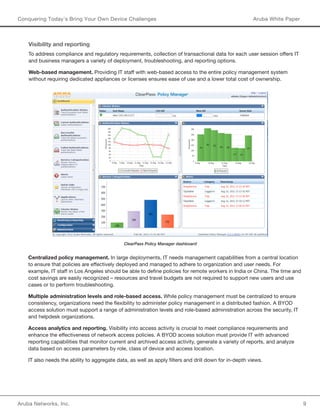
This document discusses challenges related to Bring Your Own Device (BYOD) initiatives and how to effectively manage network access. It outlines drivers for BYOD like consumer choice and IT considerations. Key challenges include managing device and data overlap, application access, policies, and helpdesk workload. Effective BYOD requires automated device onboarding, role-based policies, identifying compromised devices, and guest WiFi access. The Aruba ClearPass platform provides an integrated solution for access management across wired, wireless and VPN networks supporting any user on any device.