Aizatulin poster
•
0 likes•418 views
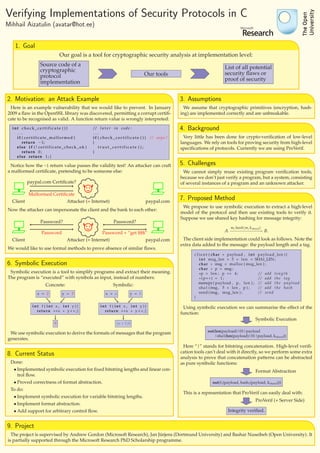
1. The goal is to develop a tool that analyzes cryptographic protocol implementations at the source code level to detect potential security flaws or prove security. 2. As motivation, the document describes a 2009 vulnerability in OpenSSL that allowed a corrupted certificate to be incorrectly validated due to a faulty return value check. 3. The tool assumes cryptographic primitives are correctly implemented but aims to verify security at the implementation level rather than just the high-level specification.
Report
Share
Report
Share
Download to read offline
Recommended
Aizatulin slides-4-3

The document describes a goal of developing a tool for automated security analysis of cryptographic protocol implementations written in C. It aims to take source code as input, perform a sound and scalable analysis, and output either known security flaws or a proof of security. Symbolic execution is proposed as a method to simplify programs and extract their meaning, mapping low-level C code to a formal language model that can be analyzed by existing tools like ProVerif. Current status is that symbolic execution has been implemented for fixed bitstring lengths and linear control flow. Further work is needed to support variable lengths, arbitrary control flow, and full format abstraction before integrating with a protocol verifier.
Secure Obfuscation for Encrypted Signatures

The document proposes a method to securely obfuscate an encrypted signature scheme. It describes using Waters' signature scheme combined with a linear encryption scheme to create an encrypted signature program. The main result is a proof that this encrypted signature program can be securely obfuscated in the standard model under the decision linear assumption, preserving the security of the underlying signature scheme.
Offensive cyber security: Smashing the stack with Python

: A necessary step in writing secure code is having an understanding of how vulnerable code can be exploited. This step is critical because unless you see the software from the vantage point of a hacker, what may look to be safe and harmless code, can have multiple vulnerabilities that result in systems running that software getting p0wned. The goal of this tech talk is to provide a step-by-step illustration of how not adhering to secure software design principles such as properly bounds checking buffers can open up computing devices to exploitation. Specifically, we will show that by using a very easy to use scripting language like python, we can do the following: 1) Smash the stack of a system running vulnerable code to gain arbitrary access. 2) Install a key logger that can phone home to a command and control server.
15.Security

Senthilkanth,MCA..
The following ppt's full topic covers Operating System for BSc CS, BCA, MSc CS, MCA students..
1.Introduction
2.OS Structures
3.Process
4.Threads
5.CPU Scheduling
6.Process Synchronization
7.Dead Locks
8.Memory Management
9.Virtual Memory
10.File system Interface
11.File system implementation
12.Mass Storage System
13.IO Systems
14.Protection
15.Security
16.Distributed System Structure
17.Distributed File System
18.Distributed Co Ordination
19.Real Time System
20.Multimedia Systems
21.Linux
22.Windows
Cryptography and network security

This document provides an overview of cryptography including:
1. Cryptography is the process of encoding messages to protect information and ensure confidentiality, integrity, authentication and other security goals.
2. There are symmetric and asymmetric encryption algorithms that use the same or different keys for encryption and decryption. Examples include AES, RSA, and DES.
3. Other techniques discussed include digital signatures, visual cryptography, and ways to implement cryptography like error diffusion and halftone visual cryptography.
Cs8792 cns - Public key cryptosystem (Unit III)

This document provides an overview of public key cryptography and asymmetric key ciphers. It begins with the underlying mathematics including primes, primality testing, factorization, Euler's totient function, Fermat's theorem, and exponentiation. It then discusses asymmetric key ciphers like RSA and Diffie-Hellman key exchange. RSA is described in more detail, including how public and private key pairs are generated using large prime numbers and exponentiation modulo a composite integer. Security relies on the difficulty of factoring large numbers.
Kleptography

The document discusses kleptography, which is the study of secretly stealing cryptographic information in a way that cannot be detected. It proposes a technique called a Secretly Embedded Trapdoor with Universal Protection (SETUP) that allows an attacker to steal private keys or other secret information from cryptosystems in a way that is undetectable, even if the cryptosystem is reverse engineered. Specifically, it describes how a SETUP could be used to steal private RSA keys during key generation or compromise the Diffie-Hellman key exchange. The goal of kleptography and a SETUP is to allow an attacker to obtain secret information like private keys in a way that cannot be detected by users, reverse engineers, or other attackers
Security Tools Foss

This document provides an overview of security tools that can be used in software development. It discusses coding standards, compiler warnings, version control, design for security, testing, and analysis tools. Coding standards and following compiler warnings can help catch simple errors. Version control allows reviewing changes and implementing hooks to catch issues early. Designing for security from the start is important. Testing on multiple levels from units to full systems helps improve quality. Static and dynamic analysis tools can find bugs without or during execution. Overall, applying security best practices throughout the development cycle leads to higher quality software.
Recommended
Aizatulin slides-4-3

The document describes a goal of developing a tool for automated security analysis of cryptographic protocol implementations written in C. It aims to take source code as input, perform a sound and scalable analysis, and output either known security flaws or a proof of security. Symbolic execution is proposed as a method to simplify programs and extract their meaning, mapping low-level C code to a formal language model that can be analyzed by existing tools like ProVerif. Current status is that symbolic execution has been implemented for fixed bitstring lengths and linear control flow. Further work is needed to support variable lengths, arbitrary control flow, and full format abstraction before integrating with a protocol verifier.
Secure Obfuscation for Encrypted Signatures

The document proposes a method to securely obfuscate an encrypted signature scheme. It describes using Waters' signature scheme combined with a linear encryption scheme to create an encrypted signature program. The main result is a proof that this encrypted signature program can be securely obfuscated in the standard model under the decision linear assumption, preserving the security of the underlying signature scheme.
Offensive cyber security: Smashing the stack with Python

: A necessary step in writing secure code is having an understanding of how vulnerable code can be exploited. This step is critical because unless you see the software from the vantage point of a hacker, what may look to be safe and harmless code, can have multiple vulnerabilities that result in systems running that software getting p0wned. The goal of this tech talk is to provide a step-by-step illustration of how not adhering to secure software design principles such as properly bounds checking buffers can open up computing devices to exploitation. Specifically, we will show that by using a very easy to use scripting language like python, we can do the following: 1) Smash the stack of a system running vulnerable code to gain arbitrary access. 2) Install a key logger that can phone home to a command and control server.
15.Security

Senthilkanth,MCA..
The following ppt's full topic covers Operating System for BSc CS, BCA, MSc CS, MCA students..
1.Introduction
2.OS Structures
3.Process
4.Threads
5.CPU Scheduling
6.Process Synchronization
7.Dead Locks
8.Memory Management
9.Virtual Memory
10.File system Interface
11.File system implementation
12.Mass Storage System
13.IO Systems
14.Protection
15.Security
16.Distributed System Structure
17.Distributed File System
18.Distributed Co Ordination
19.Real Time System
20.Multimedia Systems
21.Linux
22.Windows
Cryptography and network security

This document provides an overview of cryptography including:
1. Cryptography is the process of encoding messages to protect information and ensure confidentiality, integrity, authentication and other security goals.
2. There are symmetric and asymmetric encryption algorithms that use the same or different keys for encryption and decryption. Examples include AES, RSA, and DES.
3. Other techniques discussed include digital signatures, visual cryptography, and ways to implement cryptography like error diffusion and halftone visual cryptography.
Cs8792 cns - Public key cryptosystem (Unit III)

This document provides an overview of public key cryptography and asymmetric key ciphers. It begins with the underlying mathematics including primes, primality testing, factorization, Euler's totient function, Fermat's theorem, and exponentiation. It then discusses asymmetric key ciphers like RSA and Diffie-Hellman key exchange. RSA is described in more detail, including how public and private key pairs are generated using large prime numbers and exponentiation modulo a composite integer. Security relies on the difficulty of factoring large numbers.
Kleptography

The document discusses kleptography, which is the study of secretly stealing cryptographic information in a way that cannot be detected. It proposes a technique called a Secretly Embedded Trapdoor with Universal Protection (SETUP) that allows an attacker to steal private keys or other secret information from cryptosystems in a way that is undetectable, even if the cryptosystem is reverse engineered. Specifically, it describes how a SETUP could be used to steal private RSA keys during key generation or compromise the Diffie-Hellman key exchange. The goal of kleptography and a SETUP is to allow an attacker to obtain secret information like private keys in a way that cannot be detected by users, reverse engineers, or other attackers
Security Tools Foss

This document provides an overview of security tools that can be used in software development. It discusses coding standards, compiler warnings, version control, design for security, testing, and analysis tools. Coding standards and following compiler warnings can help catch simple errors. Version control allows reviewing changes and implementing hooks to catch issues early. Designing for security from the start is important. Testing on multiple levels from units to full systems helps improve quality. Static and dynamic analysis tools can find bugs without or during execution. Overall, applying security best practices throughout the development cycle leads to higher quality software.
Embedded device hacking Session i

The goal of the workshop is to provide a hands-on introduction to key pen-testing tools and concepts that white-hat and black-hat hackers utilize to find and exploit vulnerabilities in real-world embedded devices.
661 665

This document discusses a differential cryptanalysis attack on the RC4 stream cipher. It begins by describing how RC4 encryption works, including the key scheduling algorithm and pseudo-random generation algorithm. It then explains differential cryptanalysis, where two keys that differ in only a few bytes are used to analyze differences in the generated key streams. As an example, it analyzes a differential attack on RC4 using an 8-byte state and key where the keys differ in the last byte. The attack is demonstrated by generating key streams for two similar keys and analyzing the differences to find flaws in the cipher.
PowerShell Inside Out: Applied .NET Hacking for Enhanced Visibility by Satosh...

