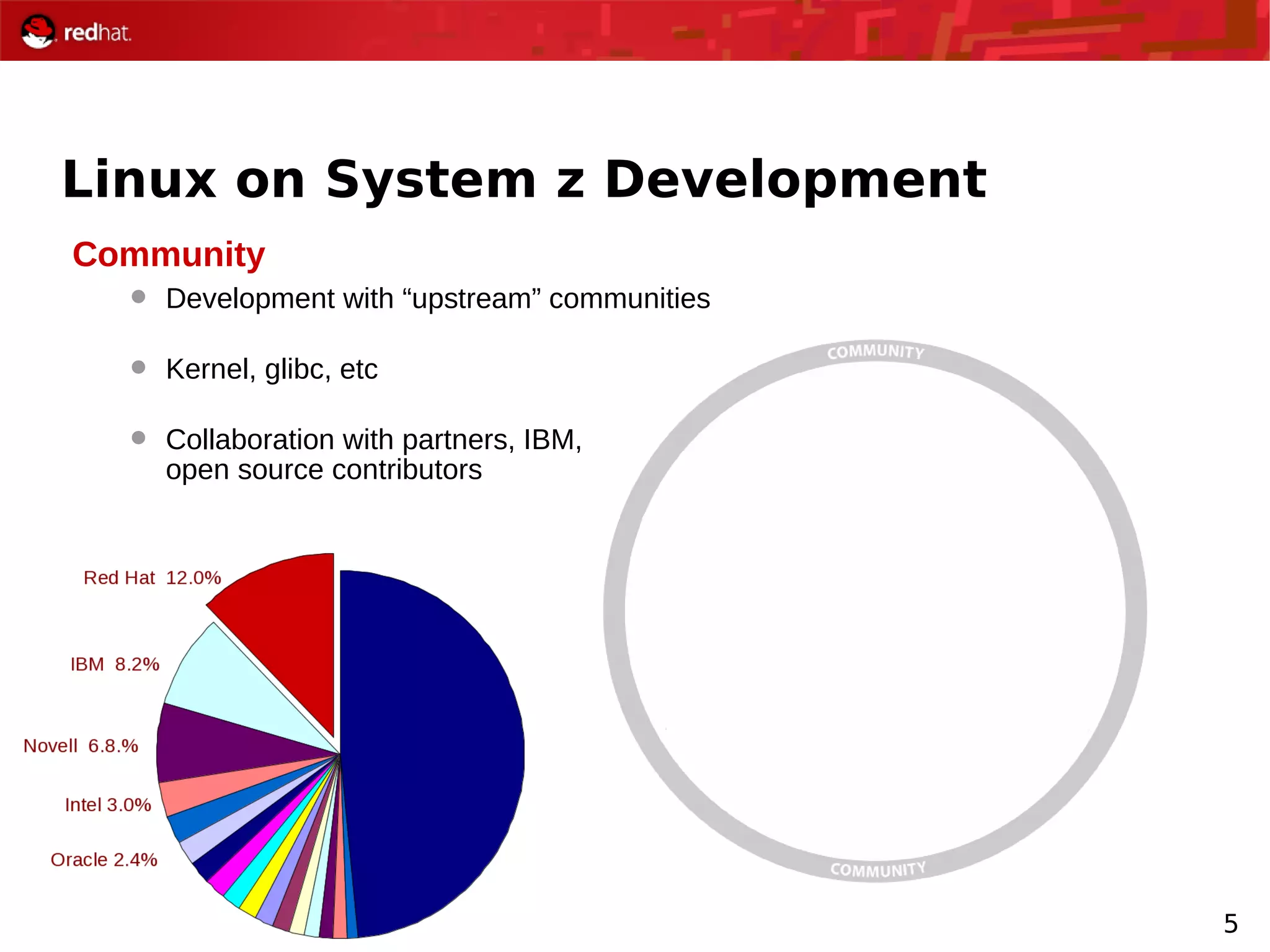
