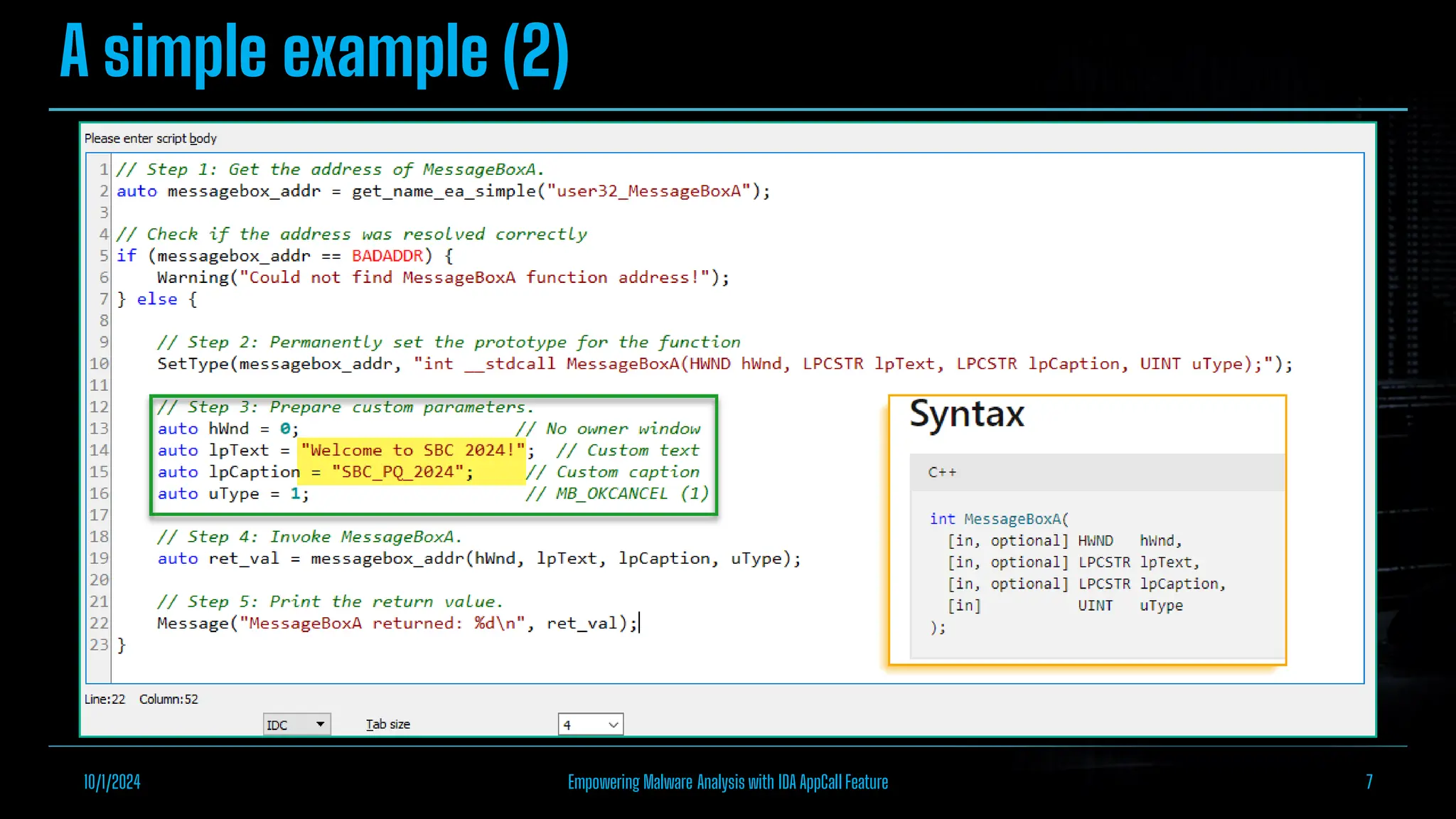
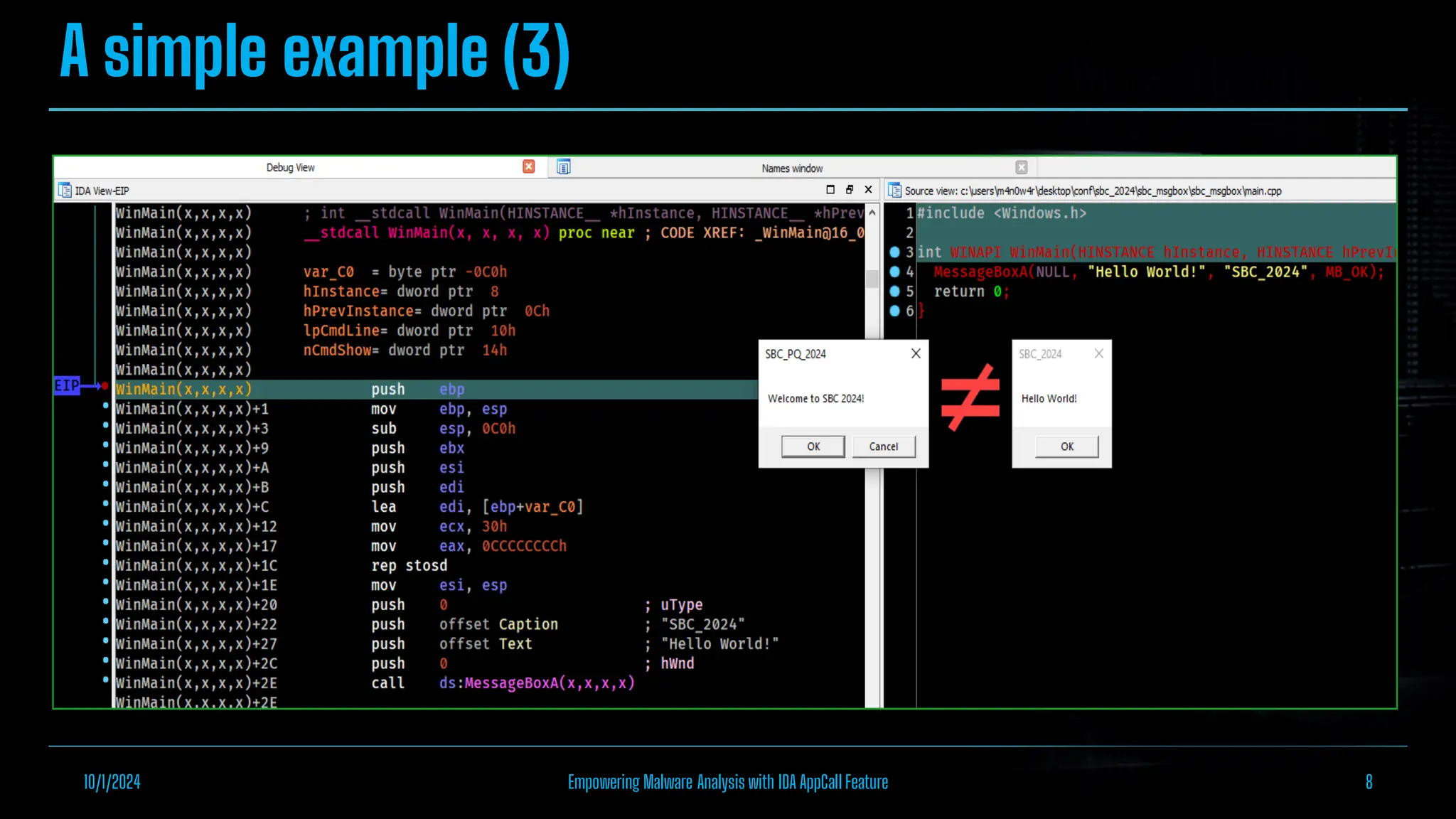
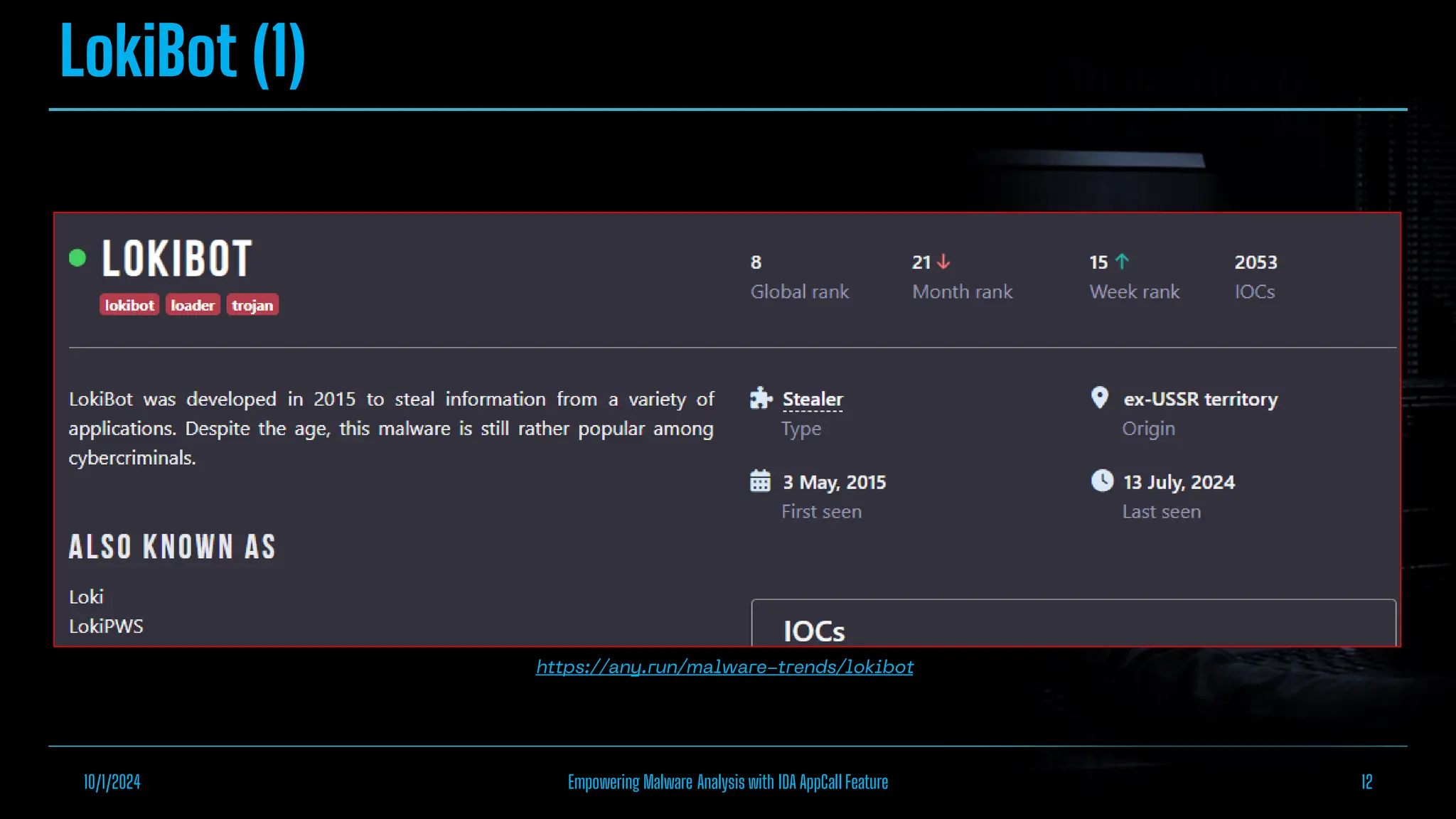
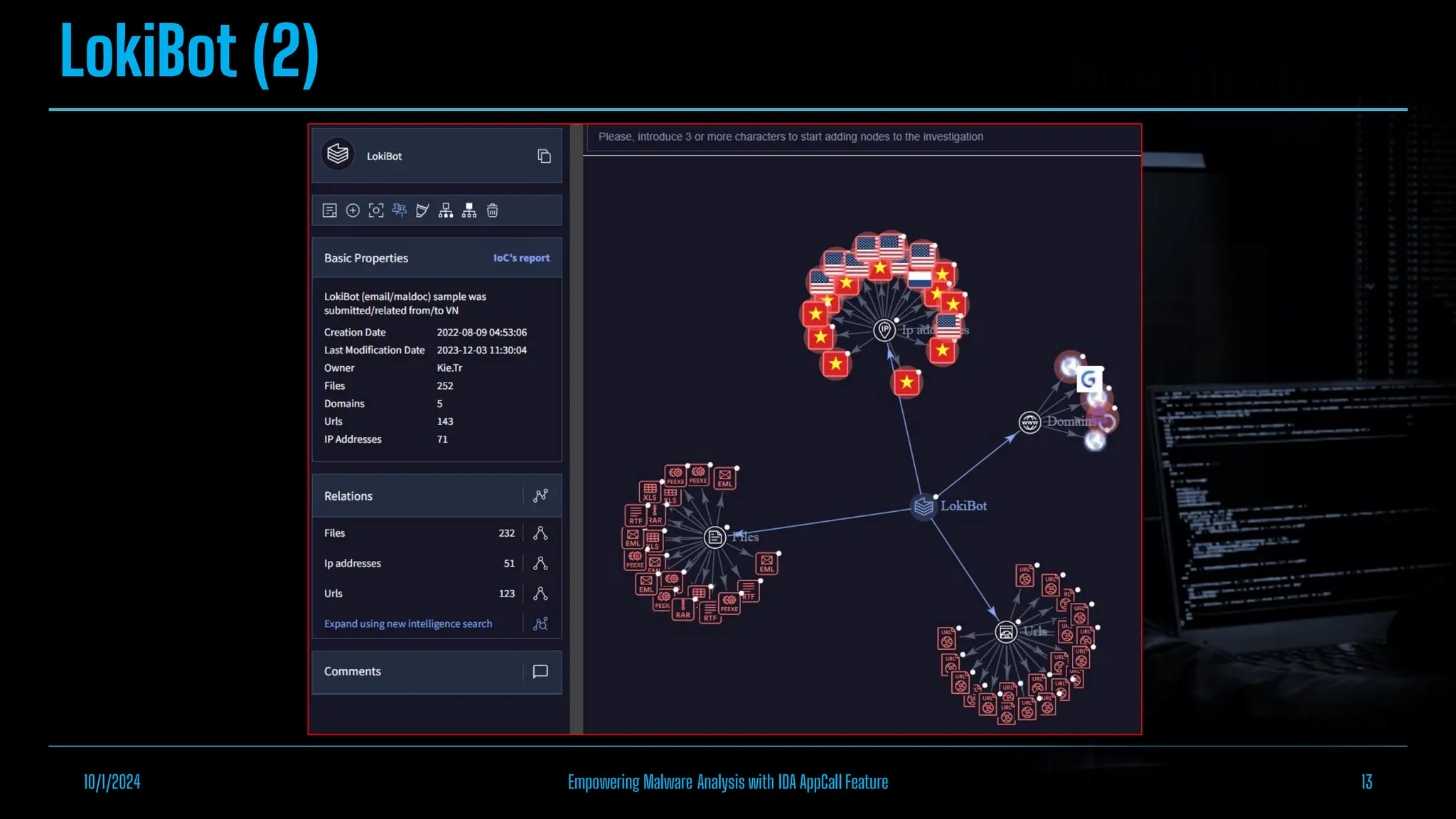
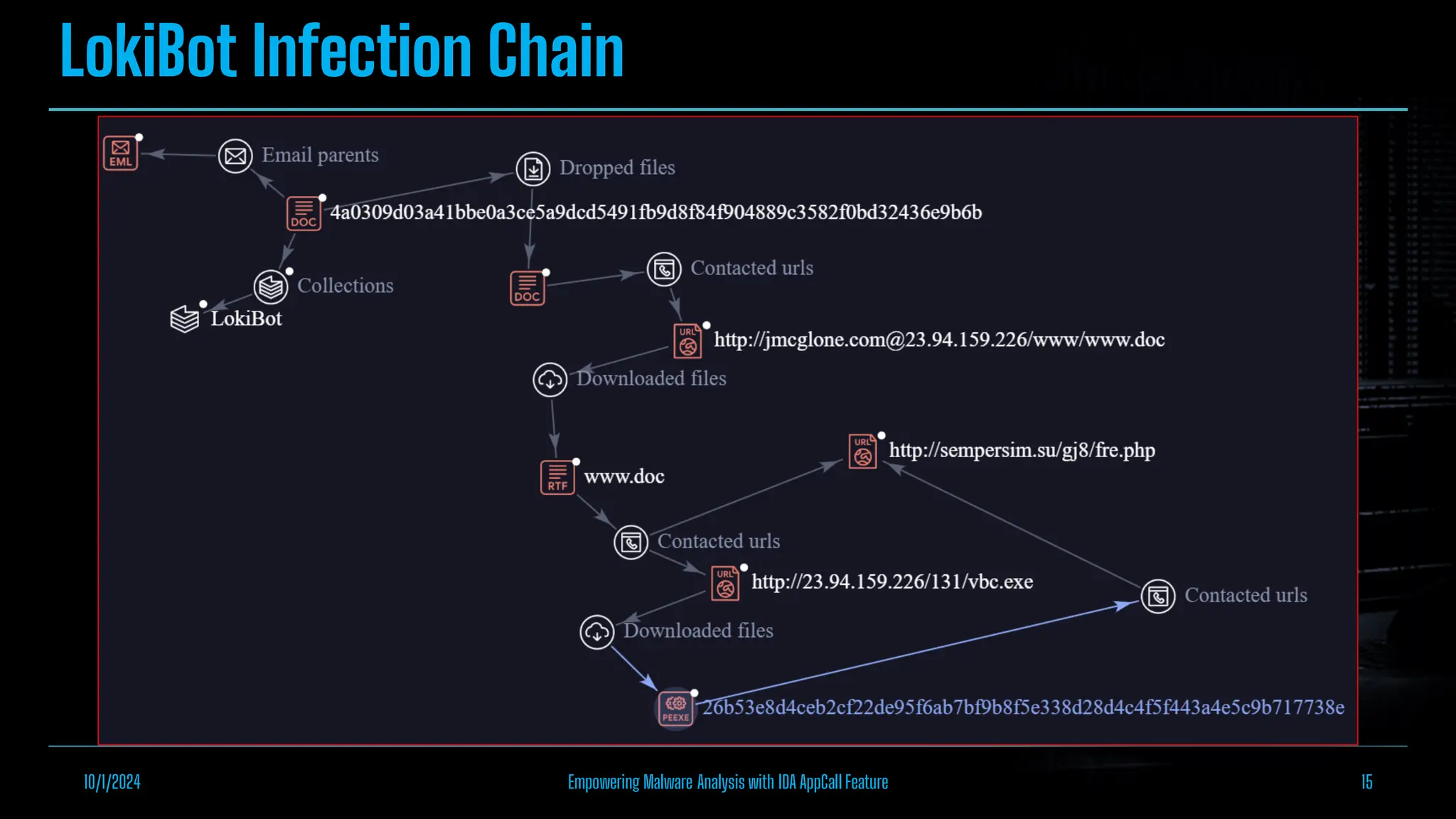
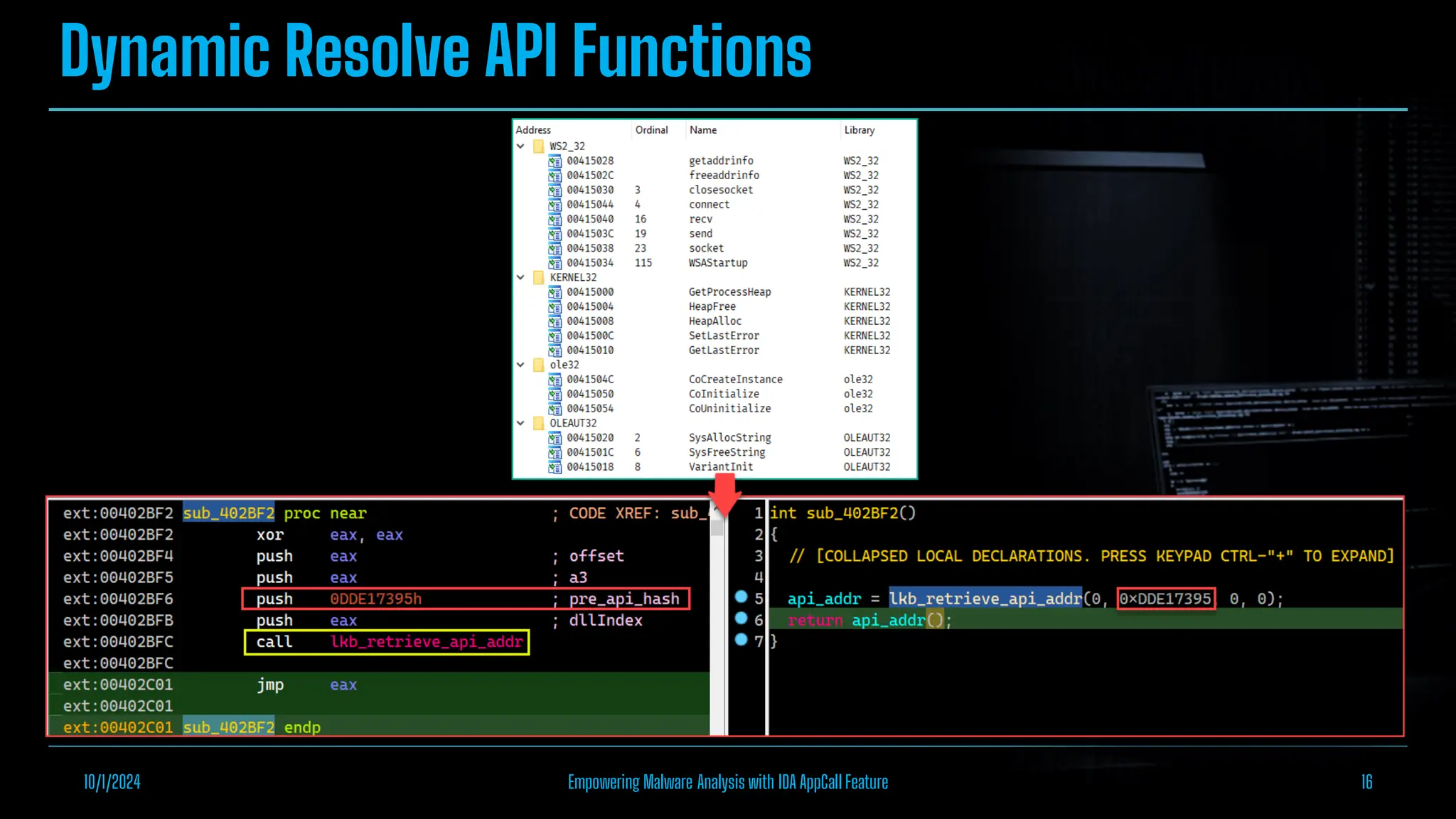