In response to the emerging use of PowerShell by attackers, Microsoft released a feature called Anti-Malware Scan Interface (AMSI) in Windows 10, allowing 3rd party companies, as well as Microsoft itself, to gain more visibility into PowerShell and other scripting engines. Since this release, various research has been done on the effectiveness of AMSI, revealing its efficacy as well as its inherent weaknesses.
Despite this advance, however, many security vendors have yet to add AMSI support in their products, perhaps due to its limited platform coverage. On the other hand, red teamers and adversaries have quickly equipped themselves with techniques which attack the weaknesses of AMSI and bypass it, making detection and prevention of PowerShell attacks even harder.
This talk will discuss how to gain greater visibility into managed program execution, especially for PowerShell, using a .NET native code hooking technique to help organizations protect themselves from such advanced attacker techniques. In this session, we will demonstrate how to enhance capabilities provided by AMSI and how to overcome its limitations, through a realistic implementation of the technique, all while analyzing the internals of .NET Framework and the PowerShell engine.
Ch34508510

International Journal of Engineering Research and Applications (IJERA) is an open access online peer reviewed international journal that publishes research and review articles in the fields of Computer Science, Neural Networks, Electrical Engineering, Software Engineering, Information Technology, Mechanical Engineering, Chemical Engineering, Plastic Engineering, Food Technology, Textile Engineering, Nano Technology & science, Power Electronics, Electronics & Communication Engineering, Computational mathematics, Image processing, Civil Engineering, Structural Engineering, Environmental Engineering, VLSI Testing & Low Power VLSI Design etc.
Latest C Interview Questions and Answers

3. What is a register variable?
Register variables are stored in the CPU registers. Its default value is a garbage value. Scope of a register variable is local to the block in which it is defined. Lifetime is till control remains within the block in which the register variable is defined. Variable stored in a CPU register can always be accessed faster than the one that is stored in memory. Therefore, if a variable is used at many places in a program, it is better to declare its storage class as register
Example: register int x=5;
Variables for loop counters can be declared as register. Note that register keyword may be ignored by some compilers.
4. Where is an auto variables stored?
Main memory and CPU registers are the two memory locations where auto variables are stored. Auto variables are defined under automatic storage class. They are stored in main memory. Memory is allocated to an automatic variable when the block which contains it is called and it is de-allocated at the completion of its block
execution.
Auto variables:
Storage
:
main memory.
Default value
:
garbage value.
Scope
:
local to the block in which the variable is defined.
Lifetime
:
till the control remains within the block in which the variable is defined.
5. What is scope & storage allocation of extern and global variables?
Extern variables: belong to the External storage class and are stored in the main memory. extern is used when we have to refer a function or variable that is implemented in another file in the same project. The scope of the extern variables is Global.
Network Security

The document discusses and provides code examples for implementing several cryptographic algorithms, including Diffie-Hellman key exchange, RSA encryption, Caesar cipher, RC4 stream cipher, and monoalphabetic cipher. It first explains the Diffie-Hellman protocol for generating a shared secret key between two parties. It then shows Java code to implement Diffie-Hellman. It also discusses RSA encryption and provides Java code to encrypt and decrypt messages. Further code examples demonstrate how to implement the Caesar cipher, RC4 stream cipher, and monoalphabetic cipher in Java.
SecurePtrs: Proving Secure Compilation with Data-Flow Back-Translation and Tu...

[PriSC 2022 talk: https://popl22.sigplan.org/home/prisc-2022#program]
Proving secure compilation of partial programs typically requires back-translating a target attack against the compiled program to an attack against the source program. To prove this back-translation step, one can syntactically translate the target attacker to a source one -- i.e., syntax-directed back-translation -- or show that the interaction traces of the target attacker can also be produced by source attackers -- i.e., trace-directed back-translation.
Syntax-directed back-translation is not suitable when the target attacker uses unstructured control flow that the source language cannot directly represent. Trace-directed back-translation works with such syntactic dissimilarity because only the external interactions of the target attacker have to be mimicked in the source, not its internal control flow. Revealing only external interactions is, however, inconvenient when sharing memory via unforgeable pointers, since information about stashed pointers to shared memory gets lost. This made prior proofs complex, since the generated attacker had to stash all reachable pointers.
In this work, we introduce more informative data-flow traces, which allow us to combine the best of syntax-directed and trace-directed back-translation. Our data-flow back-translation is simple, handles both syntactic dissimilarity and memory sharing well, and we have proved it correct in Coq.
We, moreover, develop a novel turn-taking simulation relation and use it to prove a recomposition lemma, which is key to reusing compiler correctness in such secure compilation proofs. We are the first to mechanize such a recomposition lemma in a proof assistant in the presence of memory sharing.
We put these two key innovations to use in a secure compilation proof for a code generation compiler pass between a safe source language with pointers and components, and a target language with unstructured control flow.
ENKI: Access Control for Encrypted Query Processing

Presentation given at the SWIM Seminar (University of Tsukuba) about ENKI*.
This presentation is based on the uploader's understanding of the paper and may contain inaccurate interpretations.
A summary of the paper is available at: https://mshcruz.wordpress.com/2016/07/11/summary-enki/
*Hang et al.: "ENKI: Access Control for Encrypted Query Processing". SIGMOD 2015.
Cryptography Workbook

This document is a worksheet for a cryptography and network security course. It contains definitions of key terms like cryptography, encryption, decryption, and types of attacks. It also outlines classical encryption techniques like the Caesar cipher, Playfair cipher, Hill cipher, Vigenere cipher, and transposition techniques. Finally, it covers number theory topics such as prime numbers, factorization, Fermat's theorem, Euler's theorem, and primitive roots as they relate to cryptography.
rsa-1

RSA is a widely used public-key cryptosystem. It works by generating a public and private key pair. The public key is used for encryption and digital signatures while the private key is used for decryption and signature verification. Key generation involves finding two prime numbers p and q, computing the modulus n as their product, and using these values to calculate the public and private exponents e and d respectively.
Listen and look at your PHP code

This document discusses various static analysis tools for PHP code including PHP_CodeSniffer, PHPDepend, PHPMD, phploc, phpcpd, vld, Bytekit, Padawan, Phantm, phpUnderControl, Arbit, and plugins for Sonar. It provides descriptions of what each tool analyzes and outputs including code style checks, complexity metrics, dependency graphs, duplication detection, bytecode analysis, and continuous integration reporting. Screenshots are included showing output and integrations from Sonar, phpUnderControl, and Arbit. The document argues that Sonar is the state of the art but still has room for improvement in supporting PHP-specific needs and integrating with other tools.
Iss lecture 2

This document discusses symmetric cryptography and provides an overview of symmetric cipher systems including stream ciphers like the Vernam cipher and one-time pad, as well as block ciphers like DES, Triple DES, and AES. It describes the basic components of a symmetric cipher model and the properties and modes of operation for symmetric encryption algorithms. Key topics covered include the Feistel cipher structure used by DES, the cryptanalysis of DES leading to its replacement by AES, and the advantages and disadvantages of stream and block ciphers.
Realizing Fine-Grained and Flexible Access Control to Outsourced Data with At...

Presentation given at the SWIM Seminar (University of Tsukuba) about the paper "Realizing Fine-Grained and Flexible Access Control to Outsourced Data with Attribute-Based Cryptosystems"*.
This presentation is based on the uploader's understanding of the paper and may contain inaccurate interpretations.
A summary of the paper is available at: https://mshcruz.wordpress.com/2016/07/22/summary-fine-grained-access-control-using-abe-and-abs/
*Zhao et al.: "Realizing Fine-Grained and Flexible Access Control to Outsourced Data with Attribute-Based Cryptosystems". ISPEC 2011.
Java - Concurrent programming - Thread's advanced concepts

This presentation introduces some advanced concepts of threads, as implemented in the Java platform. It is part of a series of slides dedicated to threads. This slides introduces the following concepts:
- Callable
- Futures
- Executors and executor services
- Deadlocks (brief introduction)
The presentation is took from the Java course I run in the bachelor-level informatics curriculum at the University of Padova.
OpenMI Developers Training

Introduction to developing or migrating models to be compliant to the OpenMI Standard. OpenMI is an open standard which allows dynamic linking of numerical models, such as river models rainfall-runoff models and so on. See also:
http://www.lictek.com
OpenMI Developers Training

Introduction to developing or migrating models to be compliant to the OpenMI Standard. OpenMI is an open standard which allows dynamic linking of numerical models, such as river models rainfall-runoff models and so on. See also:
http://www.lictek.com
Rfid 

The document outlines a proposed design for a radio frequency identification (RFID) system security method. It begins with an introduction and background on RFID technology and security concerns. It then presents the methodology, which involves analyzing security threats and devising an attack taxonomy. The document proposes a cryptographic authentication protocol for RFID tags that provides mutual authentication, untraceability, and resistance to various attacks. It uses encryption techniques like keyed hash functions to authenticate tags and readers while maintaining low computation and communication costs suitable for passive RFID tags.
Unit 3(1)