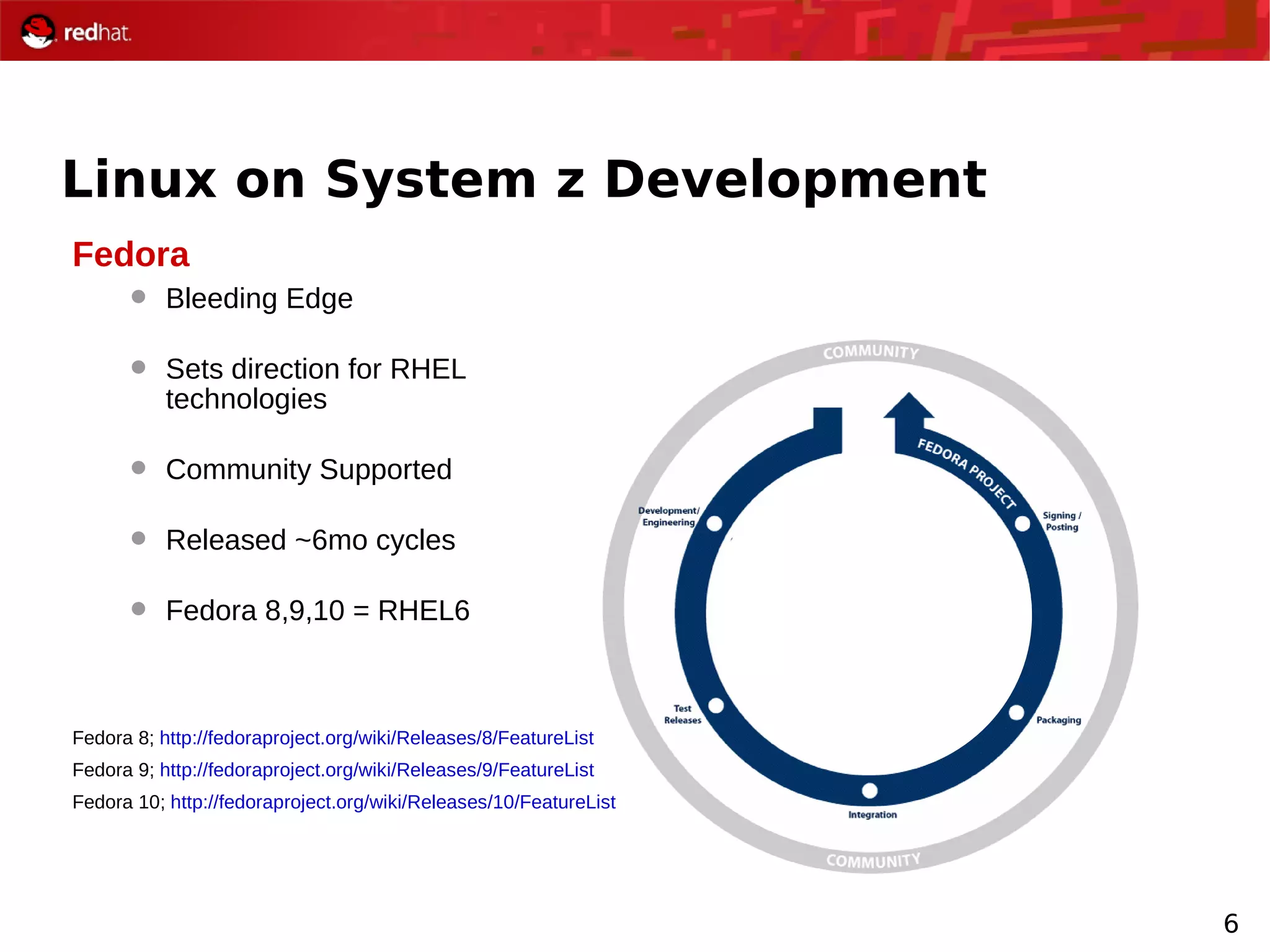
