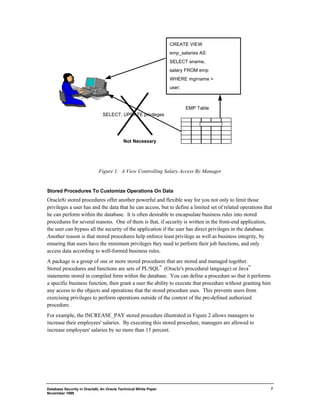
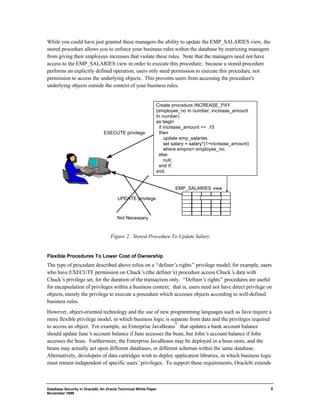
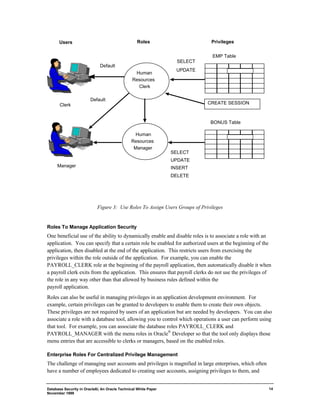
This document discusses database security features in Oracle8i. It addresses the need for fine-grained access control over data when systems are opened to partners and customers on the internet. Oracle8i provides strong user authentication, flexible privilege models, and encryption of data in transit. It also offers centralized user management and the ability to implement security policies in the database rather than in individual applications.