The document discusses principles of public-key cryptography and algorithms like RSA and Diffie-Hellman key exchange. It provides the following key points:
1. Public-key cryptography solves the key distribution problem of symmetric encryption by using different but mathematically-related public and private keys.
2. The RSA algorithm was one of the first practical public-key cryptosystems, using modular exponentiation with large prime numbers.
3. Diffie-Hellman key exchange allows two parties to jointly establish a shared secret over an insecure channel without any prior secrets. It is based on the difficulty of calculating discrete logarithms.
VHDL Part 4

This document describes functions in VHDL. It states that a function accepts arguments and returns a result of a predetermined type. When called, actual parameters are substituted for formal parameters and the function call is replaced by the return type value. A function can define local types, constants, variables, nested functions and procedures. The keywords begin and end enclose sequential statements executed when the function is called. It then provides a simple example of an inhibit gate using a function.
Unit 3(1)

The document discusses principles of public-key cryptography and the Diffie-Hellman key exchange algorithm. It begins by explaining the problems with symmetric encryption that public-key cryptography aims to address. It then provides an overview of public-key cryptosystems and their requirements. The document goes on to describe the RSA algorithm in detail and provide an example of how it works. It also explains the Diffie-Hellman key exchange algorithm, how it allows two parties to securely exchange a key without transmitting it, and provides a numerical example.
Mouawad

The document discusses research into how melody conveys emotions to listeners. It summarizes previous work analyzing music features like mode, tempo, and pitch that influence perceived emotions. A pilot study had listeners rate emotions, moods, genres, and instruments for music clips. Findings showed basic emotions like happy and sad were recognized more than others. Future work will investigate characteristics in melody that induce emotions and could be used to predict emotional impact.
Pantidi

This research examines how technology-rich learning spaces are used in practice versus how they are intended to be used. Field studies were conducted in three spaces: Dspace, Qspace, and Cspace. Findings show the actual use differs from anticipated use, and flexibility of technology, accessibility, and physical space arrangement are key to supporting learning, collaboration and creativity as intended. Future work will develop design guidelines for technology-rich learning spaces.
More Related Content
What's hot
Embedded device hacking Session i

The goal of the workshop is to provide a hands-on introduction to key pen-testing tools and concepts that white-hat and black-hat hackers utilize to find and exploit vulnerabilities in real-world embedded devices.
661 665

This document discusses a differential cryptanalysis attack on the RC4 stream cipher. It begins by describing how RC4 encryption works, including the key scheduling algorithm and pseudo-random generation algorithm. It then explains differential cryptanalysis, where two keys that differ in only a few bytes are used to analyze differences in the generated key streams. As an example, it analyzes a differential attack on RC4 using an 8-byte state and key where the keys differ in the last byte. The attack is demonstrated by generating key streams for two similar keys and analyzing the differences to find flaws in the cipher.
PowerShell Inside Out: Applied .NET Hacking for Enhanced Visibility by Satosh...

In response to the emerging use of PowerShell by attackers, Microsoft released a feature called Anti-Malware Scan Interface (AMSI) in Windows 10, allowing 3rd party companies, as well as Microsoft itself, to gain more visibility into PowerShell and other scripting engines. Since this release, various research has been done on the effectiveness of AMSI, revealing its efficacy as well as its inherent weaknesses.
Despite this advance, however, many security vendors have yet to add AMSI support in their products, perhaps due to its limited platform coverage. On the other hand, red teamers and adversaries have quickly equipped themselves with techniques which attack the weaknesses of AMSI and bypass it, making detection and prevention of PowerShell attacks even harder.
This talk will discuss how to gain greater visibility into managed program execution, especially for PowerShell, using a .NET native code hooking technique to help organizations protect themselves from such advanced attacker techniques. In this session, we will demonstrate how to enhance capabilities provided by AMSI and how to overcome its limitations, through a realistic implementation of the technique, all while analyzing the internals of .NET Framework and the PowerShell engine.
Ch34508510

International Journal of Engineering Research and Applications (IJERA) is an open access online peer reviewed international journal that publishes research and review articles in the fields of Computer Science, Neural Networks, Electrical Engineering, Software Engineering, Information Technology, Mechanical Engineering, Chemical Engineering, Plastic Engineering, Food Technology, Textile Engineering, Nano Technology & science, Power Electronics, Electronics & Communication Engineering, Computational mathematics, Image processing, Civil Engineering, Structural Engineering, Environmental Engineering, VLSI Testing & Low Power VLSI Design etc.
Latest C Interview Questions and Answers

3. What is a register variable?
Register variables are stored in the CPU registers. Its default value is a garbage value. Scope of a register variable is local to the block in which it is defined. Lifetime is till control remains within the block in which the register variable is defined. Variable stored in a CPU register can always be accessed faster than the one that is stored in memory. Therefore, if a variable is used at many places in a program, it is better to declare its storage class as register
Example: register int x=5;
Variables for loop counters can be declared as register. Note that register keyword may be ignored by some compilers.
4. Where is an auto variables stored?
Main memory and CPU registers are the two memory locations where auto variables are stored. Auto variables are defined under automatic storage class. They are stored in main memory. Memory is allocated to an automatic variable when the block which contains it is called and it is de-allocated at the completion of its block
execution.
Auto variables:
Storage
:
main memory.
Default value
:
garbage value.
Scope
:
local to the block in which the variable is defined.
Lifetime
:
till the control remains within the block in which the variable is defined.
5. What is scope & storage allocation of extern and global variables?
Extern variables: belong to the External storage class and are stored in the main memory. extern is used when we have to refer a function or variable that is implemented in another file in the same project. The scope of the extern variables is Global.
Network Security

The document discusses and provides code examples for implementing several cryptographic algorithms, including Diffie-Hellman key exchange, RSA encryption, Caesar cipher, RC4 stream cipher, and monoalphabetic cipher. It first explains the Diffie-Hellman protocol for generating a shared secret key between two parties. It then shows Java code to implement Diffie-Hellman. It also discusses RSA encryption and provides Java code to encrypt and decrypt messages. Further code examples demonstrate how to implement the Caesar cipher, RC4 stream cipher, and monoalphabetic cipher in Java.
SecurePtrs: Proving Secure Compilation with Data-Flow Back-Translation and Tu...

[PriSC 2022 talk: https://popl22.sigplan.org/home/prisc-2022#program]
Proving secure compilation of partial programs typically requires back-translating a target attack against the compiled program to an attack against the source program. To prove this back-translation step, one can syntactically translate the target attacker to a source one -- i.e., syntax-directed back-translation -- or show that the interaction traces of the target attacker can also be produced by source attackers -- i.e., trace-directed back-translation.
Syntax-directed back-translation is not suitable when the target attacker uses unstructured control flow that the source language cannot directly represent. Trace-directed back-translation works with such syntactic dissimilarity because only the external interactions of the target attacker have to be mimicked in the source, not its internal control flow. Revealing only external interactions is, however, inconvenient when sharing memory via unforgeable pointers, since information about stashed pointers to shared memory gets lost. This made prior proofs complex, since the generated attacker had to stash all reachable pointers.
In this work, we introduce more informative data-flow traces, which allow us to combine the best of syntax-directed and trace-directed back-translation. Our data-flow back-translation is simple, handles both syntactic dissimilarity and memory sharing well, and we have proved it correct in Coq.
We, moreover, develop a novel turn-taking simulation relation and use it to prove a recomposition lemma, which is key to reusing compiler correctness in such secure compilation proofs. We are the first to mechanize such a recomposition lemma in a proof assistant in the presence of memory sharing.
We put these two key innovations to use in a secure compilation proof for a code generation compiler pass between a safe source language with pointers and components, and a target language with unstructured control flow.
ENKI: Access Control for Encrypted Query Processing

Presentation given at the SWIM Seminar (University of Tsukuba) about ENKI*.
This presentation is based on the uploader's understanding of the paper and may contain inaccurate interpretations.
A summary of the paper is available at: https://mshcruz.wordpress.com/2016/07/11/summary-enki/
*Hang et al.: "ENKI: Access Control for Encrypted Query Processing". SIGMOD 2015.
Cryptography Workbook

This document is a worksheet for a cryptography and network security course. It contains definitions of key terms like cryptography, encryption, decryption, and types of attacks. It also outlines classical encryption techniques like the Caesar cipher, Playfair cipher, Hill cipher, Vigenere cipher, and transposition techniques. Finally, it covers number theory topics such as prime numbers, factorization, Fermat's theorem, Euler's theorem, and primitive roots as they relate to cryptography.
rsa-1

RSA is a widely used public-key cryptosystem. It works by generating a public and private key pair. The public key is used for encryption and digital signatures while the private key is used for decryption and signature verification. Key generation involves finding two prime numbers p and q, computing the modulus n as their product, and using these values to calculate the public and private exponents e and d respectively.
Listen and look at your PHP code

This document discusses various static analysis tools for PHP code including PHP_CodeSniffer, PHPDepend, PHPMD, phploc, phpcpd, vld, Bytekit, Padawan, Phantm, phpUnderControl, Arbit, and plugins for Sonar. It provides descriptions of what each tool analyzes and outputs including code style checks, complexity metrics, dependency graphs, duplication detection, bytecode analysis, and continuous integration reporting. Screenshots are included showing output and integrations from Sonar, phpUnderControl, and Arbit. The document argues that Sonar is the state of the art but still has room for improvement in supporting PHP-specific needs and integrating with other tools.
Iss lecture 2

This document discusses symmetric cryptography and provides an overview of symmetric cipher systems including stream ciphers like the Vernam cipher and one-time pad, as well as block ciphers like DES, Triple DES, and AES. It describes the basic components of a symmetric cipher model and the properties and modes of operation for symmetric encryption algorithms. Key topics covered include the Feistel cipher structure used by DES, the cryptanalysis of DES leading to its replacement by AES, and the advantages and disadvantages of stream and block ciphers.
Realizing Fine-Grained and Flexible Access Control to Outsourced Data with At...

