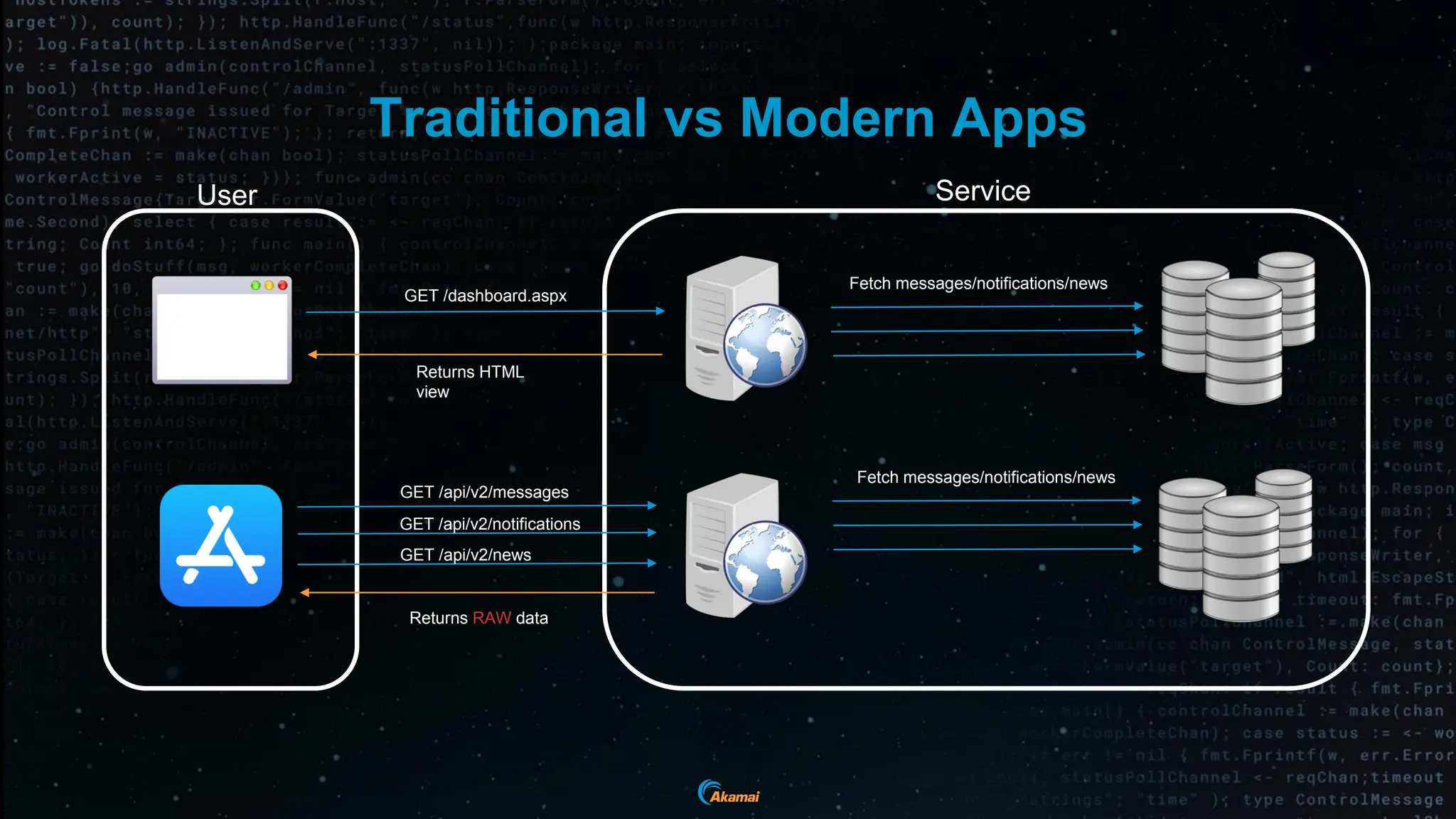
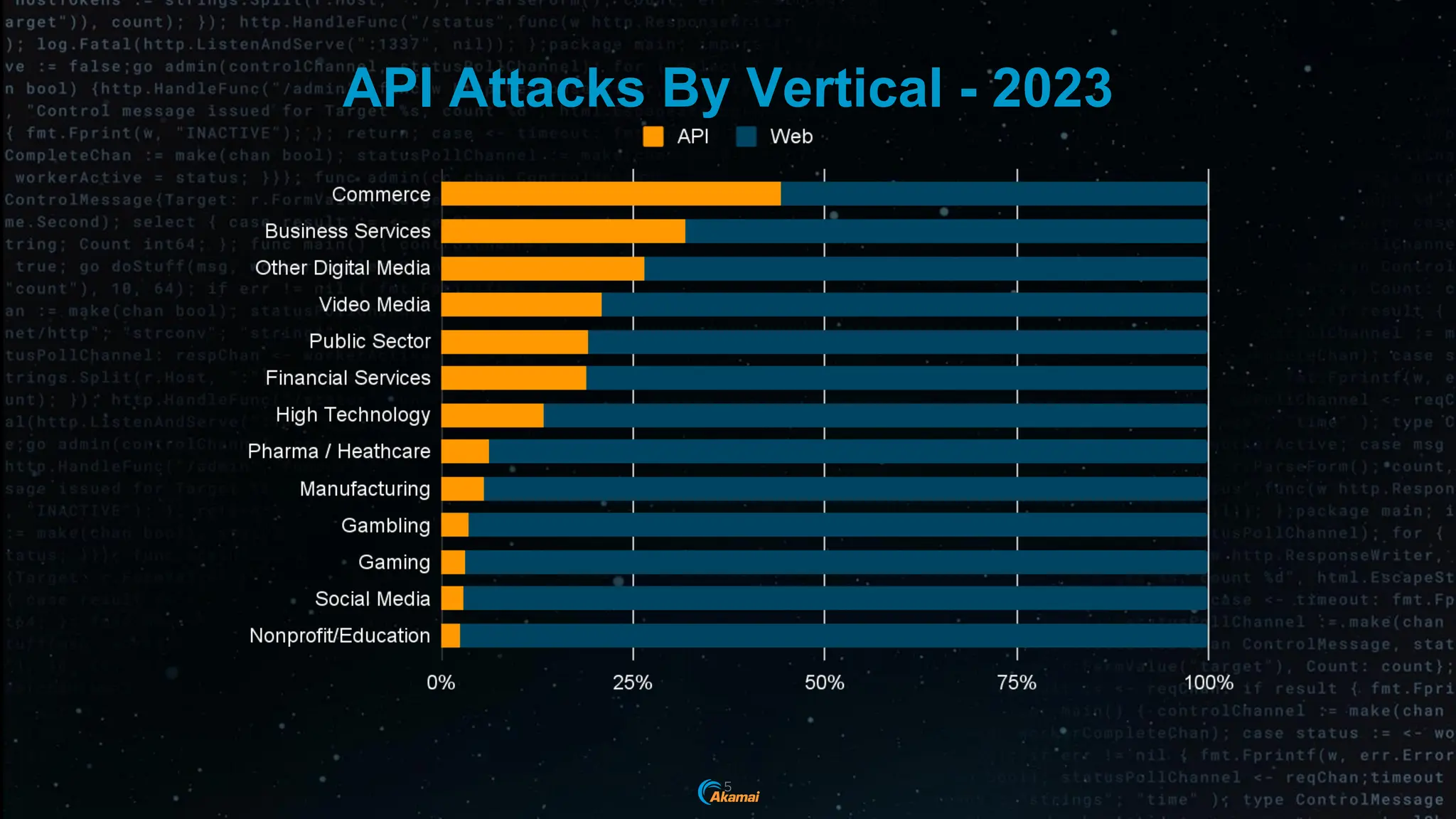
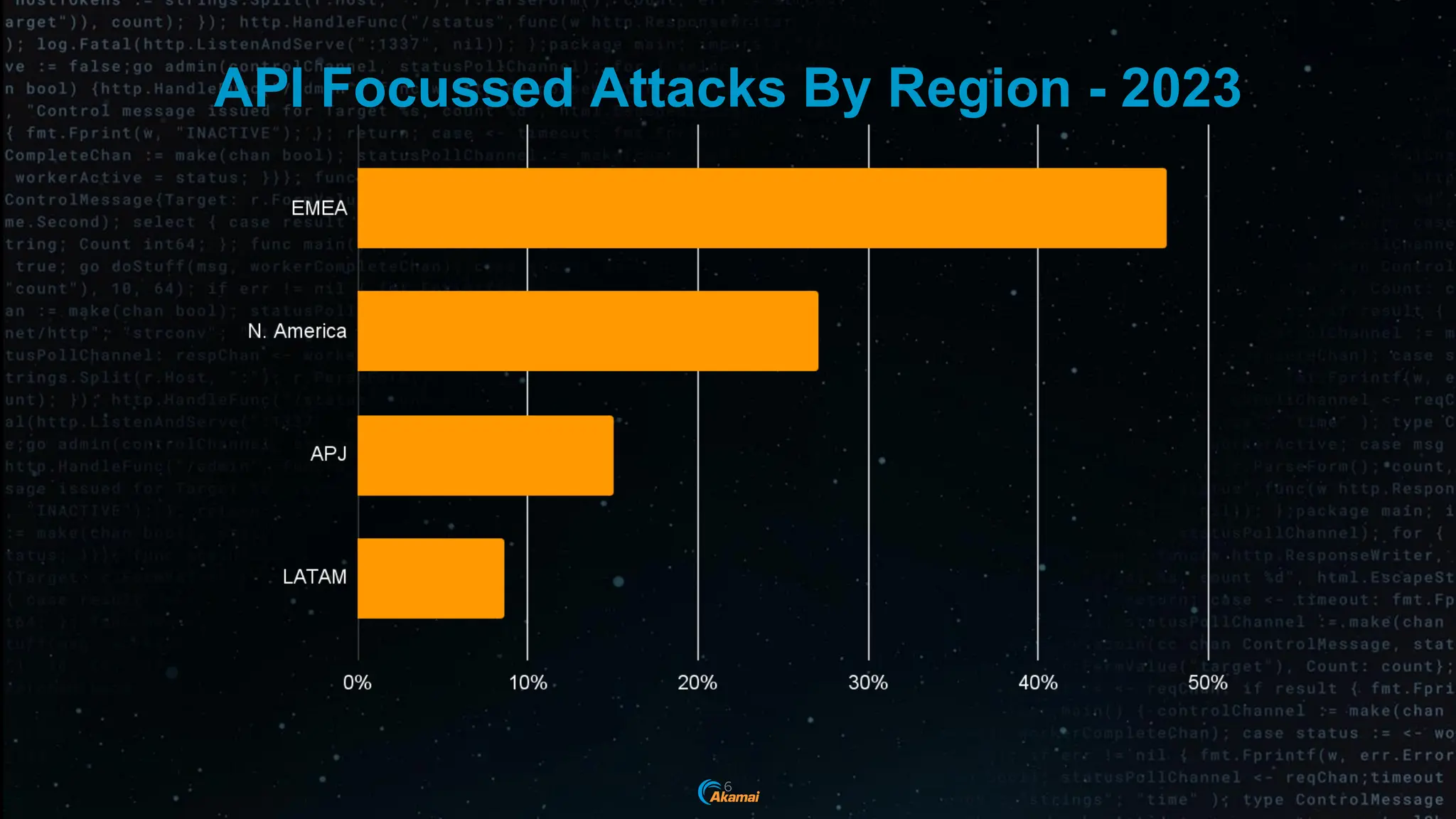