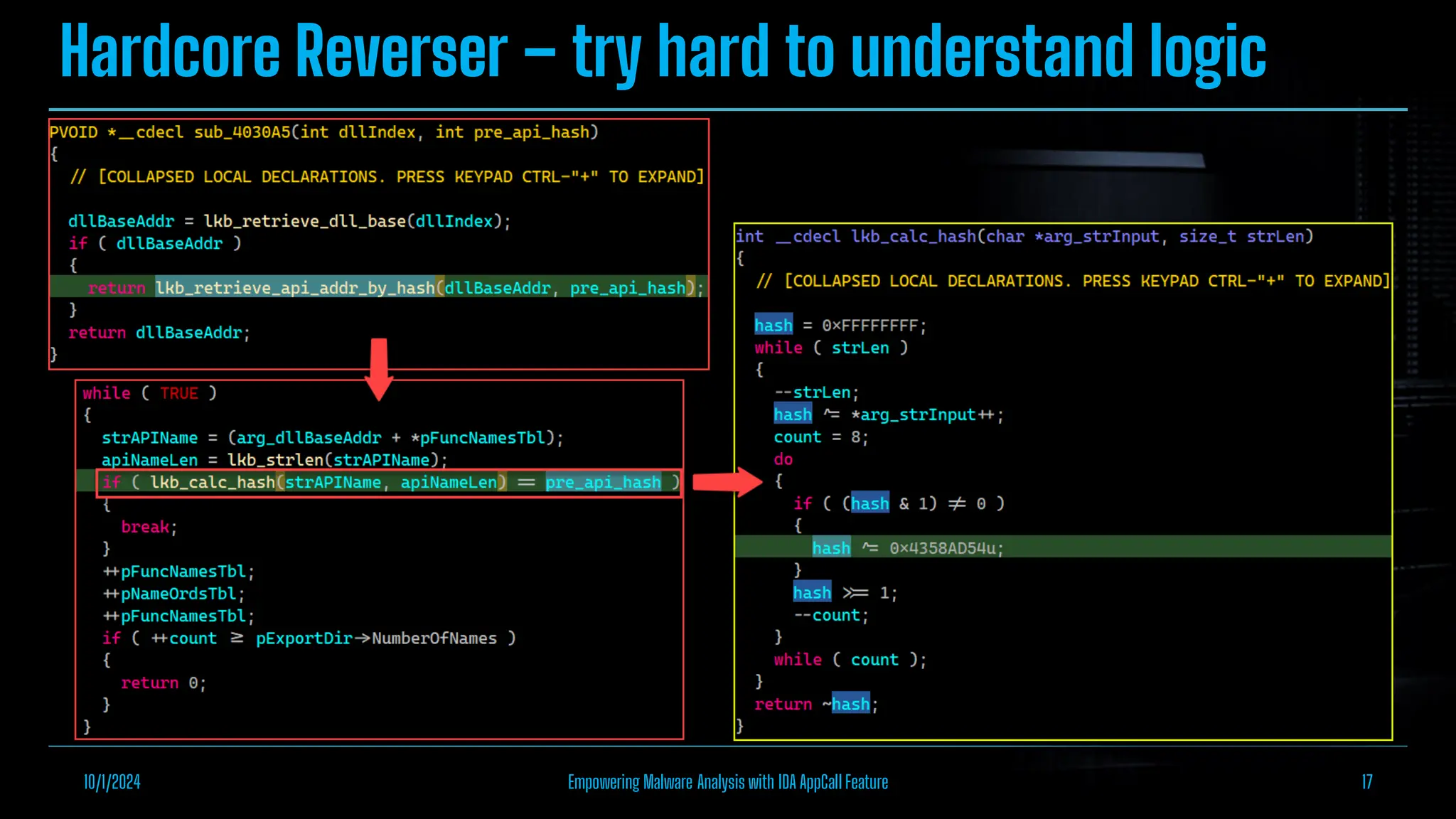
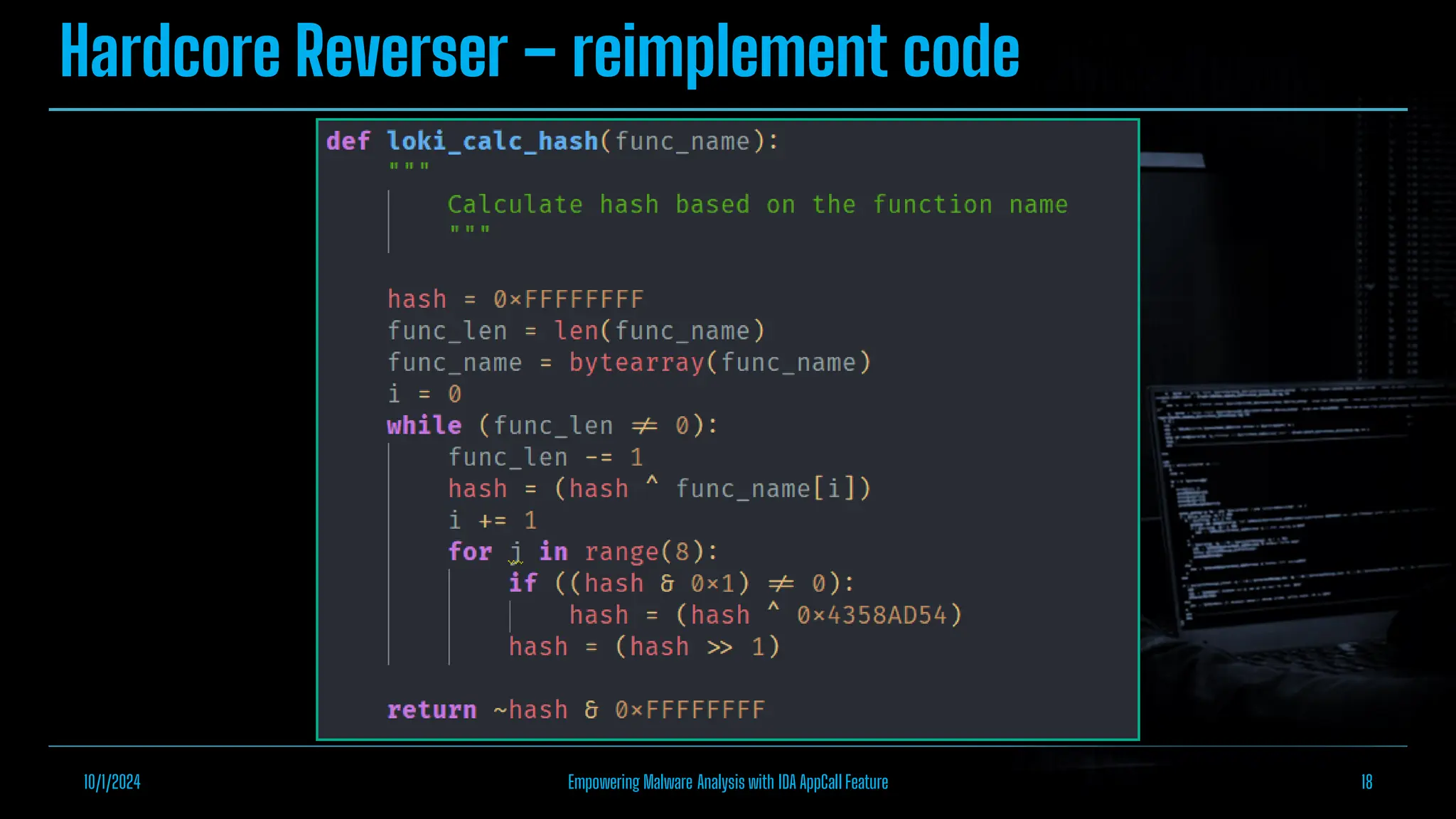
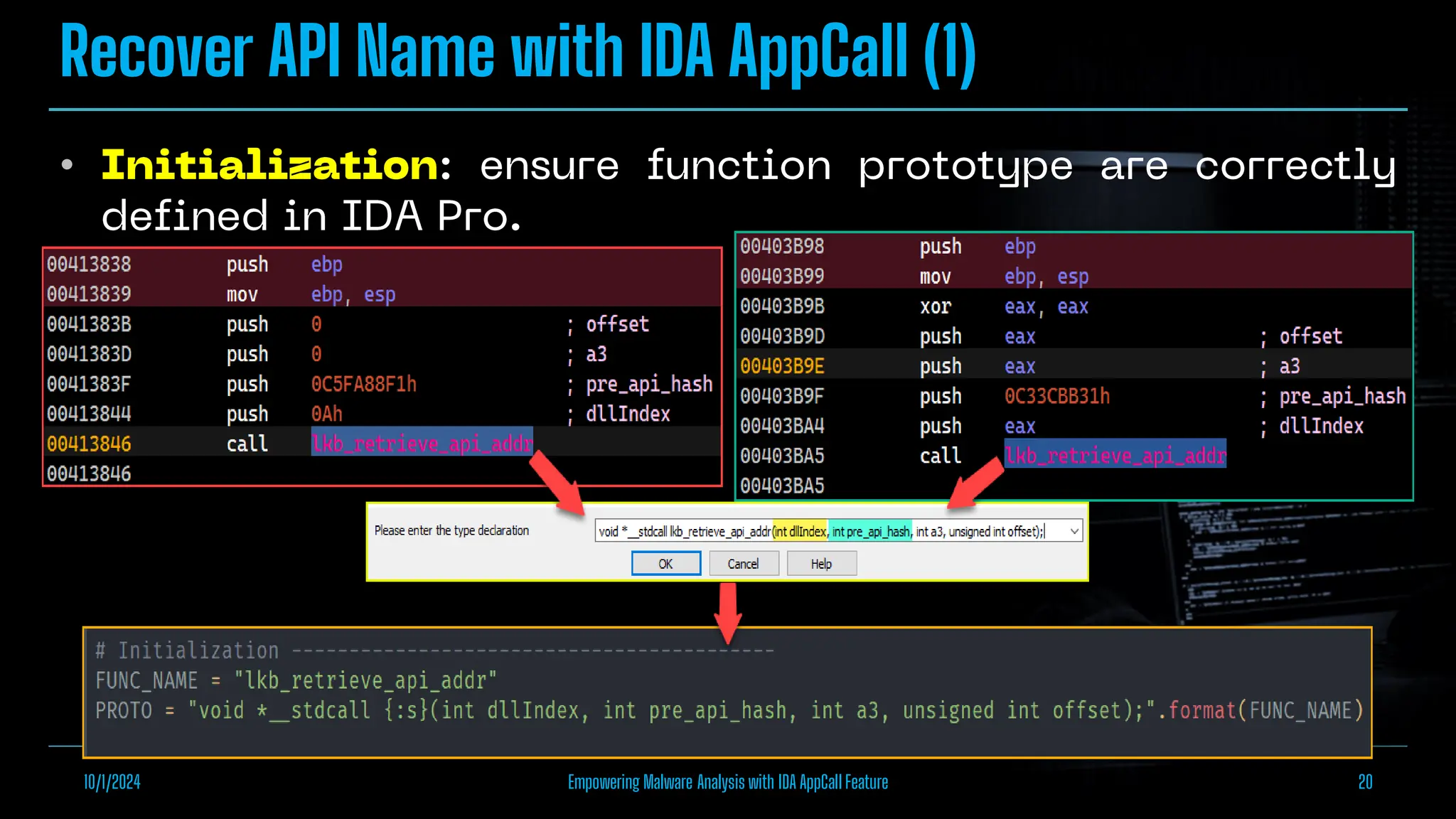
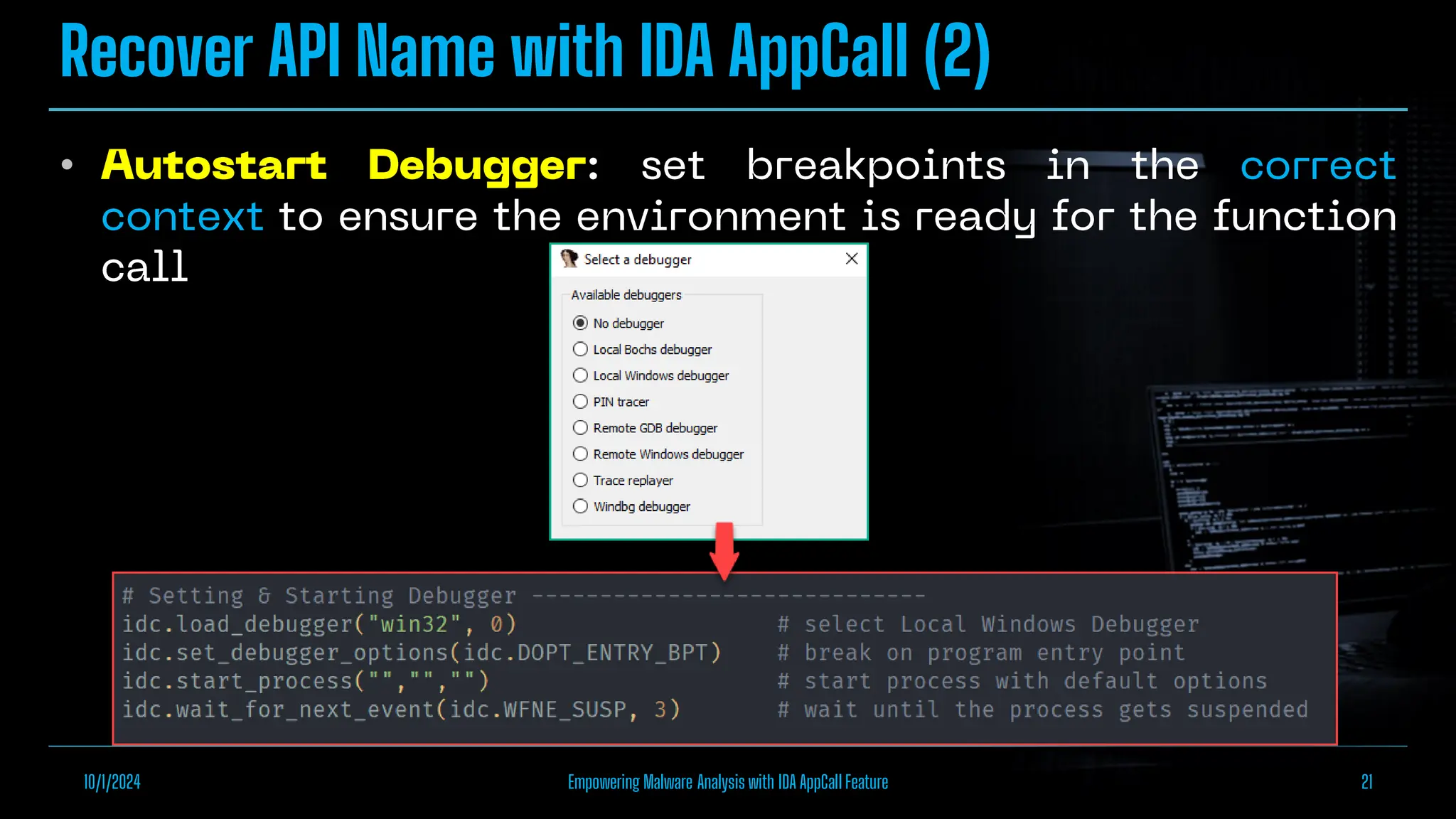
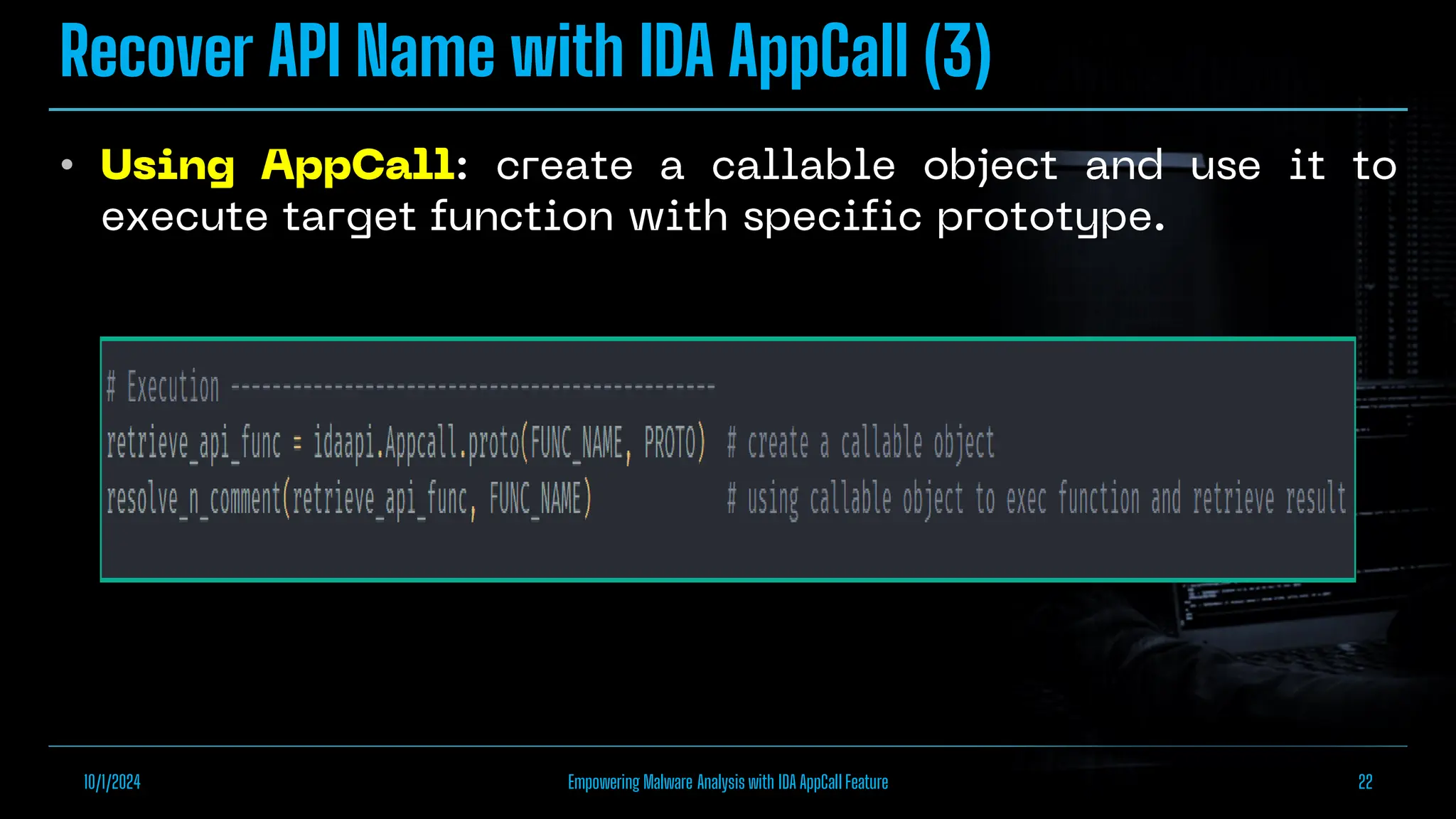