Presentation given at the SWIM Seminar (University of Tsukuba) about the paper "Realizing Fine-Grained and Flexible Access Control to Outsourced Data with Attribute-Based Cryptosystems"*.
This presentation is based on the uploader's understanding of the paper and may contain inaccurate interpretations.
A summary of the paper is available at: https://mshcruz.wordpress.com/2016/07/22/summary-fine-grained-access-control-using-abe-and-abs/
*Zhao et al.: "Realizing Fine-Grained and Flexible Access Control to Outsourced Data with Attribute-Based Cryptosystems". ISPEC 2011.
Java - Concurrent programming - Thread's advanced concepts

This presentation introduces some advanced concepts of threads, as implemented in the Java platform. It is part of a series of slides dedicated to threads. This slides introduces the following concepts:
- Callable
- Futures
- Executors and executor services
- Deadlocks (brief introduction)
The presentation is took from the Java course I run in the bachelor-level informatics curriculum at the University of Padova.
OpenMI Developers Training

Introduction to developing or migrating models to be compliant to the OpenMI Standard. OpenMI is an open standard which allows dynamic linking of numerical models, such as river models rainfall-runoff models and so on. See also:
http://www.lictek.com
OpenMI Developers Training

Introduction to developing or migrating models to be compliant to the OpenMI Standard. OpenMI is an open standard which allows dynamic linking of numerical models, such as river models rainfall-runoff models and so on. See also:
http://www.lictek.com
Rfid 

The document outlines a proposed design for a radio frequency identification (RFID) system security method. It begins with an introduction and background on RFID technology and security concerns. It then presents the methodology, which involves analyzing security threats and devising an attack taxonomy. The document proposes a cryptographic authentication protocol for RFID tags that provides mutual authentication, untraceability, and resistance to various attacks. It uses encryption techniques like keyed hash functions to authenticate tags and readers while maintaining low computation and communication costs suitable for passive RFID tags.
Unit 3(1)

The document discusses principles of public-key cryptography and algorithms like RSA and Diffie-Hellman key exchange. It provides the following key points:
1. Public-key cryptography solves the key distribution problem of symmetric encryption by using different but mathematically-related public and private keys.
2. The RSA algorithm was one of the first practical public-key cryptosystems, using modular exponentiation with large prime numbers.
3. Diffie-Hellman key exchange allows two parties to jointly establish a shared secret over an insecure channel without any prior secrets. It is based on the difficulty of calculating discrete logarithms.
VHDL Part 4

This document describes functions in VHDL. It states that a function accepts arguments and returns a result of a predetermined type. When called, actual parameters are substituted for formal parameters and the function call is replaced by the return type value. A function can define local types, constants, variables, nested functions and procedures. The keywords begin and end enclose sequential statements executed when the function is called. It then provides a simple example of an inhibit gate using a function.
Unit 3(1)

The document discusses principles of public-key cryptography and the Diffie-Hellman key exchange algorithm. It begins by explaining the problems with symmetric encryption that public-key cryptography aims to address. It then provides an overview of public-key cryptosystems and their requirements. The document goes on to describe the RSA algorithm in detail and provide an example of how it works. It also explains the Diffie-Hellman key exchange algorithm, how it allows two parties to securely exchange a key without transmitting it, and provides a numerical example.
What's hot (20)
PowerShell Inside Out: Applied .NET Hacking for Enhanced Visibility by Satosh...

PowerShell Inside Out: Applied .NET Hacking for Enhanced Visibility by Satosh...
SecurePtrs: Proving Secure Compilation with Data-Flow Back-Translation and Tu...

SecurePtrs: Proving Secure Compilation with Data-Flow Back-Translation and Tu...
ENKI: Access Control for Encrypted Query Processing

ENKI: Access Control for Encrypted Query Processing
Realizing Fine-Grained and Flexible Access Control to Outsourced Data with At...

Realizing Fine-Grained and Flexible Access Control to Outsourced Data with At...
Java - Concurrent programming - Thread's advanced concepts

Java - Concurrent programming - Thread's advanced concepts
Viewers also liked
Mouawad

The document discusses research into how melody conveys emotions to listeners. It summarizes previous work analyzing music features like mode, tempo, and pitch that influence perceived emotions. A pilot study had listeners rate emotions, moods, genres, and instruments for music clips. Findings showed basic emotions like happy and sad were recognized more than others. Future work will investigate characteristics in melody that induce emotions and could be used to predict emotional impact.
Pantidi

This research examines how technology-rich learning spaces are used in practice versus how they are intended to be used. Field studies were conducted in three spaces: Dspace, Qspace, and Cspace. Findings show the actual use differs from anticipated use, and flexibility of technology, accessibility, and physical space arrangement are key to supporting learning, collaboration and creativity as intended. Future work will develop design guidelines for technology-rich learning spaces.
Wilkie

This document provides details about Katie Wilkie's PhD research which aims to identify conceptual metaphors used by musicians to understand musical concepts like pitch, melody, and harmony. The research will involve discussions with musicians to elicit these metaphors, which will then be used to evaluate existing music interaction designs and inform the creation of new, more intuitive designs. The contributions will include increased knowledge of how metaphors aid musical understanding and guidelines for designing music interactions based on conceptual metaphors.
Dupressoir

François Dupressoir is a PhD student at the Computing Department of the Open University. His research focuses on verifying authentication properties of C security protocol code using general verifiers like VCC. Previous approaches to verifying C protocol implementations relied on unsound assumptions, large amounts of trusted annotations, or were limited in scalability. Dupressoir aims to provide a new approach using minimal trusted annotations that is accessible to non-experts and can verify real C code.
Abraham

This doctoral research explores how users make sense of and use information when seeking information from web-based resources. The research examines user behaviors and strategies as they interact with information sources to identify examples of how users collect, evaluate, understand, interpret, and integrate new information. Three empirical studies were conducted involving participants completing information seeking tasks. The results provide insights into users' information interaction strategies and sensemaking activities. Implications for the design of technologies to better support sensemaking are discussed.
Aizatulin

The document summarizes the author's PhD research which aims to verify implementations of cryptographic protocols in C by extracting an abstract model from the running code using concolic (concrete and symbolic) execution. This approach produces a symbolic execution trace that reveals the structure of messages sent over the network and checks performed on incoming messages. The author has been able to extract traces for a simple request-response protocol implemented in OpenSSL. Future work involves handling loops and buffer lengths soundly and making the extracted models compatible with verification tools like ProVerif and CryptoVerif.
Session3

The document provides an overview of the Software Development Life Cycle (SDLC) and popular software development methodologies. It describes the SDLC model which includes requirements analysis, design, coding, testing, and maintenance. It also summarizes three other models: the prototyping model which uses iterative prototyping and customer feedback; the Rapid Application Development (RAD) model which emphasizes short development cycles and component reuse; and the component assembly model which develops software from reusable components.
Formal analysis-crypto-proto

The document discusses formal modeling and analysis of cryptographic protocols. It introduces formal methods, the Dolev-Yao model, pi-calculus as a modeling language, and the ProVerif tool. As an example, a naïve handshake protocol is presented and a man-in-the-middle attack is demonstrated. The talk concludes that formal methods provide rigorous analysis of protocol security properties.
Oops index

This document provides an overview of object-oriented programming concepts using C++. It discusses C++ as an improvement over C that allows both object-oriented and procedural programming. The keys sections define objects, encapsulation, polymorphism, inheritance and classes. It also discusses defining classes in C++, objects and encapsulation, messages and polymorphism, data abstraction and natural building blocks of OOP. Later sections provide examples of polymorphism in applications and programs.
Teaching Students with Emojis, Emoticons, & Textspeak

This document discusses how emojis, emoticons, and text speak can be used to teach students. It provides background on the origins of emoticons in 1982 as ways to convey tone and feelings in text communications. It then suggests that with text speak and emojis, students can translate, decode, summarize, play with language, and add emotion to language. A number of websites and apps that can be used for emoji-related activities, lessons, and discussions are also listed.
Study: The Future of VR, AR and Self-Driving Cars

We asked LinkedIn members worldwide about their levels of interest in the latest wave of technology: whether they’re using wearables, and whether they intend to buy self-driving cars and VR headsets as they become available. We asked them too about their attitudes to technology and to the growing role of Artificial Intelligence (AI) in the devices that they use. The answers were fascinating – and in many cases, surprising.
This SlideShare explores the full results of this study, including detailed market-by-market breakdowns of intention levels for each technology – and how attitudes change with age, location and seniority level. If you’re marketing a tech brand – or planning to use VR and wearables to reach a professional audience – then these are insights you won’t want to miss.
Hype vs. Reality: The AI Explainer

Artificial intelligence (AI) is everywhere, promising self-driving cars, medical breakthroughs, and new ways of working. But how do you separate hype from reality? How can your company apply AI to solve real business problems?
Here’s what AI learnings your business should keep in mind for 2017.
Viewers also liked (12)
Teaching Students with Emojis, Emoticons, & Textspeak

Teaching Students with Emojis, Emoticons, & Textspeak
Similar to Aizatulin poster
SRAVANByCPP

this is good power point presentations for c++ learners , simply it is explains cpp features with some basic examples
Chapter 15 - Security

The Security Problem
Program Threats
System and Network Threats
Cryptography as a Security Tool
User Authentication
Implementing Security Defenses
Firewalling to Protect Systems and Networks
Computer-Security Classifications
An Example: Windows XP
Pascal script maxbox_ekon_14_2