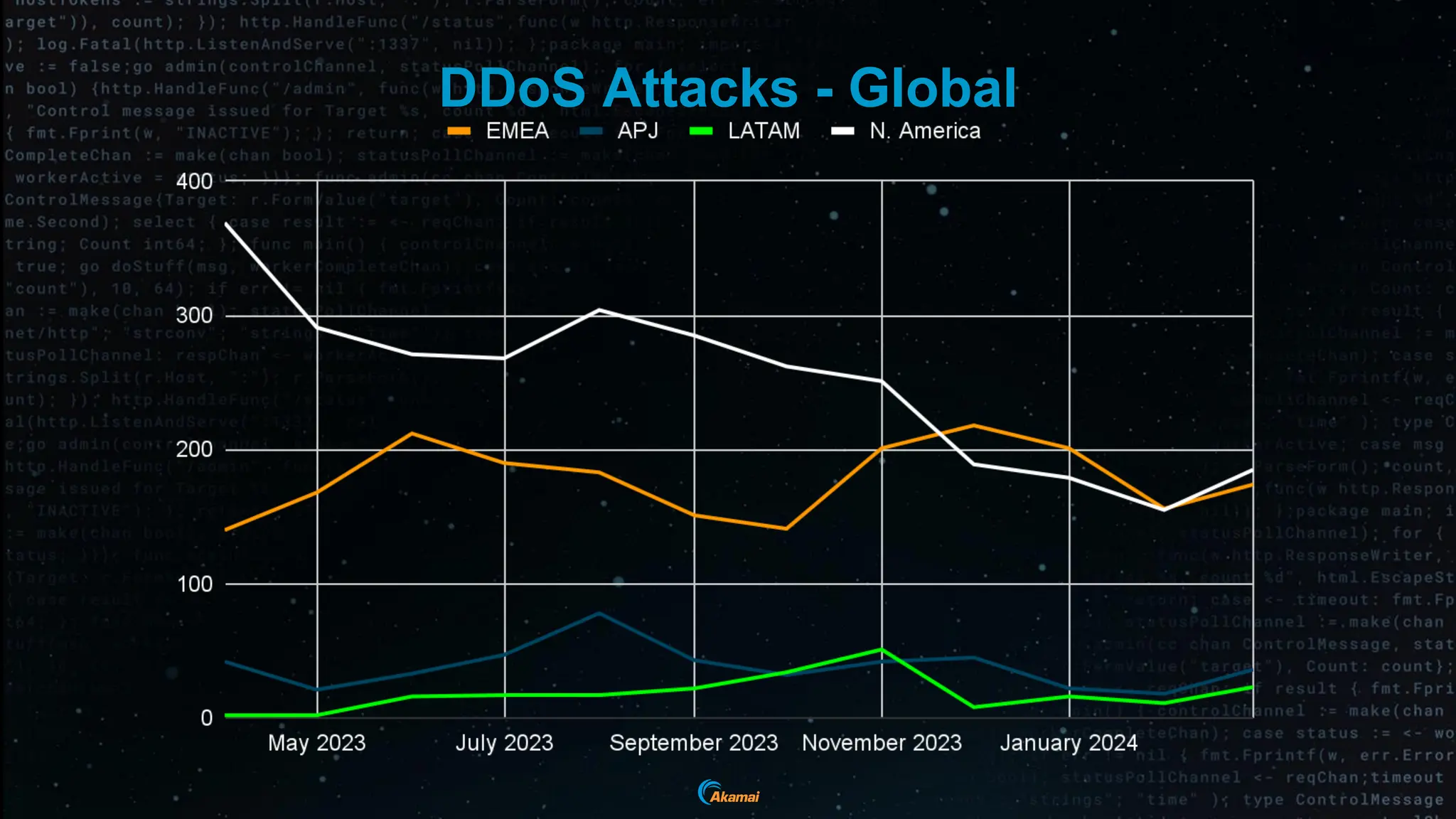
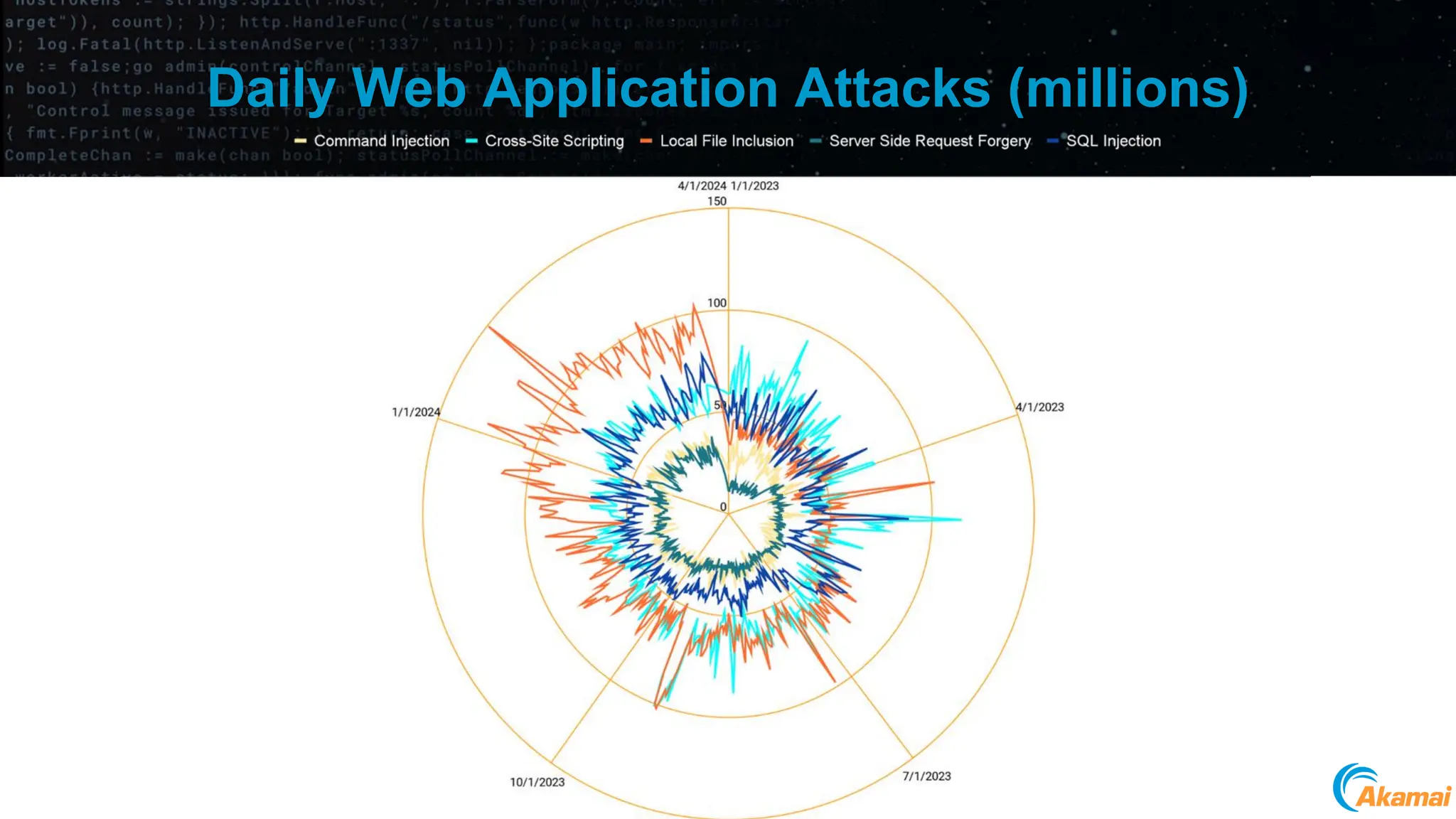
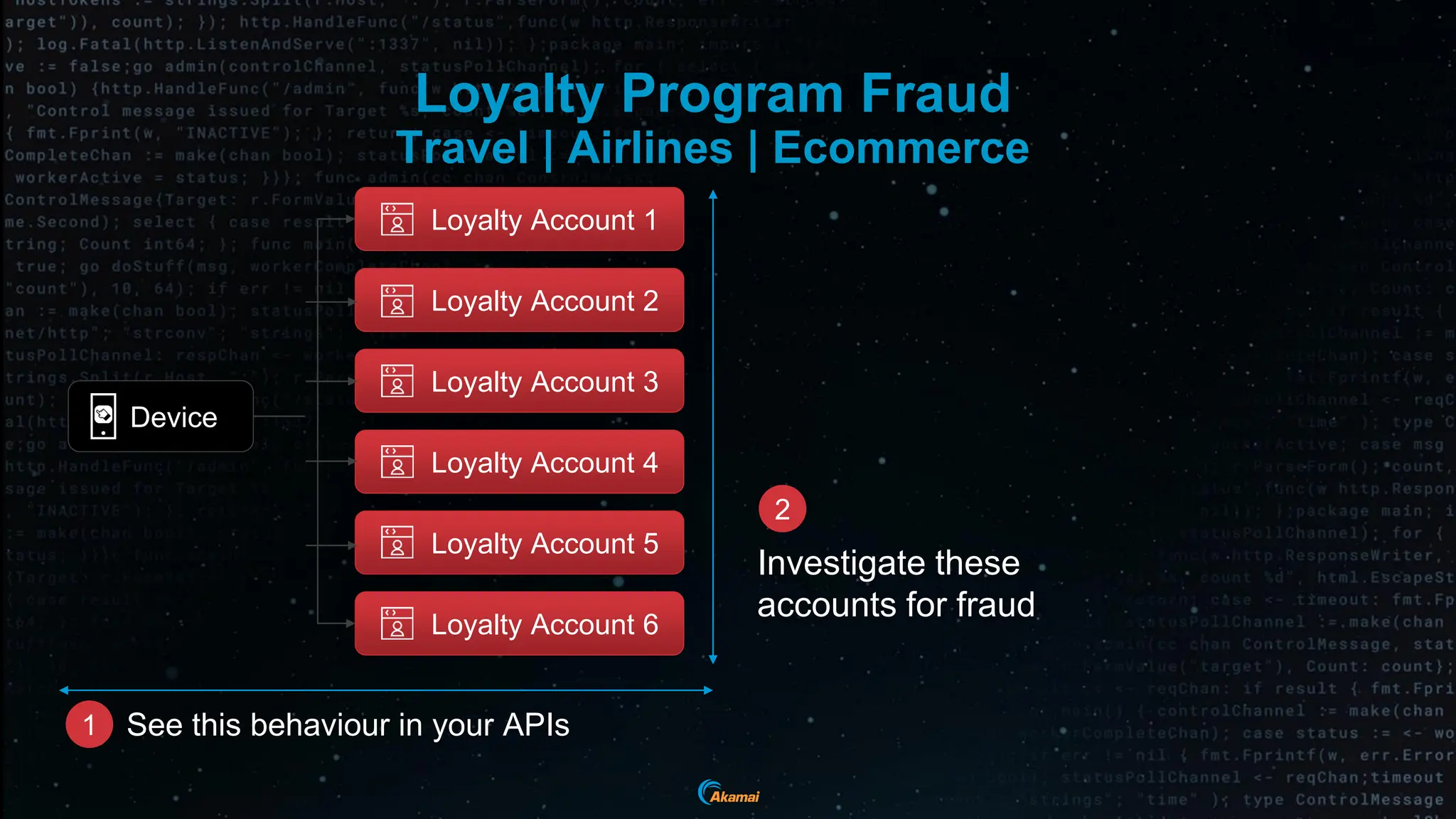
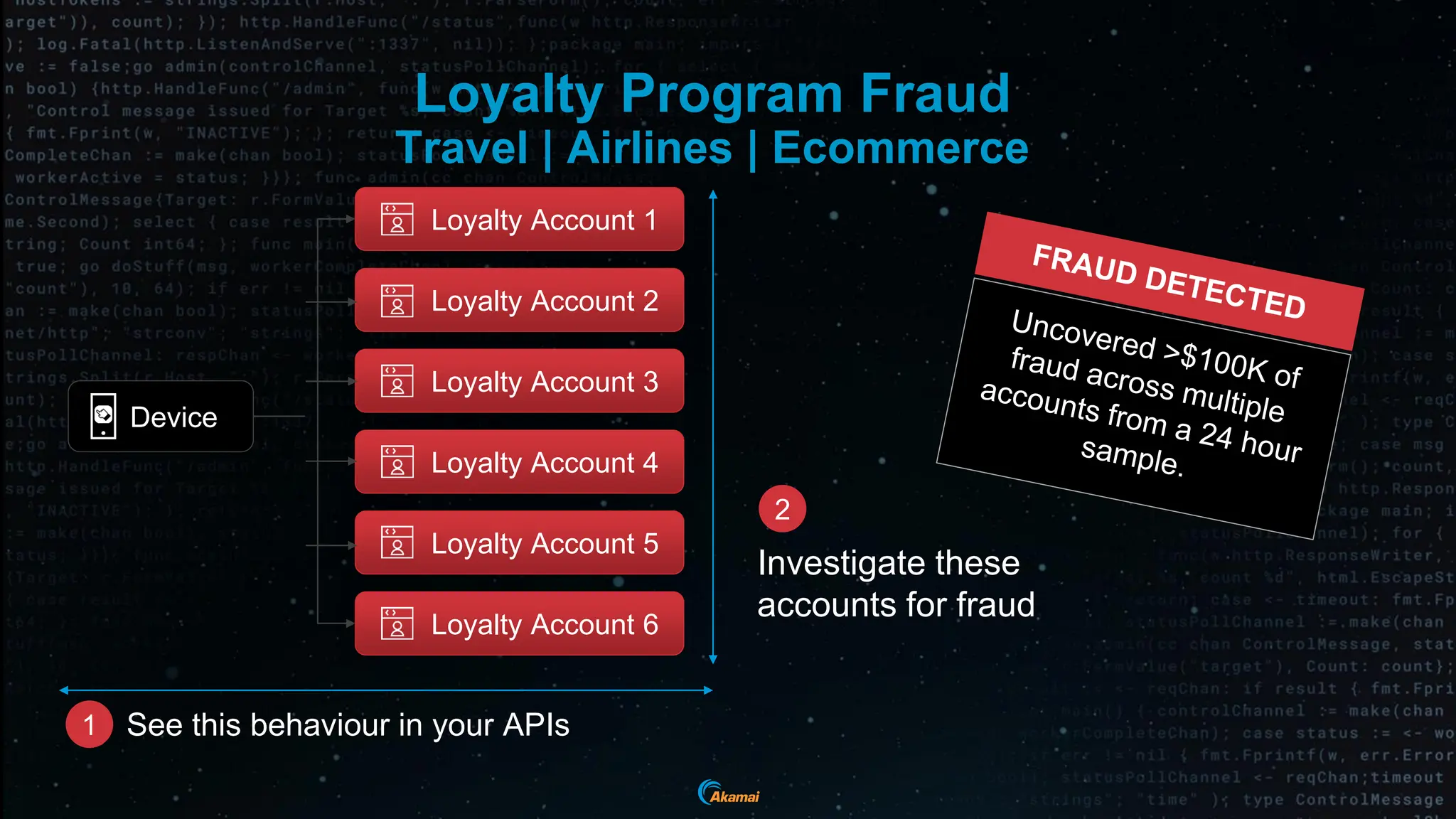
