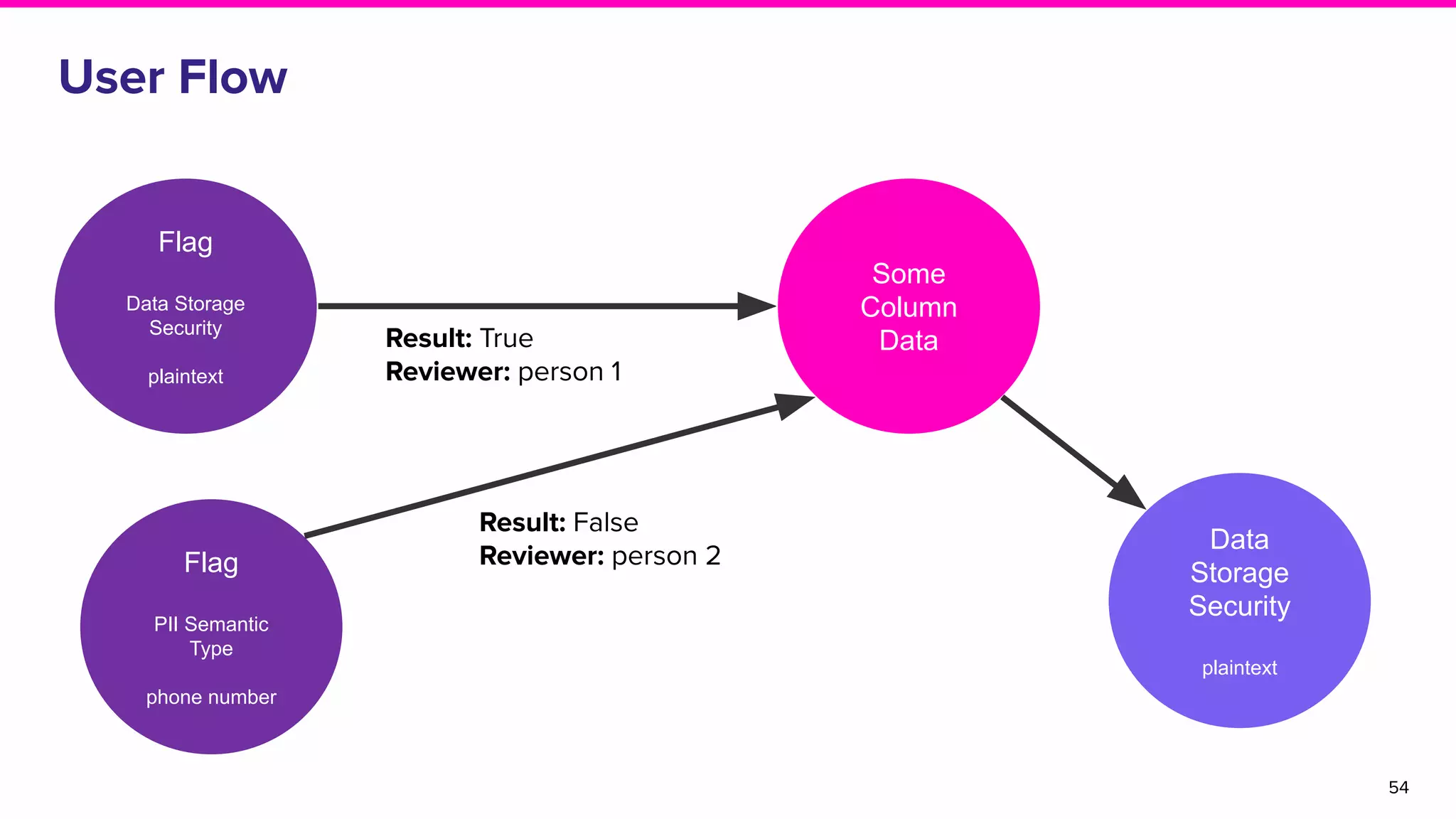
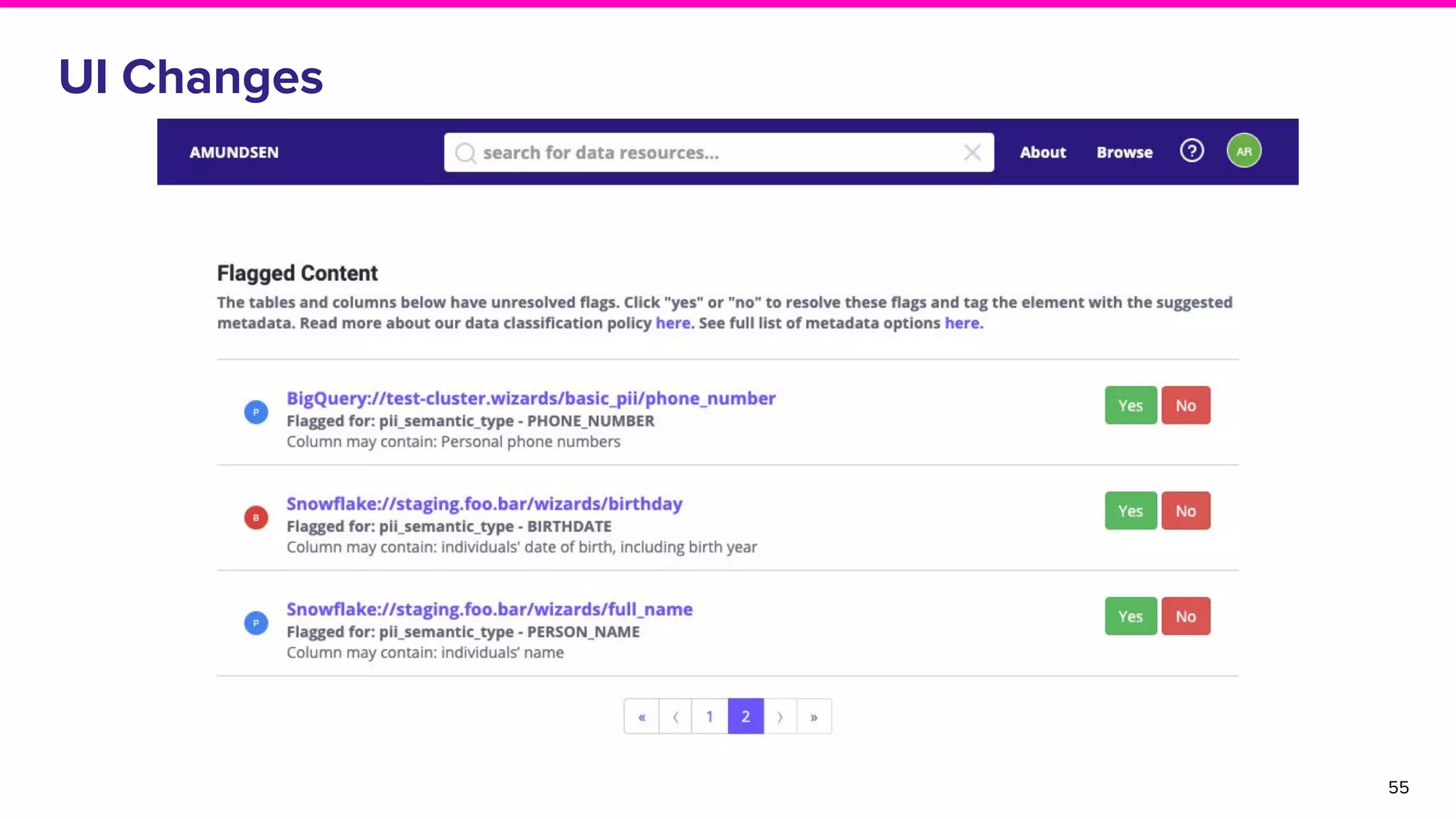
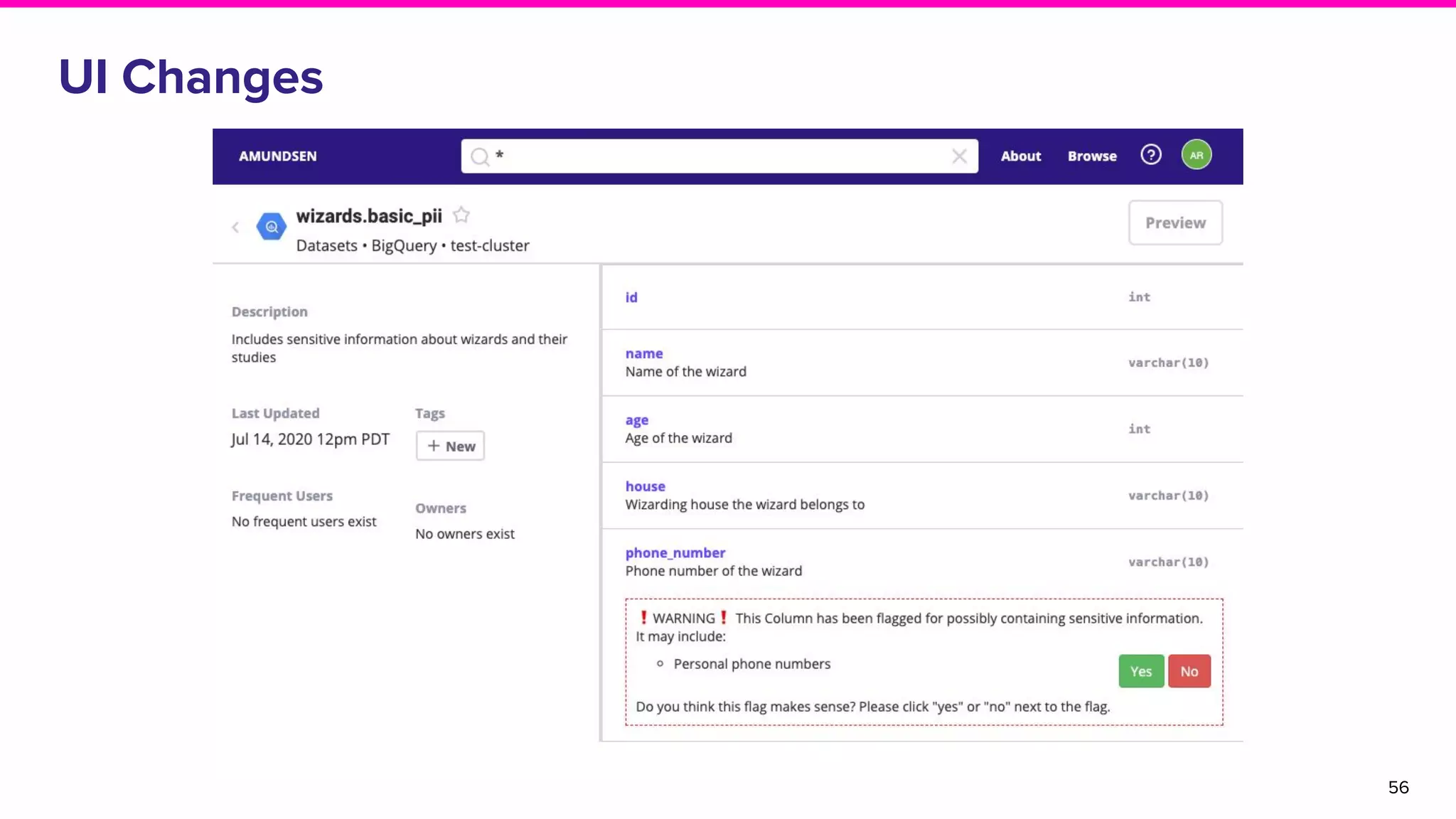