PascalScript is a scripting engine that allows scripts written in Object Pascal to be executed at runtime in Delphi and Free Pascal applications. It provides advantages like allowing customization without recompiling and updating applications by distributing new script files. The engine works by compiling scripts to bytecode using a compiler component, and executing the bytecode using an executer component. It supports common data types, functions, classes, and calling external libraries.
Symbolic Execution (introduction and hands-on)

An introduction to Symbolic Execution. Hands-on using the angr binary framework.
hands-on material: https://github.com/ercoppa/symbolic-execution-tutorial
reference: Roberto Baldoni, Emilio Coppa, Daniele Cono D'Elia, Camil Demetrescu, Irene Finocchi. A Survey of Symbolic Execution Techniques. ACM Computing Surveys (ACM CSUR), 51(3), 2018. http://season-lab.github.io/papers/survey-symbolic-execution-preprint-CSUR18.pdf
Ransomware for fun and non-profit

The document discusses how ransomware works by encrypting files on a victim's computer and demanding payment to decrypt the files. It explains the basic process of how ransomware encrypts files, displays a ransom message, and transmits encryption keys to the attacker. The document also provides examples of code that could be used to implement various functions required for a basic ransomware program, such as generating encryption keys, encrypting files, and displaying messages. Finally, it discusses techniques malware developers use to avoid detection by antivirus software.
Cypherock Assessment (1).pdf

Title: Embedded Security Analysis Task: Side Channel Analysis and Fault Injection
Objective:
The objective of this task is to assess your ability to work with Python tools, C programming,
Computer Architecture, and apply side channel analysis and fault injection techniques to
uncover a hidden flag embedded within an ELF file compiled for an STM32 processor. You will
use the Lascar and Rainbow tools from Ledger's repository to analyze the binary and retrieve
the hidden flag.
Requirements:
1. Proficiency in Python programming.
2. Basic understanding of side channel analysis and fault injection concepts.
3. Familiarity with ELF file format and embedded systems.
Task Description:
Setup and Familiarization:
1. Clone the Ledger's repository containing Lascar and Rainbow tools.
2. Install the necessary dependencies and set up the environment as per the provided
documentation.
3. Review the documentation and examples to understand how Lascar and Rainbow tools
are used for side channel analysis and fault injection.
Binary Analysis:
1. You will be provided with an ELF file compiled for an STM32 processor.
2. Study the provided stubbed source code for the binary to understand its functionality and
potential vulnerabilities.
Side Channel Analysis/ Fault Injection:
1. Choose a specific side channel analysis technique or fault injection technique based on
your analysis of the binary.
2. Implement the chosen technique using Lascar or Rainbow tools to extract information
from the binary.
3. Document your approach, code snippets, and any findings from the side channel
analysis.
4. Provide a detailed explanation of your fault injection methodology, along with relevant
code snippets and observations.
Flag Retrieval:
1. Apply the insights gained from side channel analysis and fault injection to uncover the
hidden secret embedded within the binary.
2. Document the process you followed to successfully retrieve the secret.
3. Provide the extracted secret as proof of completion.
Evaluation Criteria:
You will be evaluated based on the following criteria:
1. Understanding of side channel analysis and fault injection concepts.
2. Proficiency in understanding the assignment and applying conceptual knowledge in
practice.
3. Explanation of the approach taken.
4. Successful retrieval of the hidden flag.
Submit all scripts, analysis, images, documentation in form of a zip file directly to Cypherock.
C sharp chap6

1. An array is a collection of variables of the same type that are referred to by a common name. Arrays provide a convenient way of grouping related data of the same type.
2. Arrays organize data in a way that allows for easy manipulation and sorting of elements. Declaring data as an array is more elegant than declaring many individual variables when multiple pieces of related data are involved.
3. C# supports one-dimensional and multi-dimensional arrays. Elements in arrays are accessed using an index. Arrays are zero-indexed and bounds checked to prevent errors. The Length property provides the size of the array.
Real-World WebAppSec Flaws - Examples and Countermeasues

A presentation at the Sydney WebApp meeting for the security stream. Covers some easy to follow examples of more common things found and general recommendations for development teams.
Notes on c++

The document provides an introduction to object-oriented programming concepts in C++ including objects, classes, data abstraction, encapsulation, inheritance, polymorphism, dynamic binding, and message passing. It then describes the structure of a C++ program including include files, class definitions, data declarations, member functions, and main functions. Finally, it discusses control structures in C++ including decision making statements like if/else and switch statements, looping statements like while, do-while and for loops, and functions.
FORECAST: Fast Generation of Accurate Context-Aware Signatures of Control-Hij...

The document summarizes FORECAST, a system that can automatically generate accurate context-aware signatures for control-hijacking attacks from a single instance. FORECAST instruments programs to log all memory updates, allowing it to identify control and data dependencies at runtime. When an attack is detected, the memory update log is used to generate a signature representing each attack packet as a regular expression. FORECAST was tested on several network services and able to generate accurate signatures within seconds.
iPhone Seminar Part 2

The PPTs from one of the event of iWillStudy.com - a leading start-up in the education space in India. This PPT is being used at an event where they taught iPhone programming and applications development.
Eight simple rules to writing secure PHP programs

This document provides eight rules for writing secure PHP programs:
1. Use proper cryptography and do not invent your own algorithms.
2. Validate all input from external sources before using.
3. Sanitize data sent to databases or other systems to prevent injection attacks.
4. Avoid leaking sensitive information through error messages or other means.
5. Properly manage user sessions to prevent hijacking and ensure users remain authenticated.
6. Enforce authentication and authorization separately using least privilege.
7. Use SSL/TLS to encrypt all authenticated or sensitive communications.
8. Keep security straightforward and avoid relying on obscurity.
DIRA: Automatic Detection, Identification, and Repair of Controll-Hijacking a...

DIRA is a compile-time solution that provides automatic detection, identification, and repair of control-hijacking attacks. It uses memory updates logging to maintain a runtime log of all changes to a program's memory state. This log is used to detect attacks by checking for changes to control pointers, identify attacks by tracing data back to its source, and repair attacks by restoring memory states from pre-images in the log.
Encryption/Decryption Algorithm for Devanagri Script(Affine Cipher)

It introduces Affine Cipher as an algorithm to be used for Encryption and Decryption of Devanagri Script.
Lattice based Merkle for post-quantum epoch

Maksim Iavich in Bucharest, Romania on November 8-9th 2018 at DefCamp #9.
The videos and other presentations can be found on https://def.camp/archive
EEE 3rd year oops cat 3 ans

The document is a test paper for the course CS2311 - Object-Oriented Programming at PERI INSTITUTE OF TECCHNOLOGY. It contains 15 questions testing concepts related to OOP such as classes, objects, inheritance, polymorphism, operator overloading, templates, and exception handling. It also includes questions about file handling and formatted I/O functions in C++. The test has a duration of 180 minutes and is worth a maximum of 100 marks, divided into multiple choice questions worth 2 marks each (Part A) and longer answer questions worth 16 marks each (Part B).
Lab manual object oriented technology (it 303 rgpv) (usefulsearch.org) (usef...

This document provides a lab manual for the fourth semester computer science engineering course on Object Oriented Technology. It includes the syllabus, rationale for object oriented programming, hardware and software requirements, a list of practical experiments to be conducted, and sample code for some of the experiments. The experiments cover topics like function overloading, inheritance, polymorphism, constructors, destructors, copy constructors, friend functions, and use of local, static and global objects. Each experiment is followed by sample output and questions related to the concepts covered in the program. The document aims to provide guidance to students on the practical implementation of object oriented programming concepts using C++.
MPI

MPI is a language-independent communications protocol used to program parallel computers. It allows processes to communicate and synchronize through point-to-point and collective communication primitives. The document discusses how to install MPI on Linux clusters, describes common MPI functions for communication (e.g. MPI_Send, MPI_Recv) and collective operations (e.g. MPI_Bcast, MPI_Reduce). It also provides an example MPI program to demonstrate basic point-to-point communication between two processes.
venkatesh.pptx

The document provides an overview of the C programming language. It discusses that C is a general purpose, procedural language developed in 1972 at Bell Labs. C is a middle-level language as it allows programming at both high-level and assembly-level. Key aspects of C covered include data types, variables, operators, functions, arrays, pointers, memory management, and file handling. The document also provides examples of various C programming concepts.
C tutorial

This document provides a quick introduction to the C programming language. It begins with an overview of writing and running C programs, including compiling source code into an executable binary. It then discusses some key C programming concepts like functions, memory, variables, and data types. The document uses simple examples like a "Hello World" program to demonstrate basic C syntax and how programs are executed. Overall, it aims to give new C programmers a high-level understanding of some essential C programming fundamentals in about 3 pages.
Similar to Aizatulin poster (20)
Real-World WebAppSec Flaws - Examples and Countermeasues

Real-World WebAppSec Flaws - Examples and Countermeasues
FORECAST: Fast Generation of Accurate Context-Aware Signatures of Control-Hij...

FORECAST: Fast Generation of Accurate Context-Aware Signatures of Control-Hij...
DIRA: Automatic Detection, Identification, and Repair of Controll-Hijacking a...

DIRA: Automatic Detection, Identification, and Repair of Controll-Hijacking a...
Encryption/Decryption Algorithm for Devanagri Script(Affine Cipher)

Encryption/Decryption Algorithm for Devanagri Script(Affine Cipher)
Lab manual object oriented technology (it 303 rgpv) (usefulsearch.org) (usef...