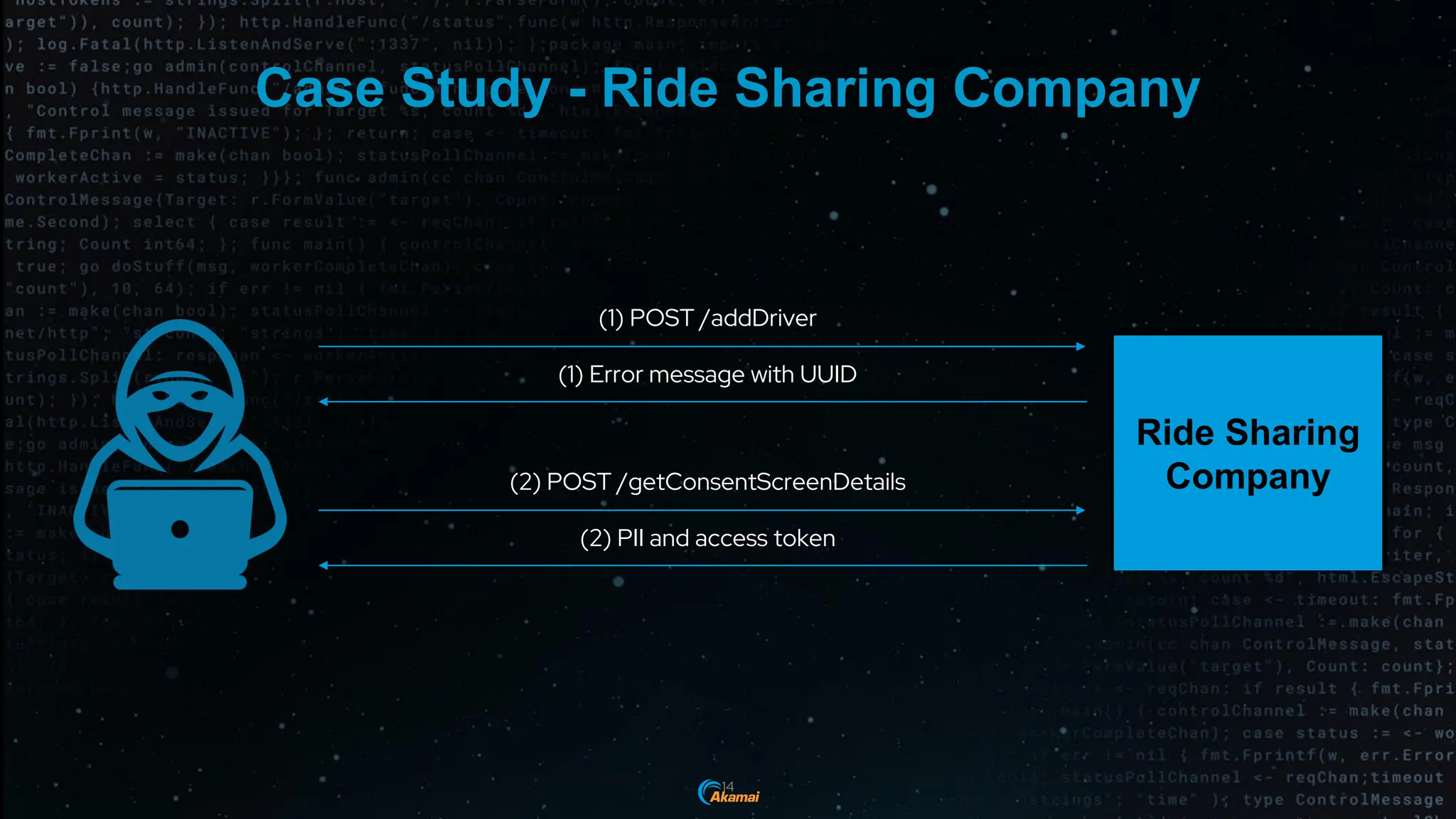
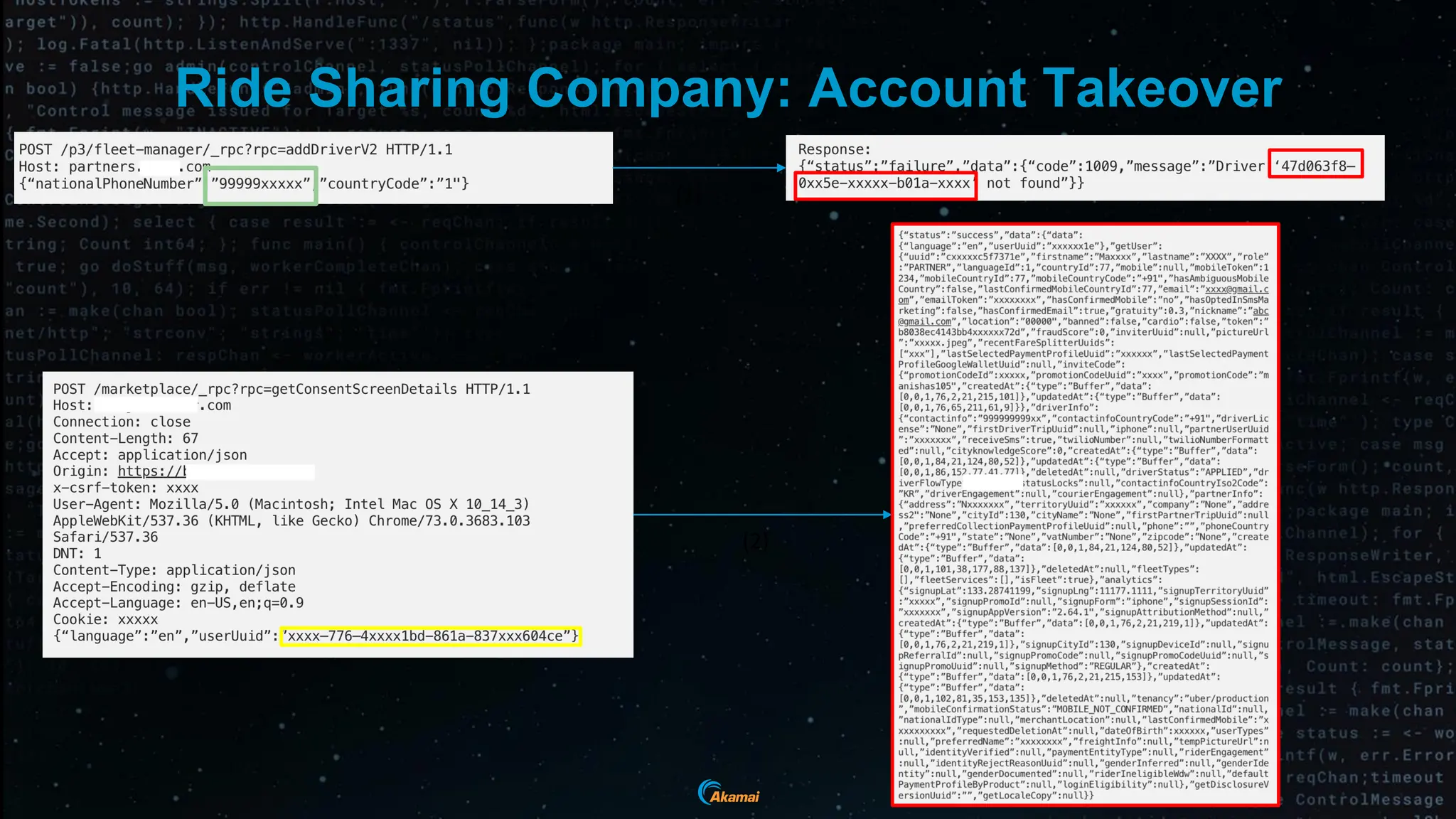
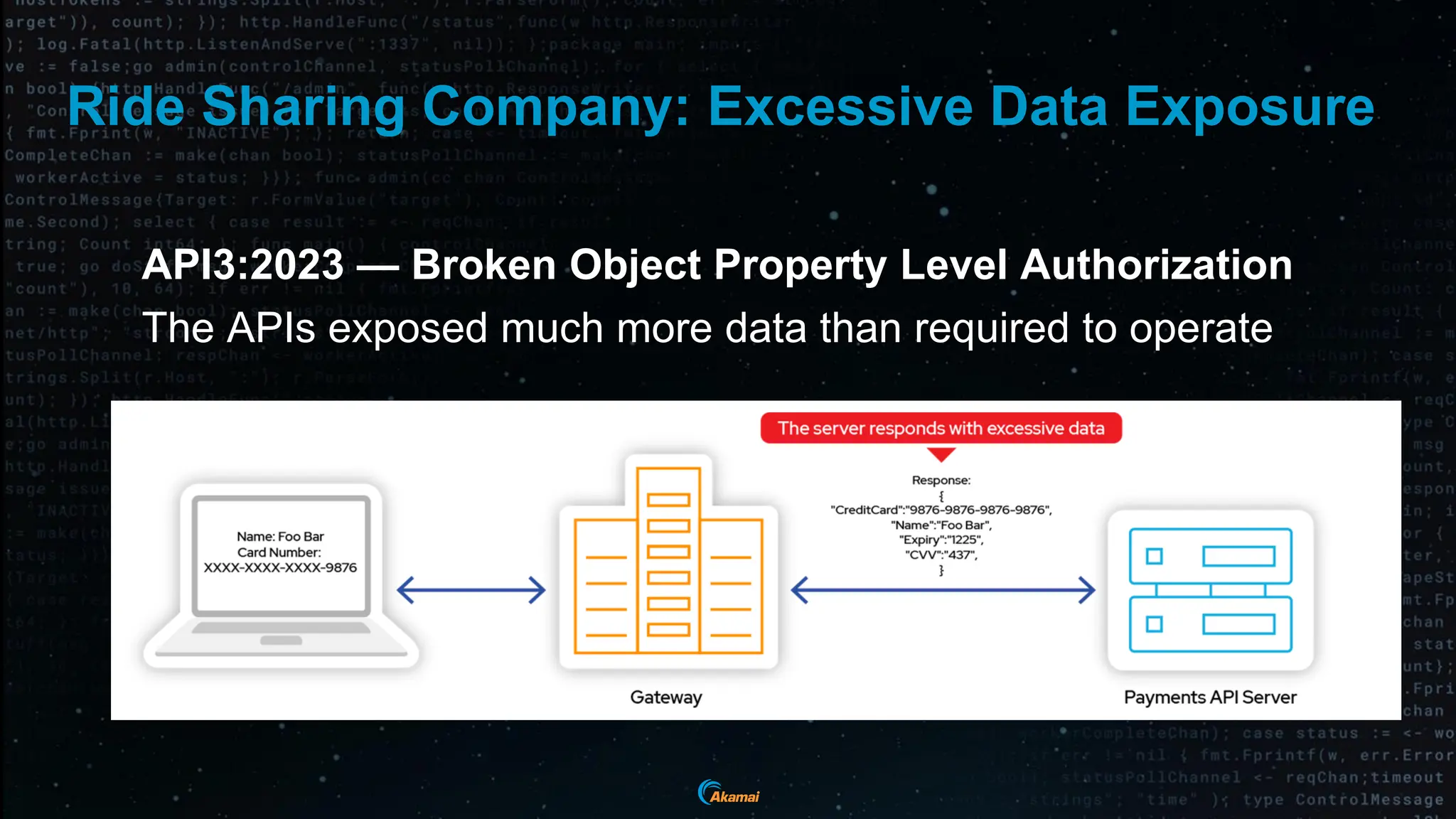
