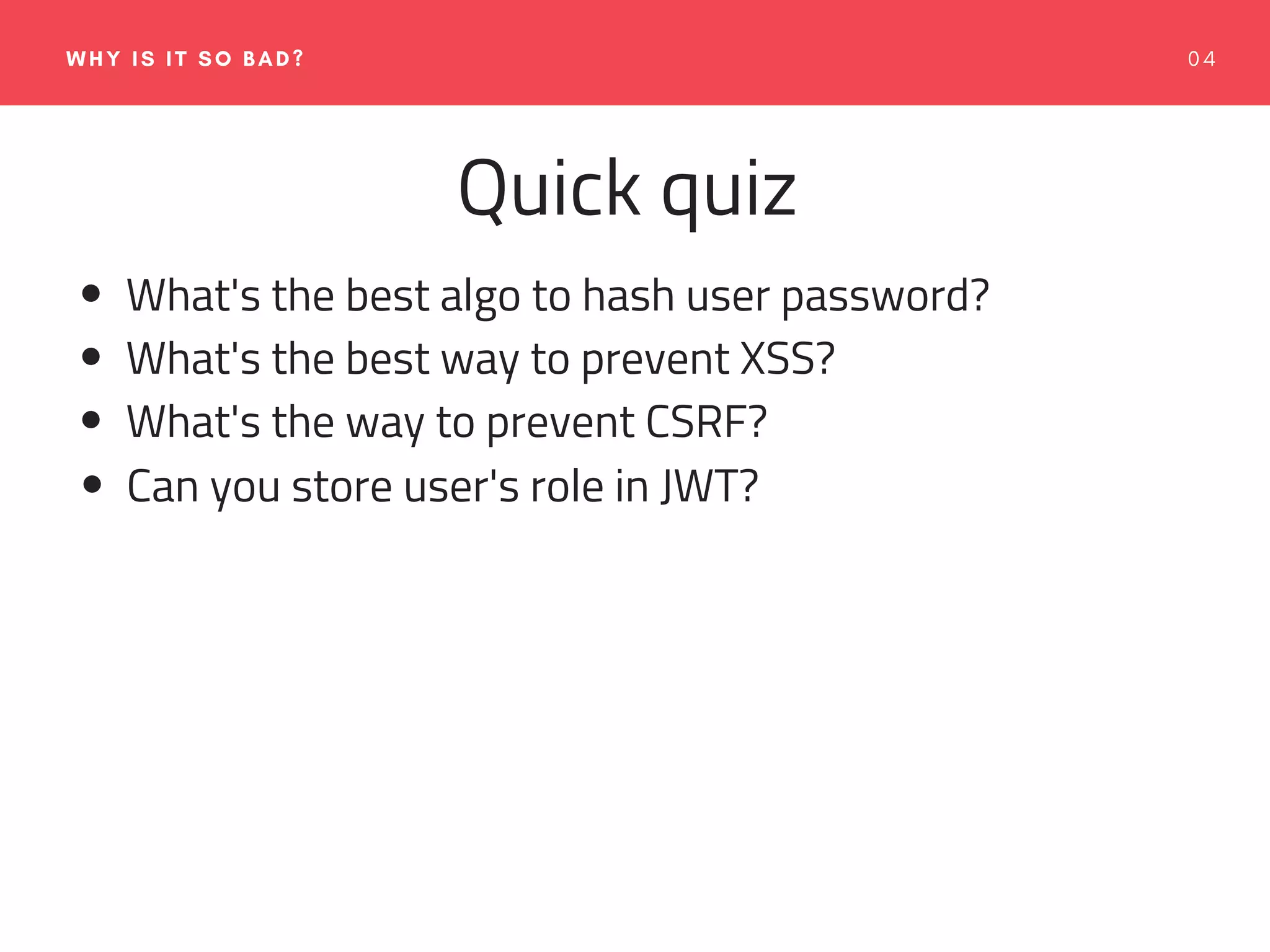
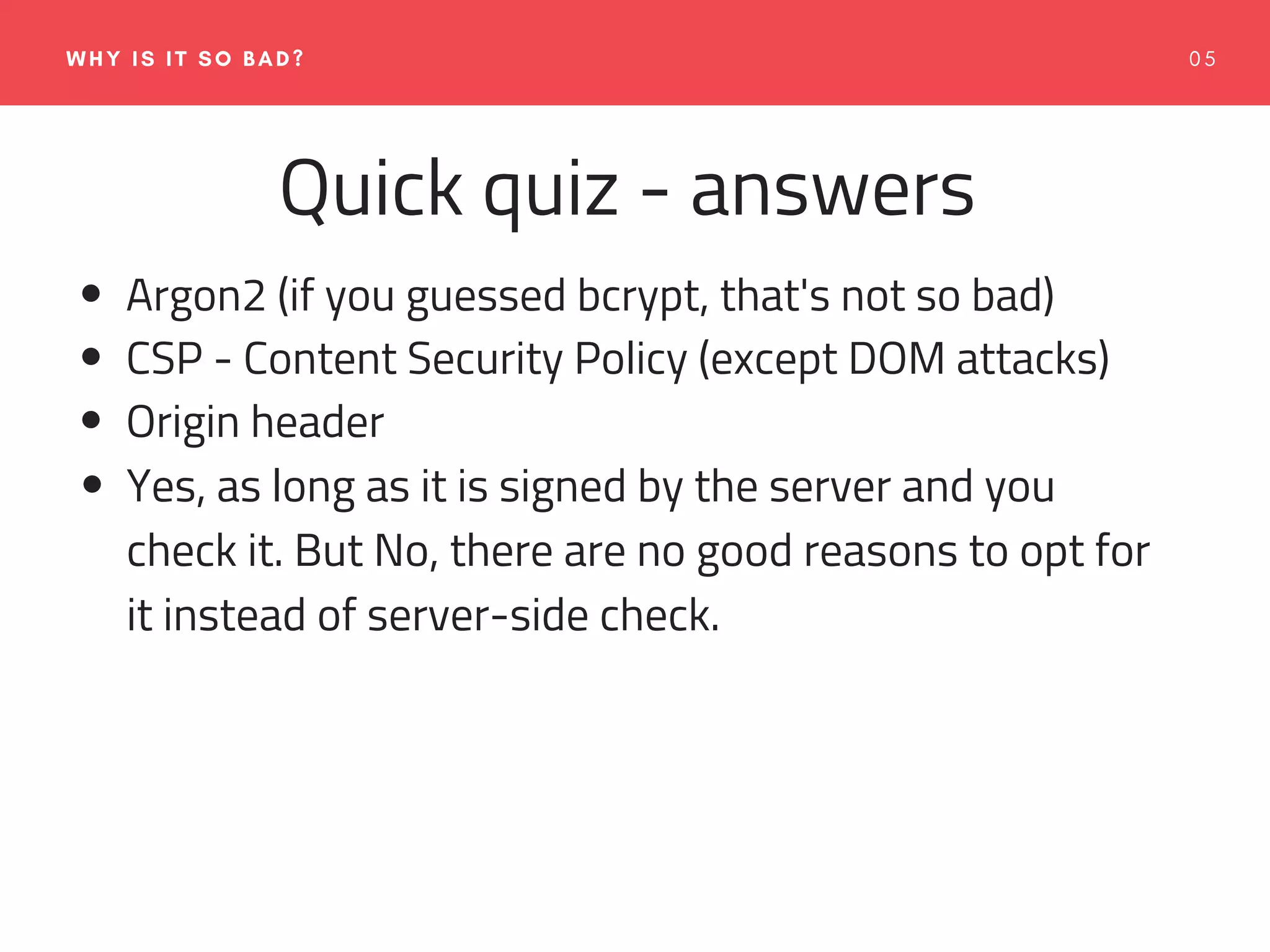
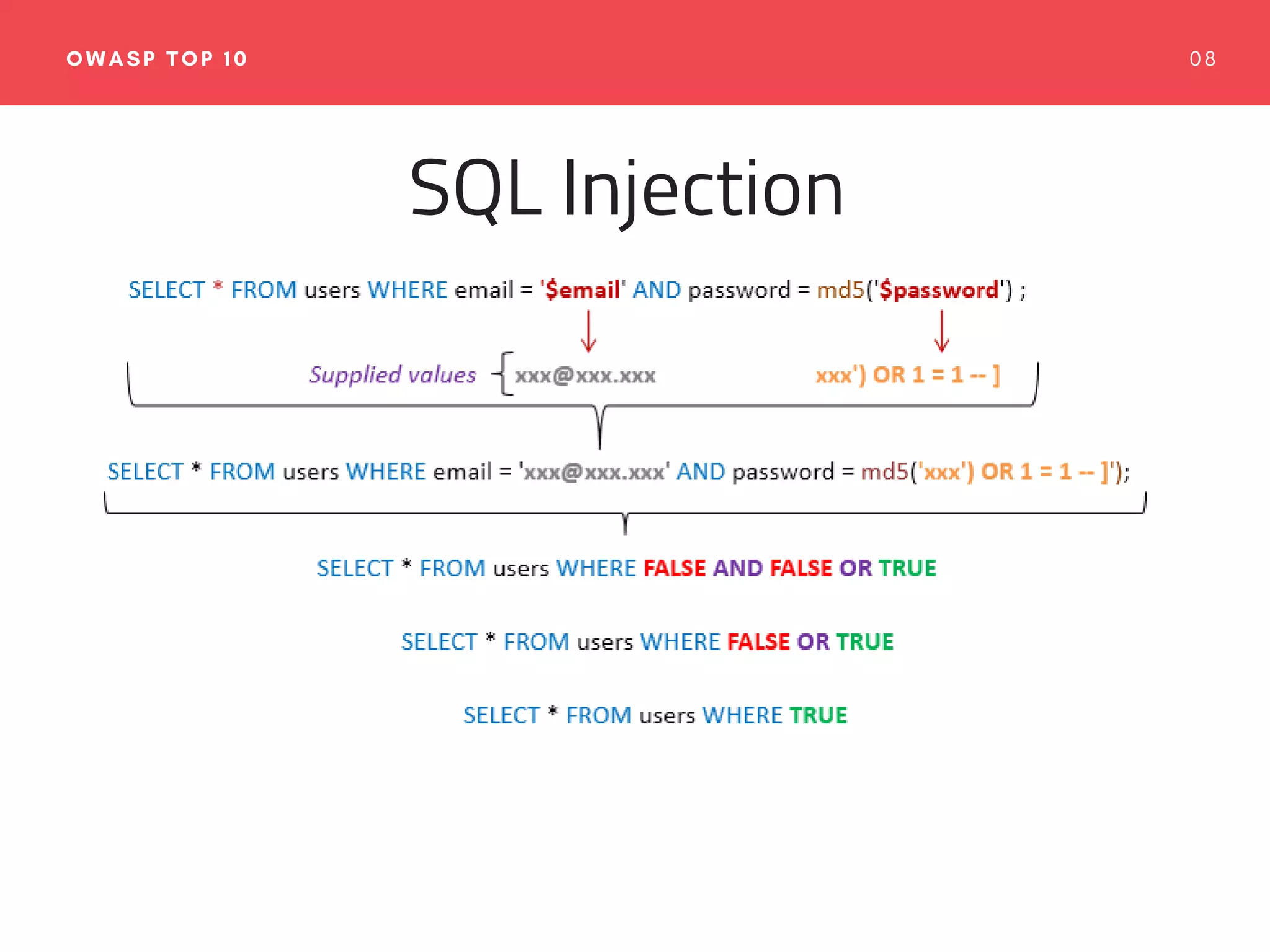