Lab manual object oriented technology (it 303 rgpv) (usefulsearch.org) (usef...
More from anesah
Van der merwe

This document summarizes a PhD research project exploring how online social media is used to support local governance. It describes a case study of a small community that uses online discussion forums to discuss local issues. Analysis identified five patterns of "governance conversation" including sharing information, providing feedback, coordinating responses, informally mediating issues, and engaging in discussion of complex problems. While no binding decisions were made online, the discussions supported governance action. The research examines how online tools can both facilitate instrumental problem-solving and support expressive deliberation that accommodates pluralism in local governance.
Thomas

Keerthi Thomas is a PhD student at the Open University, supervised by Prof. Bashar Nuseibeh, Dr. Arosha Bandara, and Mr. Blaine Price. Her research focuses on eliciting and analyzing users' privacy requirements for mobile applications. Previous work has shown privacy requirements vary based on users' changing contexts. However, most existing approaches do not address challenges of understanding privacy needs for mobile apps. Thomas proposes a systematic approach using a user-centric model combining contextual and interaction data to capture how privacy requirements are "distilled" from empirical studies of mobile social networking app users.
Taubenberger

This document summarizes Stefan Taubenberger's PhD research on using business process security requirements for IT security risk assessment. The research aims to determine if IT security risks can be reliably evaluated solely based on assessing adherence to security requirements, without using probabilities and events. The approach involves modeling business processes, identifying critical assets and security requirements, and evaluating how well security controls and processes meet the requirements. Preliminary validation using a reinsurance company's processes supports the idea that risks can be determined this way. The research seeks to address limitations of traditional risk assessment approaches.
Sach

Rien Sach is conducting PhD research on the effects of feedback on the motivation of software engineers. Motivation is important for aspects like productivity and quality. Feedback is a key factor in theories of motivation. The research will identify types of feedback software engineers receive through interviews and diaries, then study the impact of feedback on motivation through further studies and observations. The goal is to better understand how feedback affects software engineers' motivation, behavior, productivity and attitudes.
Rae

The author is researching the effects of feedback on the motivation of software engineers. In the first stage, the author plans to conduct interviews and diary studies to identify types of feedback received by software engineers and their experiences with feedback. In the second stage, additional studies will explore the impact of feedback on engineers' motivation. Finally, the author will observe engineers at work to see feedback in context and compare to prior findings. The goal is to better understand how feedback affects engineers' motivation and how this is manifested in behavior, productivity, or attitude. Key theories that inform the research are Hackman and Oldman's Job Characteristics Theory and Herzberg's Motivational-Hygiene Theory.
Pantidi

This document discusses research examining how technology-rich learning spaces are used in practice. The research focuses on three multi-purpose spaces called Dspace, Qspace, and Cspace. Ethnographic field studies were conducted in these spaces to understand how people interact with each other and the technology, and to gain insights into how the physical space impacts technology use. Preliminary findings show the importance of technology positioning, flexibility, and a sense of ownership over the technology.
Corneli

Joe Corneli is a PhD student at the Knowledge Media Institute studying semantic adaptivity and social networking in personal learning environments. His research focuses on developing a unified methodology to map activity patterns in social contexts to better support the learning process. He plans to implement his ideas using tools like Etherpad for analyzing live social interactions, RDF for managing relationship data, and WordNet for clustering and annotating content to help simplify information and connect resources for learners. By the end of his PhD, he hopes to build a "PLE IDE" tool to offer personalized support for learners and developers.
Collins

Tom Collins is a PhD student at the Centre for Research in Computing studying how current methods for pattern discovery in music can be improved and integrated into an automated composition system. He is improving pattern discovery algorithms in two ways: 1) developing a new formula to rate discovered patterns based on empirical user ratings, and 2) creating a new algorithm called SIACT that outperforms existing algorithms at finding translational patterns based on benchmarks set by a music analyst. His presentation will demonstrate these improvements and how they are incorporated into a user interface.
Xambo

This document summarizes Anna Xambó's research on collaborative music making on multi-touch surfaces. She developed a prototype that allows groups of up to four users to collaboratively create music using pre-composed materials. Case studies were conducted and analyzed to evaluate creative engagement. The analysis identified key concepts like collaboration, musical aesthetics, and system design. Based on the findings, responsiveness and a balance of shared/individual controls were highlighted as important for maximizing engagement.
Ullmann

The document is an abstract for a PhD student conference that describes Thomas Daniel Ullmann's proposed PhD thesis. The thesis aims to develop a framework for mash-up learning environments that allows users to reflect on resources to make informed decisions. Mash-ups combine separate data sources and APIs to create new applications. The goal is to provide reflection functionality in a mash-up environment by including manually and automatically added indicators to foster reflection on resources and topics.
Tran

This document summarizes a PhD student's research on how experiences in 3D virtual worlds influence perceptions of 2D e-commerce websites. The student aims to understand consumer experiences in virtual worlds and how those shape expectations of shopping online. Through qualitative interviews, they are identifying affordances that virtual worlds provide for commerce, such as interactive 3D product viewing, and how those compare to websites. The goal is to develop design guidelines for virtual world shopping and integrating virtual and real-world commerce experiences. Preliminary findings suggest virtual worlds allow navigation of 3D store environments and social browsing with others in real-time.
Quinto

The document summarizes a PhD student's research on developing a Debate Dashboard to reduce the barriers to adoption of online argument mapping tools. The Dashboard would provide three types of visual feedback on conversations to users: details on participants, how users interact, and the generated content. This feedback aims to decrease the cognitive effort required for users and make the benefits of argument mapping tools more apparent. An initial prototype of the Dashboard will be designed by integrating selected visualization tools and tested through expert interviews and a user survey.
Pluss

This research aims to develop a computational model of non-cooperative dialogue behavior by analyzing political interviews. The researcher identified phenomena called "non-cooperative features" that characterize uncooperative exchanges. A measure called "degree of non-cooperation" quantifies the number of these features to distinguish cooperative vs uncooperative interviews. The model will formalize how participants make decisions based on conversational obligations and goals to exhibit cooperative or non-cooperative behavior.
Pawlik

This document provides information about Aleksandra Pawlik's PhD research project which aims to explore how best to support scientific end-user software development. The research will focus on identifying problematic and successful tools/techniques used by scientific developers through case studies of projects that transition from limited to extended contexts or involve software professionals. Qualitative methods like interviews and observation will be used to understand the challenges and how support can be improved.
Overbeeke

This document is a conference paper describing a PhD student's research exploring how to better support people in understanding the dynamics of a research community. The student aims to identify key elements that define a research area, gaps in existing tools, and improve support by addressing these gaps, which may be due to a lack of data integration. An empirical study involving tasks and questionnaires with subjects will help identify problems people encounter and inform the framework being developed.
Nguyen

This document summarizes a PhD student's research on generating natural language explanations of entailments in OWL ontologies to help non-specialists understand and debug ontologies. The research aims to identify common justification patterns and develop an approach to explaining justifications in an accessible way using techniques from proof presentations. A preliminary study identified the most frequent patterns in a corpus of ontologies. The research will further analyze justification patterns and test explanations' effectiveness through user studies.
Murphy

Brendan Murphy is a PhD student at the University of Glasgow investigating mobile learning in the home care domain. His research questions examine whether learning is more successful in a mobile environment compared to a classroom, the processes learners go through with mobile technology, and how the findings can influence mobile learning design. Previous related studies found that ease of use and access to integrated patient information were important for home care workers using mobile devices. Murphy conducted initial domain analysis and user profiles with home care staff to better understand the domain and current technology use. The home care service in Glasgow is complex, providing daily services to over 10,000 clients through 3,000 carers supervised by 220 coordinators.
Moyo

This project aims to investigate the impact of affect expression using embodied conversational agents in computer-based learning environments. The researcher will develop an affect expression strategy and implement it in a tutoring system across two domains. Initial studies will evaluate how well participants can identify an agent's expressions using different communication channels. Further work will integrate the strategies into an online tutoring system and evaluate its effectiveness in classroom settings over time.
Montrieux

Lionel Montrieux is a PhD student supervised by Dr. Charles B. Haley and Dr. Yijun Yu in the Computing Department at the Open University. His research focuses on merging verifiable and evolving access control properties. Specifically, he aims to extend UMLsec to specify more complex access control models, verify that UML models enforce access control properties, generate code from UMLsec specifications, and develop a framework to merge conflicting access control properties when systems evolve.
Ma

The document discusses Lin Ma's PhD research on analyzing presuppositions in natural language requirements. Presuppositions are implicit commitments in language that simplify communication but can cause misunderstanding if not made explicit. The research aims to automatically detect presuppositions triggered by definite descriptions in requirements and identify which are not explicitly stated. It will use natural language processing techniques and knowledge sources to classify definite descriptions and analyze how presuppositions project in requirements texts.
Recently uploaded
What is an RPA CoE? Session 1 – CoE Vision

In the first session, we will review the organization's vision and how this has an impact on the COE Structure.
Topics covered:
• The role of a steering committee
• How do the organization’s priorities determine CoE Structure?
Speaker:
Chris Bolin, Senior Intelligent Automation Architect Anika Systems
The Microsoft 365 Migration Tutorial For Beginner.pptx

This presentation will help you understand the power of Microsoft 365. However, we have mentioned every productivity app included in Office 365. Additionally, we have suggested the migration situation related to Office 365 and how we can help you.
You can also read: https://www.systoolsgroup.com/updates/office-365-tenant-to-tenant-migration-step-by-step-complete-guide/
Biomedical Knowledge Graphs for Data Scientists and Bioinformaticians

