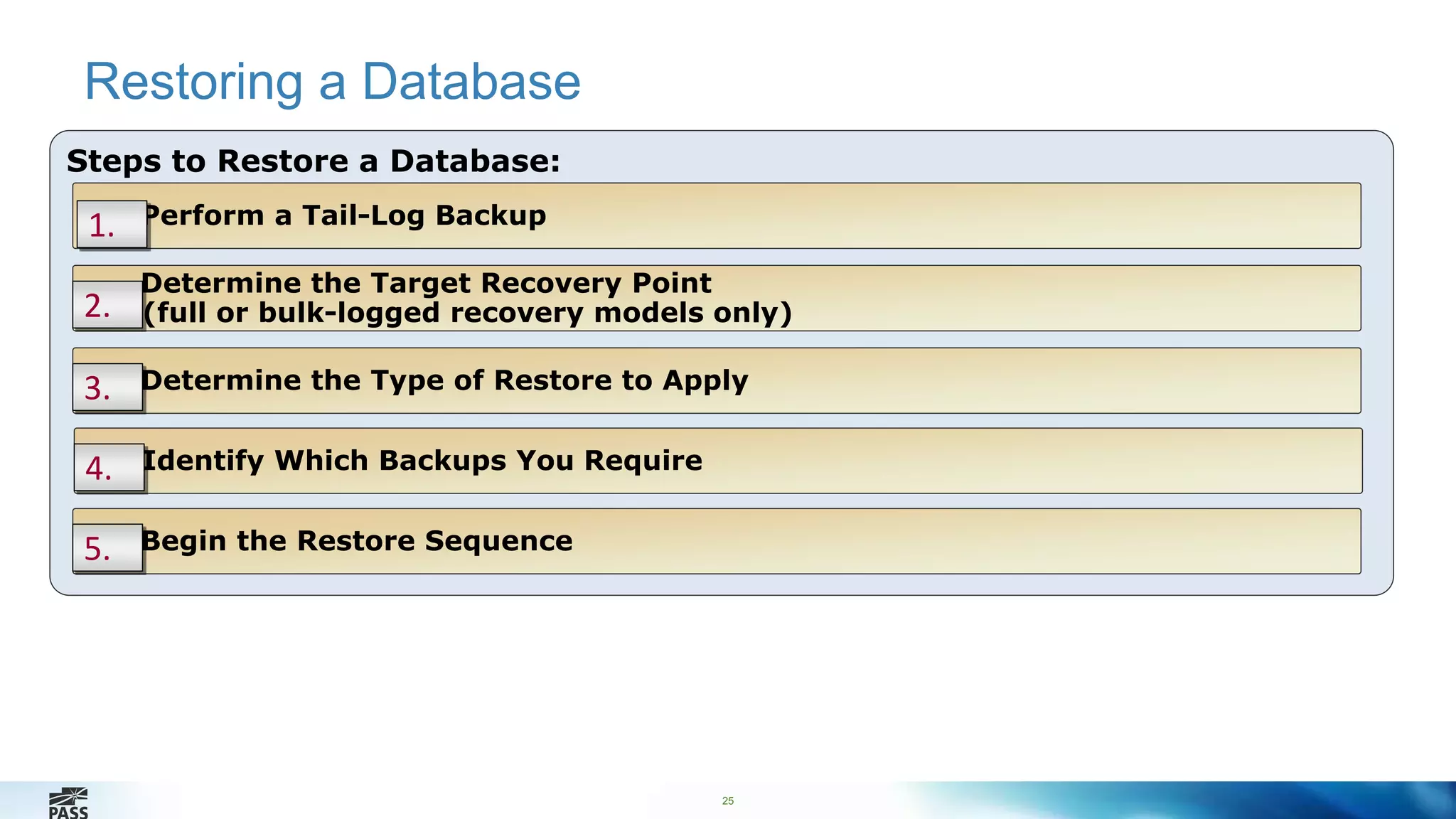
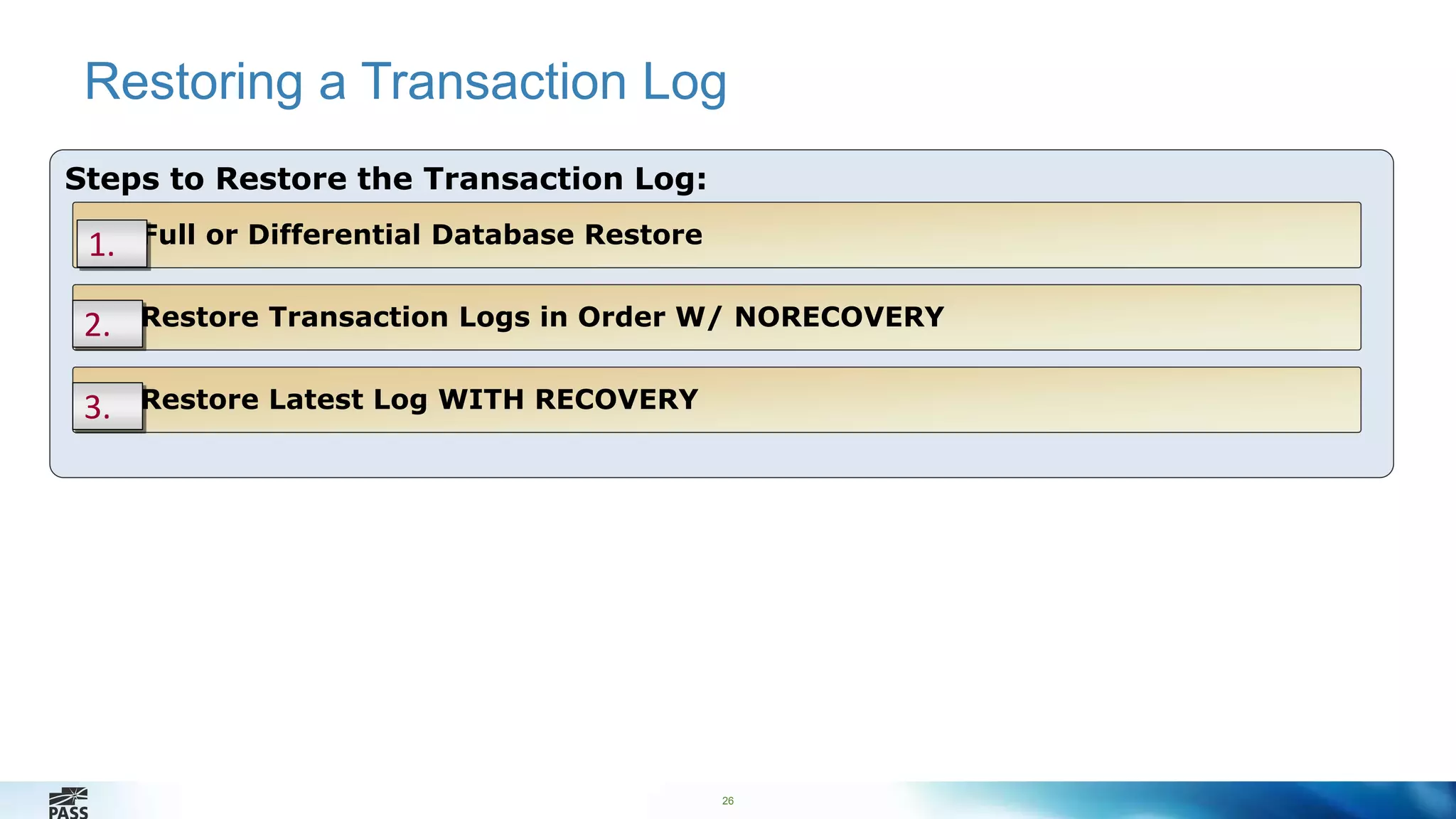
This document outlines the features and strategies for database backup and encryption in SQL Server 2014, led by Percy Reyes. It details types of backups, recovery models, and the importance and implementation of backup encryption while also covering backup integrity and restore processes. Additionally, it provides practical demonstrations on performing encrypted backups and restoring user databases.