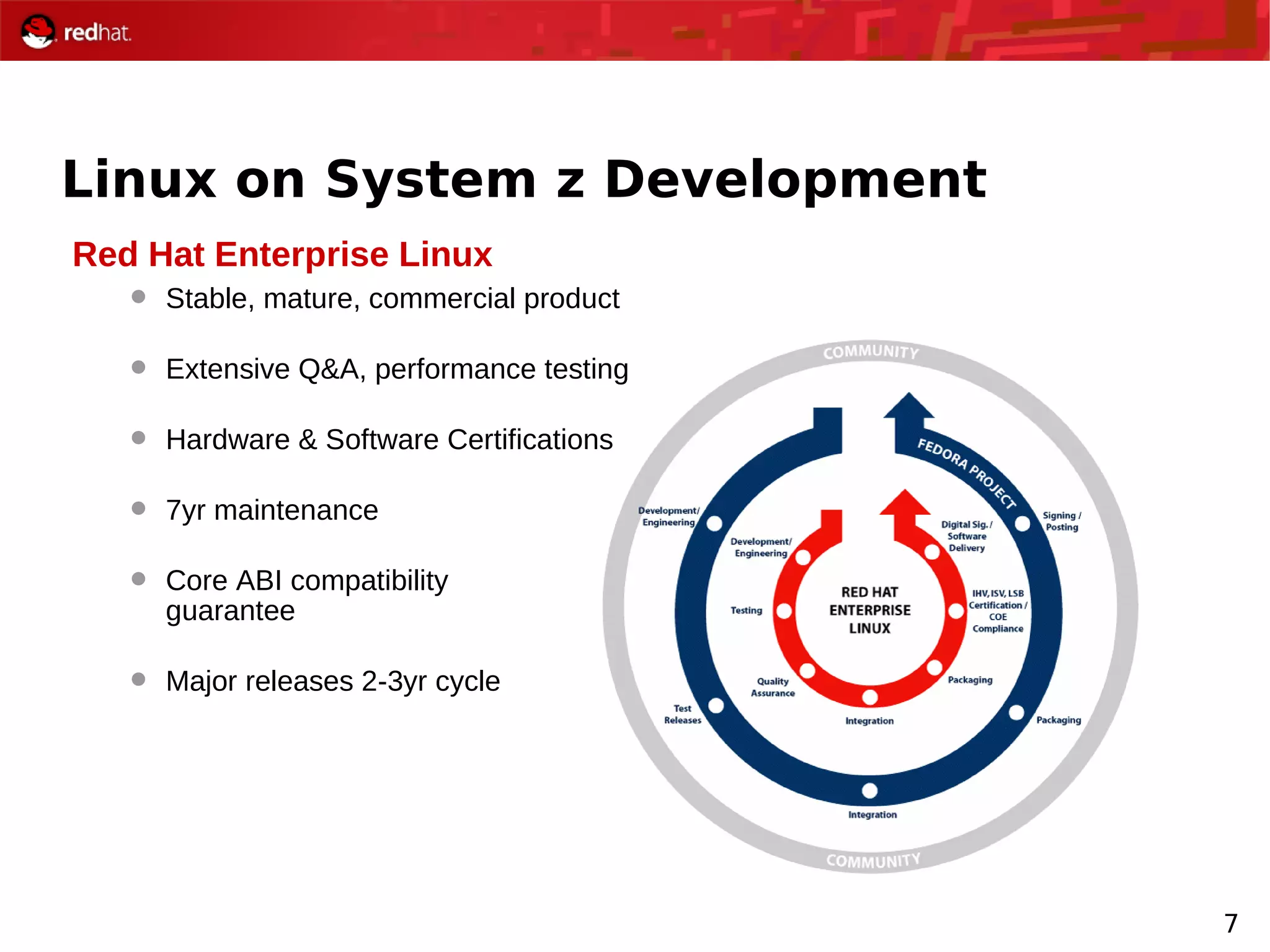