Dmitrii Kamaev, PhD
Senior Product Owner - QIAGEN
HCL Notes and Domino License Cost Reduction in the World of DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-and-domino-license-cost-reduction-in-the-world-of-dlau/
The introduction of DLAU and the CCB & CCX licensing model caused quite a stir in the HCL community. As a Notes and Domino customer, you may have faced challenges with unexpected user counts and license costs. You probably have questions on how this new licensing approach works and how to benefit from it. Most importantly, you likely have budget constraints and want to save money where possible. Don’t worry, we can help with all of this!
We’ll show you how to fix common misconfigurations that cause higher-than-expected user counts, and how to identify accounts which you can deactivate to save money. There are also frequent patterns that can cause unnecessary cost, like using a person document instead of a mail-in for shared mailboxes. We’ll provide examples and solutions for those as well. And naturally we’ll explain the new licensing model.
Join HCL Ambassador Marc Thomas in this webinar with a special guest appearance from Franz Walder. It will give you the tools and know-how to stay on top of what is going on with Domino licensing. You will be able lower your cost through an optimized configuration and keep it low going forward.
These topics will be covered
- Reducing license cost by finding and fixing misconfigurations and superfluous accounts
- How do CCB and CCX licenses really work?
- Understanding the DLAU tool and how to best utilize it
- Tips for common problem areas, like team mailboxes, functional/test users, etc
- Practical examples and best practices to implement right away
JavaLand 2024: Application Development Green Masterplan

My presentation slides I used at JavaLand 2024
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency

Freshworks creates AI-boosted business software that helps employees work more efficiently and effectively. Managing data across multiple RDBMS and NoSQL databases was already a challenge at their current scale. To prepare for 10X growth, they knew it was time to rethink their database strategy. Learn how they architected a solution that would simplify scaling while keeping costs under control.
Apps Break Data

How information systems are built or acquired puts information, which is what they should be about, in a secondary place. Our language adapted accordingly, and we no longer talk about information systems but applications. Applications evolved in a way to break data into diverse fragments, tightly coupled with applications and expensive to integrate. The result is technical debt, which is re-paid by taking even bigger "loans", resulting in an ever-increasing technical debt. Software engineering and procurement practices work in sync with market forces to maintain this trend. This talk demonstrates how natural this situation is. The question is: can something be done to reverse the trend?
Digital Banking in the Cloud: How Citizens Bank Unlocked Their Mainframe

Inconsistent user experience and siloed data, high costs, and changing customer expectations – Citizens Bank was experiencing these challenges while it was attempting to deliver a superior digital banking experience for its clients. Its core banking applications run on the mainframe and Citizens was using legacy utilities to get the critical mainframe data to feed customer-facing channels, like call centers, web, and mobile. Ultimately, this led to higher operating costs (MIPS), delayed response times, and longer time to market.
Ever-changing customer expectations demand more modern digital experiences, and the bank needed to find a solution that could provide real-time data to its customer channels with low latency and operating costs. Join this session to learn how Citizens is leveraging Precisely to replicate mainframe data to its customer channels and deliver on their “modern digital bank” experiences.
5th LF Energy Power Grid Model Meet-up Slides

5th Power Grid Model Meet-up
It is with great pleasure that we extend to you an invitation to the 5th Power Grid Model Meet-up, scheduled for 6th June 2024. This event will adopt a hybrid format, allowing participants to join us either through an online Mircosoft Teams session or in person at TU/e located at Den Dolech 2, Eindhoven, Netherlands. The meet-up will be hosted by Eindhoven University of Technology (TU/e), a research university specializing in engineering science & technology.
Power Grid Model
The global energy transition is placing new and unprecedented demands on Distribution System Operators (DSOs). Alongside upgrades to grid capacity, processes such as digitization, capacity optimization, and congestion management are becoming vital for delivering reliable services.
Power Grid Model is an open source project from Linux Foundation Energy and provides a calculation engine that is increasingly essential for DSOs. It offers a standards-based foundation enabling real-time power systems analysis, simulations of electrical power grids, and sophisticated what-if analysis. In addition, it enables in-depth studies and analysis of the electrical power grid’s behavior and performance. This comprehensive model incorporates essential factors such as power generation capacity, electrical losses, voltage levels, power flows, and system stability.
Power Grid Model is currently being applied in a wide variety of use cases, including grid planning, expansion, reliability, and congestion studies. It can also help in analyzing the impact of renewable energy integration, assessing the effects of disturbances or faults, and developing strategies for grid control and optimization.
What to expect
For the upcoming meetup we are organizing, we have an exciting lineup of activities planned:
-Insightful presentations covering two practical applications of the Power Grid Model.
-An update on the latest advancements in Power Grid -Model technology during the first and second quarters of 2024.
-An interactive brainstorming session to discuss and propose new feature requests.
-An opportunity to connect with fellow Power Grid Model enthusiasts and users.
Main news related to the CCS TSI 2023 (2023/1695)

An English 🇬🇧 translation of a presentation to the speech I gave about the main changes brought by CCS TSI 2023 at the biggest Czech conference on Communications and signalling systems on Railways, which was held in Clarion Hotel Olomouc from 7th to 9th November 2023 (konferenceszt.cz). Attended by around 500 participants and 200 on-line followers.
The original Czech 🇨🇿 version of the presentation can be found here: https://www.slideshare.net/slideshow/hlavni-novinky-souvisejici-s-ccs-tsi-2023-2023-1695/269688092 .
The videorecording (in Czech) from the presentation is available here: https://youtu.be/WzjJWm4IyPk?si=SImb06tuXGb30BEH .
Artificial Intelligence and Electronic Warfare

Artificial Intelligence and Electronic WarfarePapadakis K.-Cyber-Information Warfare Analyst & Cyber Defense/Security Consultant-Hellenic MoD
AI & Electronic WarfareMonitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift
Overview
Dive into the world of anomaly detection on edge devices with our comprehensive hands-on tutorial. This SlideShare presentation will guide you through the entire process, from data collection and model training to edge deployment and real-time monitoring. Perfect for those looking to implement robust anomaly detection systems on resource-constrained IoT/edge devices.
Key Topics Covered
1. Introduction to Anomaly Detection
- Understand the fundamentals of anomaly detection and its importance in identifying unusual behavior or failures in systems.
2. Understanding Edge (IoT)
- Learn about edge computing and IoT, and how they enable real-time data processing and decision-making at the source.
3. What is ArgoCD?
- Discover ArgoCD, a declarative, GitOps continuous delivery tool for Kubernetes, and its role in deploying applications on edge devices.
4. Deployment Using ArgoCD for Edge Devices
- Step-by-step guide on deploying anomaly detection models on edge devices using ArgoCD.
5. Introduction to Apache Kafka and S3
- Explore Apache Kafka for real-time data streaming and Amazon S3 for scalable storage solutions.
6. Viewing Kafka Messages in the Data Lake
- Learn how to view and analyze Kafka messages stored in a data lake for better insights.
7. What is Prometheus?
- Get to know Prometheus, an open-source monitoring and alerting toolkit, and its application in monitoring edge devices.
8. Monitoring Application Metrics with Prometheus
- Detailed instructions on setting up Prometheus to monitor the performance and health of your anomaly detection system.
9. What is Camel K?
- Introduction to Camel K, a lightweight integration framework built on Apache Camel, designed for Kubernetes.
10. Configuring Camel K Integrations for Data Pipelines
- Learn how to configure Camel K for seamless data pipeline integrations in your anomaly detection workflow.
11. What is a Jupyter Notebook?
- Overview of Jupyter Notebooks, an open-source web application for creating and sharing documents with live code, equations, visualizations, and narrative text.
12. Jupyter Notebooks with Code Examples
- Hands-on examples and code snippets in Jupyter Notebooks to help you implement and test anomaly detection models.
Connector Corner: Seamlessly power UiPath Apps, GenAI with prebuilt connectors

Join us to learn how UiPath Apps can directly and easily interact with prebuilt connectors via Integration Service--including Salesforce, ServiceNow, Open GenAI, and more.
The best part is you can achieve this without building a custom workflow! Say goodbye to the hassle of using separate automations to call APIs. By seamlessly integrating within App Studio, you can now easily streamline your workflow, while gaining direct access to our Connector Catalog of popular applications.
We’ll discuss and demo the benefits of UiPath Apps and connectors including:
Creating a compelling user experience for any software, without the limitations of APIs.
Accelerating the app creation process, saving time and effort
Enjoying high-performance CRUD (create, read, update, delete) operations, for
seamless data management.
Speakers:
Russell Alfeche, Technology Leader, RPA at qBotic and UiPath MVP
Charlie Greenberg, host
GNSS spoofing via SDR (Criptored Talks 2024)