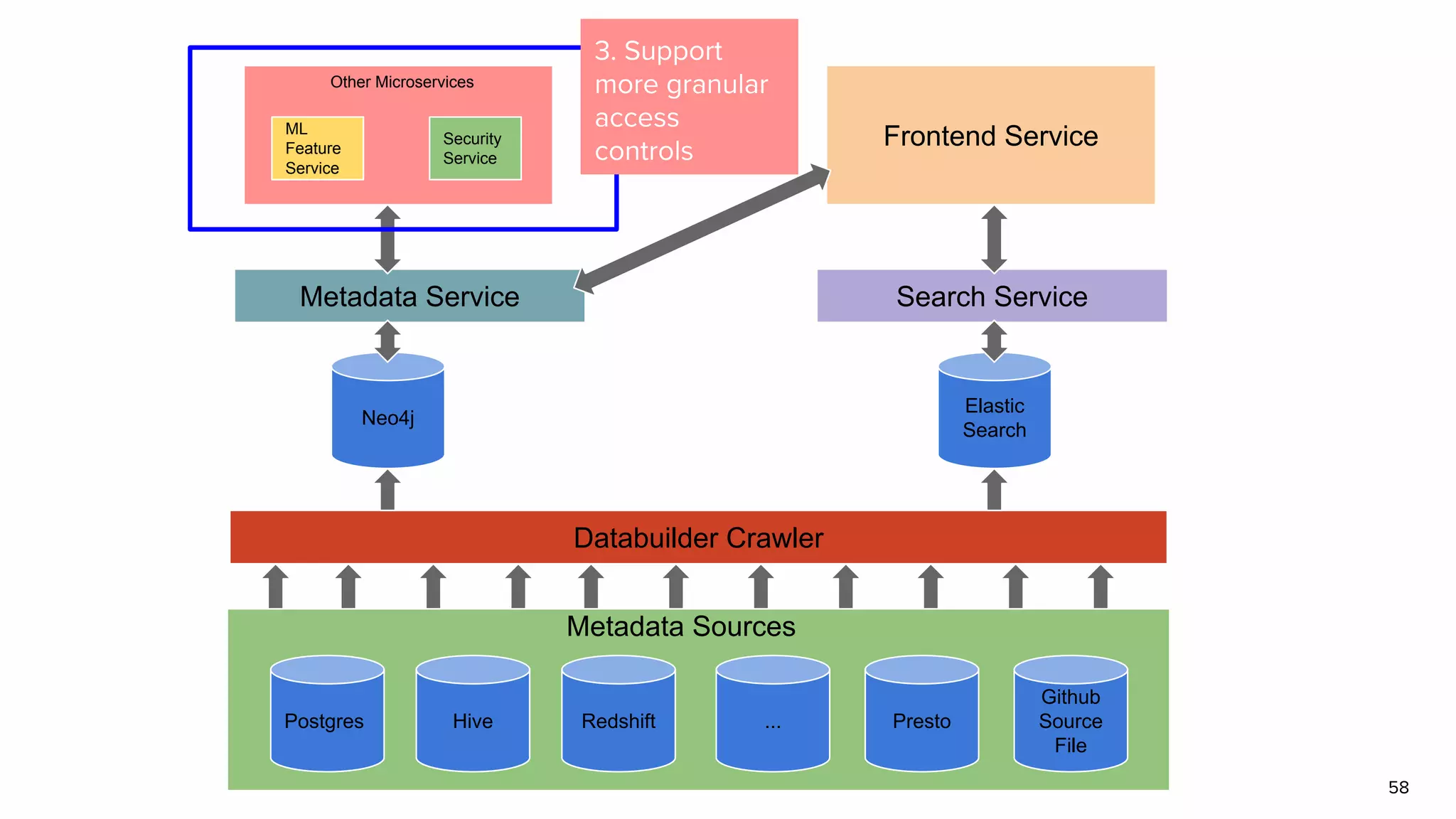
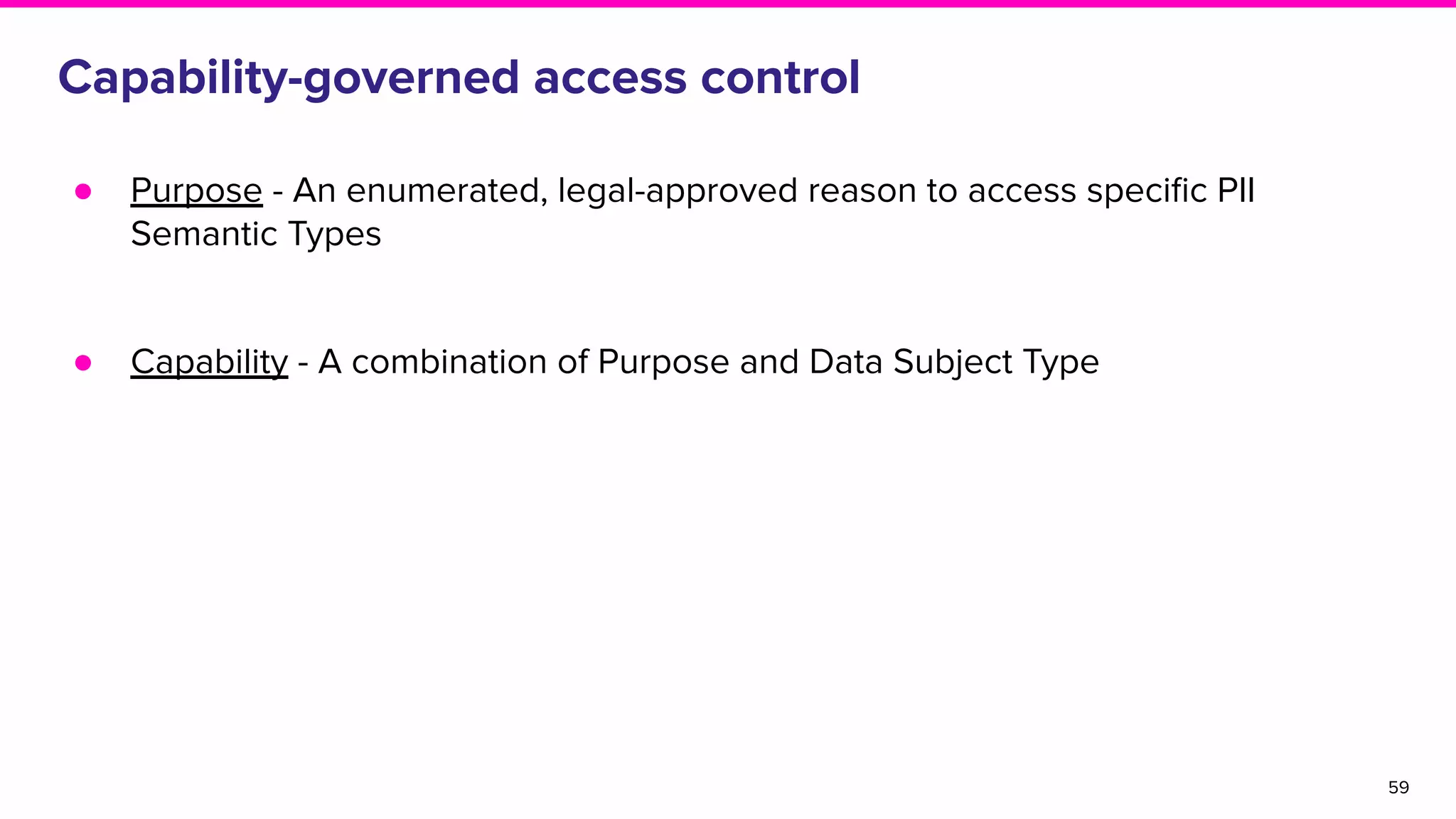
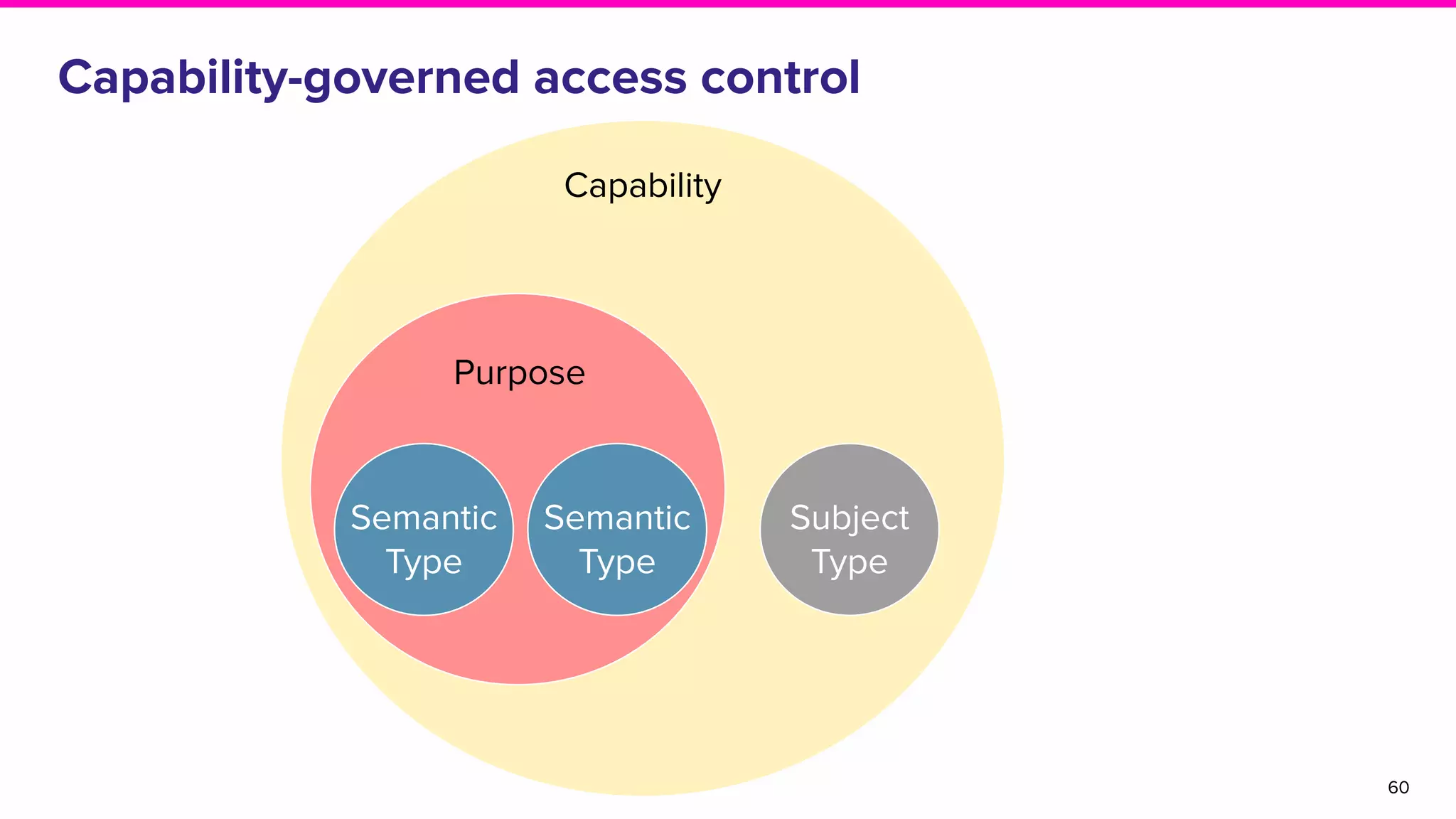