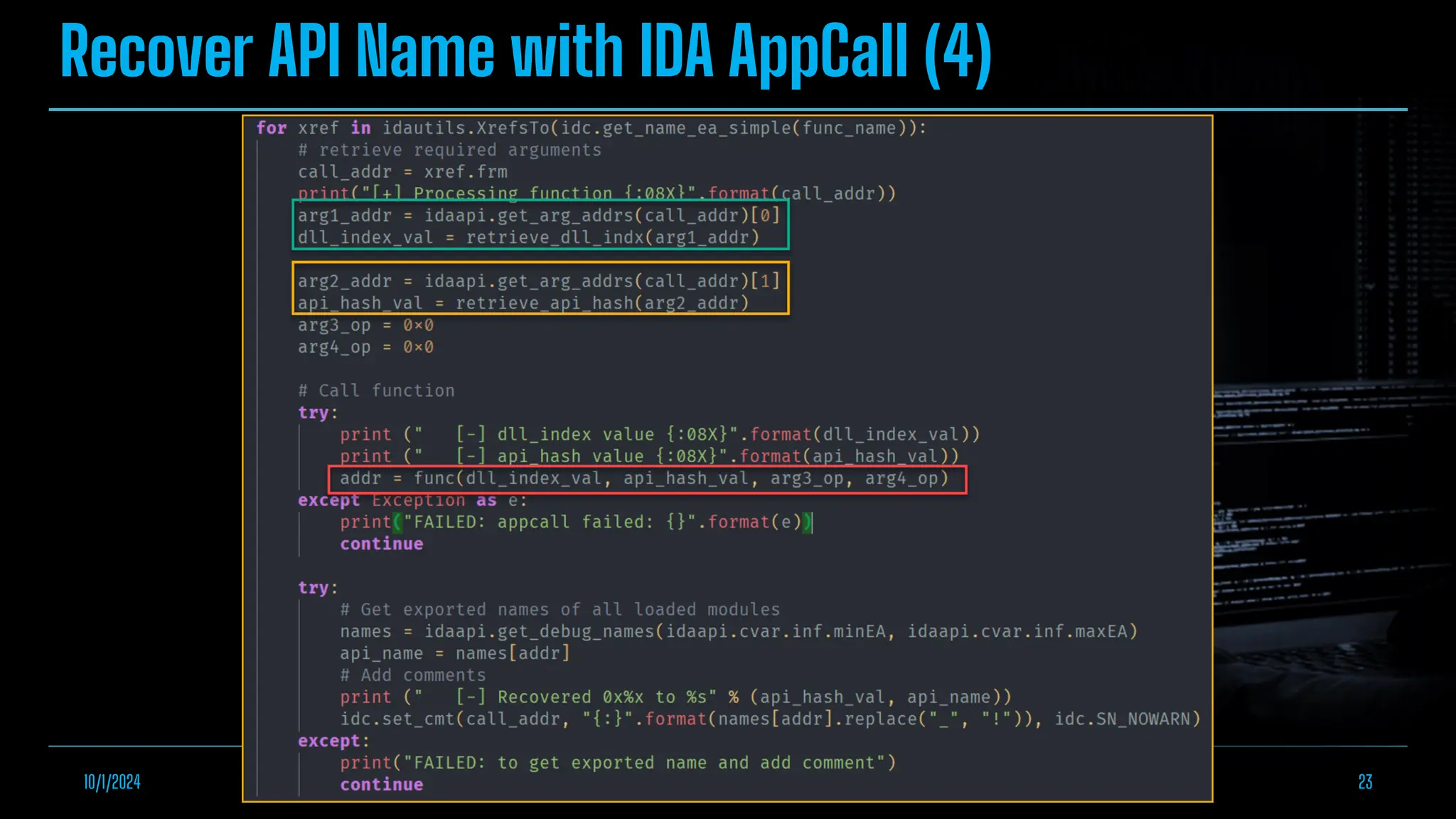
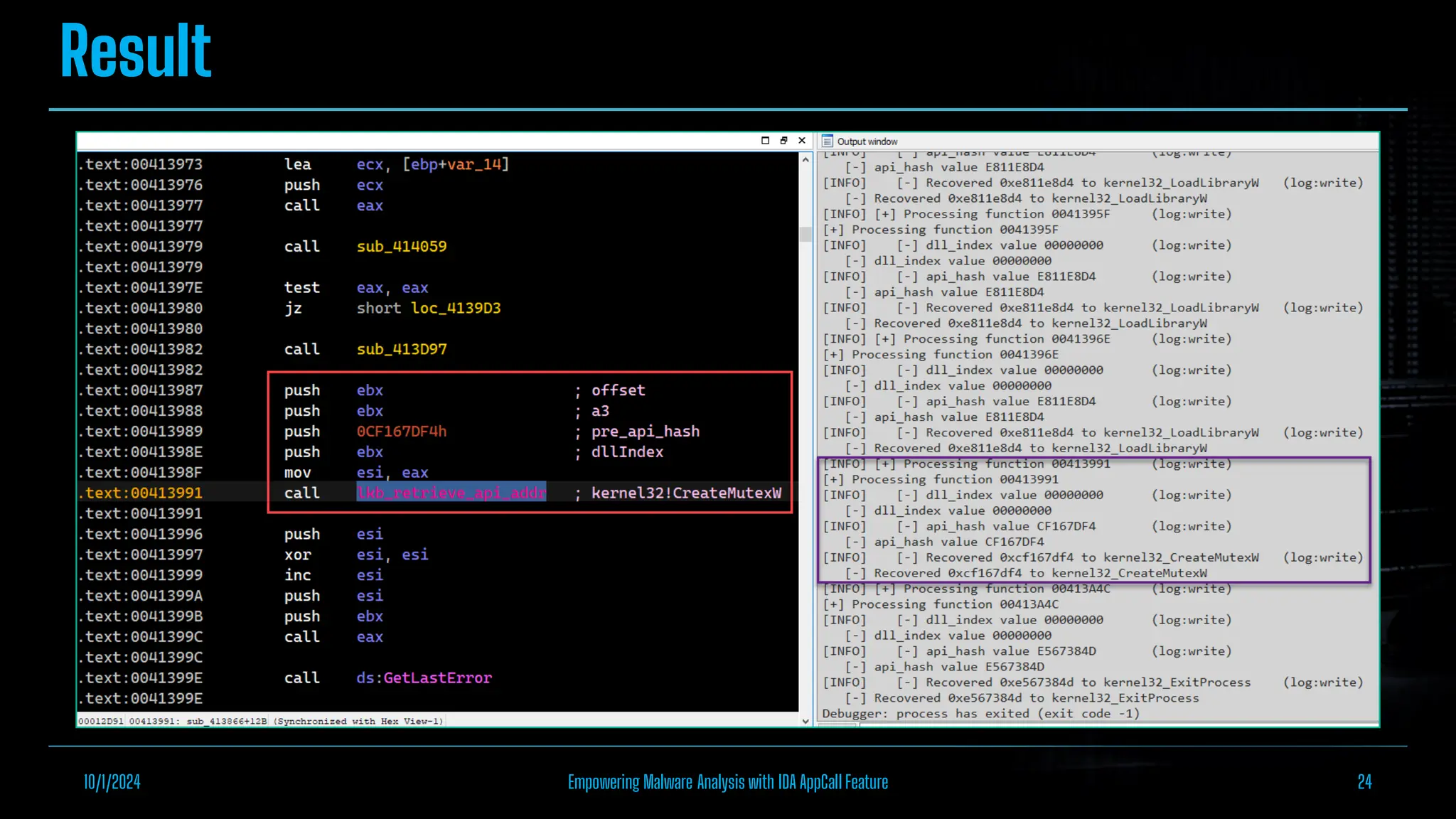
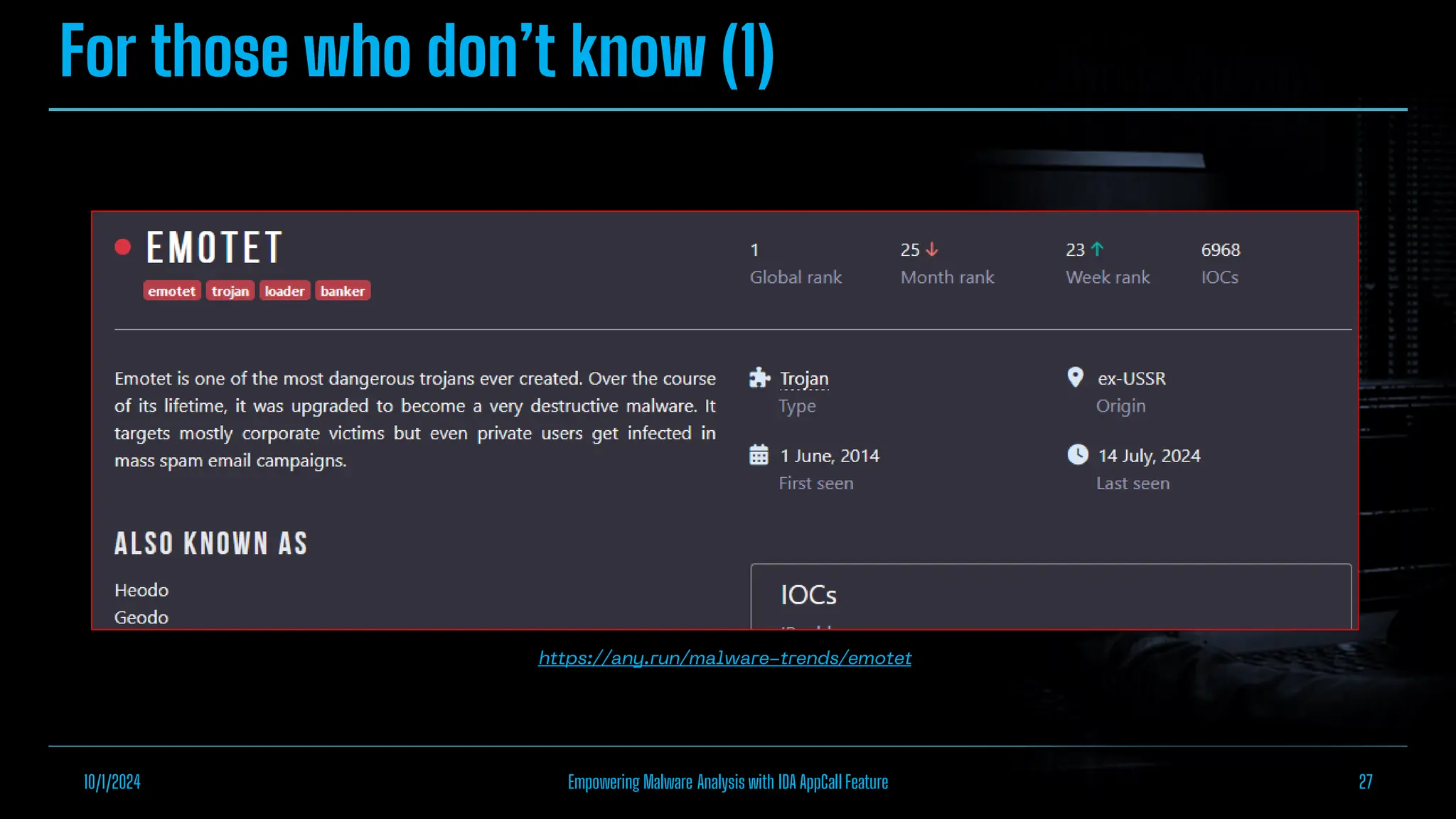
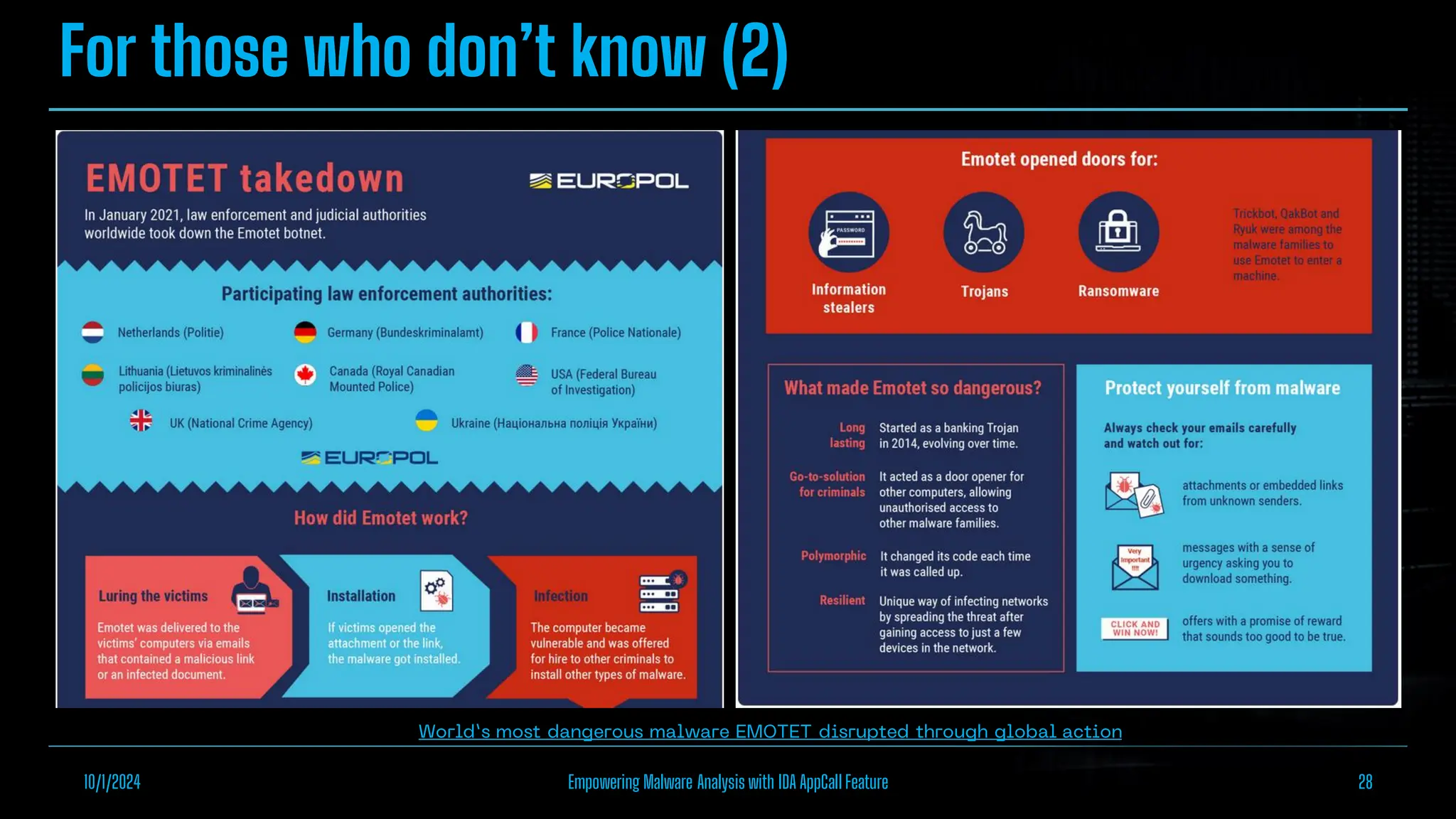
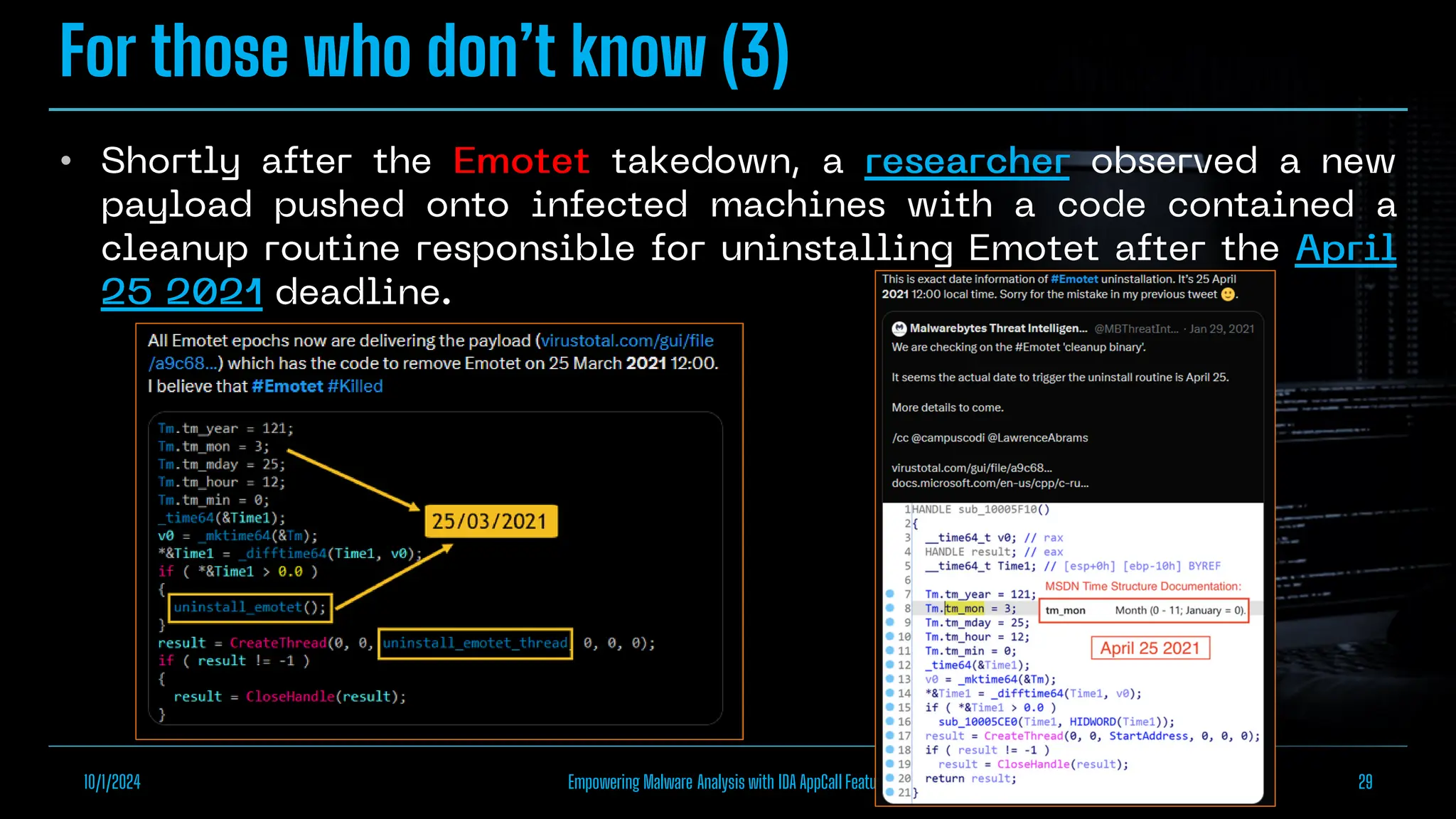
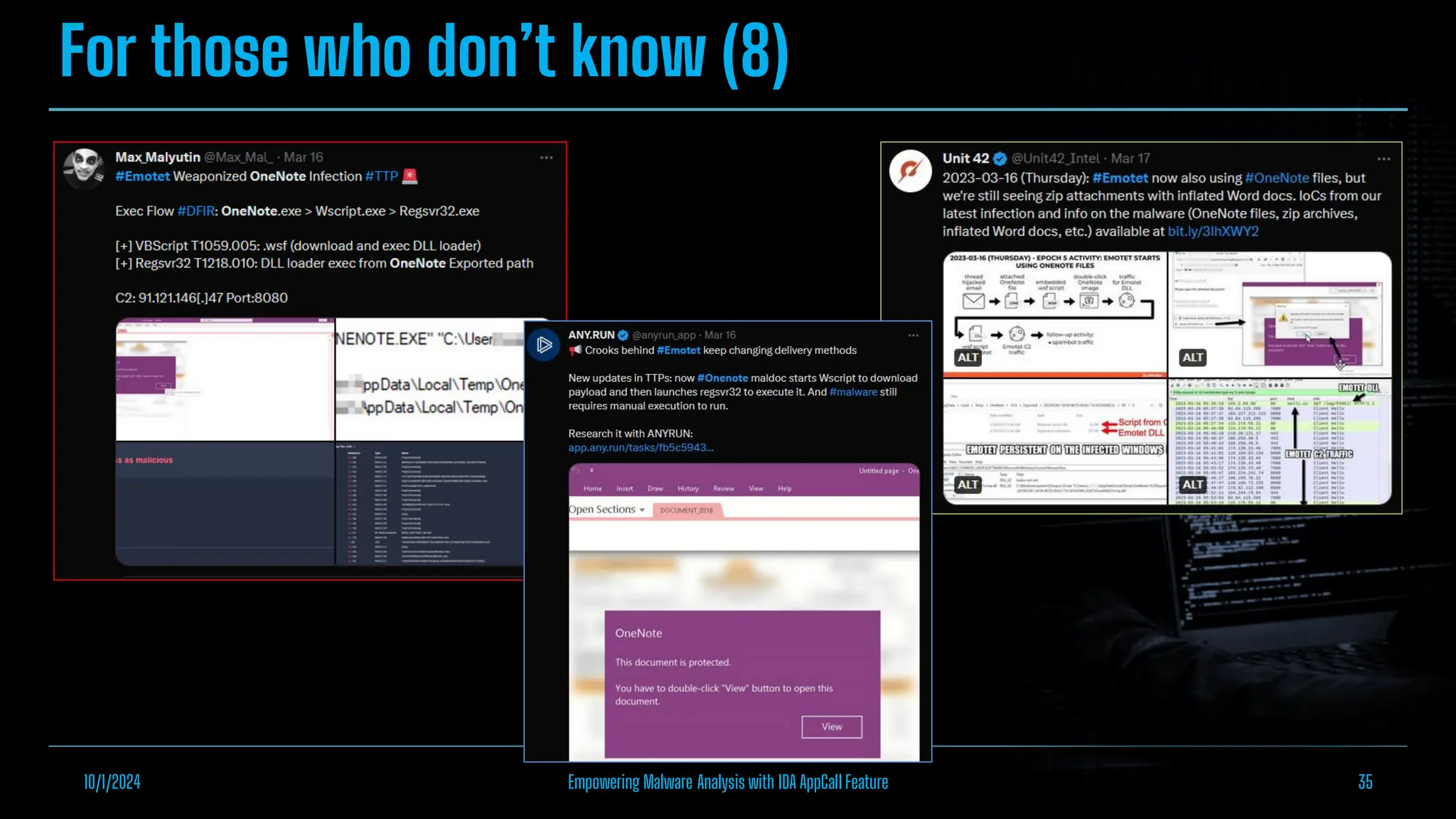