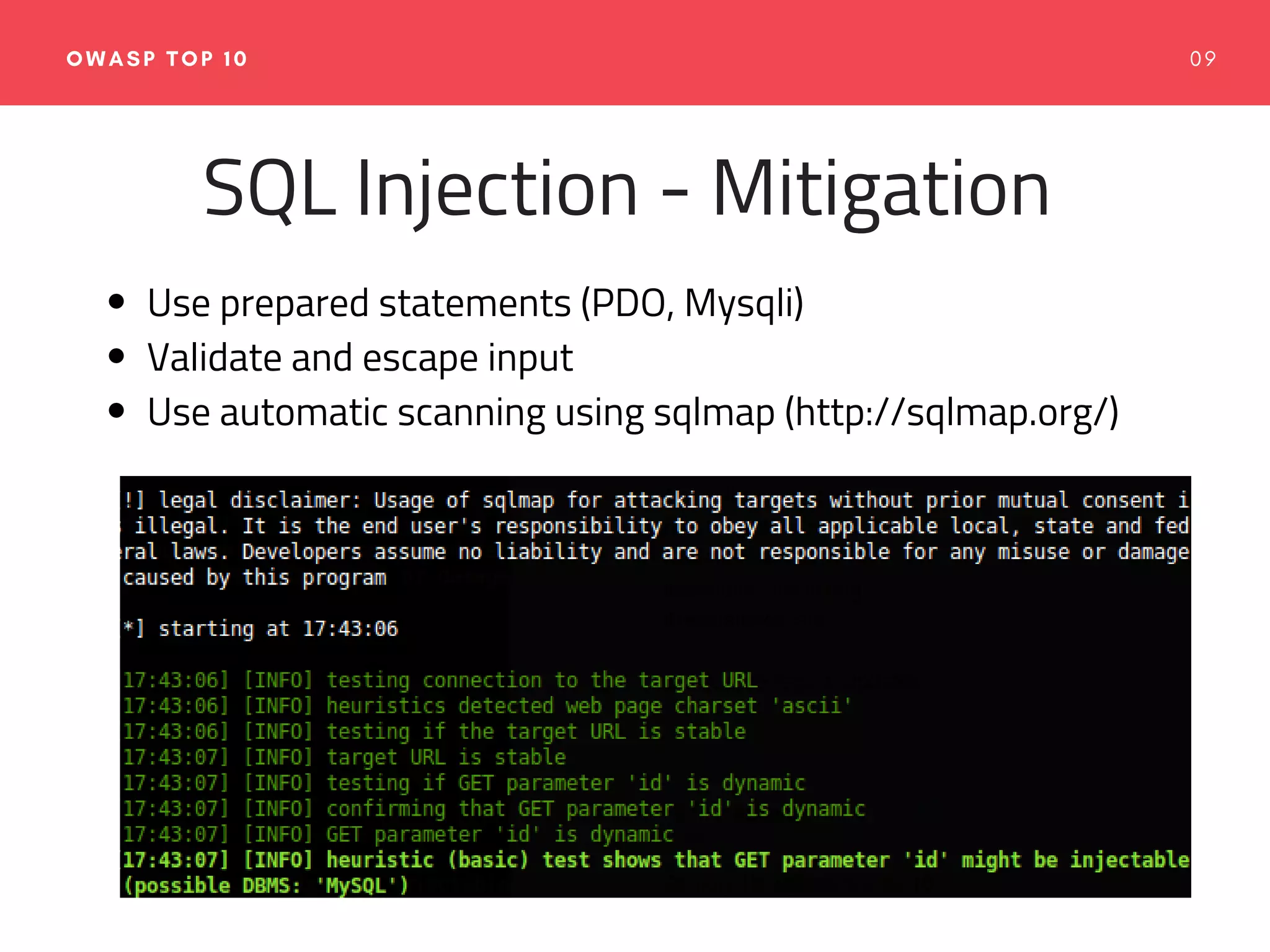
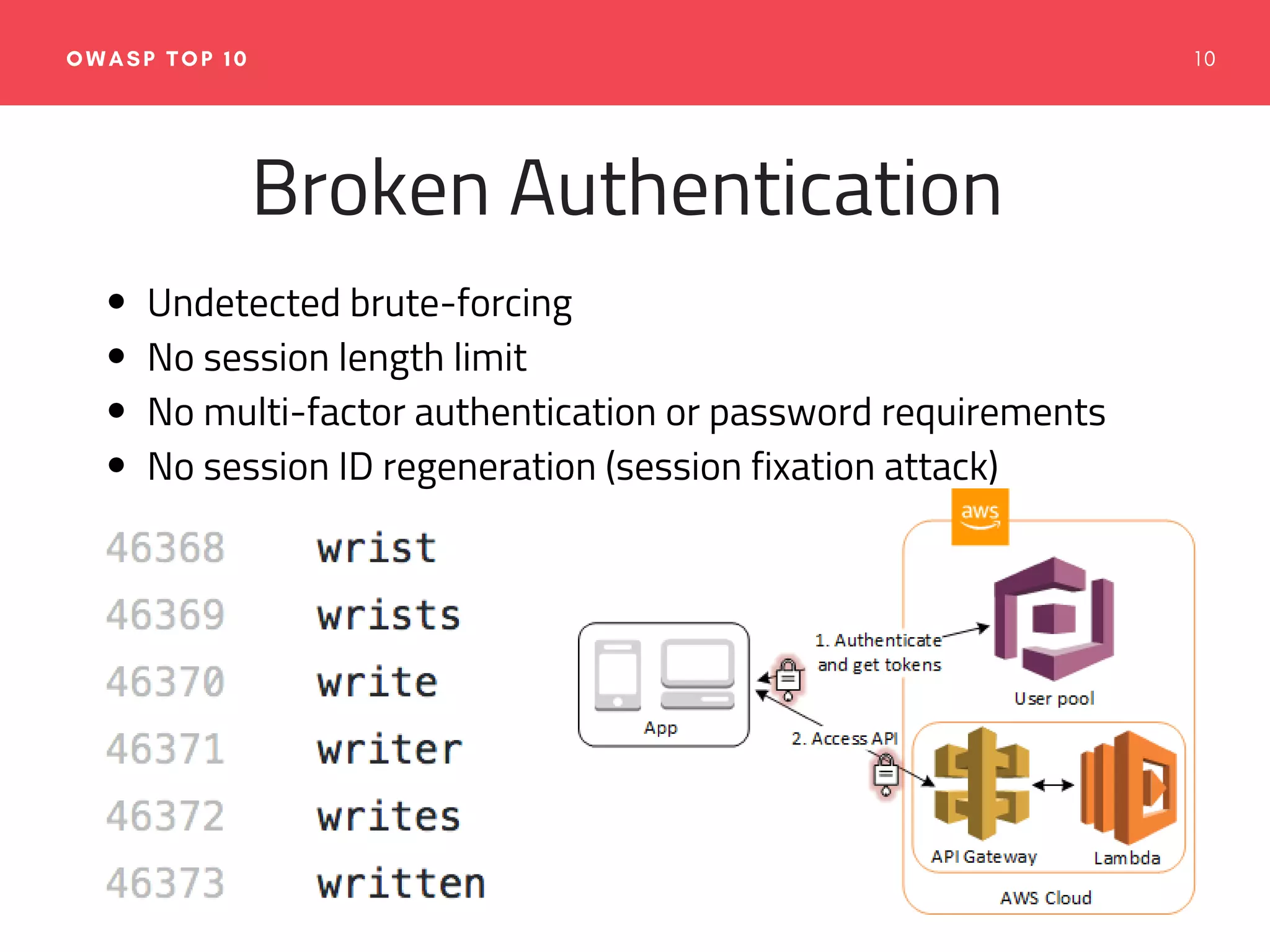
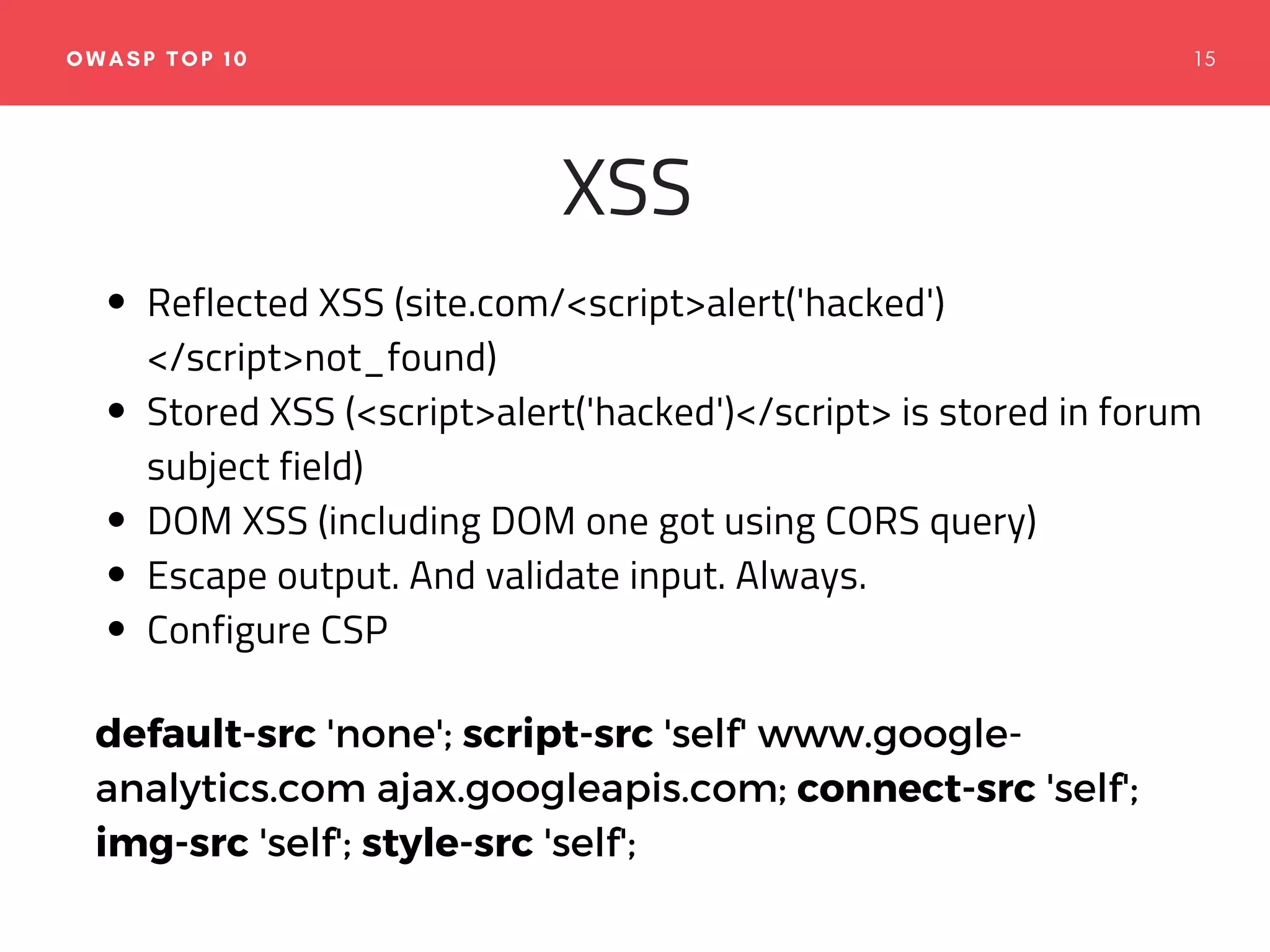
The document emphasizes the importance of web application security, discussing typical security threats and the OWASP Top 10 vulnerabilities. It offers practical tools and strategies to prevent attacks, such as adopting secure development practices, utilizing security headers, and implementing proper logging and monitoring. The authors, experienced in software development and security consulting, advocate for the integration of security education and tools in the development process.