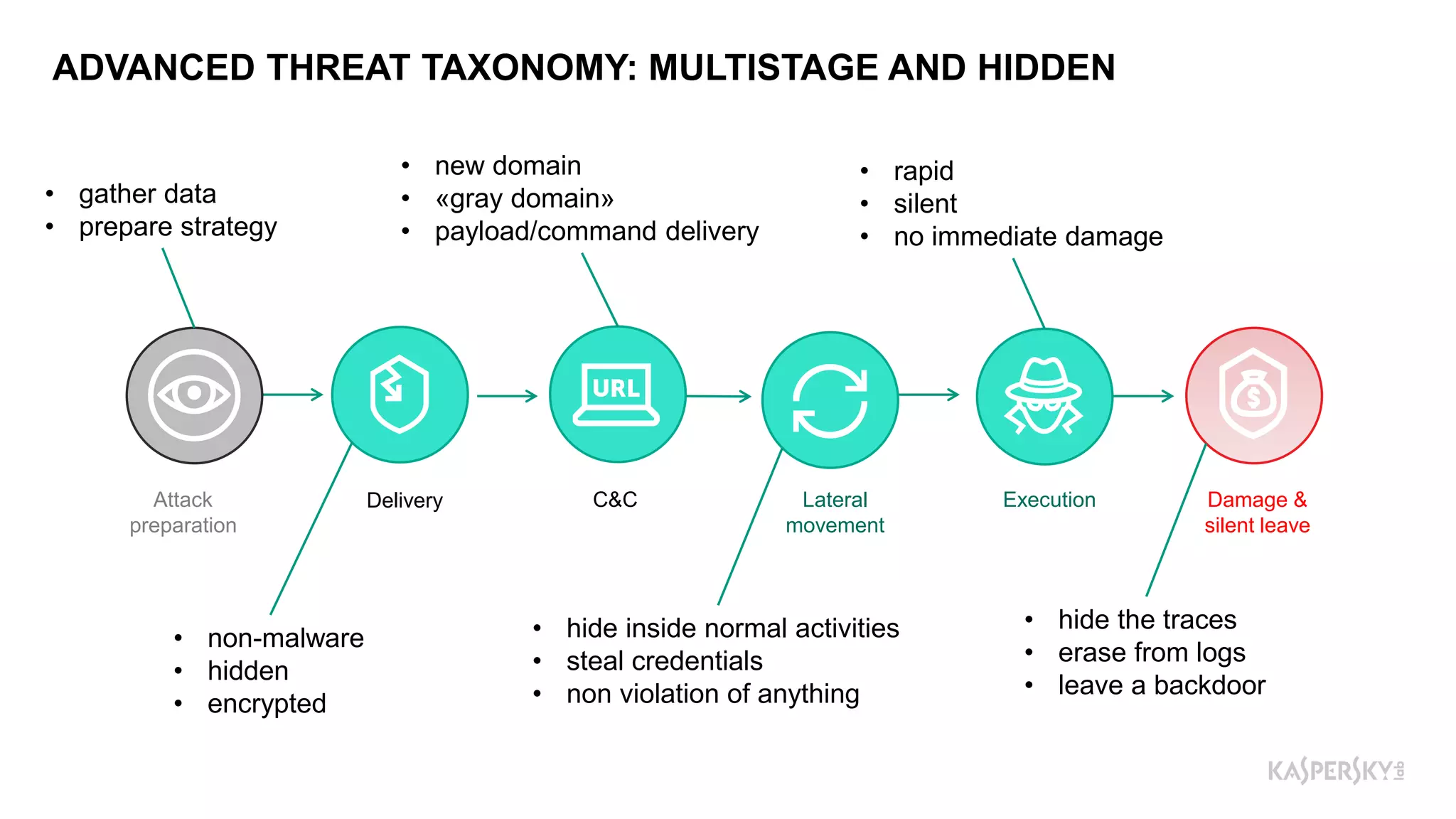
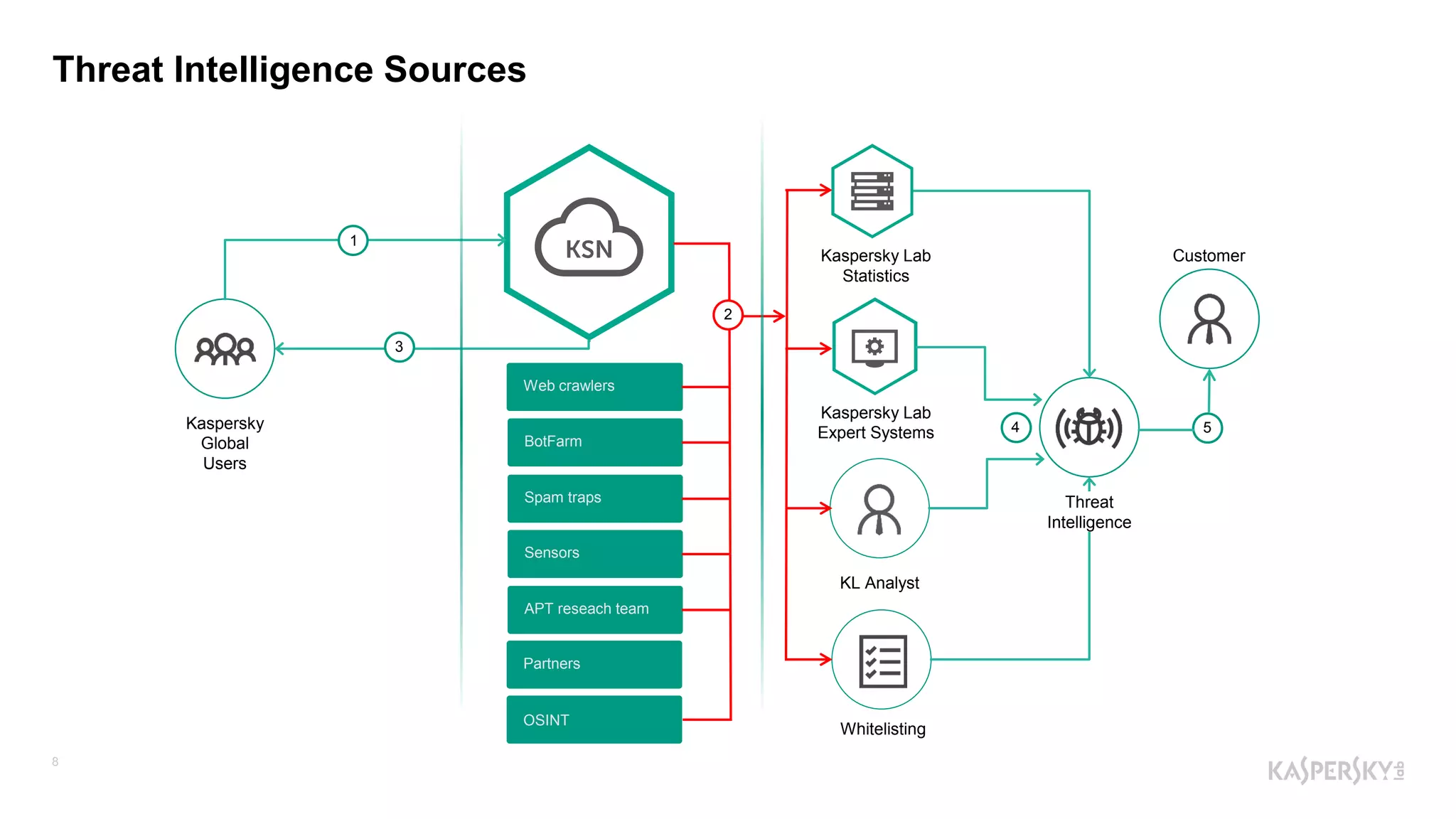
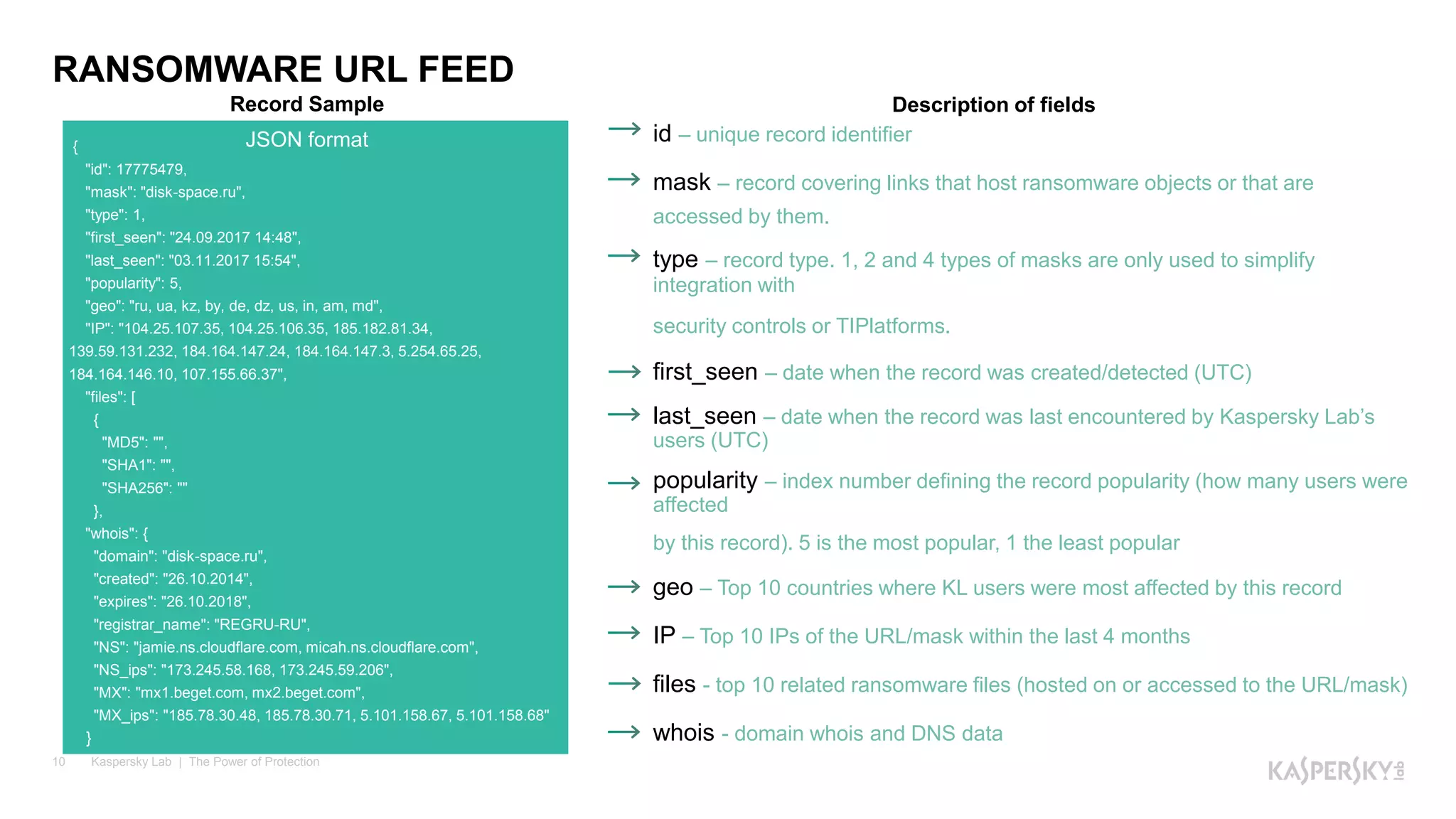
