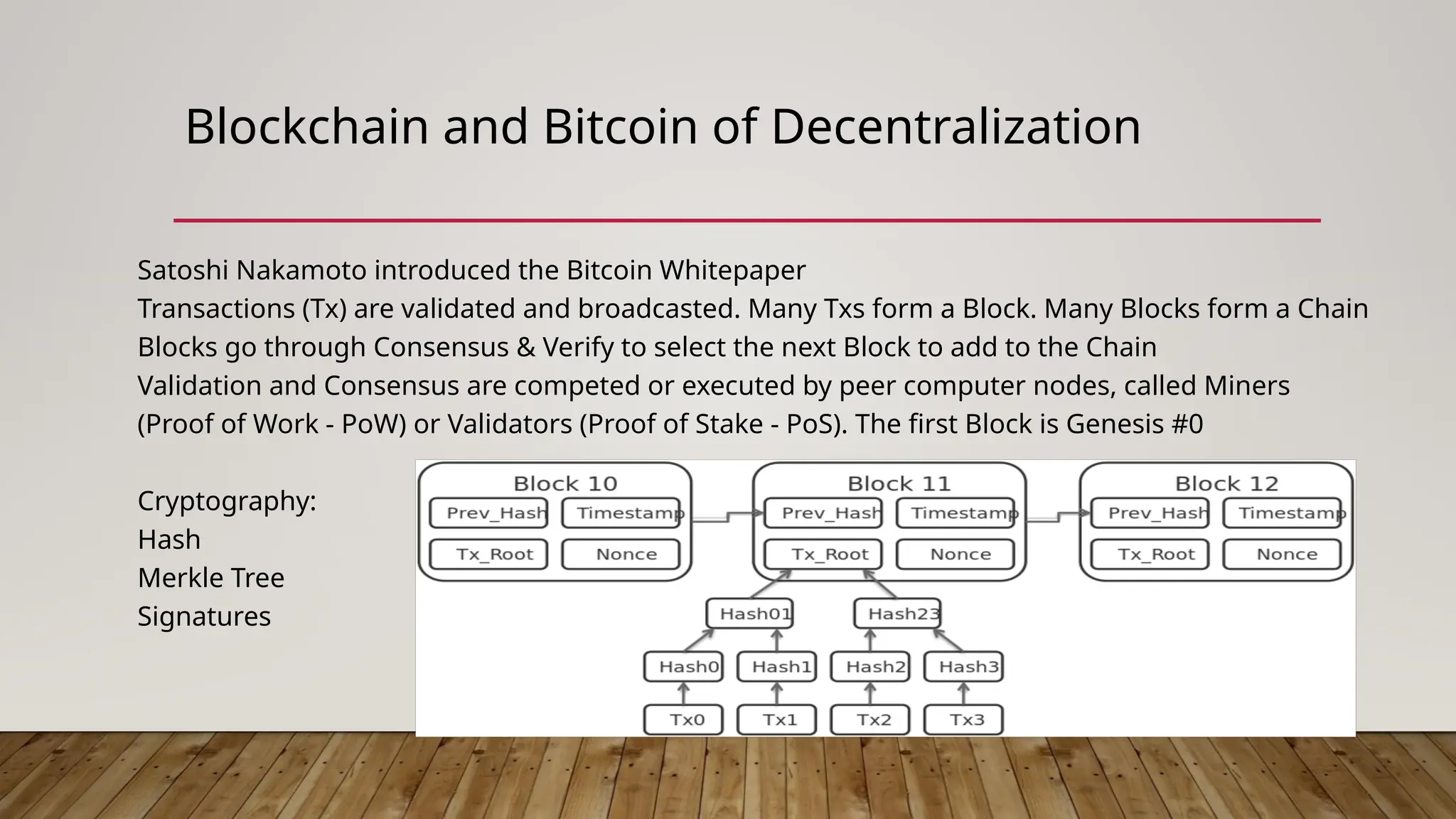
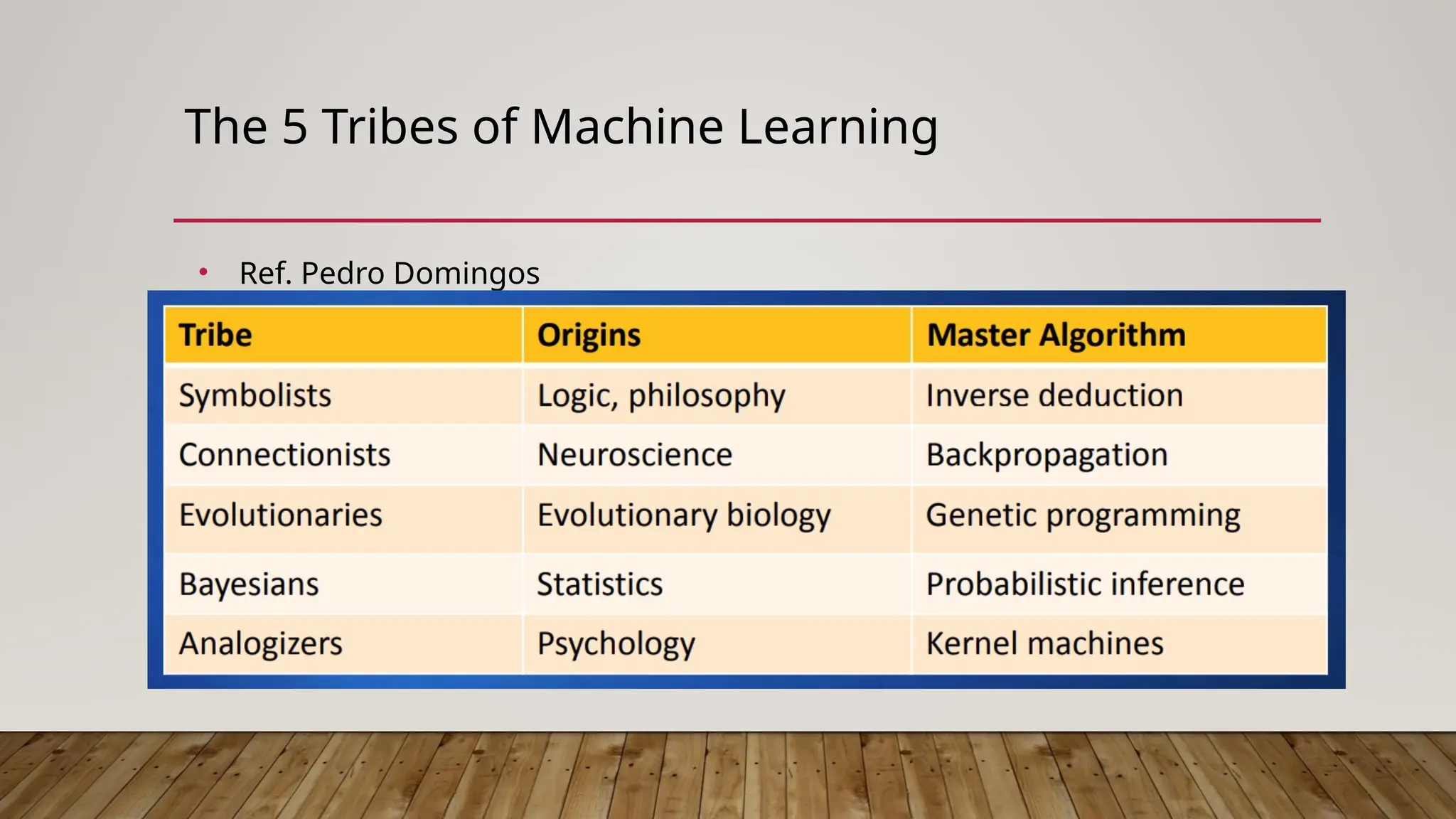
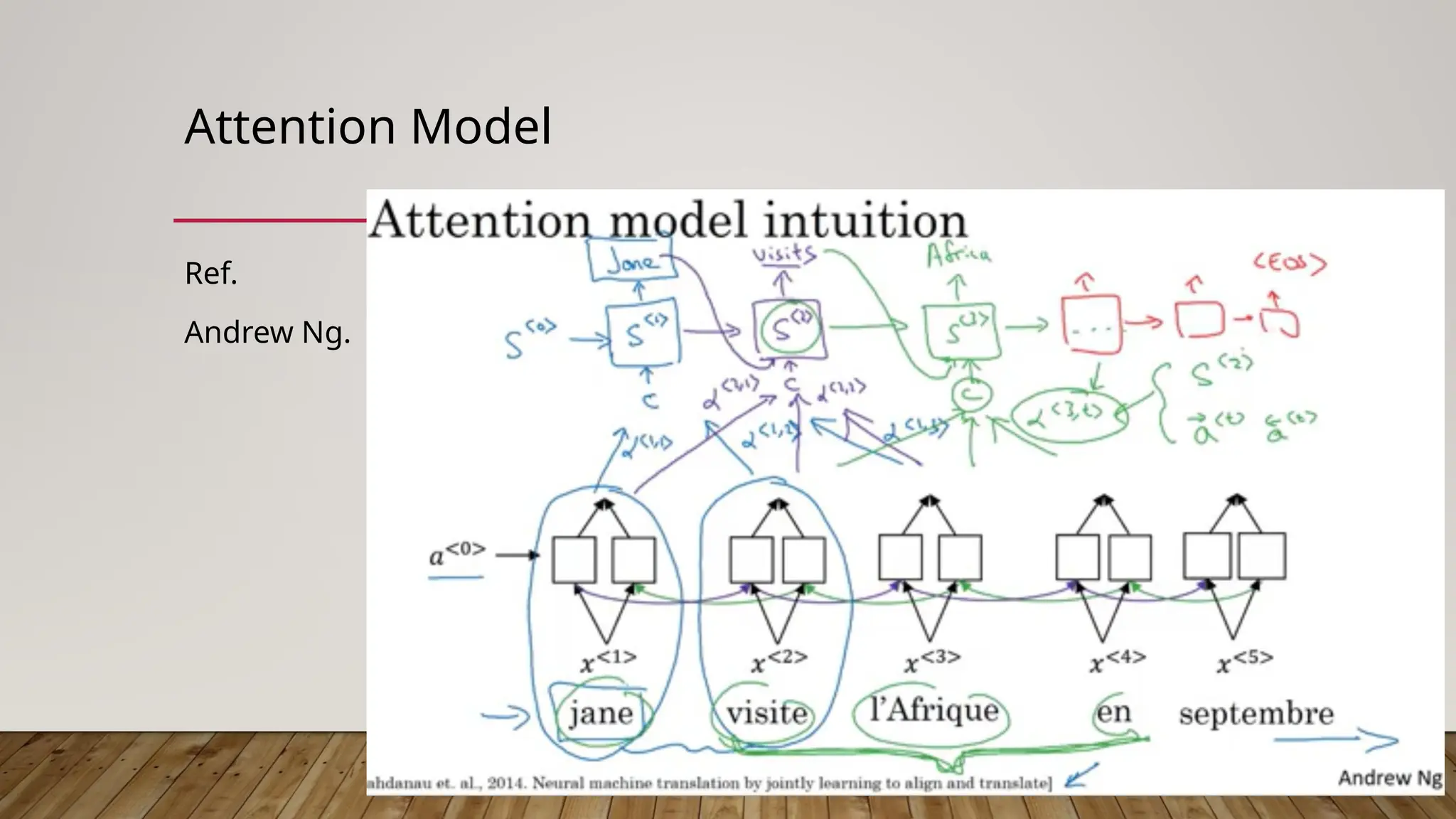
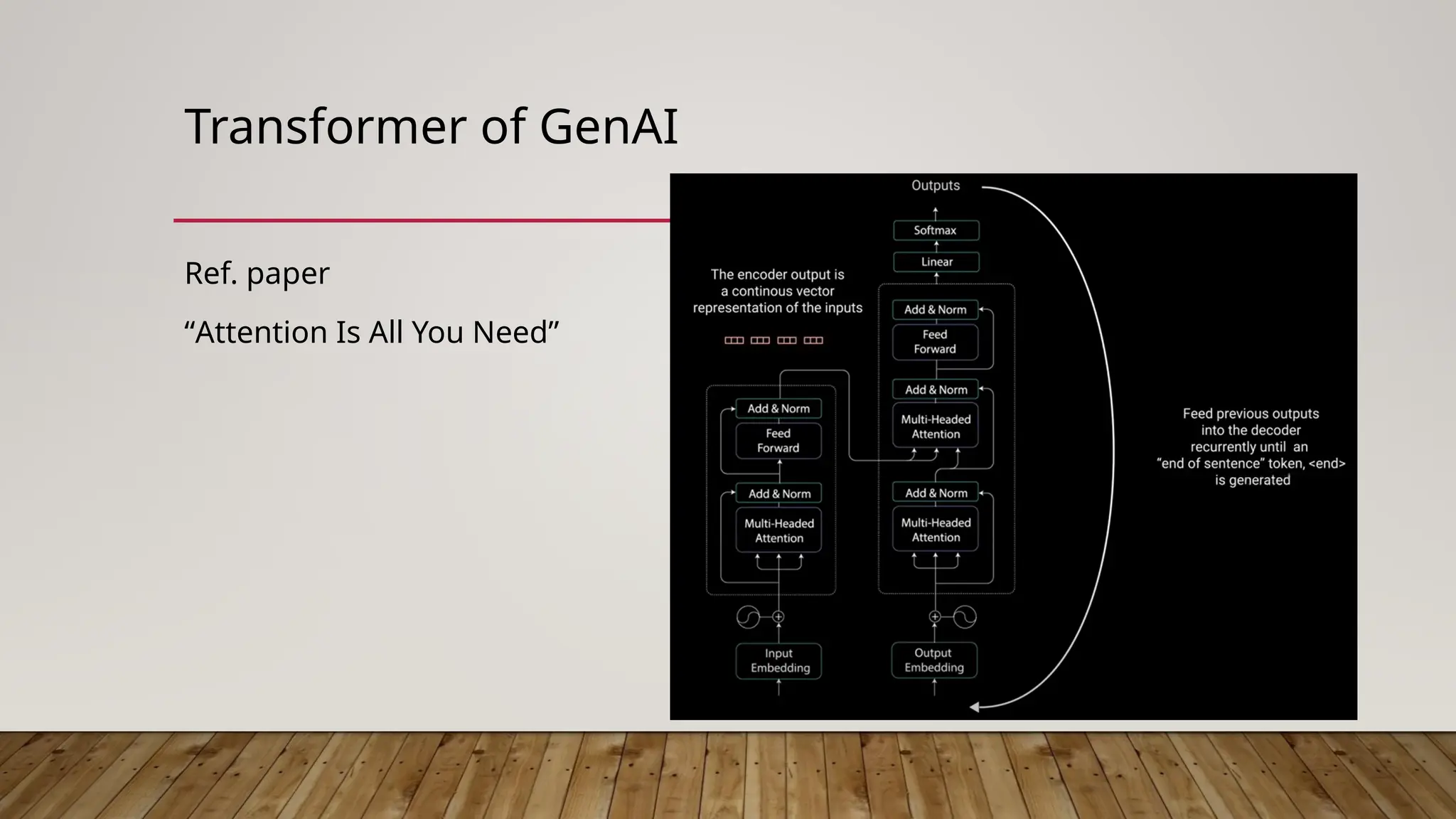
The document discusses the intersection of information security, blockchain technology, and artificial intelligence (AI) in the context of web3, highlighting key principles such as confidentiality, integrity, and availability. It emphasizes the importance of decentralized systems in ensuring the security of digital assets and addresses challenges like the blockchain trilemma of decentralization, security, and scalability. Additionally, the document explores the role of zero-knowledge proofs (ZKP) in enhancing privacy within AI and machine learning models, while also noting potential risks associated with web3 technologies.