This document contains questions from previous years' exams on the subject of algorithms, specifically regarding dynamic programming, greedy techniques, and related algorithms. It is divided into multiple parts covering different topics:
- Part A contains short answer and descriptive questions on dynamic programming techniques like coin changing, Floyd's algorithm, knapsack problem, and greedy algorithms.
- Part B contains longer descriptive questions requiring explanations and examples regarding dynamic programming, Floyd's algorithm, optimal binary search trees, knapsack problem, traveling salesman problem, and greedy algorithms like Prim's, Kruskal's and Dijkstra's algorithms.
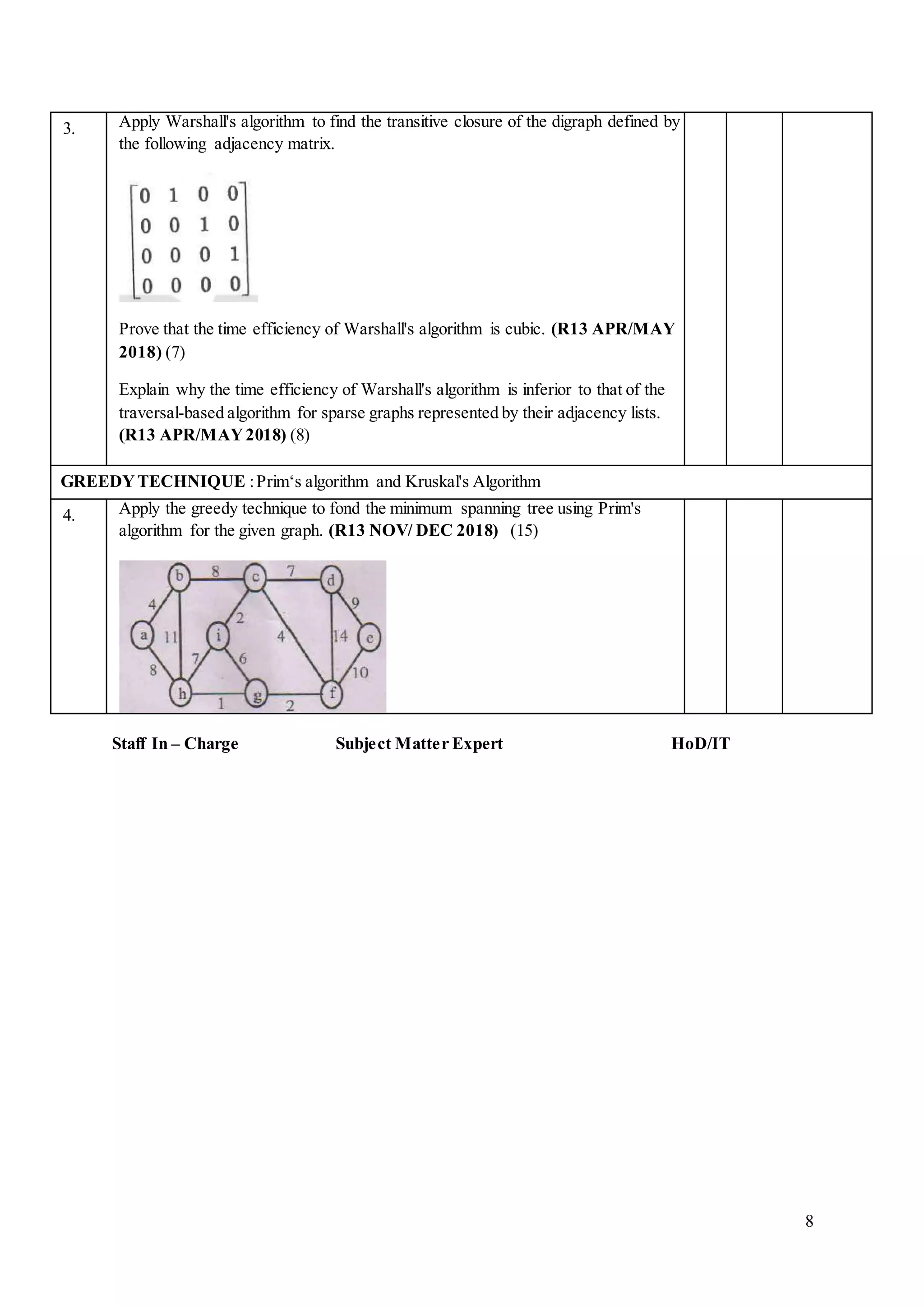
- Part C contains even more in-depth questions solving problems using dynamic programming, Warshall's algorithm