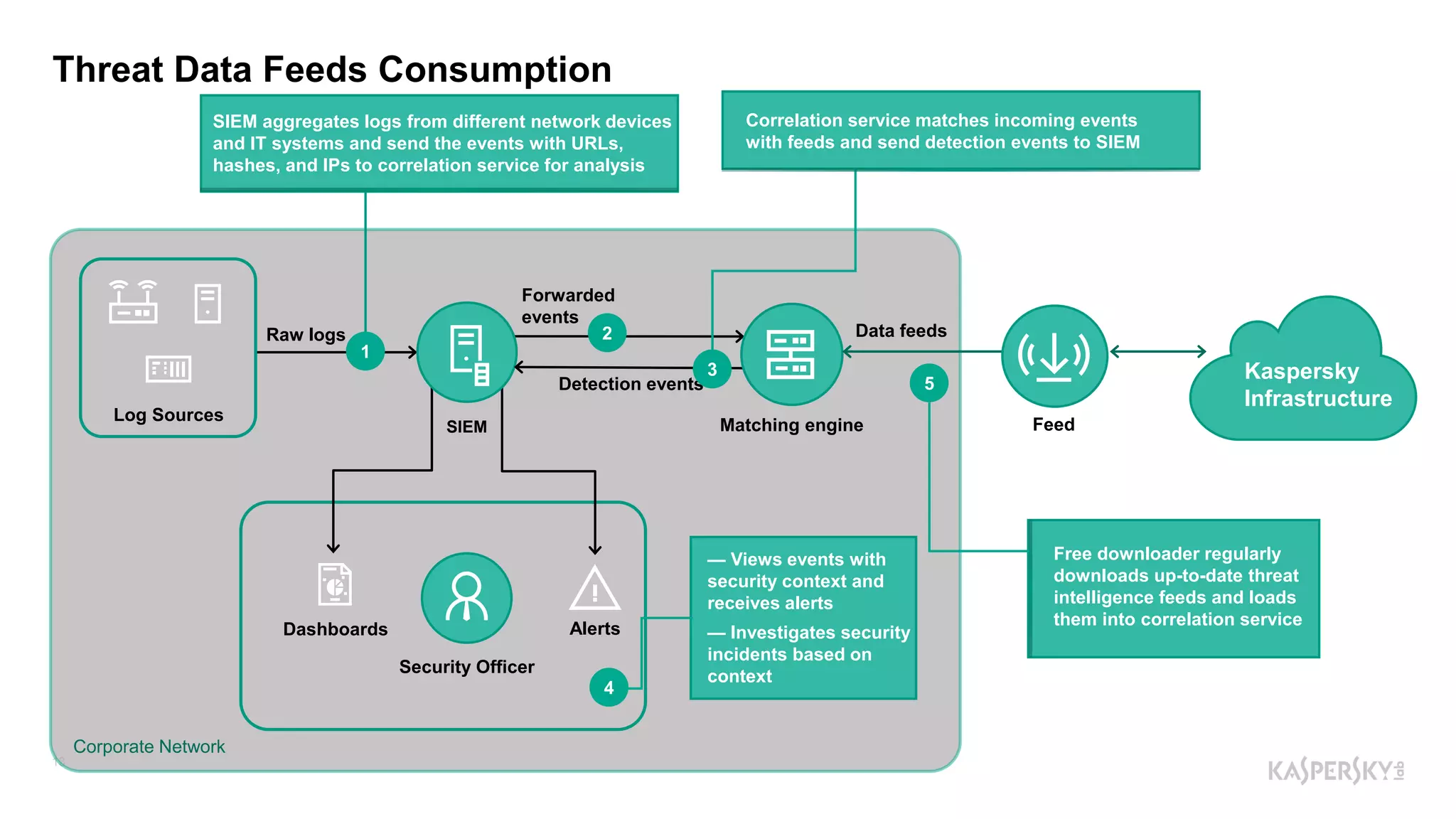
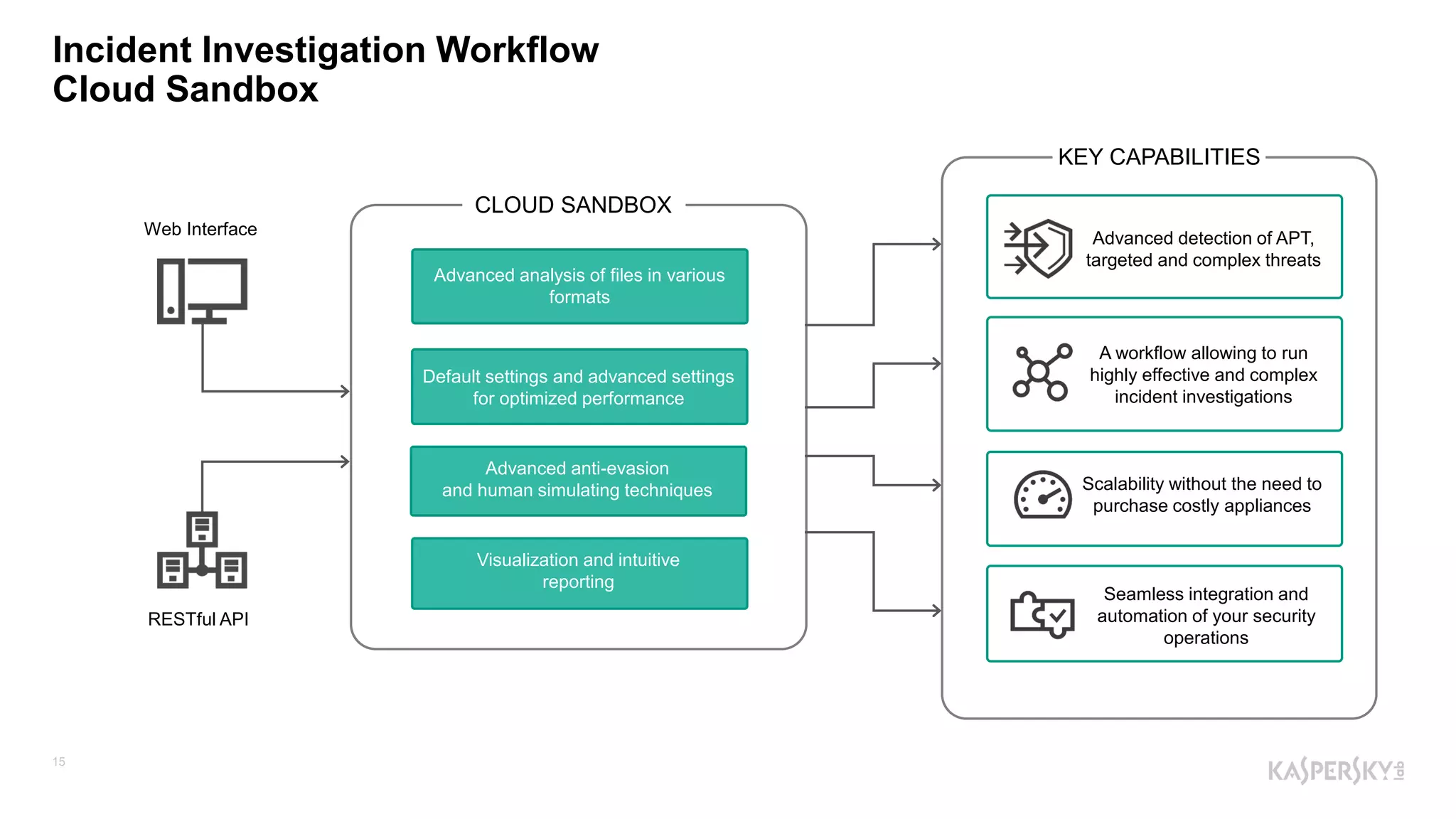