In the realm of cybersecurity, offensive security practices act as a critical shield. By simulating real-world attacks in a controlled environment, these techniques expose vulnerabilities before malicious actors can exploit them. This proactive approach allows manufacturers to identify and fix weaknesses, significantly enhancing system security.
This presentation delves into the development of a system designed to mimic Galileo's Open Service signal using software-defined radio (SDR) technology. We'll begin with a foundational overview of both Global Navigation Satellite Systems (GNSS) and the intricacies of digital signal processing.
The presentation culminates in a live demonstration. We'll showcase the manipulation of Galileo's Open Service pilot signal, simulating an attack on various software and hardware systems. This practical demonstration serves to highlight the potential consequences of unaddressed vulnerabilities, emphasizing the importance of offensive security practices in safeguarding critical infrastructure.
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-und-domino-lizenzkostenreduzierung-in-der-welt-von-dlau/
DLAU und die Lizenzen nach dem CCB- und CCX-Modell sind für viele in der HCL-Community seit letztem Jahr ein heißes Thema. Als Notes- oder Domino-Kunde haben Sie vielleicht mit unerwartet hohen Benutzerzahlen und Lizenzgebühren zu kämpfen. Sie fragen sich vielleicht, wie diese neue Art der Lizenzierung funktioniert und welchen Nutzen sie Ihnen bringt. Vor allem wollen Sie sicherlich Ihr Budget einhalten und Kosten sparen, wo immer möglich. Das verstehen wir und wir möchten Ihnen dabei helfen!
Wir erklären Ihnen, wie Sie häufige Konfigurationsprobleme lösen können, die dazu führen können, dass mehr Benutzer gezählt werden als nötig, und wie Sie überflüssige oder ungenutzte Konten identifizieren und entfernen können, um Geld zu sparen. Es gibt auch einige Ansätze, die zu unnötigen Ausgaben führen können, z. B. wenn ein Personendokument anstelle eines Mail-Ins für geteilte Mailboxen verwendet wird. Wir zeigen Ihnen solche Fälle und deren Lösungen. Und natürlich erklären wir Ihnen das neue Lizenzmodell.
Nehmen Sie an diesem Webinar teil, bei dem HCL-Ambassador Marc Thomas und Gastredner Franz Walder Ihnen diese neue Welt näherbringen. Es vermittelt Ihnen die Tools und das Know-how, um den Überblick zu bewahren. Sie werden in der Lage sein, Ihre Kosten durch eine optimierte Domino-Konfiguration zu reduzieren und auch in Zukunft gering zu halten.
Diese Themen werden behandelt
- Reduzierung der Lizenzkosten durch Auffinden und Beheben von Fehlkonfigurationen und überflüssigen Konten
- Wie funktionieren CCB- und CCX-Lizenzen wirklich?
- Verstehen des DLAU-Tools und wie man es am besten nutzt
- Tipps für häufige Problembereiche, wie z. B. Team-Postfächer, Funktions-/Testbenutzer usw.
- Praxisbeispiele und Best Practices zum sofortigen Umsetzen
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Are you ready to revolutionize how you handle data? Join us for a webinar where we’ll bring you up to speed with the latest advancements in Generative AI technology and discover how leveraging FME with tools from giants like Google Gemini, Amazon, and Microsoft OpenAI can supercharge your workflow efficiency.
During the hour, we’ll take you through:
Guest Speaker Segment with Hannah Barrington: Dive into the world of dynamic real estate marketing with Hannah, the Marketing Manager at Workspace Group. Hear firsthand how their team generates engaging descriptions for thousands of office units by integrating diverse data sources—from PDF floorplans to web pages—using FME transformers, like OpenAIVisionConnector and AnthropicVisionConnector. This use case will show you how GenAI can streamline content creation for marketing across the board.
Ollama Use Case: Learn how Scenario Specialist Dmitri Bagh has utilized Ollama within FME to input data, create custom models, and enhance security protocols. This segment will include demos to illustrate the full capabilities of FME in AI-driven processes.
Custom AI Models: Discover how to leverage FME to build personalized AI models using your data. Whether it’s populating a model with local data for added security or integrating public AI tools, find out how FME facilitates a versatile and secure approach to AI.
We’ll wrap up with a live Q&A session where you can engage with our experts on your specific use cases, and learn more about optimizing your data workflows with AI.
This webinar is ideal for professionals seeking to harness the power of AI within their data management systems while ensuring high levels of customization and security. Whether you're a novice or an expert, gain actionable insights and strategies to elevate your data processes. Join us to see how FME and AI can revolutionize how you work with data!
zkStudyClub - LatticeFold: A Lattice-based Folding Scheme and its Application...

Folding is a recent technique for building efficient recursive SNARKs. Several elegant folding protocols have been proposed, such as Nova, Supernova, Hypernova, Protostar, and others. However, all of them rely on an additively homomorphic commitment scheme based on discrete log, and are therefore not post-quantum secure. In this work we present LatticeFold, the first lattice-based folding protocol based on the Module SIS problem. This folding protocol naturally leads to an efficient recursive lattice-based SNARK and an efficient PCD scheme. LatticeFold supports folding low-degree relations, such as R1CS, as well as high-degree relations, such as CCS. The key challenge is to construct a secure folding protocol that works with the Ajtai commitment scheme. The difficulty, is ensuring that extracted witnesses are low norm through many rounds of folding. We present a novel technique using the sumcheck protocol to ensure that extracted witnesses are always low norm no matter how many rounds of folding are used. Our evaluation of the final proof system suggests that it is as performant as Hypernova, while providing post-quantum security.
Paper Link: https://eprint.iacr.org/2024/257
Recently uploaded (20)
9 CEO's who hit $100m ARR Share Their Top Growth Tactics Nathan Latka, Founde...

9 CEO's who hit $100m ARR Share Their Top Growth Tactics Nathan Latka, Founde...
The Microsoft 365 Migration Tutorial For Beginner.pptx

The Microsoft 365 Migration Tutorial For Beginner.pptx
Biomedical Knowledge Graphs for Data Scientists and Bioinformaticians

Biomedical Knowledge Graphs for Data Scientists and Bioinformaticians
HCL Notes and Domino License Cost Reduction in the World of DLAU

HCL Notes and Domino License Cost Reduction in the World of DLAU
JavaLand 2024: Application Development Green Masterplan

JavaLand 2024: Application Development Green Masterplan
Overcoming the PLG Trap: Lessons from Canva's Head of Sales & Head of EMEA Da...

Overcoming the PLG Trap: Lessons from Canva's Head of Sales & Head of EMEA Da...
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency

Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency
Digital Banking in the Cloud: How Citizens Bank Unlocked Their Mainframe

Digital Banking in the Cloud: How Citizens Bank Unlocked Their Mainframe
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift.pdf
Connector Corner: Seamlessly power UiPath Apps, GenAI with prebuilt connectors

Connector Corner: Seamlessly power UiPath Apps, GenAI with prebuilt connectors
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Driving Business Innovation: Latest Generative AI Advancements & Success Story
zkStudyClub - LatticeFold: A Lattice-based Folding Scheme and its Application...

zkStudyClub - LatticeFold: A Lattice-based Folding Scheme and its Application...
Aizatulin poster
- 1. Verifying Implementations of Security Protocols in C Mihhail Aizatulin (avatar@hot.ee) 1. Goal Our goal is a tool for cryptographic security analysis at implementation level: Source code of a List of all potential cryptographic Our tools security flaws or protocol proof of security implementation 2. Motivation: an Attack Example 3. Assumptions Here is an example vulnerability that we would like to prevent. In January We assume that cryptographic primitives (encryption, hash- 2009 a flaw in the OpenSSL library was discovered, permitting a corrupt certifi- ing) are implemented correctly and are unbreakable. cate to be recognised as valid. A function return value is wrongly interpreted: int check_certificate ( ) { / / l a t e r in code : 4. Background ... ... if ( certificate_malformed ) if ( check_certificate ()) / / oops ! Very little has been done for crypto-verification of low-level r e t u r n − 1; { languages. We rely on tools for proving security from high-level else if ( ! certificate_check_ok ) trust_certificate (); specifications of protocols. Currently we are using ProVerif. return 0 ; } else return 1 ; } Notice how the -1 return value passes the validity test! An attacker can craft 5. Challenges a malformed certificate, pretending to be someone else: We cannot simply reuse existing program verification tools, because we don’t just verify a program, but a system, consisting paypal.com Certificate? of several instances of a program and an unknown attacker. Malformed Certificate Client Attacker (= Internet) paypal.com 7. Proposed Method We propose to use symbolic execution to extract a high-level Now the attacker can impersonate the client and the bank to each other: model of the protocol and then use existing tools to verify it. Suppose we use shared key hashing for message integrity: Password? Password? m, hash(m, k shared ) Password Password + “get $$$” A−−−−−−−−−− B. → Client Attacker (= Internet) paypal.com The client side implementation could look as follows. Note the extra data added to the message: the payload length and a tag. We would like to use formal methods to prove absence of similar flaws. c l i e n t ( char ∗ payload , i n t payload_len ) { i n t msg_len = 5 + l e n + SHA1_LEN ; 6. Symbolic Execution char ∗ msg = malloc ( msg_len ) ; char ∗ p = msg ; Symbolic execution is a tool to simplify programs and extract their meaning. ∗p = l e n ; p += 4 ; / / add l e n g t h The program is “executed” with symbols as input, instead of numbers: ∗ ( p++) = 1 ; / / add t h e t a g memcpy( payload , p , l e n ) ; / / add t h e p a y l o a d Concrete: Symbolic: sha1 ( msg , 5 + len , p ) ; / / add t h e h a s h x = 2 y = 3 x = a y = b send ( msg , msg_len ) ; / / send } int f ( int x , int y ) { int f ( int x , int y ) { Using symbolic execution we can summarise the effect of the r e t u r n ++x ∗ y + + ; } r e t u r n ++x ∗ y + + ; } function: Symbolic Execution 9 ( a + 1) b out(len(payload)|01|payload We use symbolic execution to derive the formats of messages that the program |sha1(len(payload)|01|payload, kshared )) generates. Here “|” stands for bitstring concatenation. High-level verifi- 8. Current Status cation tools can’t deal with it directly, so we perform some extra analysis to prove that concatenation patterns can be abstracted Done: as pure symbolic functions: • Implemented symbolic execution for fixed bitstring lengths and linear con- Format Abstraction trol flow. • Proved correctness of format abstraction. out(f 1(payload, hash1(payload, kshared ))) To do: This is a representation that ProVerif can easily deal with: • Implement symbolic execution for variable bitstring lengths. ProVerif (+ Server Side) • Implement format abstraction. • Add support for arbitrary control flow. Integrity verified. 9. Project The project is supervised by Andrew Gordon (Microsoft Research), Jan Jürjens (Dortmund University) and Bashar Nuseibeh (Open University). It is partially supported through the Microsoft Research PhD Scholarship programme.