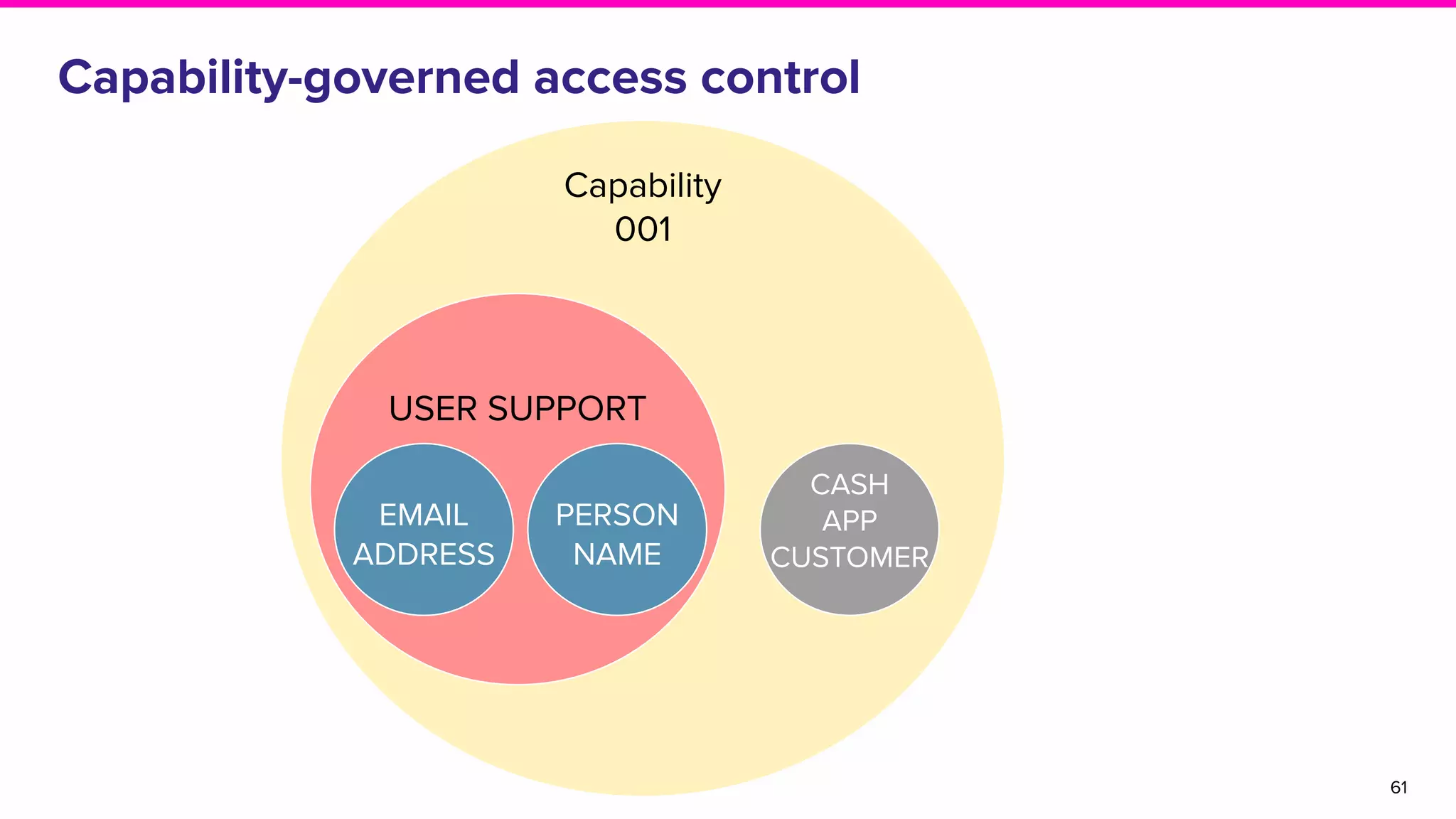
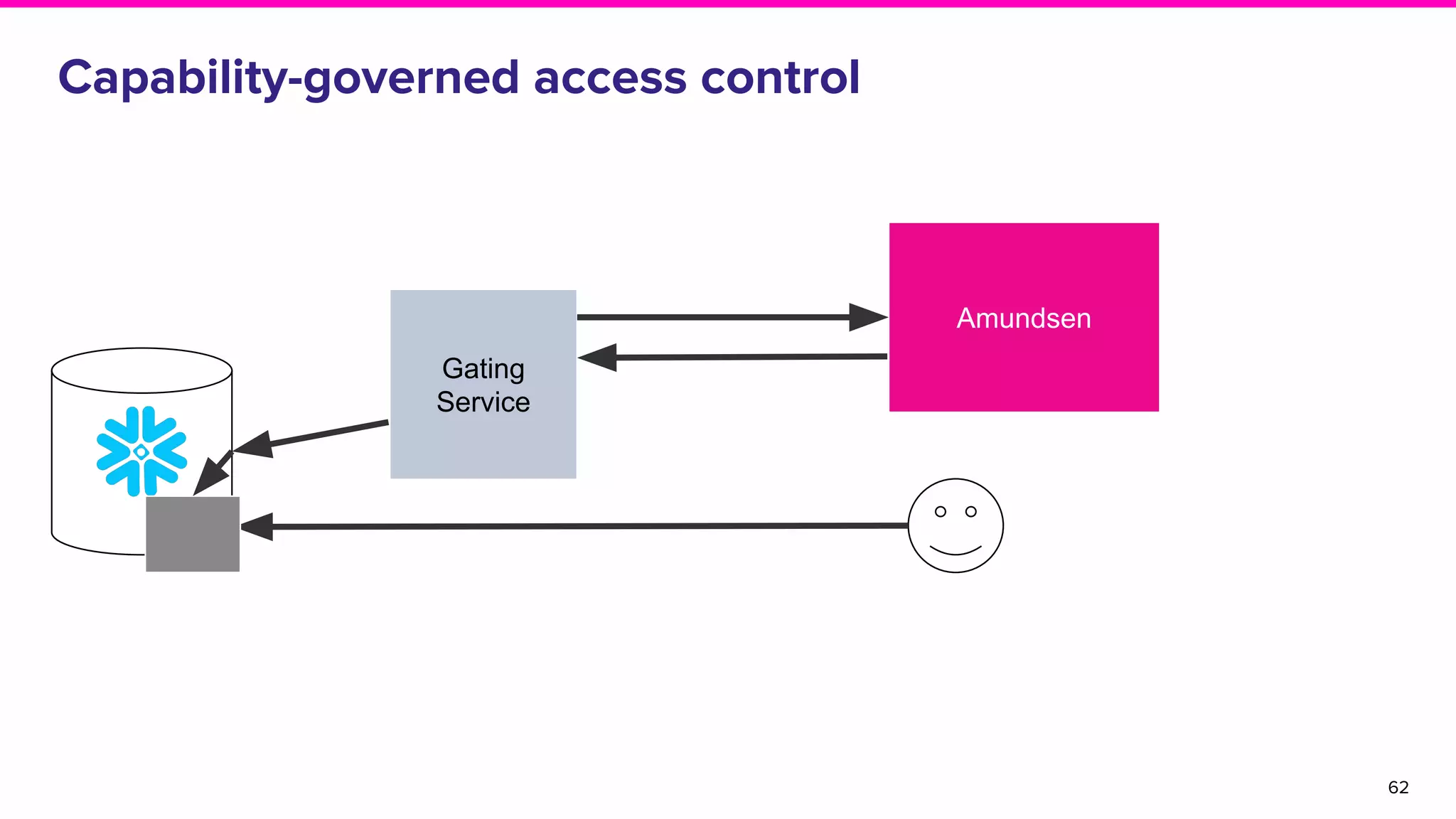