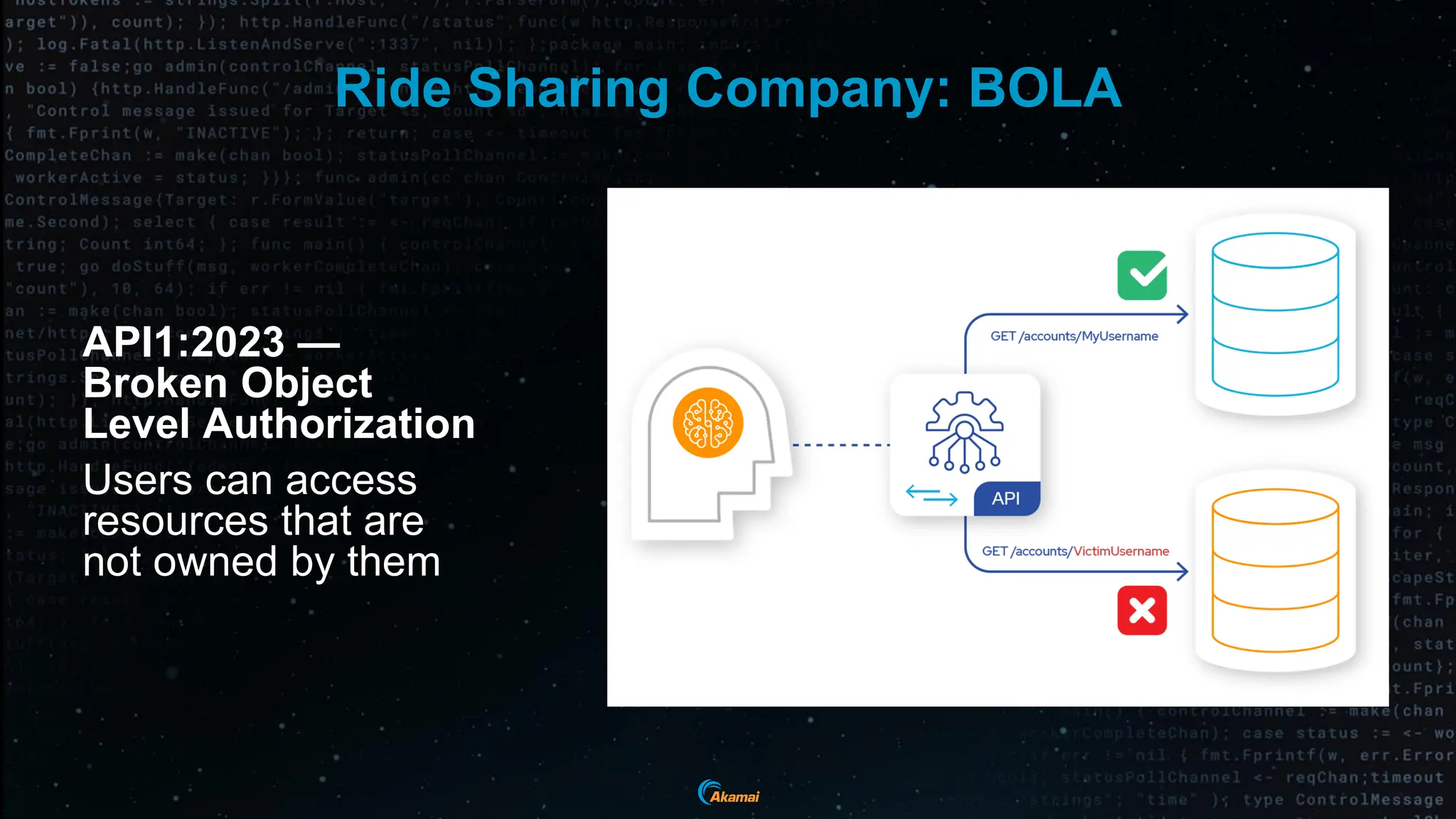
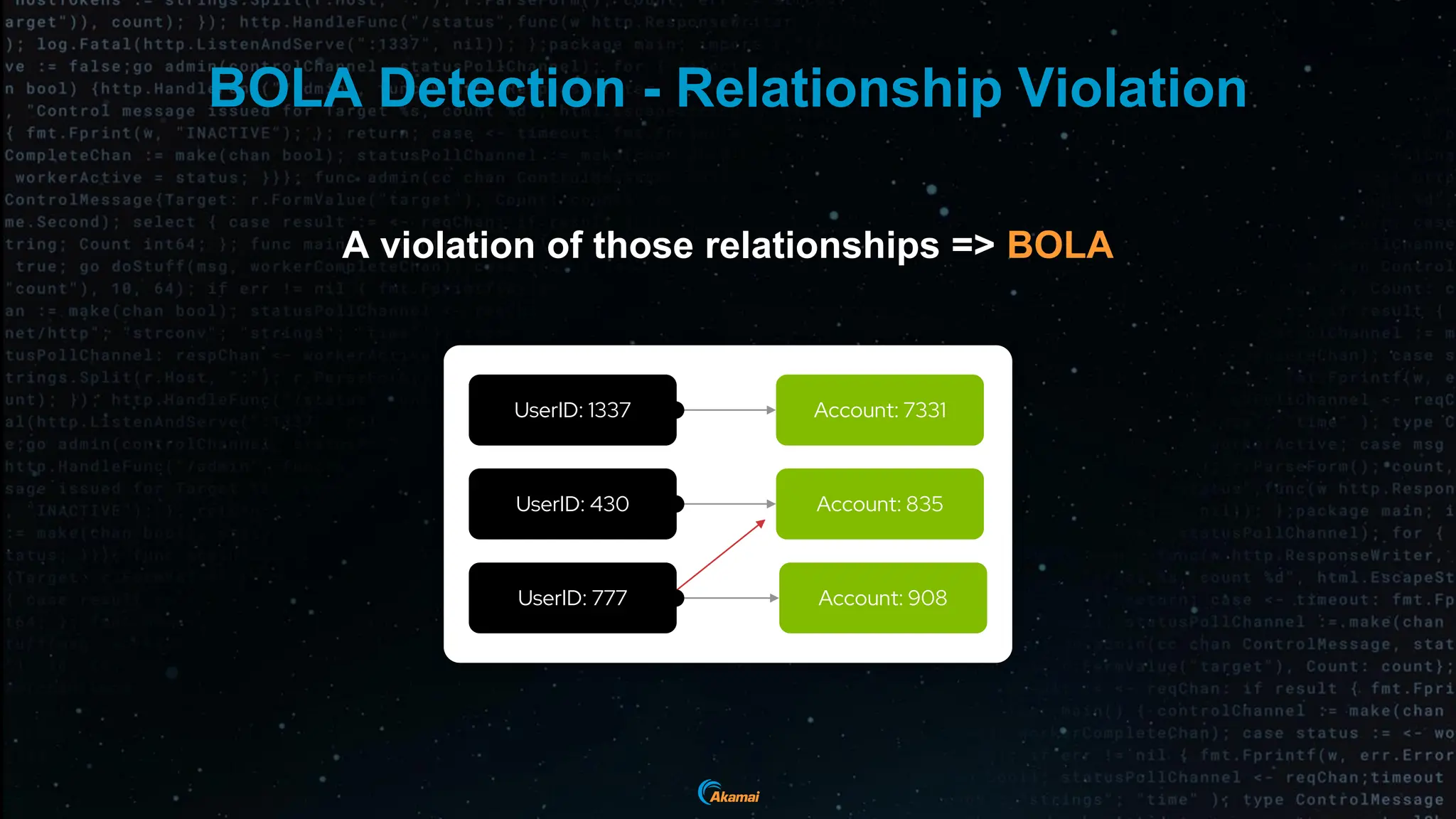
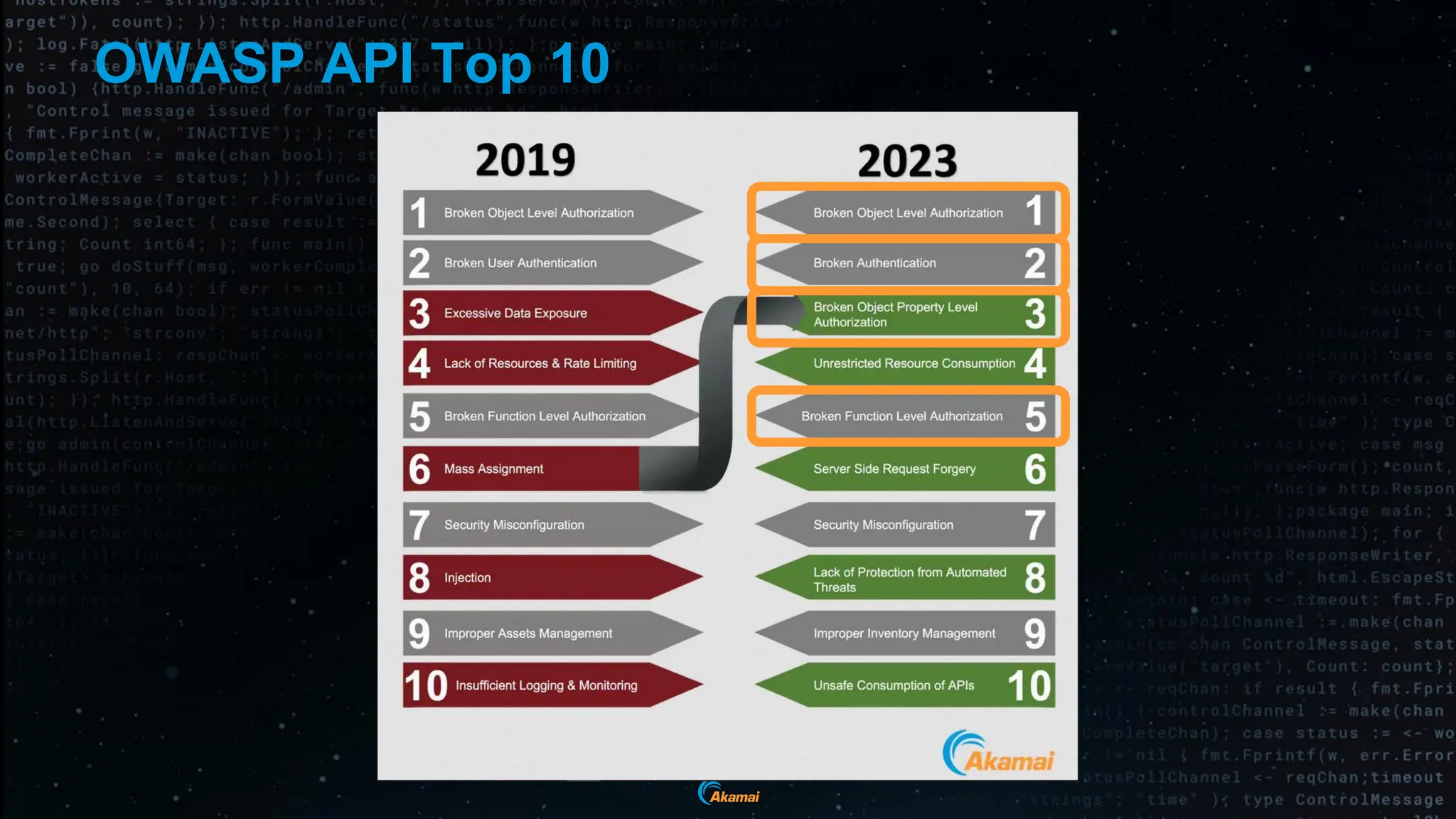
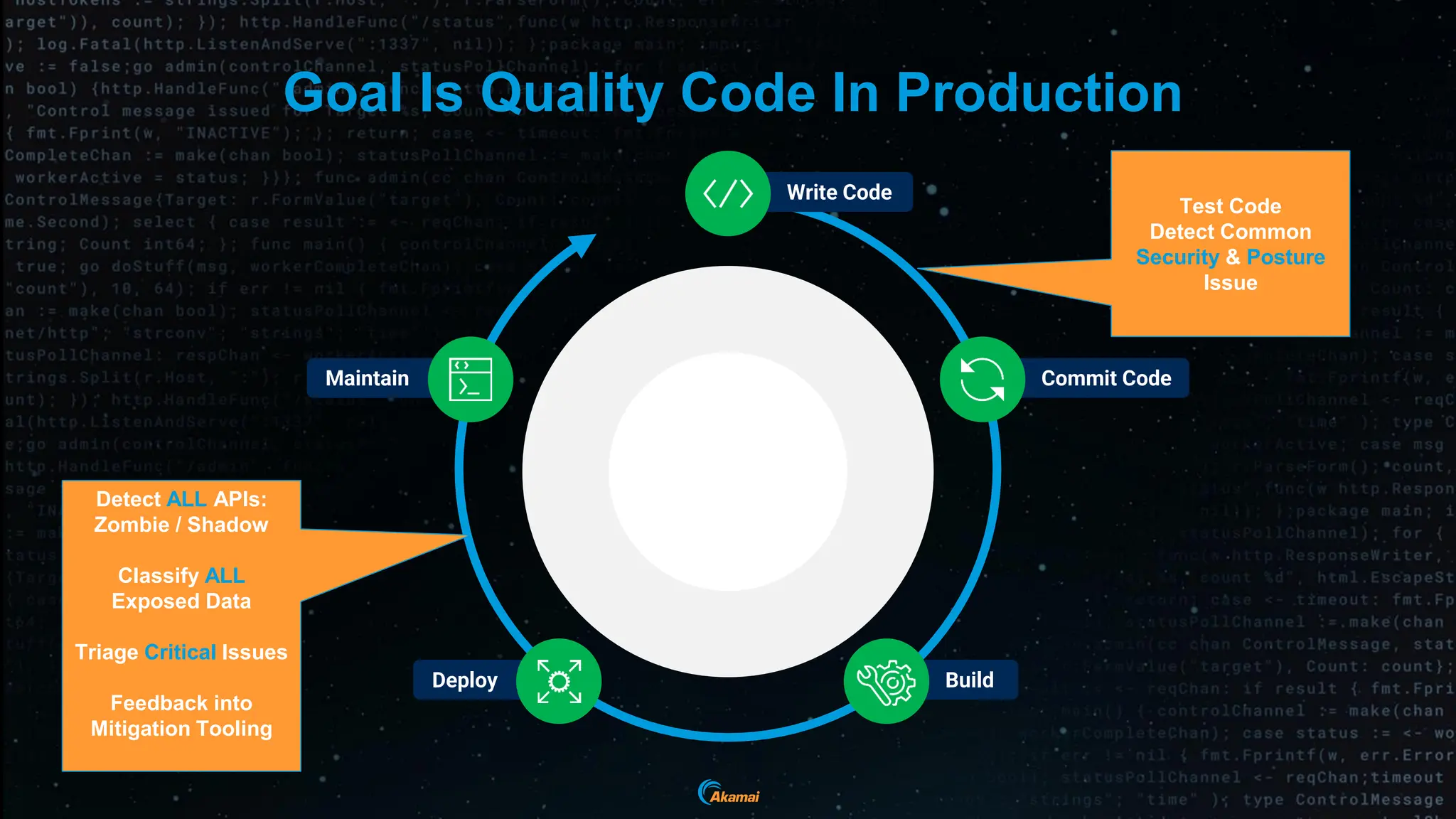