![Performing a Full Database Backup
14
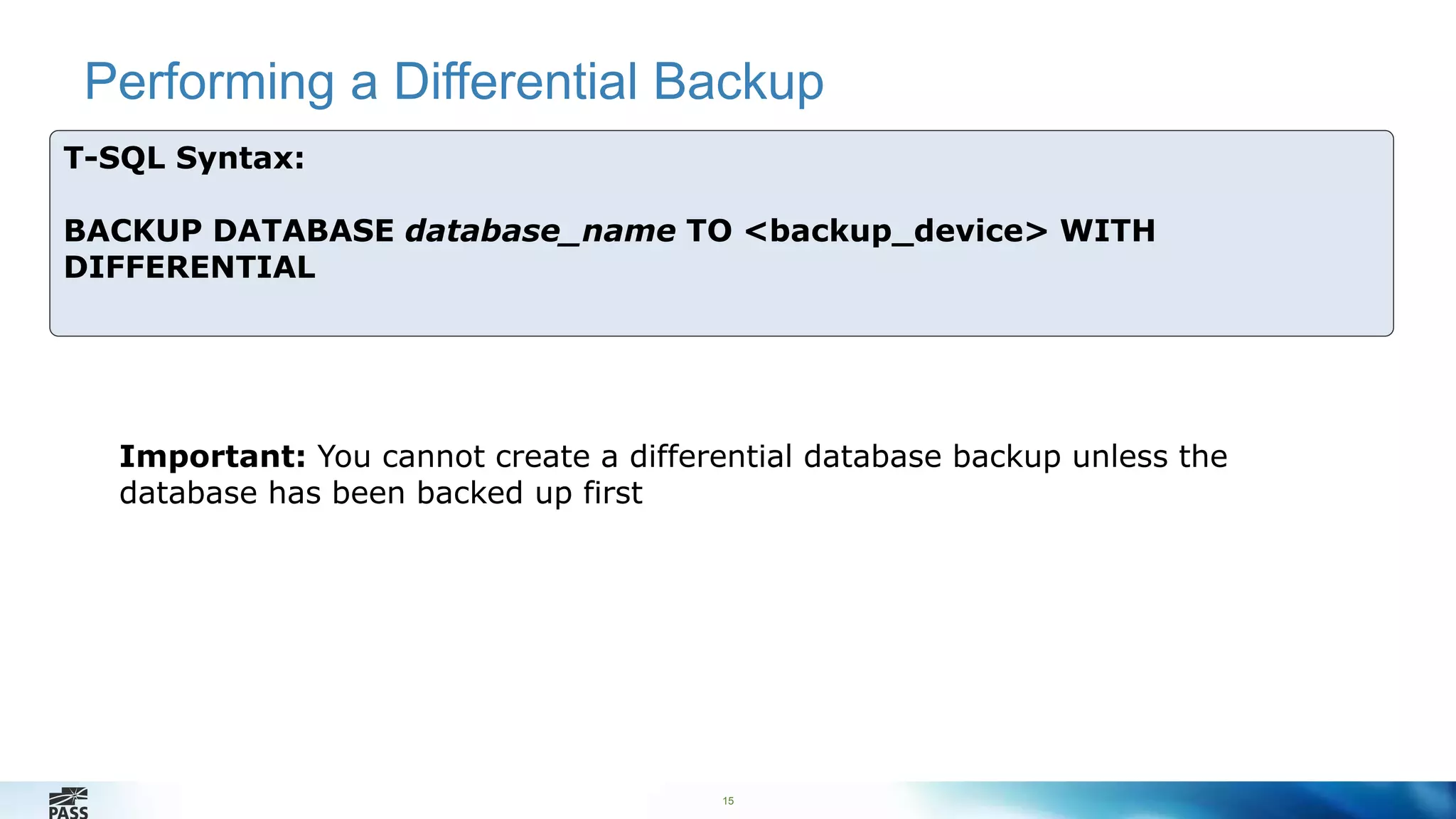
T-SQL Syntax:
BACKUP DATABASE database
TO backup_device [ ,...n ]
[ WITH with_options [ ,...o ] ] ;
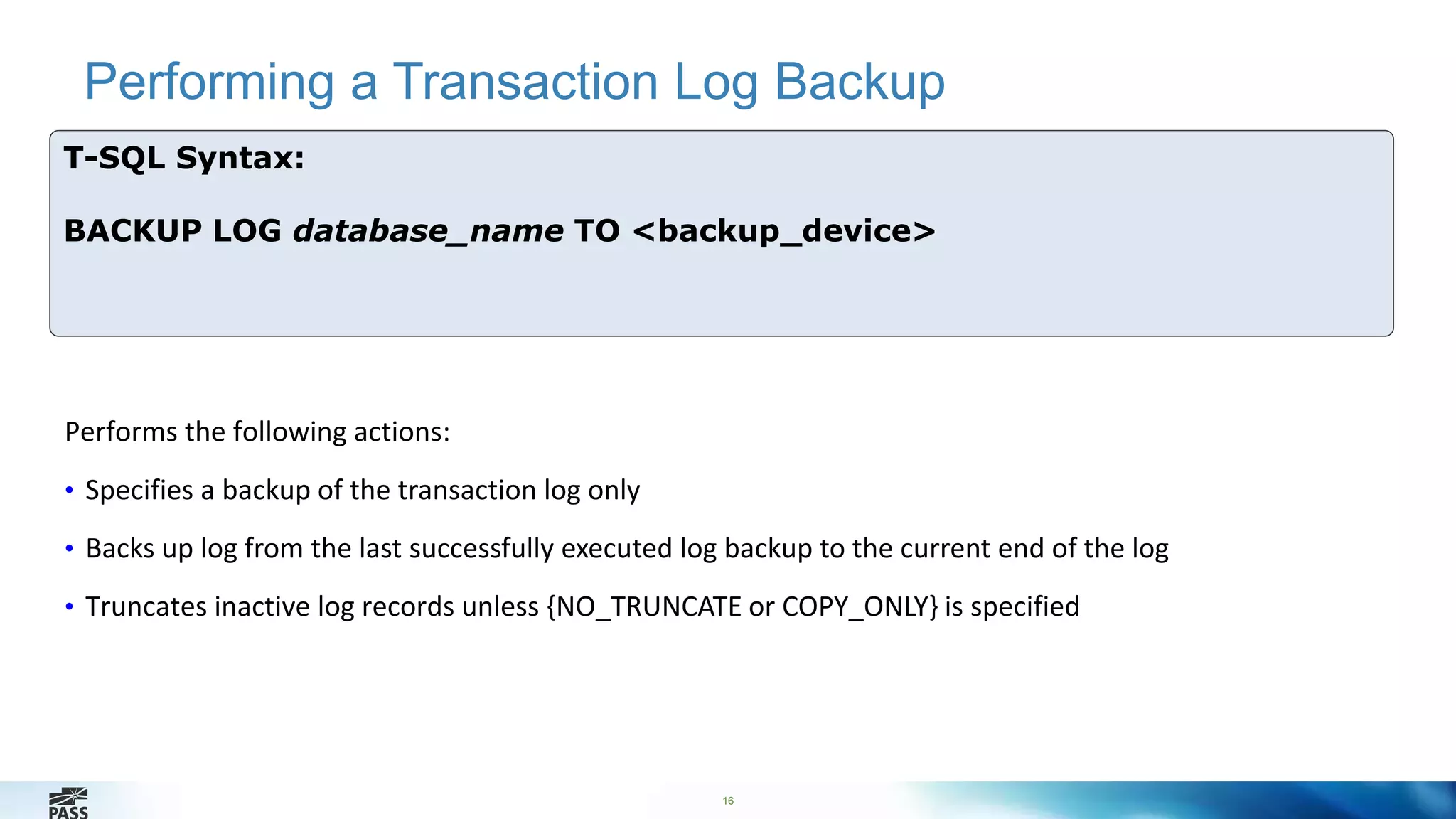
Performs the following actions:
• Backups up the specified database
• Specifies the backup device
• Specifies options i.e. { COMPRESSION | NO_COMPRESSION }](https://image.slidesharecdn.com/sqlserver2014backupencryption-percyreyes-141203005135-conversion-gate02/75/24-HOP-edicion-Espanol-Sql-server-2014-backup-encryption-Percy-Reyes-14-2048.jpg)