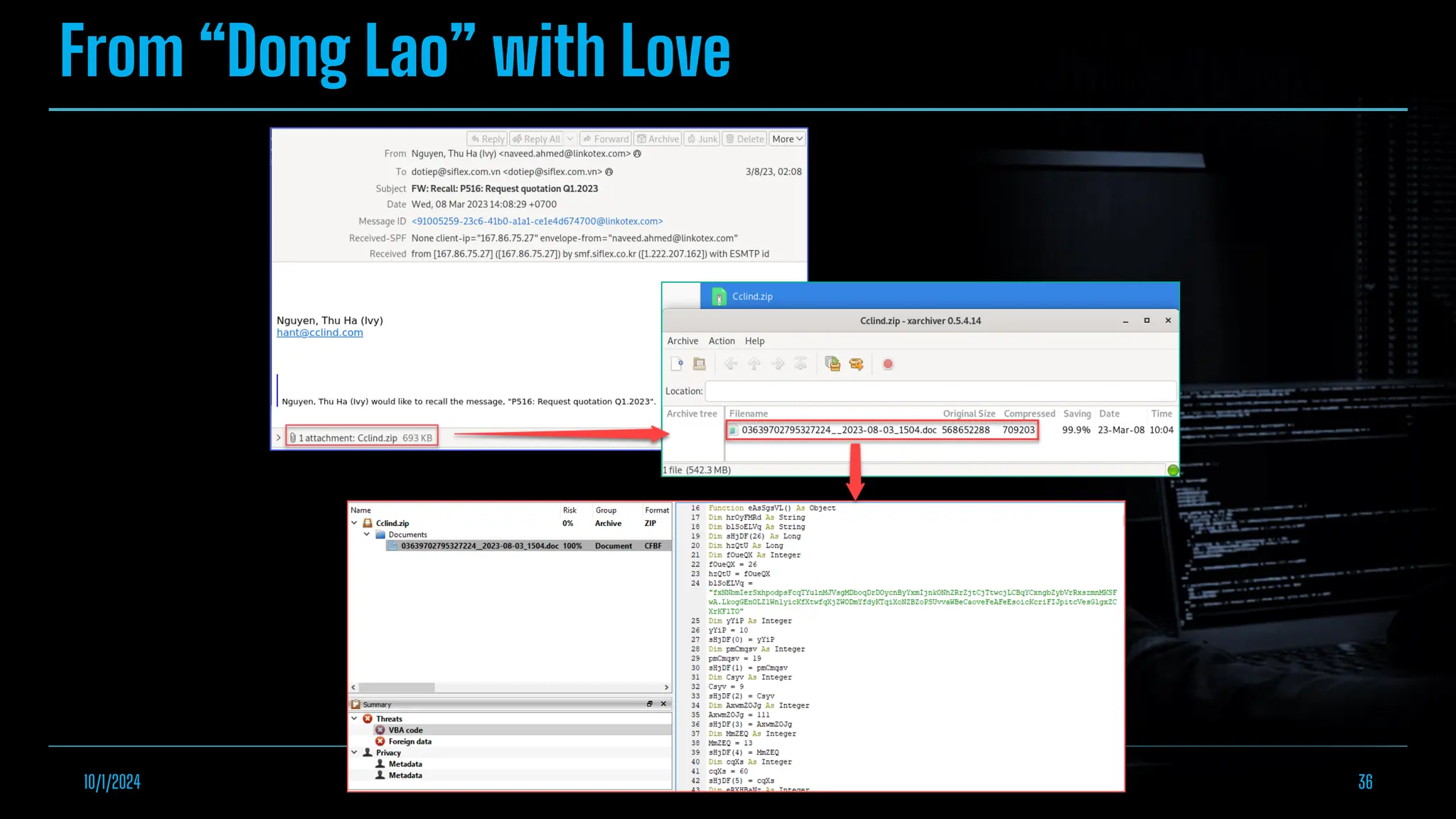
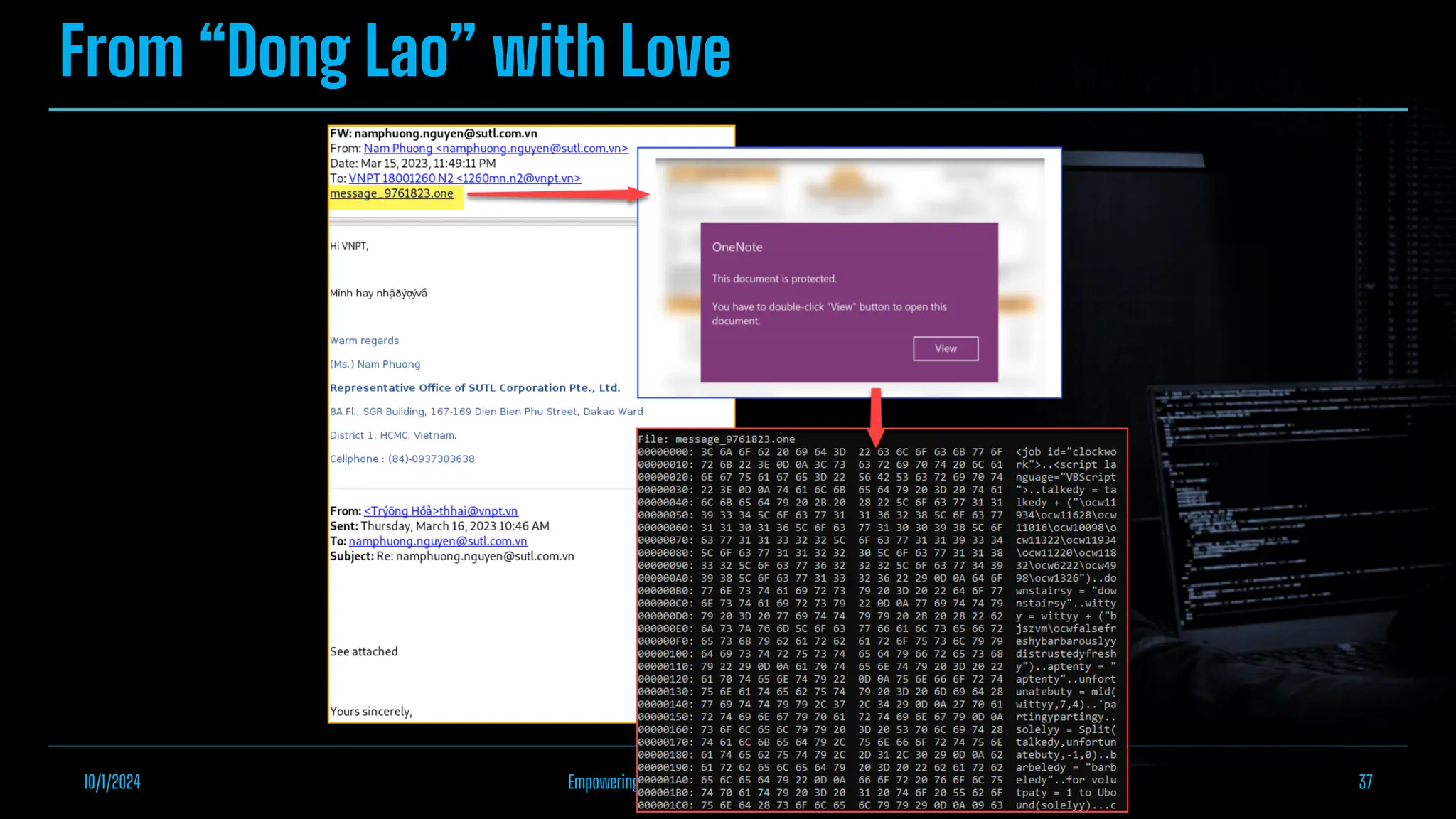
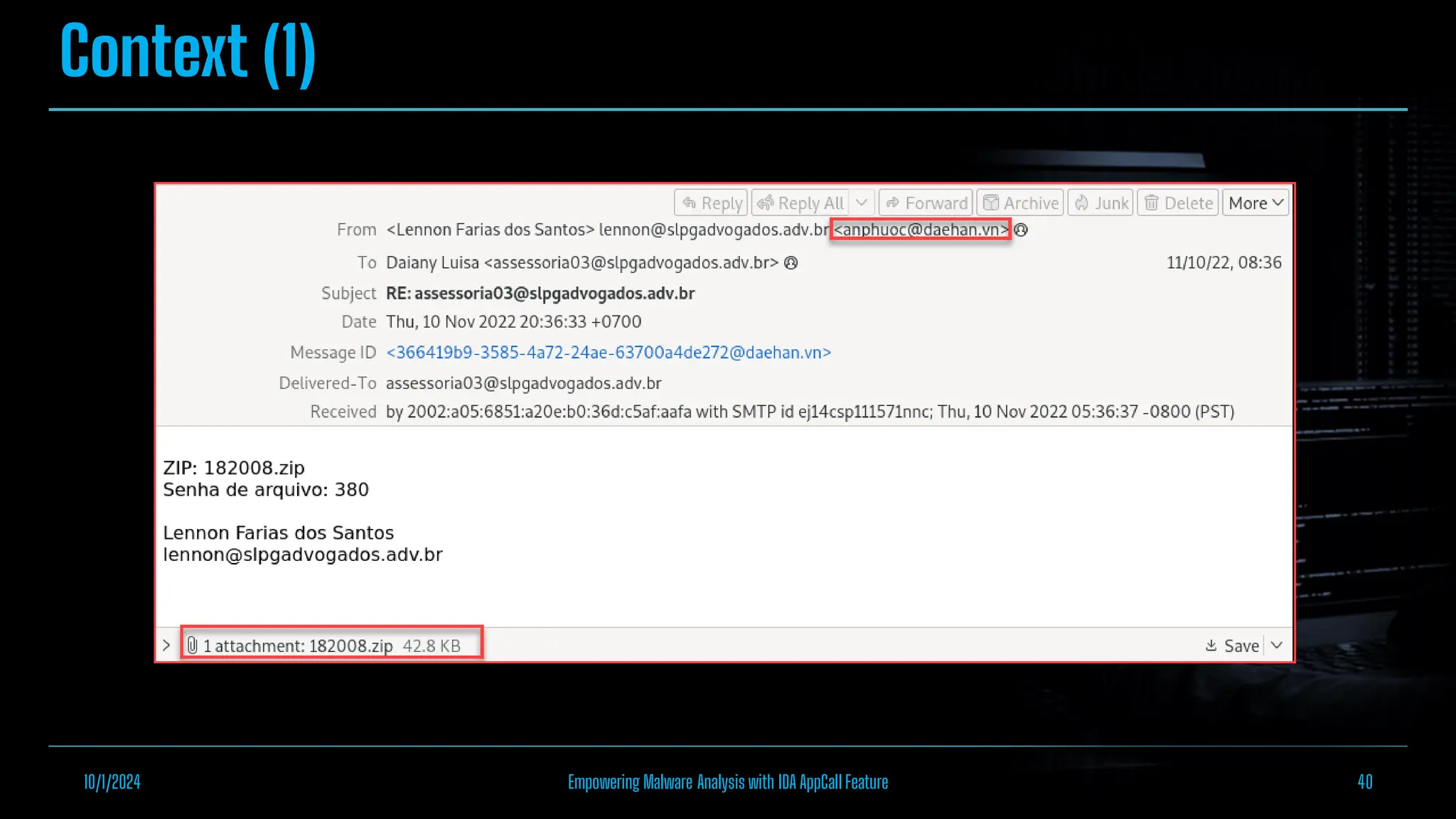
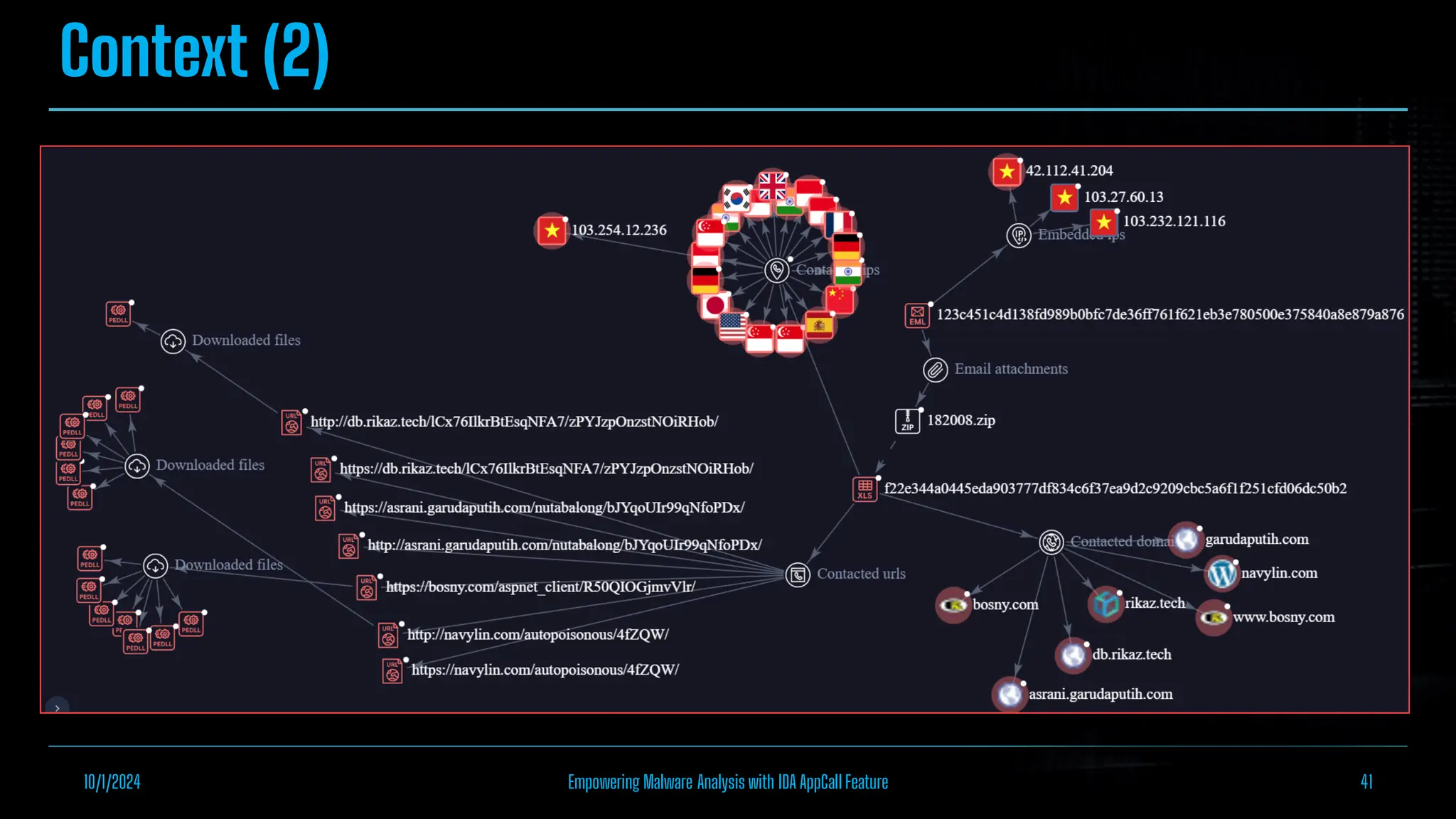
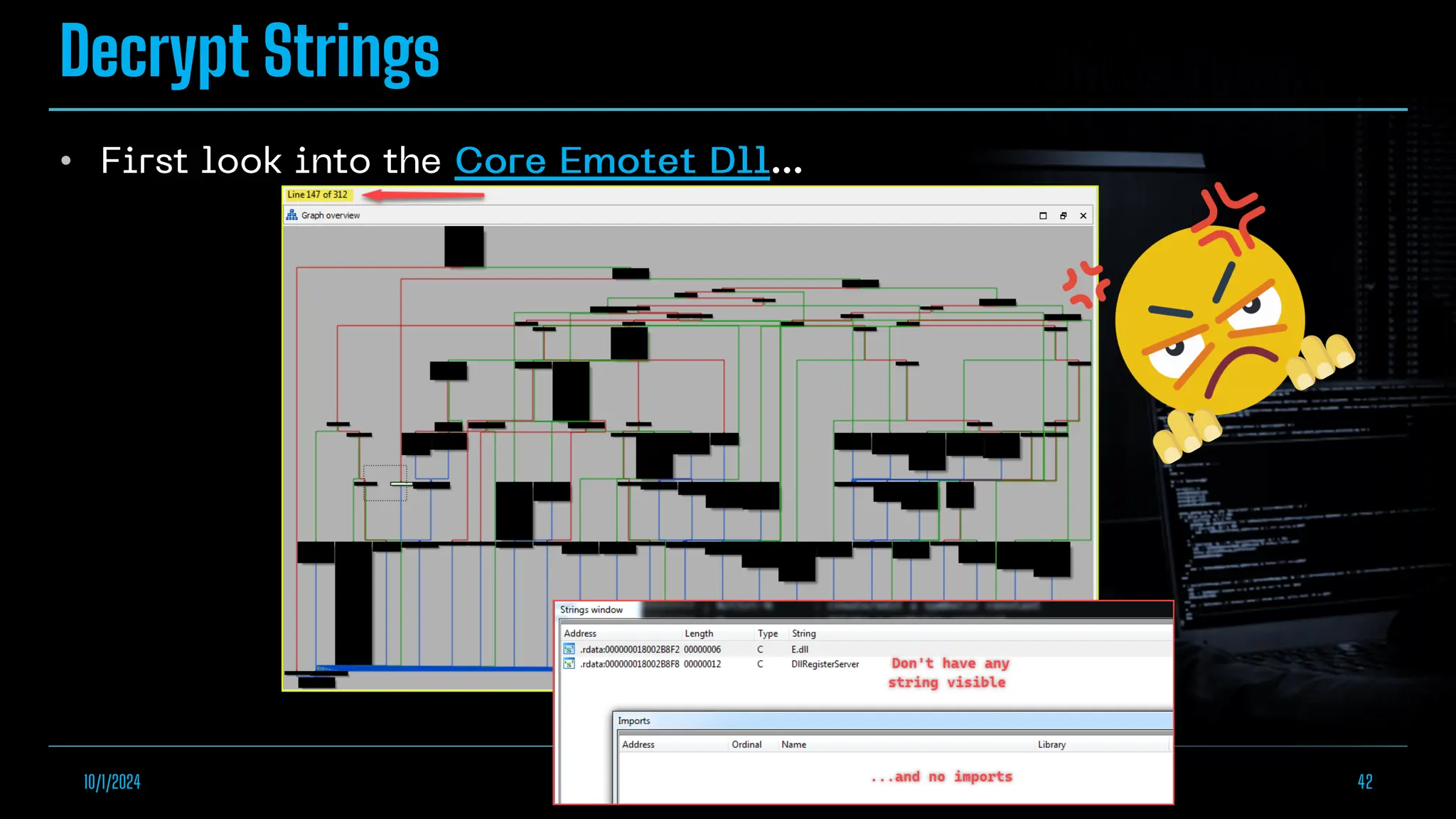