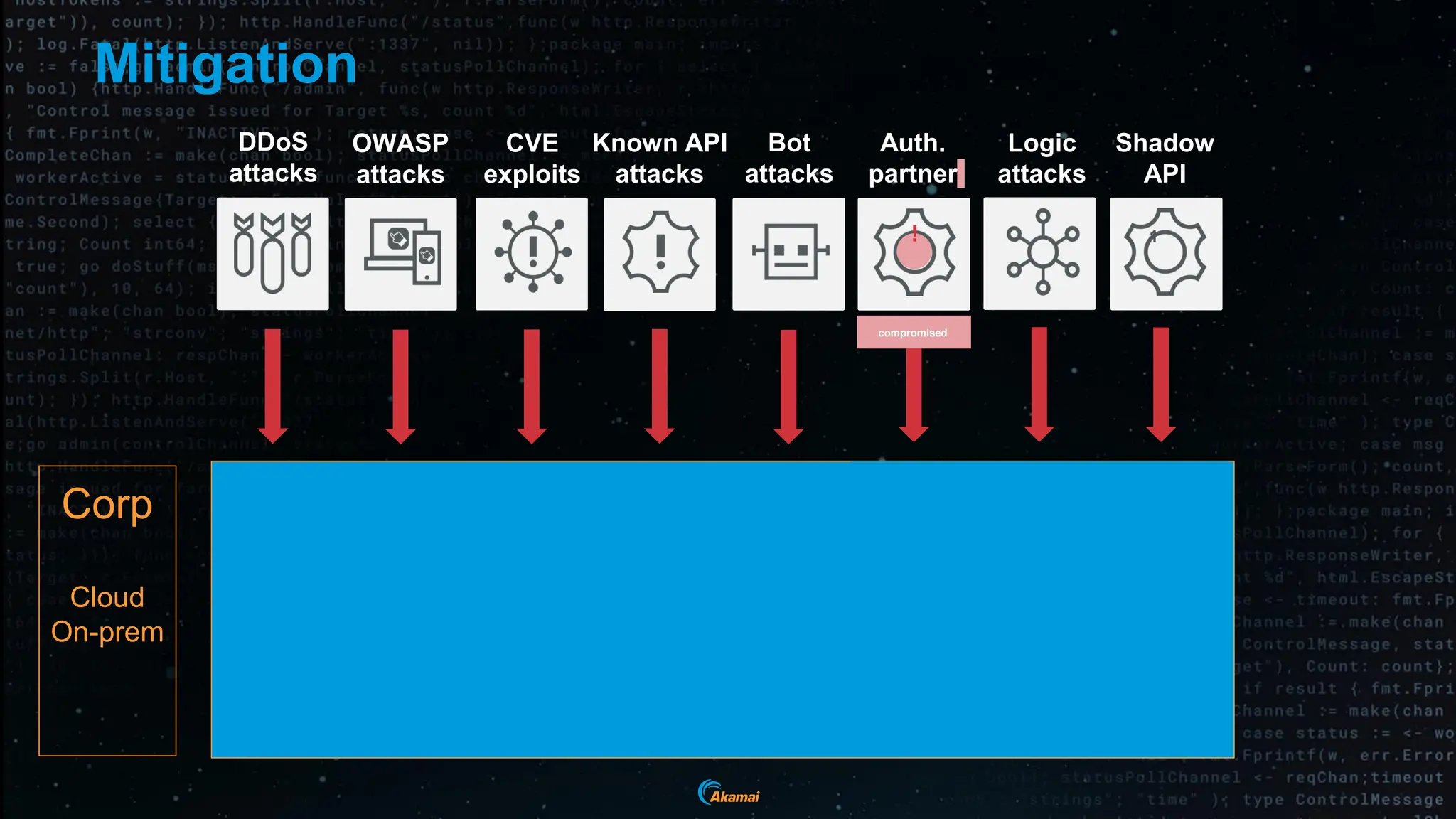
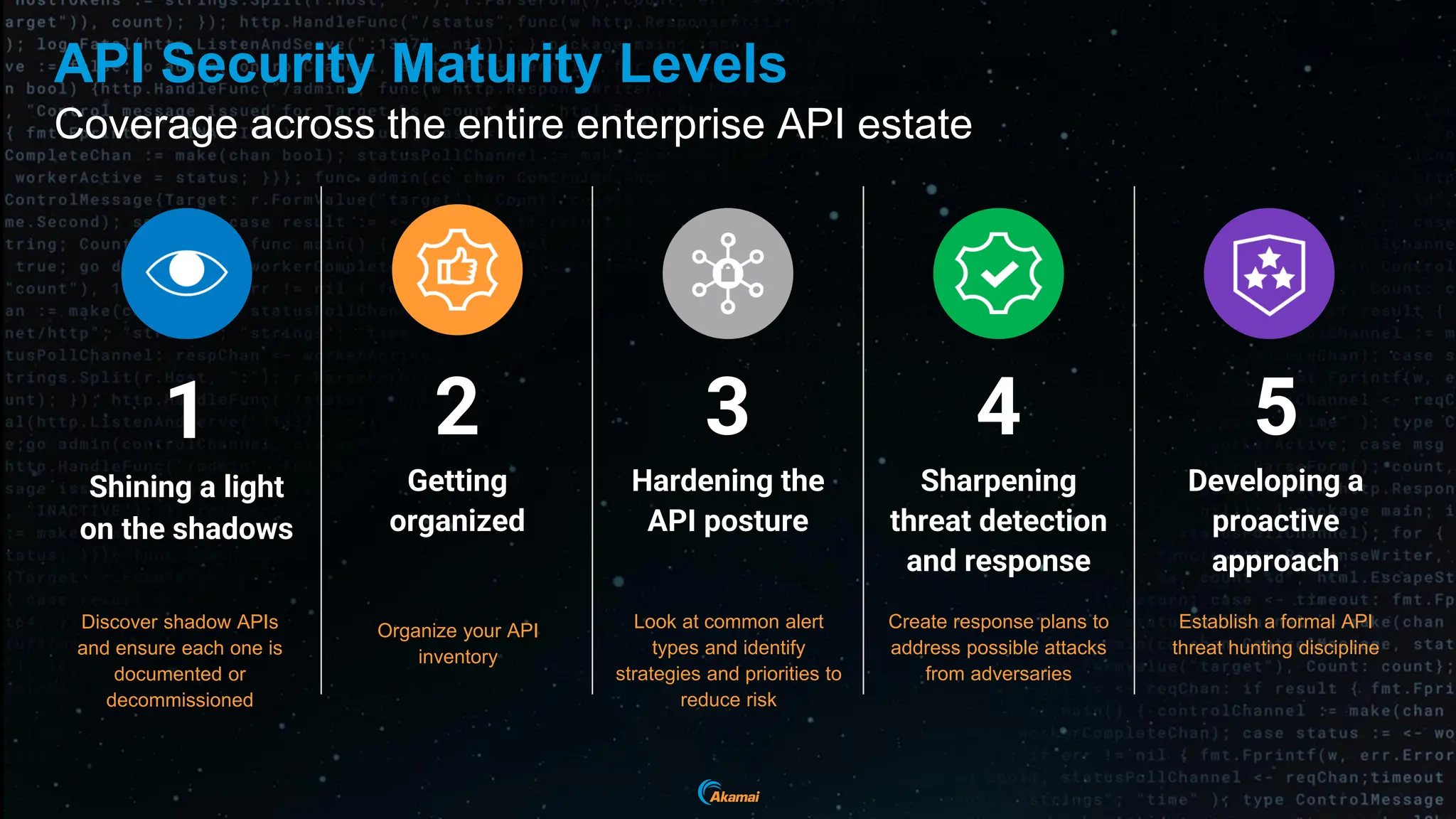
The document discusses the rising security challenges posed by APIs, highlighting common attack vectors such as DDoS, injection, and business logic abuse. It emphasizes the importance of understanding API exposure and implementing protective measures to prevent attacks, similar to past mistakes made with web security. The takeaway is that APIs are a primary target for attacks, and organizations must ensure adequate security and inventory management of their API landscape.