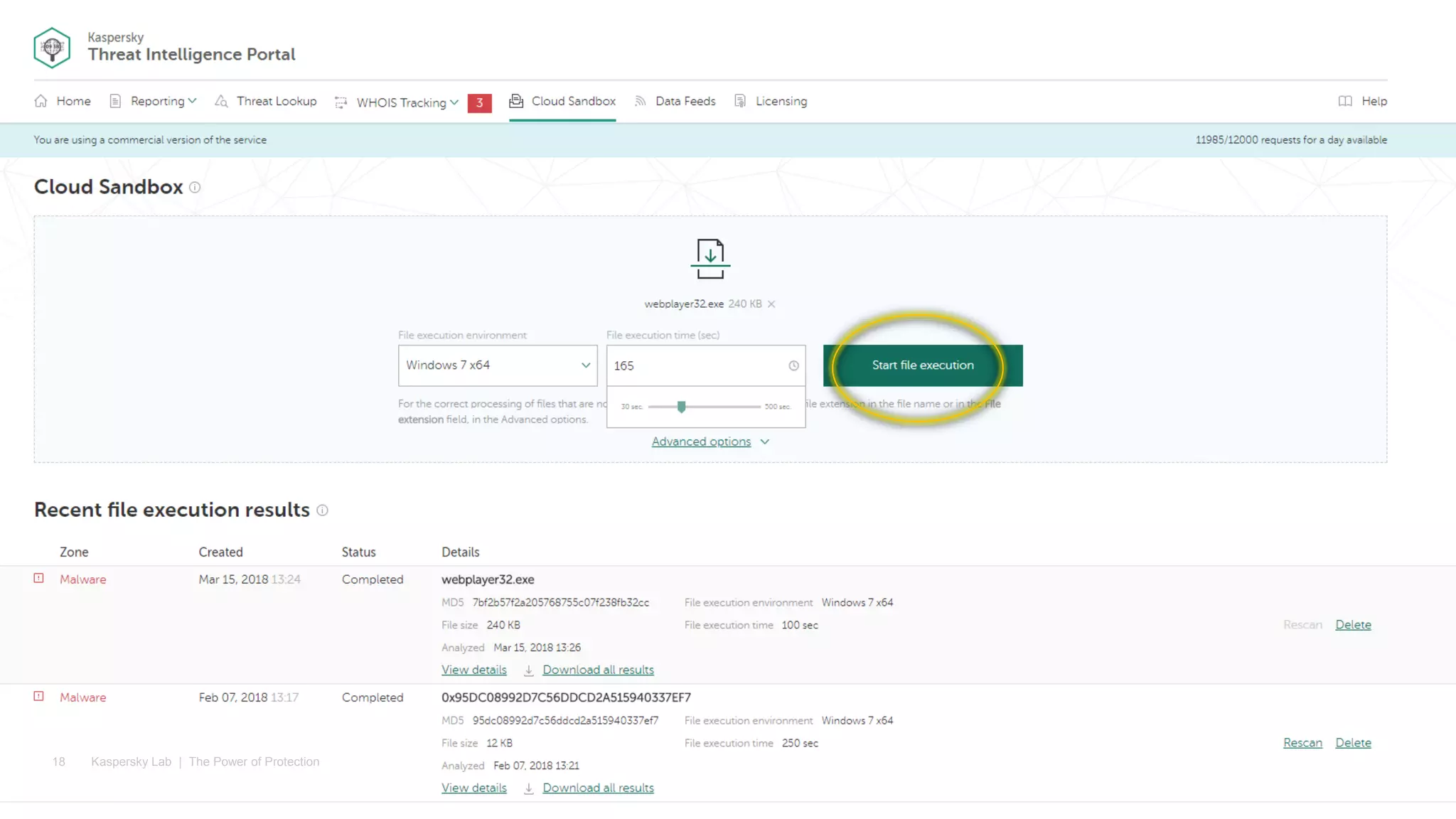
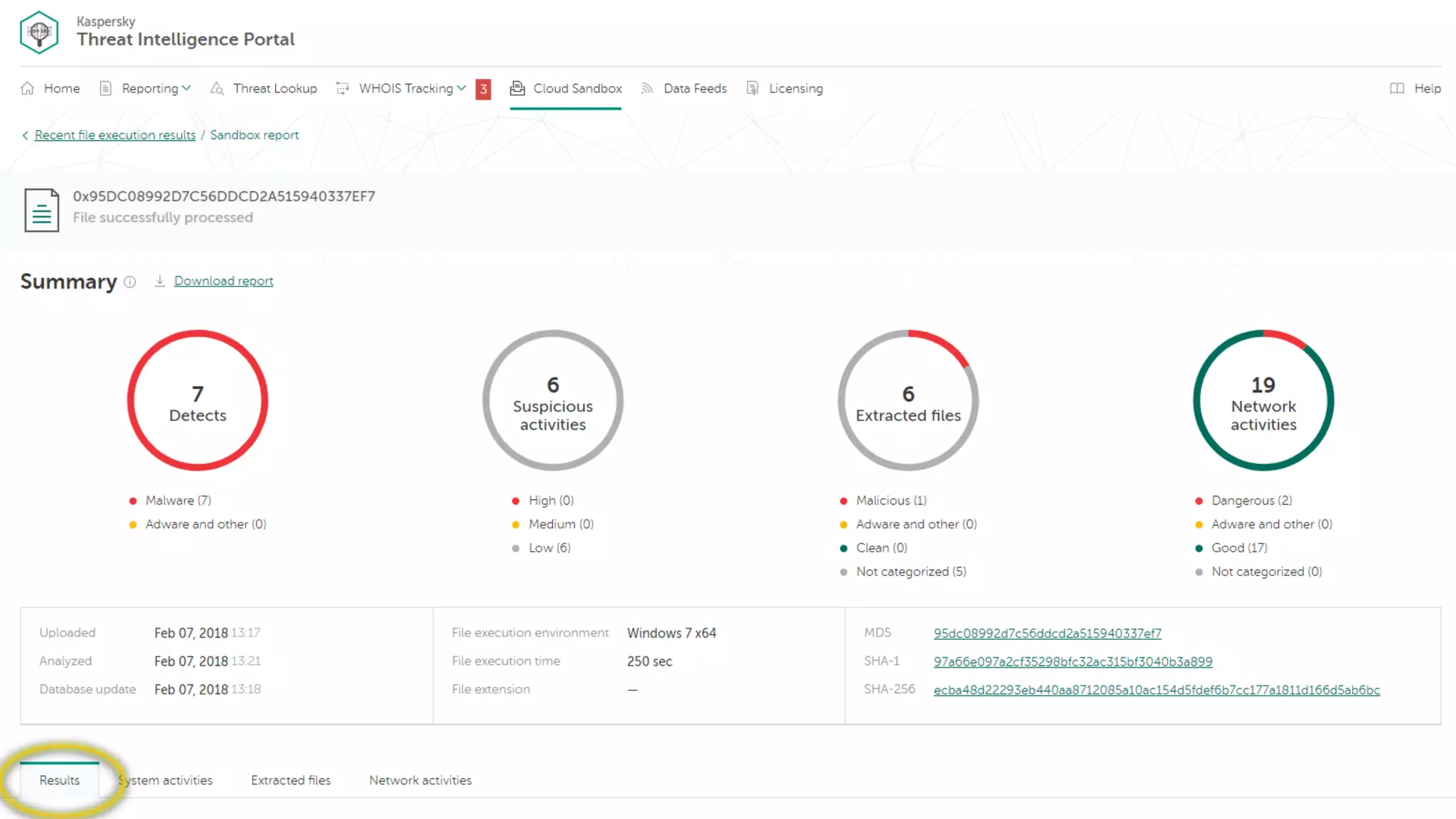
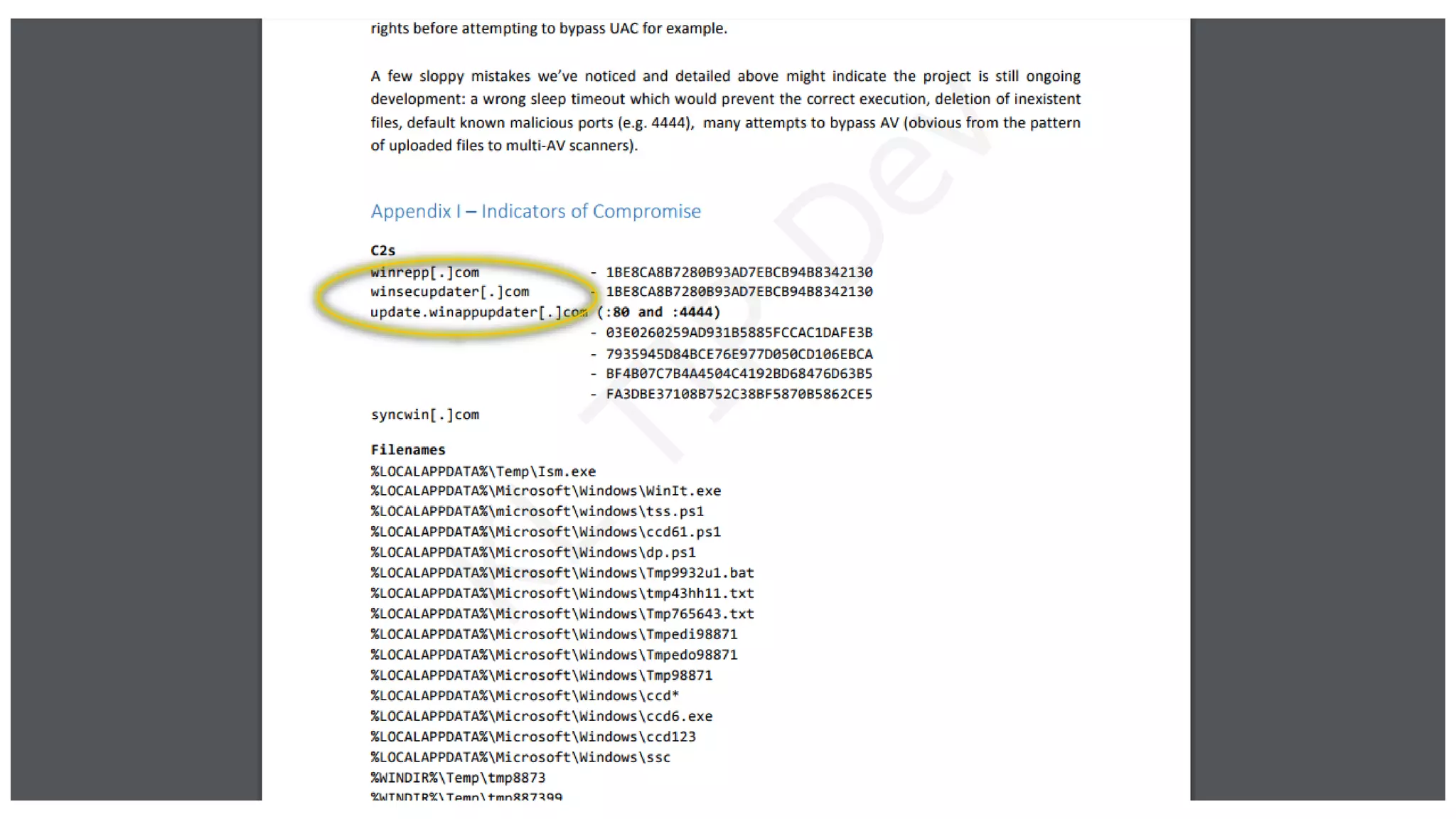