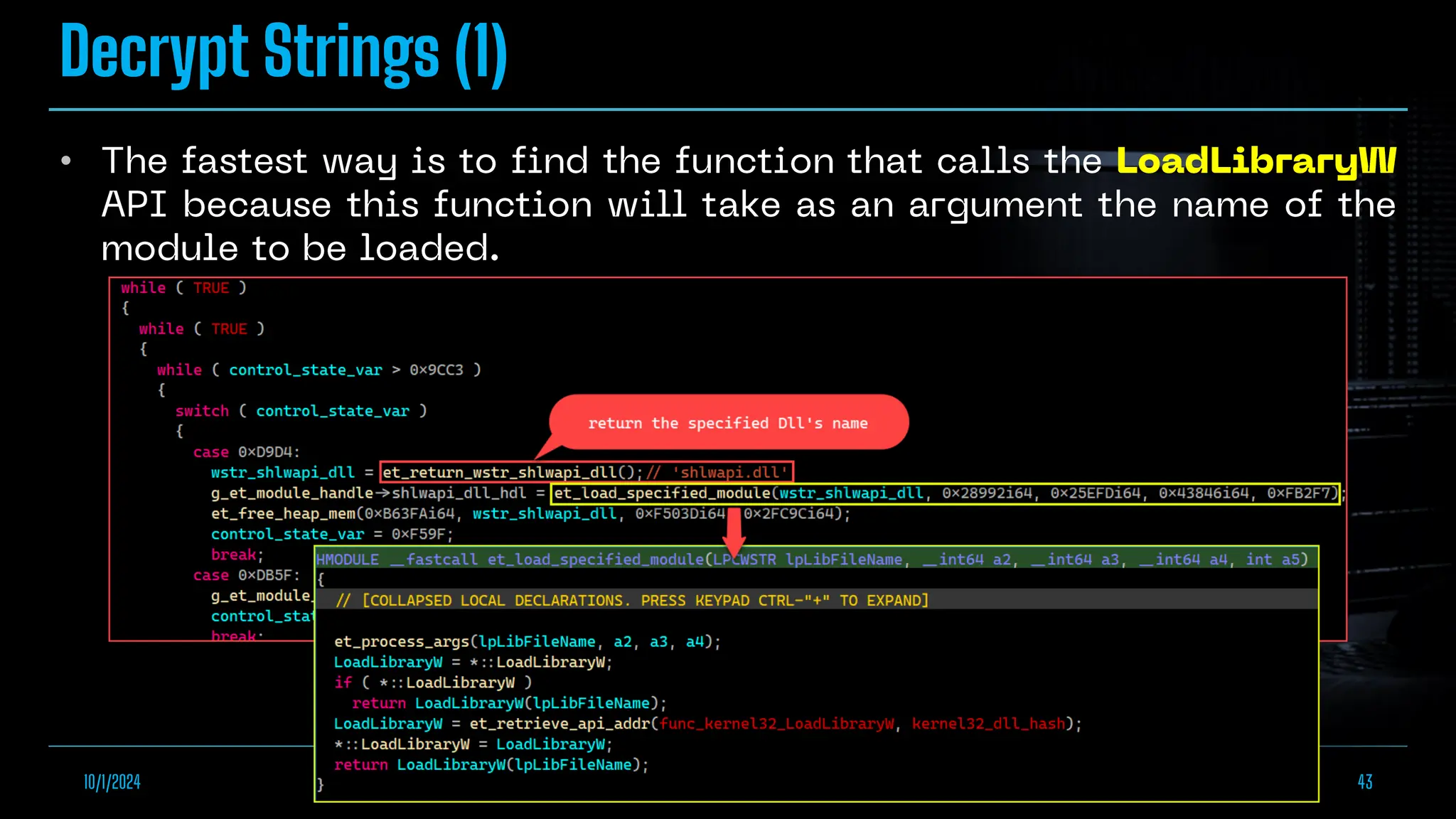
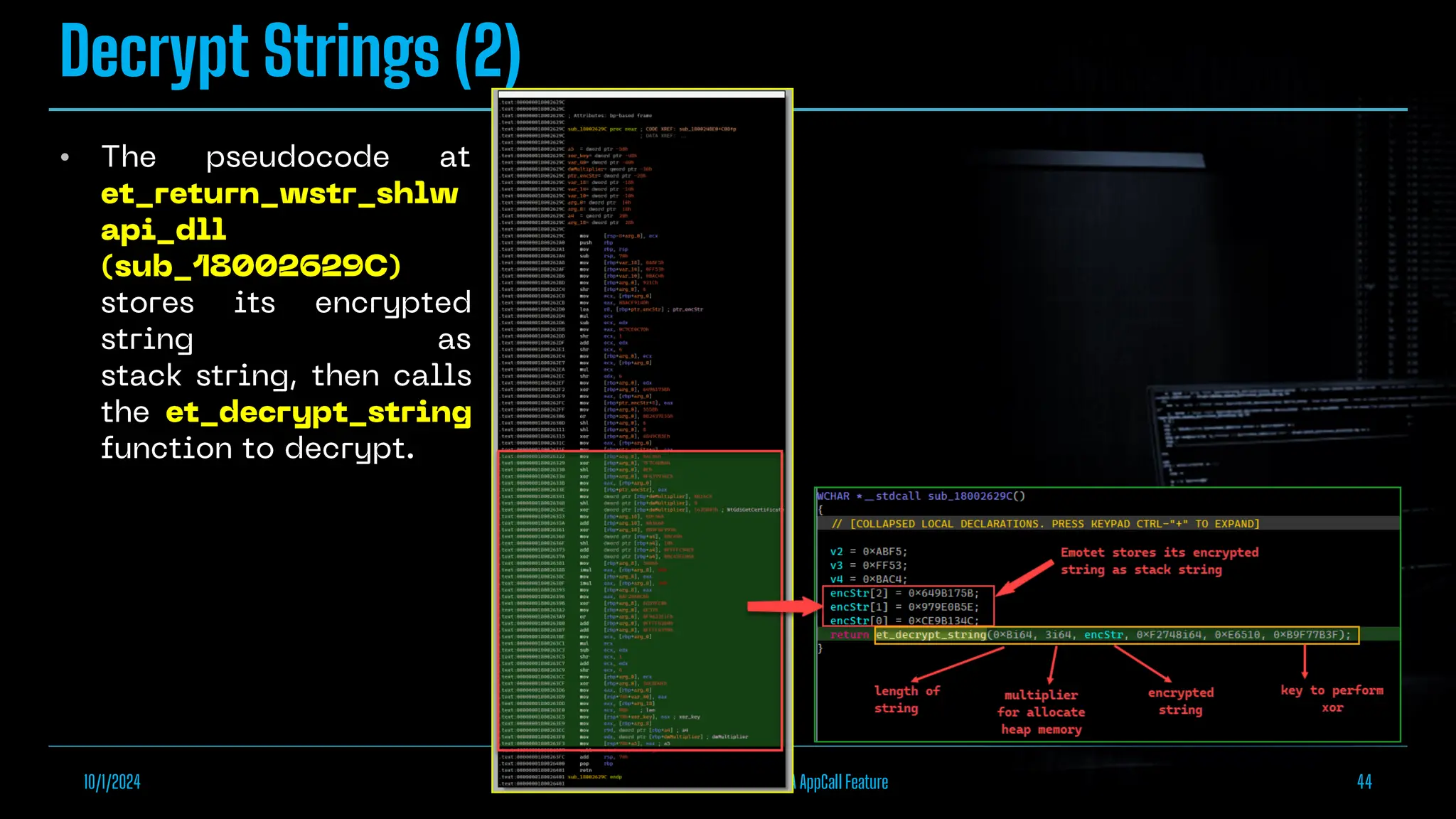
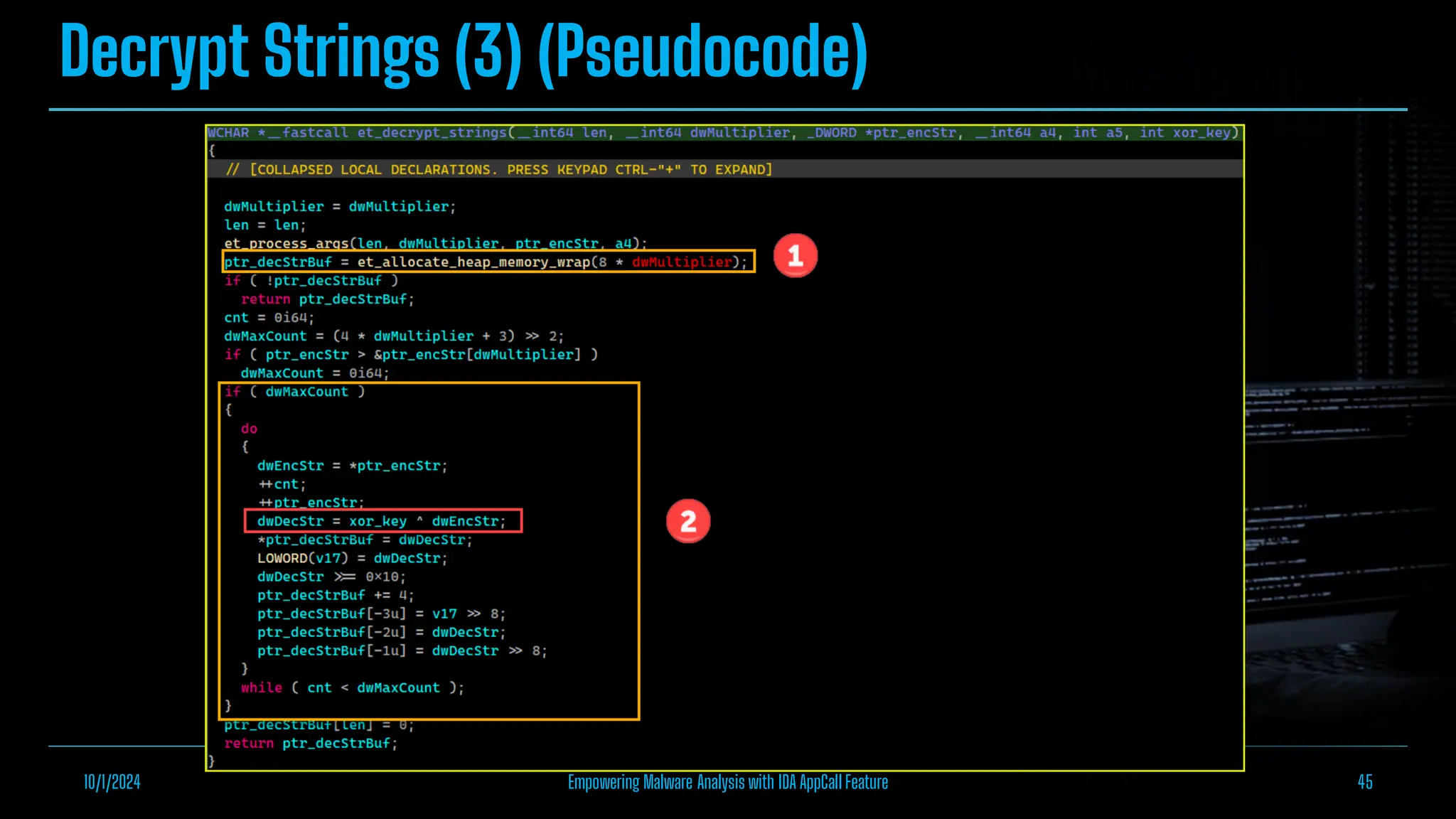
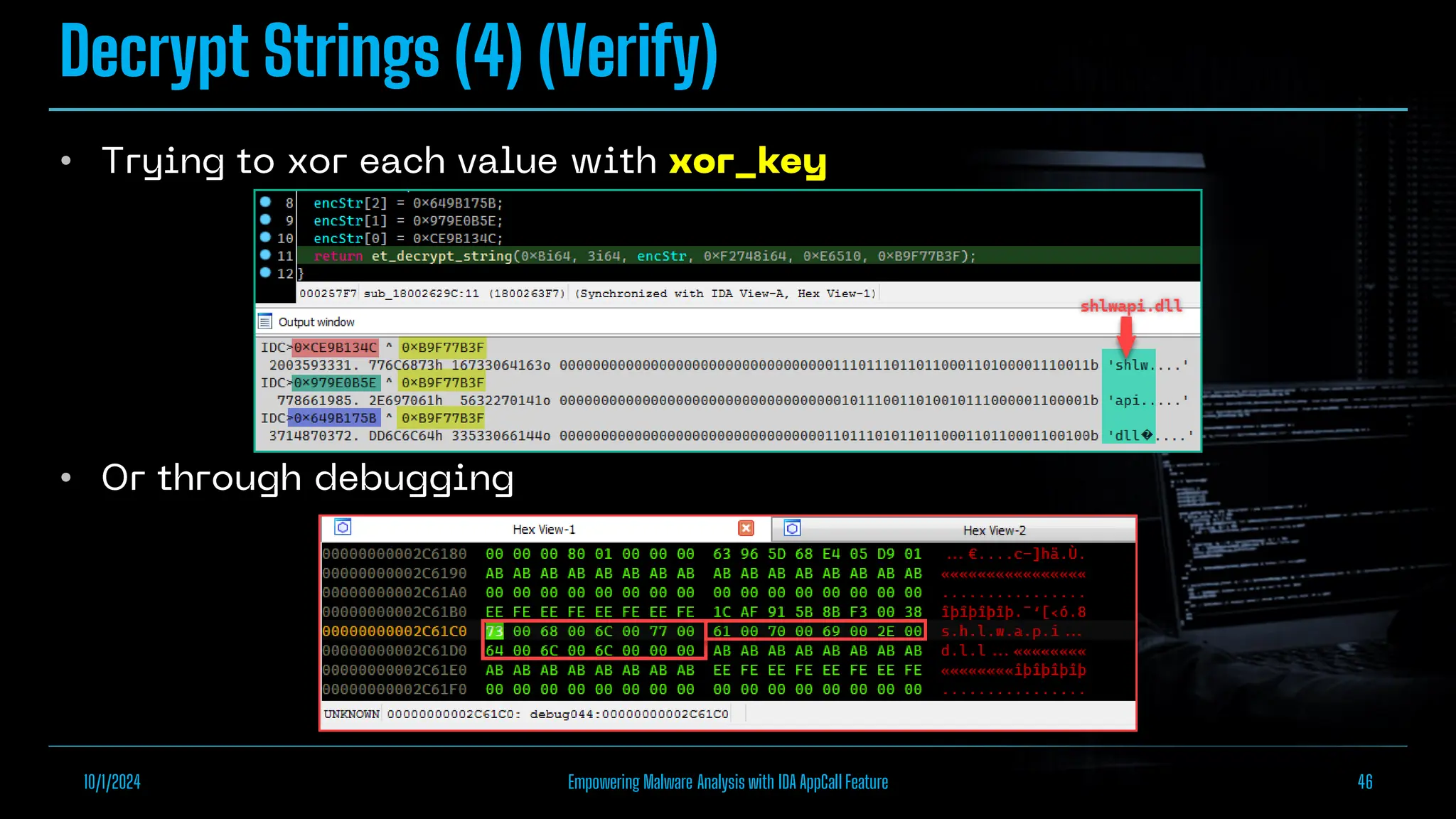
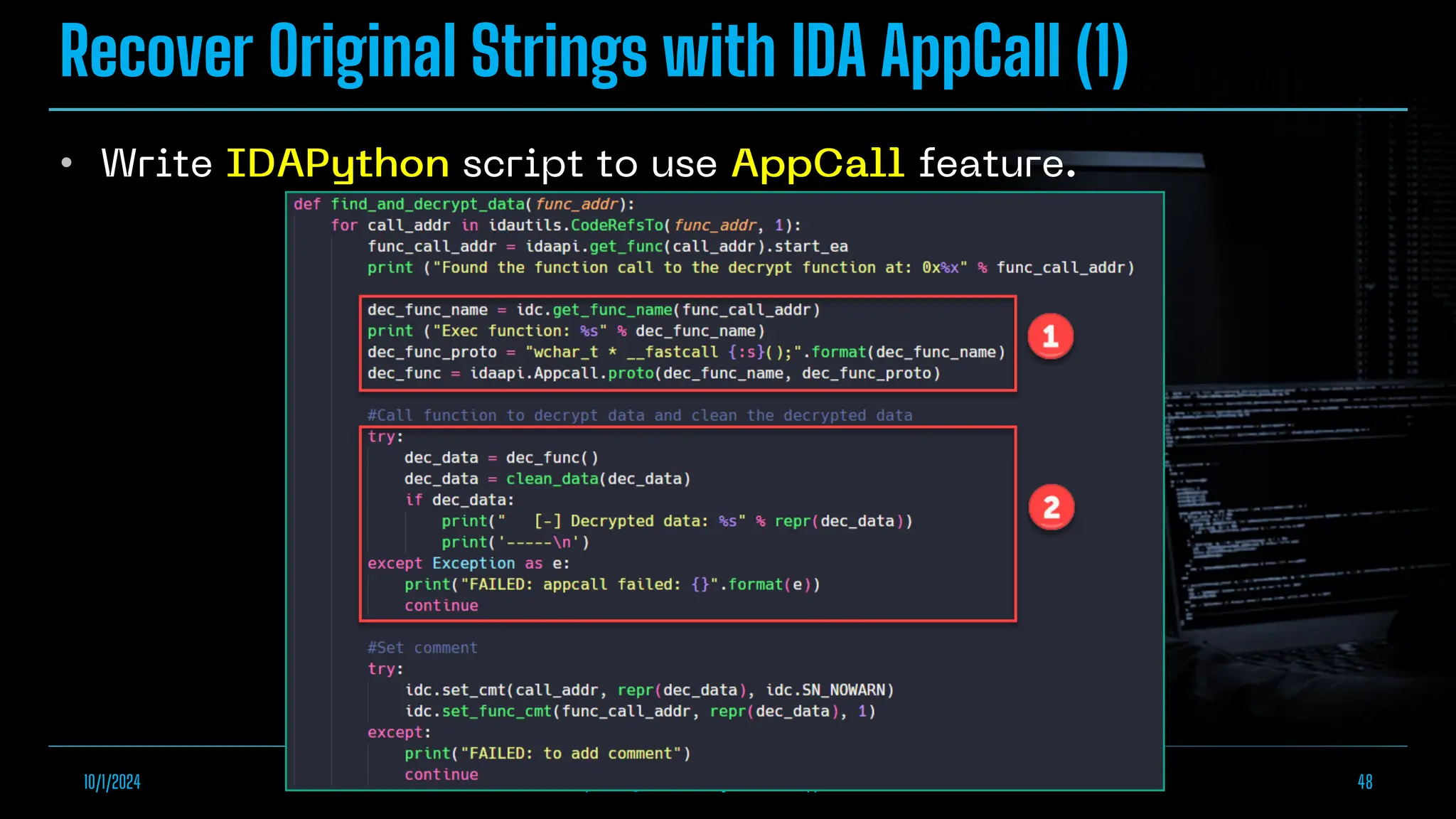
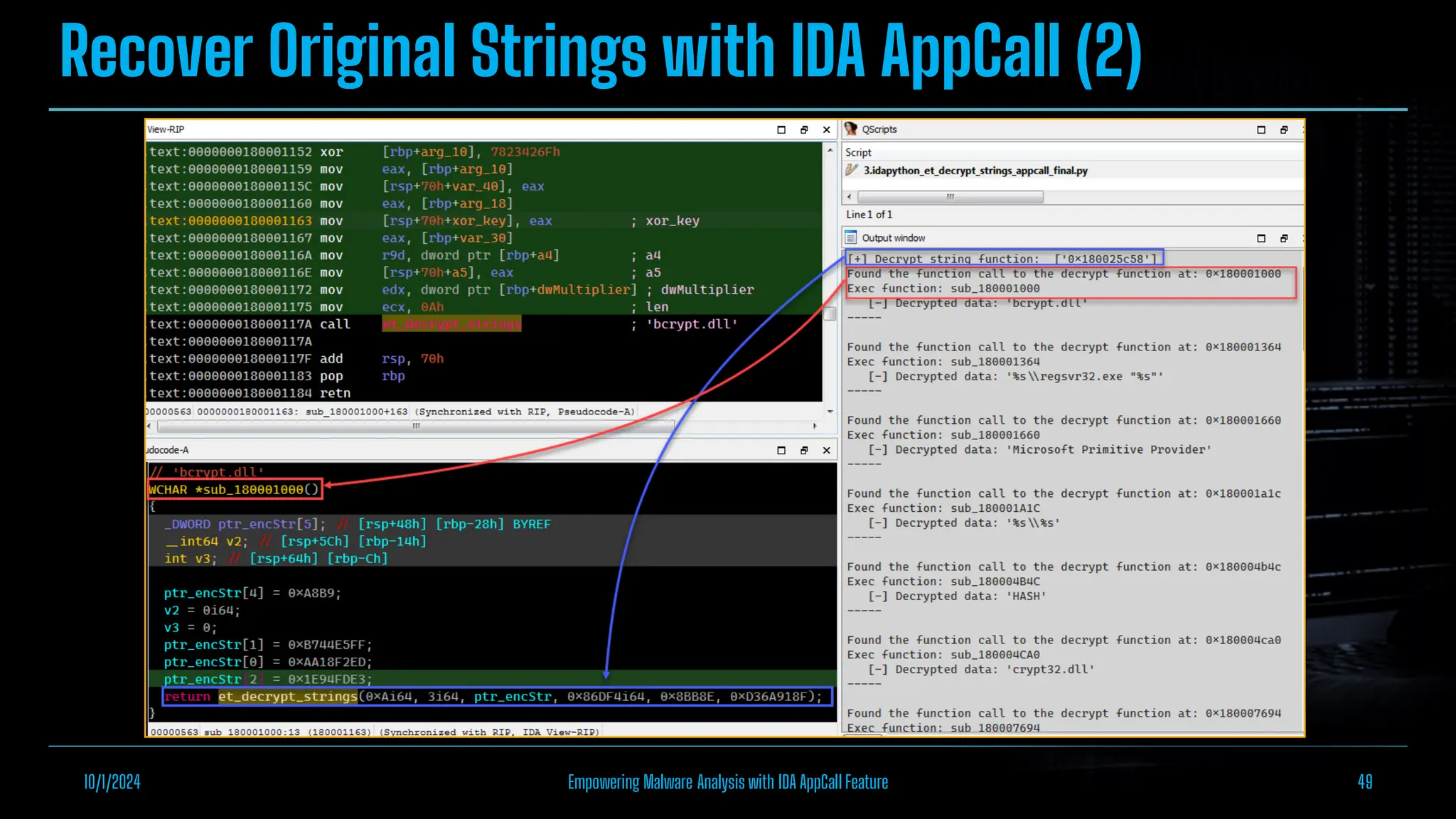
