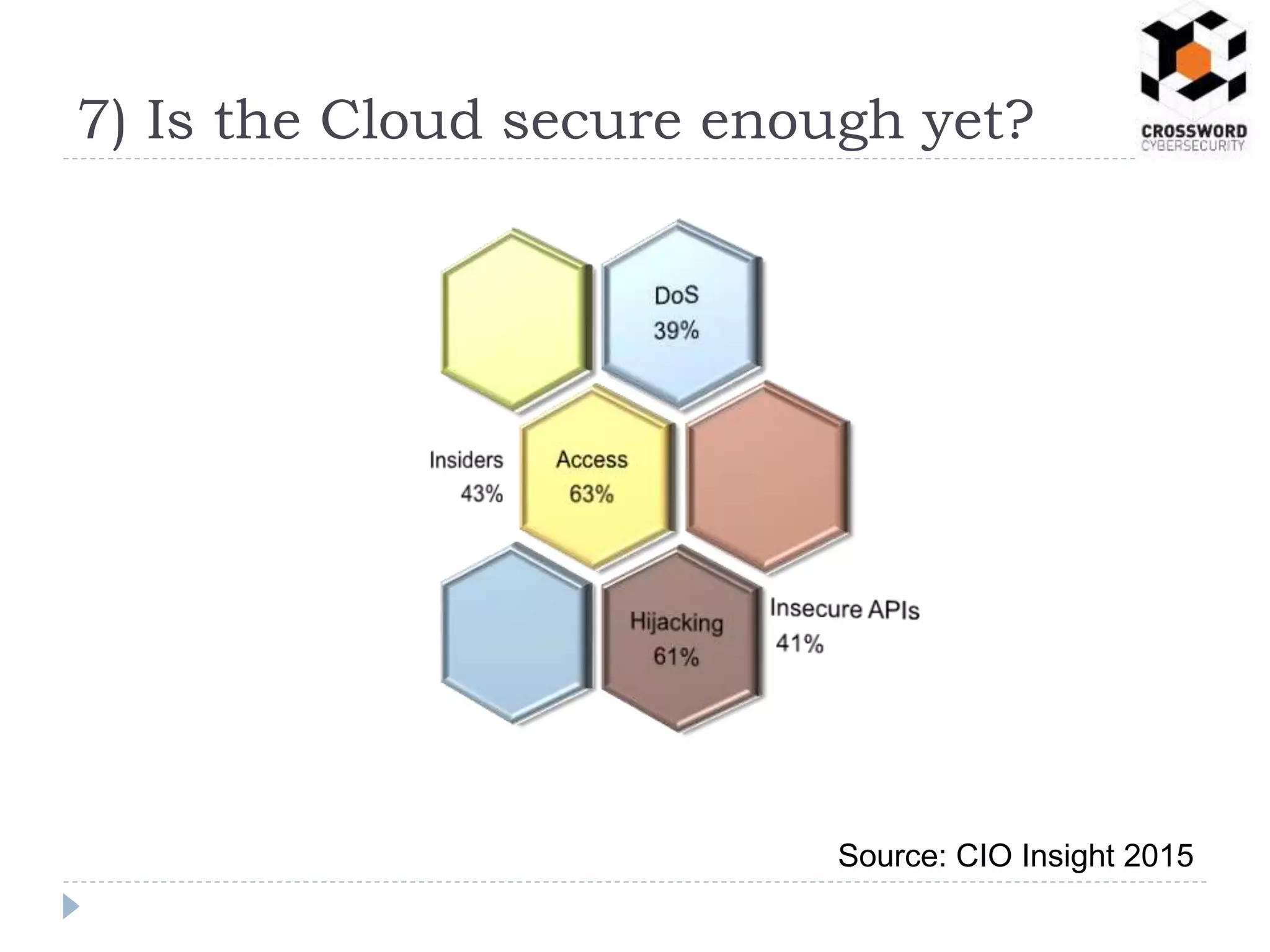
Within the next 3 years, there will likely be a major cyber attack or data breach that fundamentally changes how industry executives view cyber security (1). As organizations become more interconnected through business partnerships and the internet of things, the traditional concept of network perimeters will be outdated, and every employee, supplier, and connected device will be a potential security risk (2, 3). Cyber criminals and hackers will increase in sophistication and organization, potentially collaborating with other threat groups like terrorists or state actors (4). To address these growing challenges, industries and governments will need to increase collaboration on threat information sharing and security standards (5). The massive expansion of internet-connected devices and data volumes will vastly increase the potential attack surface that must be