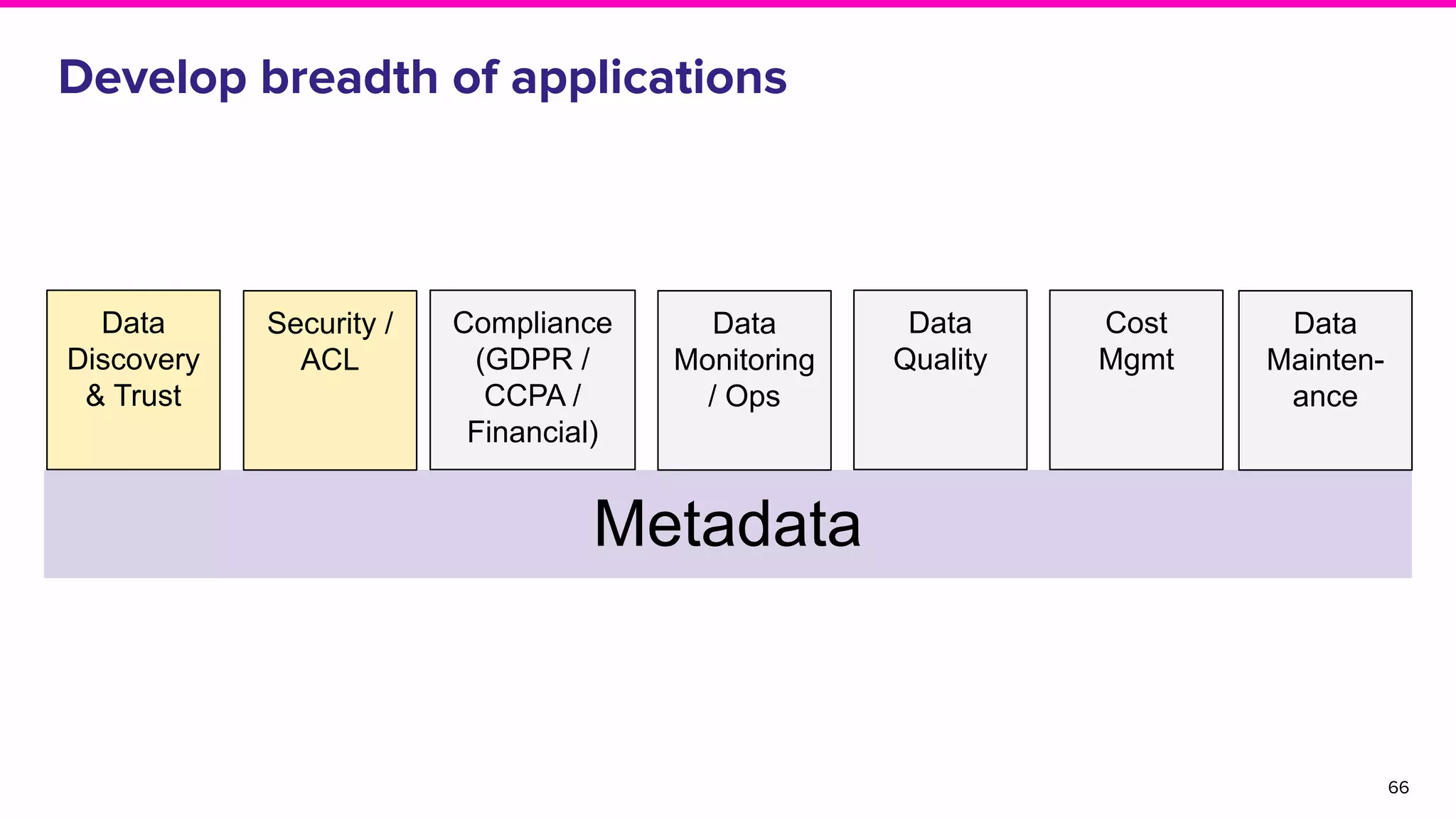
The document discusses Amundsen, a data discovery and metadata management tool designed to enhance data trustworthiness and accessibility. It highlights the challenges organizations face in managing and finding trustworthy data, such as heavy user interruptions and increased database load, while outlining the tool's features and integration with existing systems. Amundsen aims to automate data inventorying, improve metadata management, and support access controls, with a growing community and user adoption at companies like Lyft and Square.