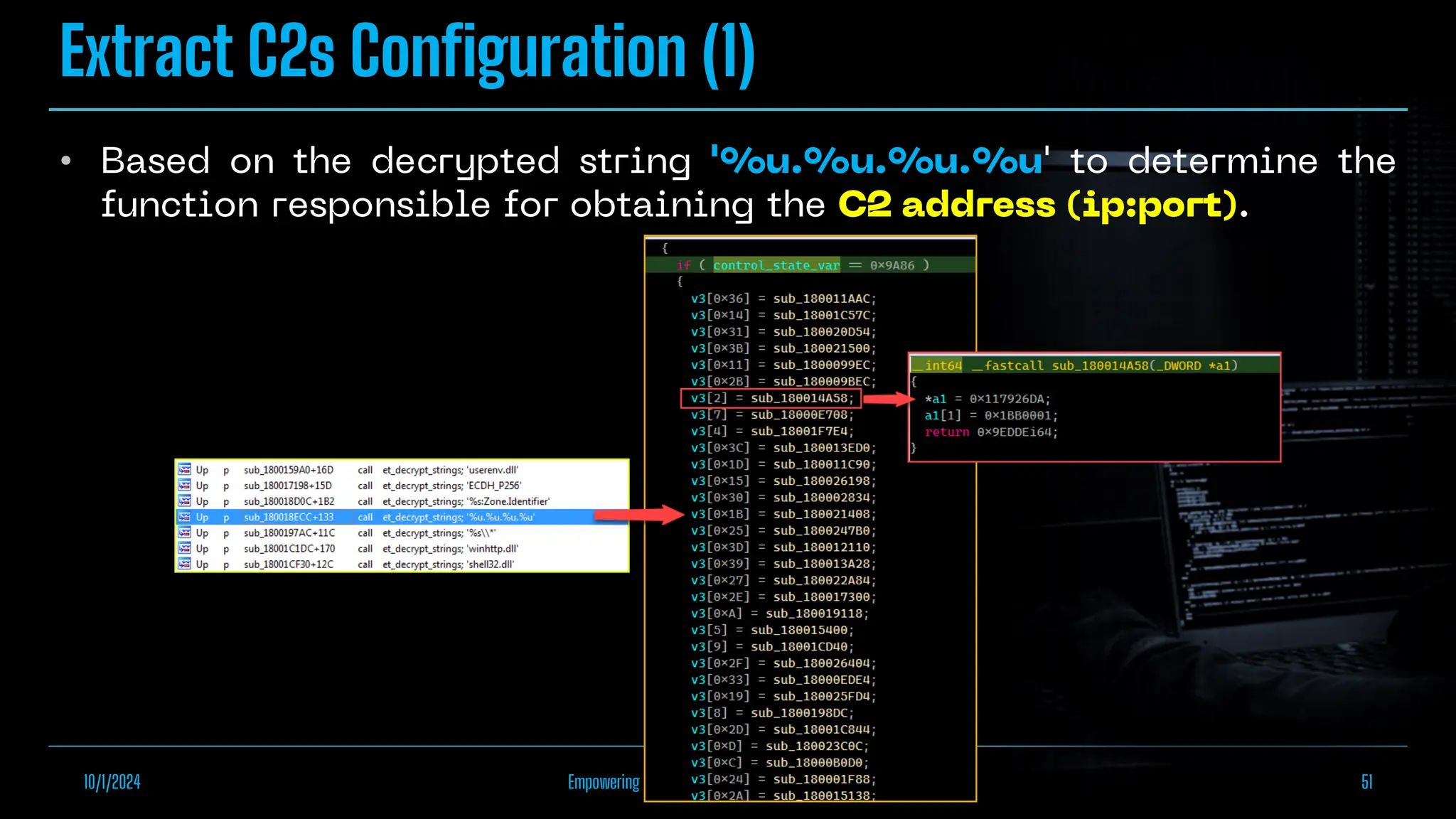
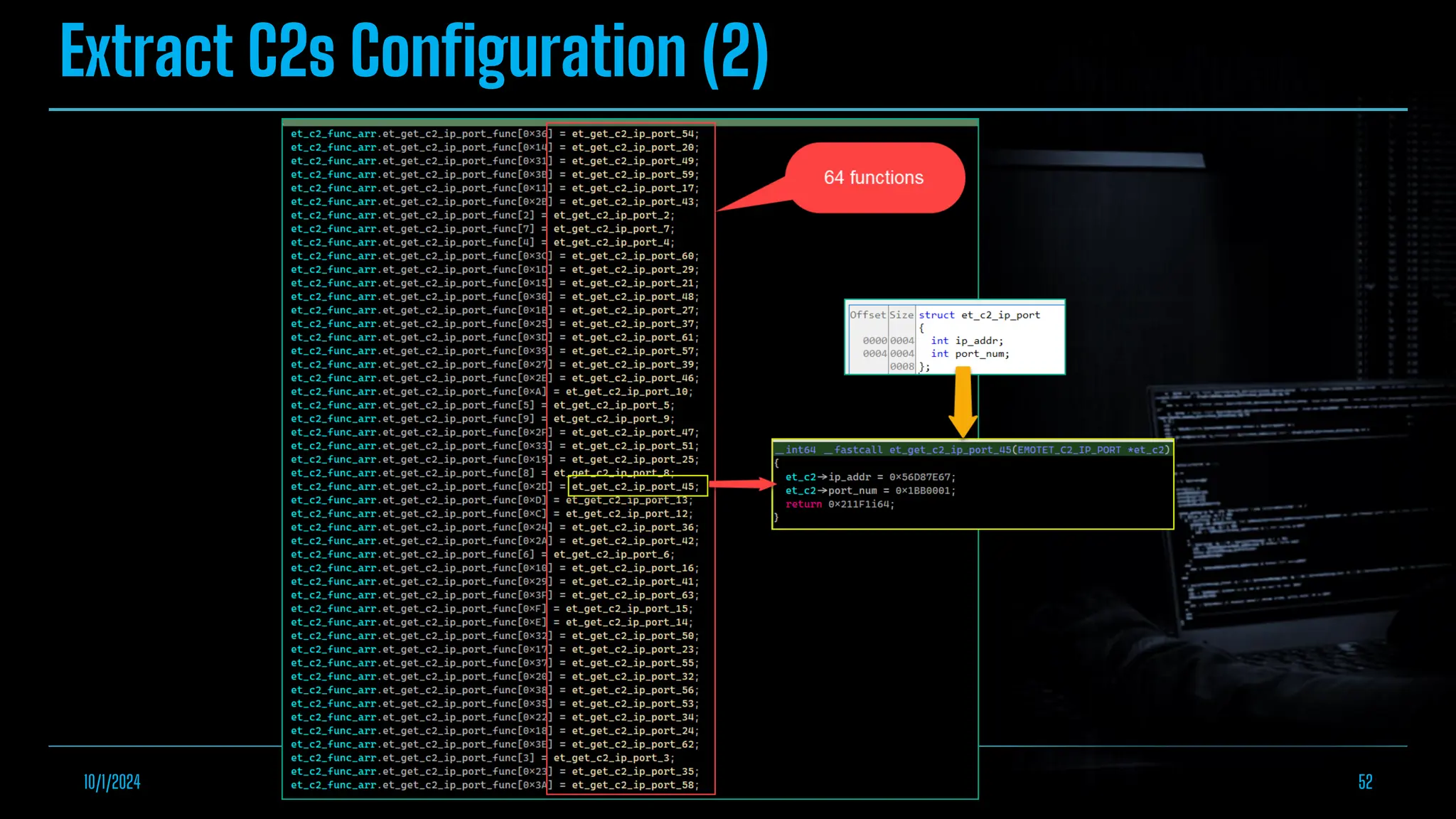
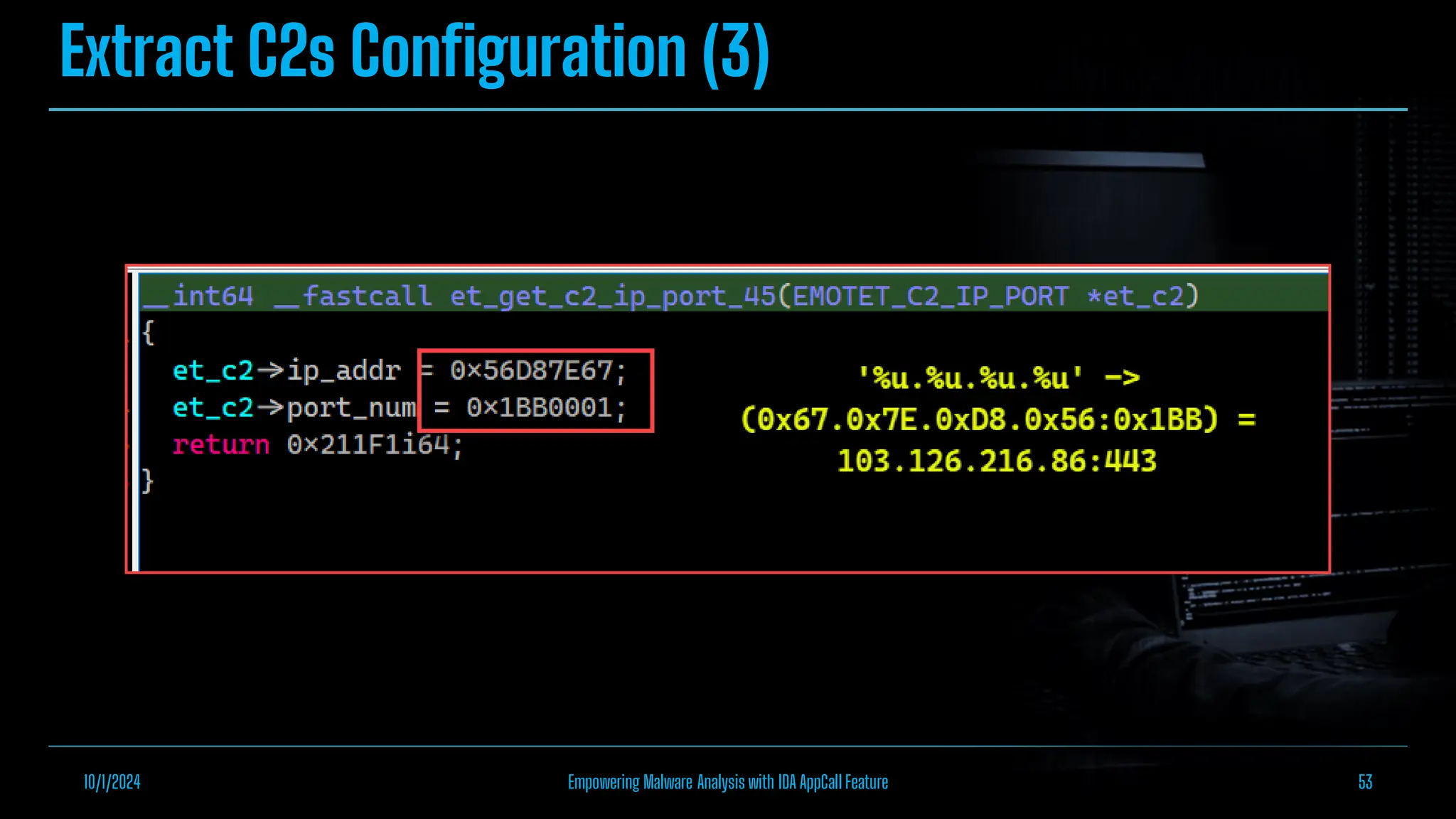
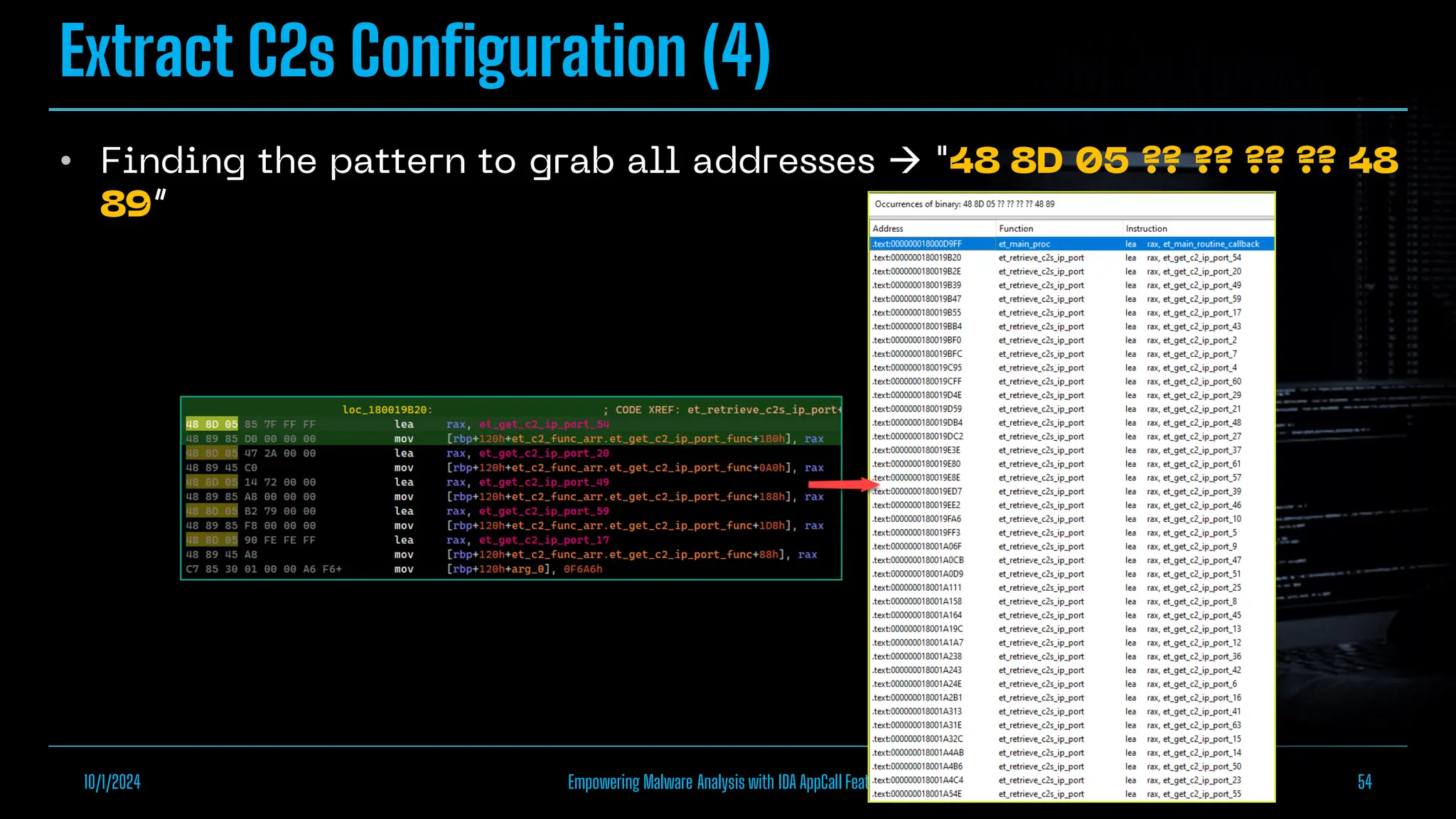
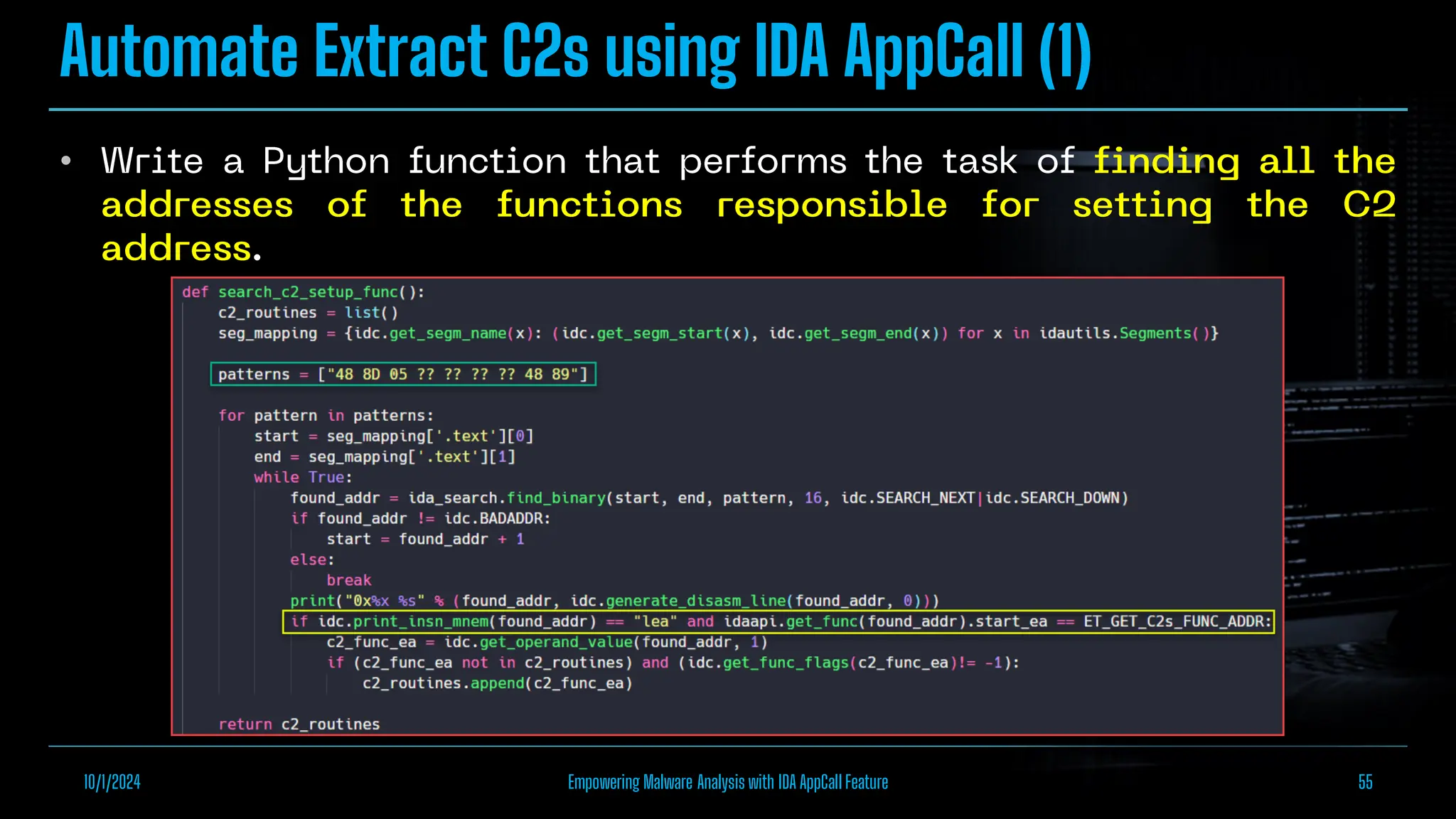
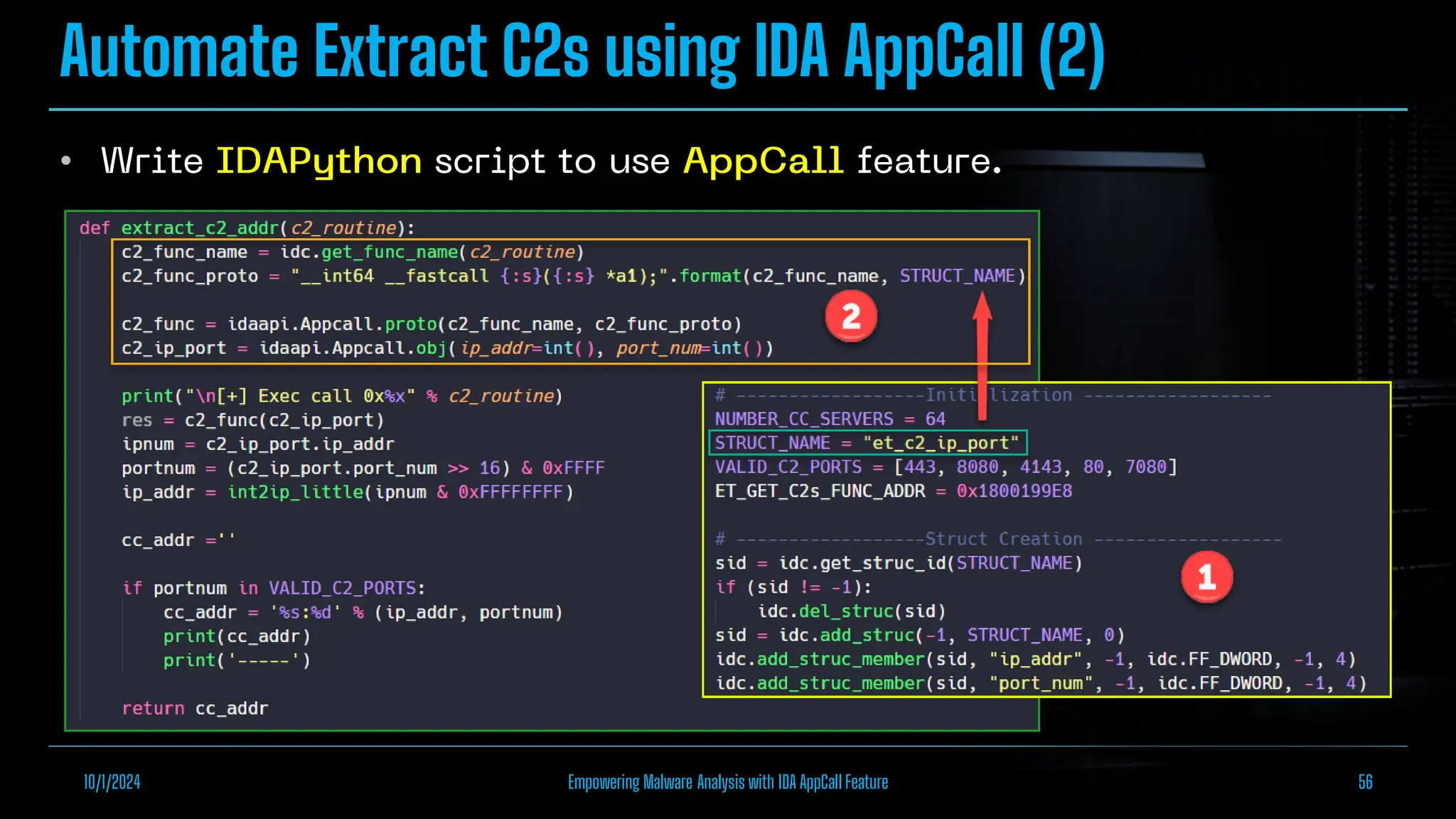