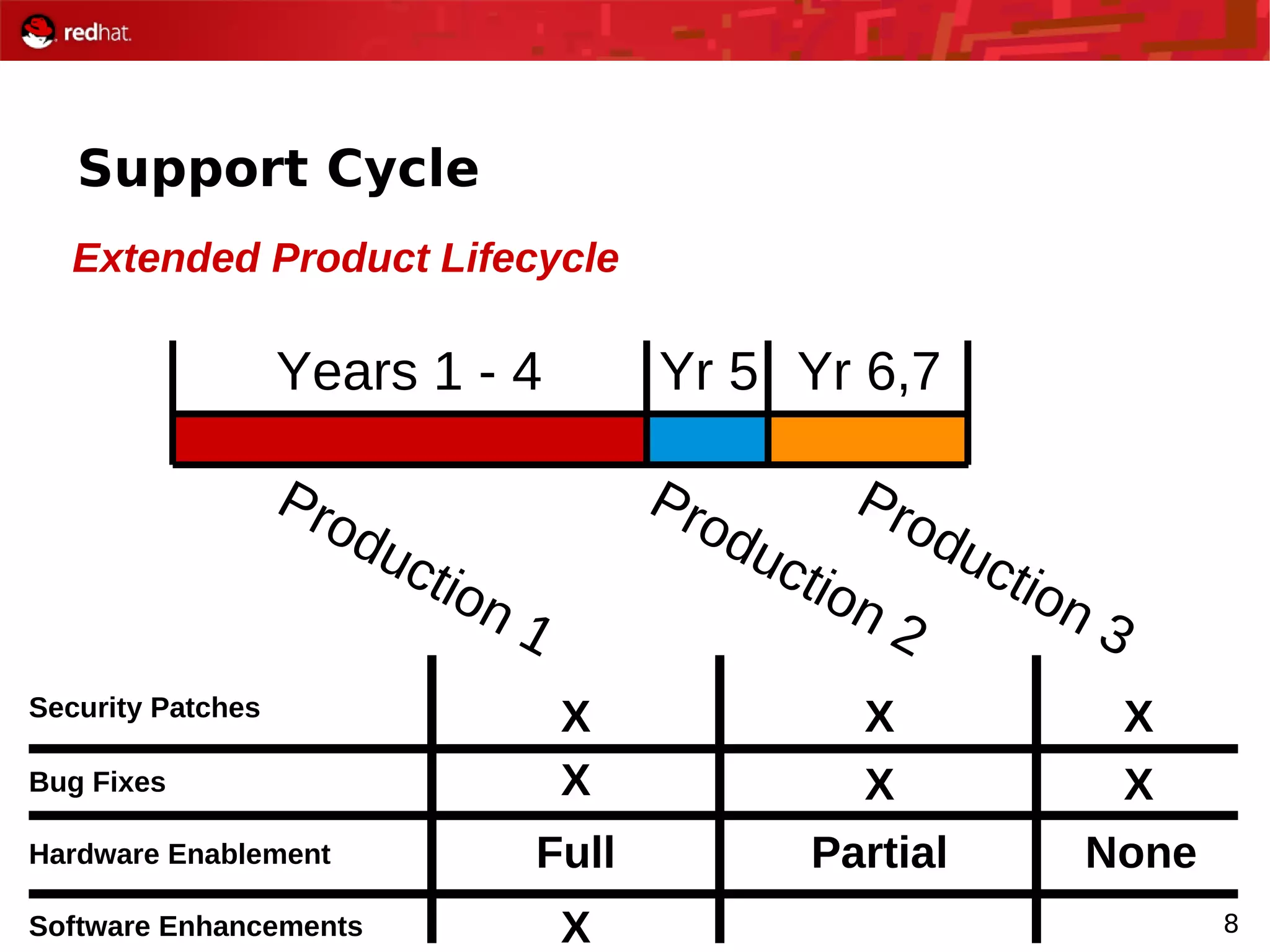