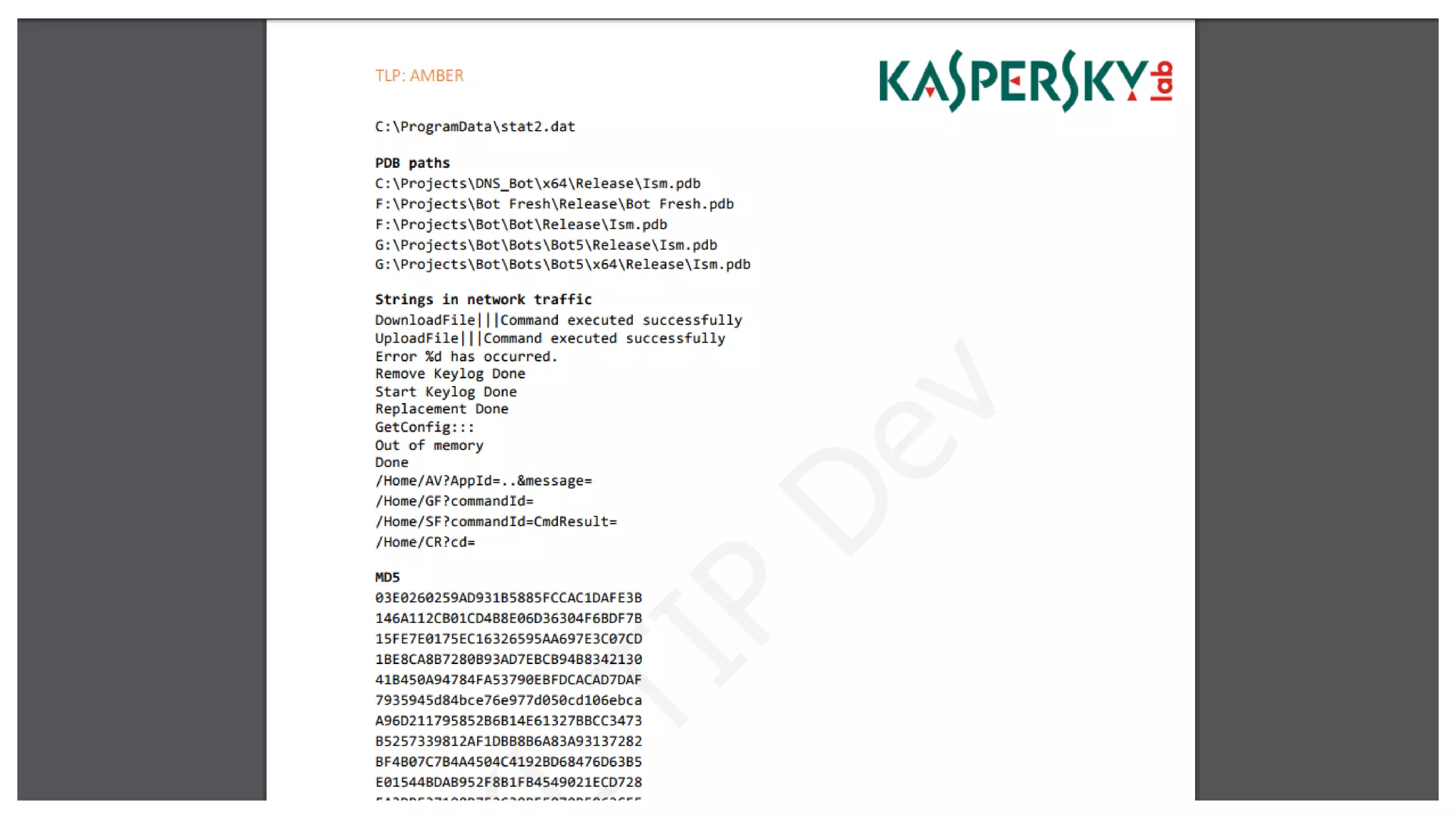
The document outlines Kaspersky Lab's Threat Intelligence capabilities, highlighting advanced threat taxonomy, incident response, and various data feeds for threat detection and analysis. It details mechanisms for threat hunting, investigation, and the framework for reporting different types of threats, including APT and financial threats. Additionally, it emphasizes Kaspersky's cloud sandbox for advanced analysis and integration with security controls.