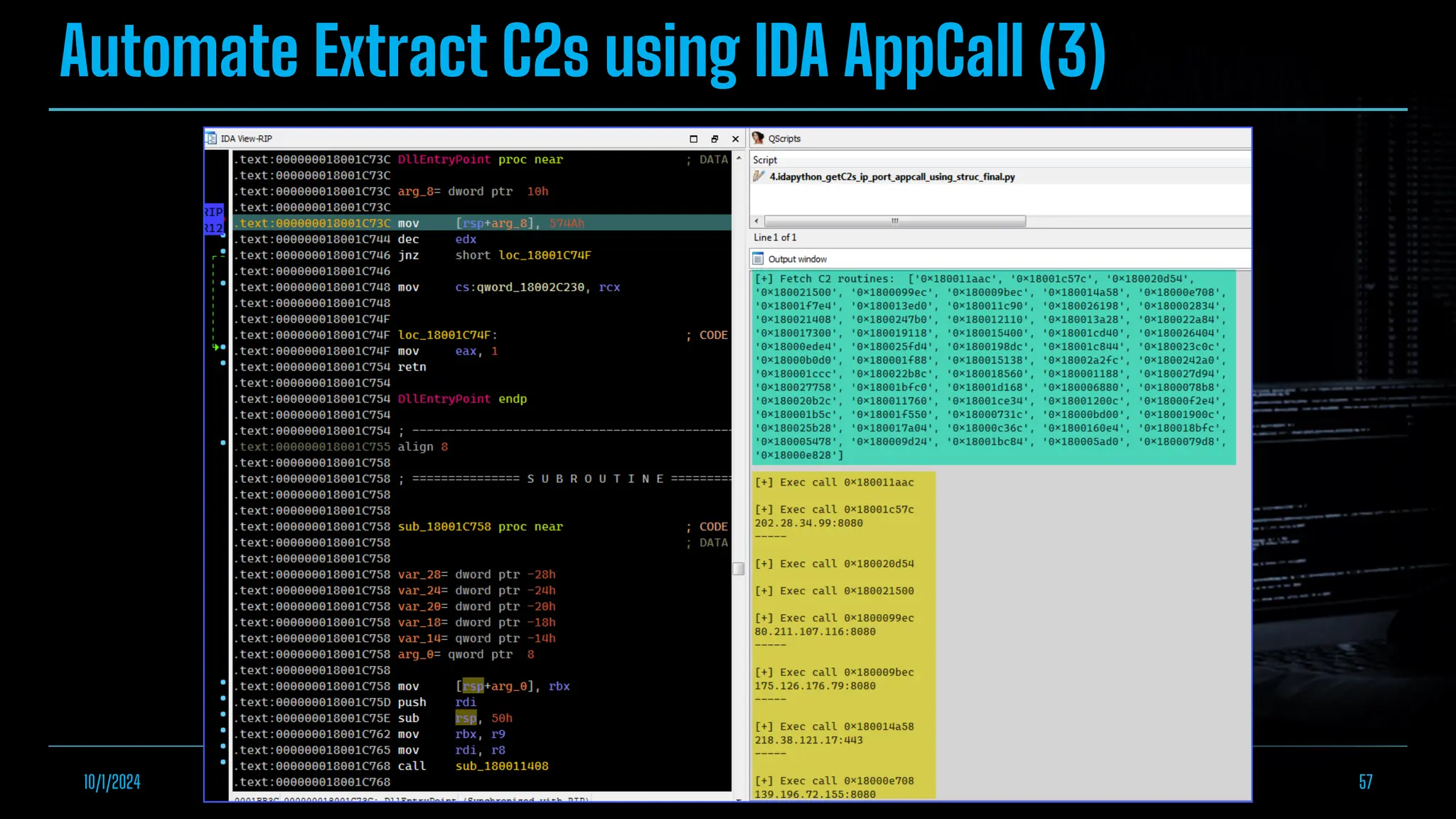
The document discusses empowering malware analysis using the IDA appcall feature, presenting its functions and applications in analyzing different malware types. Key topics include recovering API names, decrypting strings, and extracting configurations from malware like Lokibot and Emotet. It includes examples, analyses, and resources for reversing techniques, aimed at enhancing malware analysis skills.