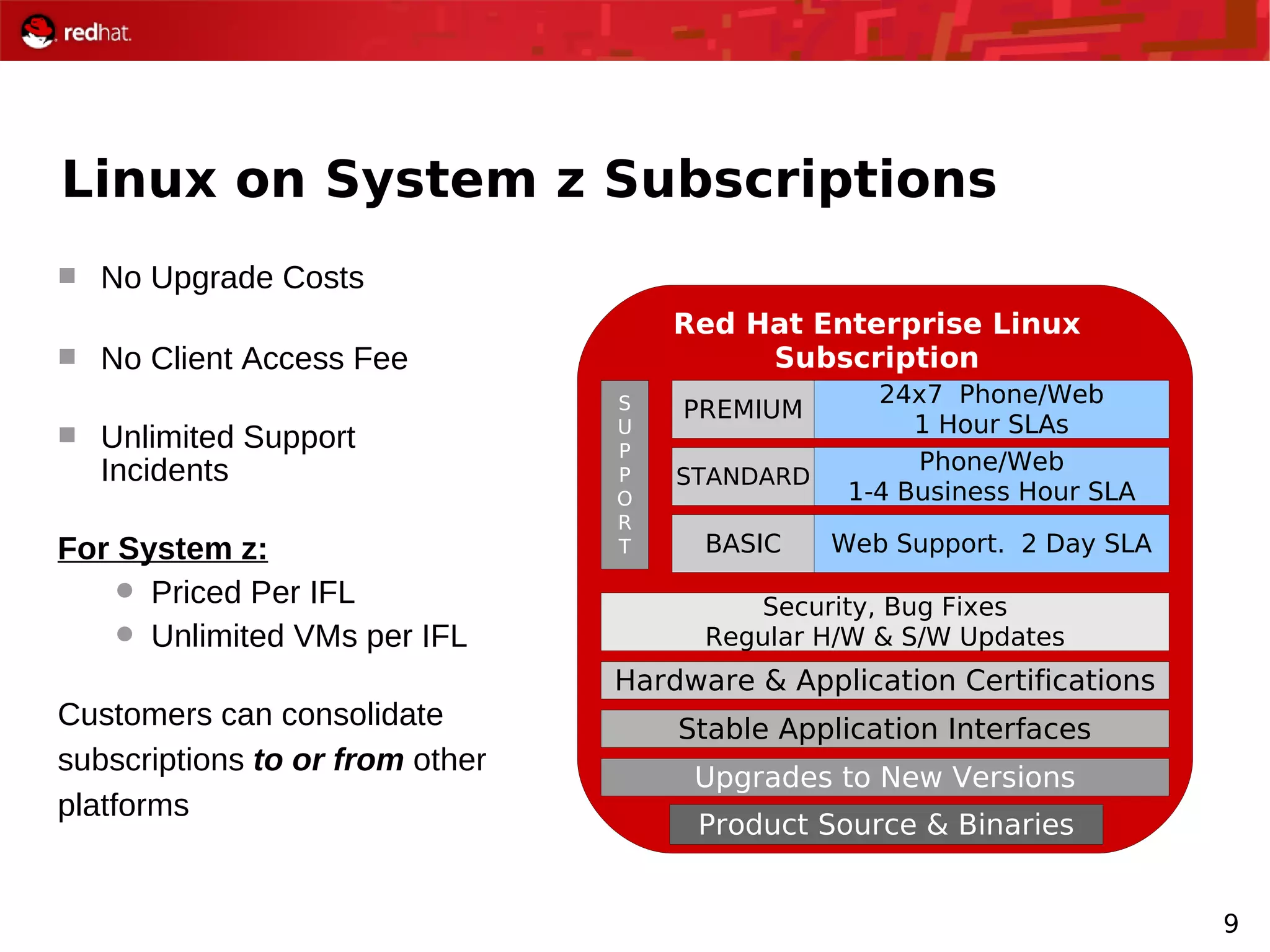
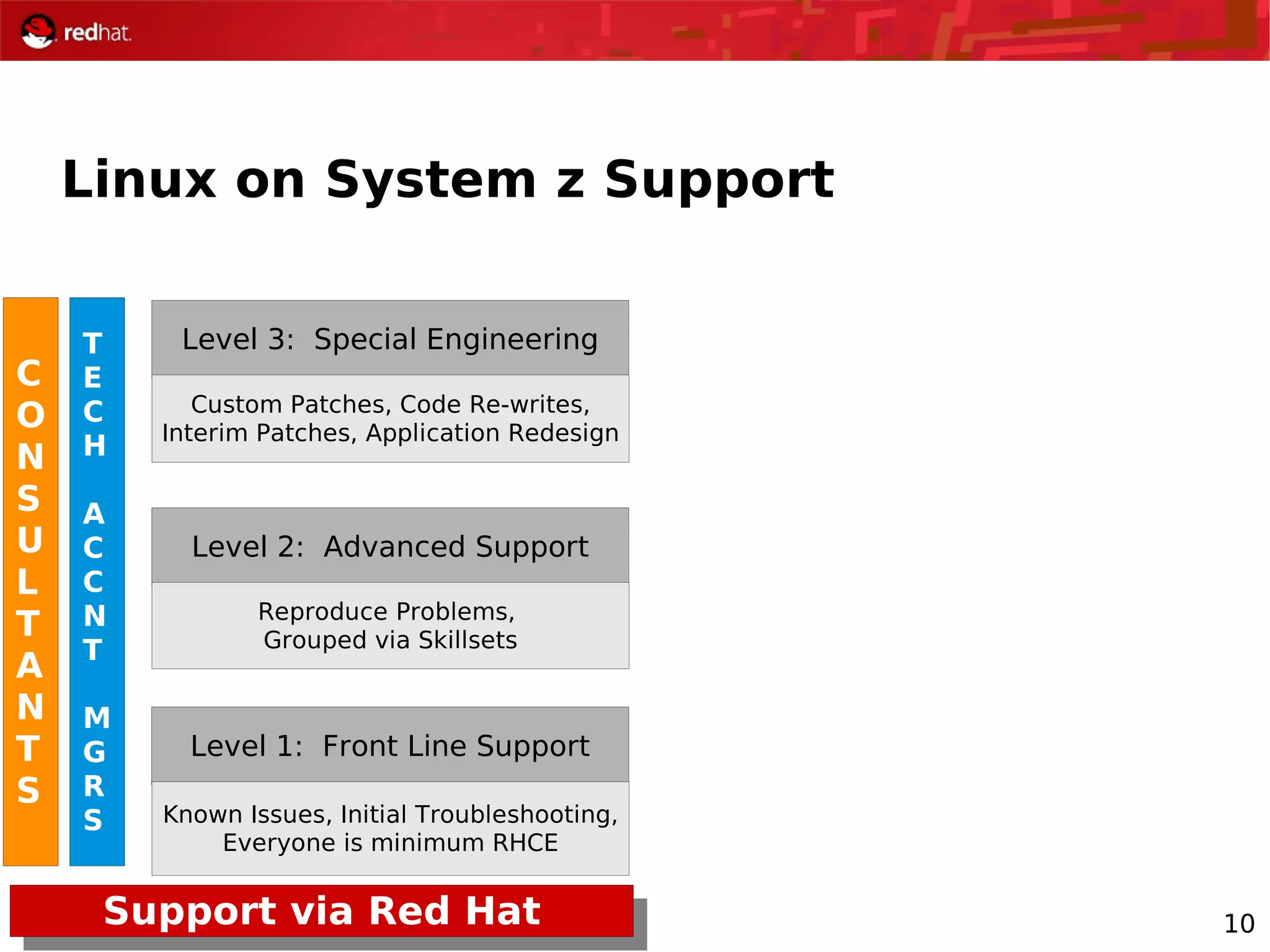
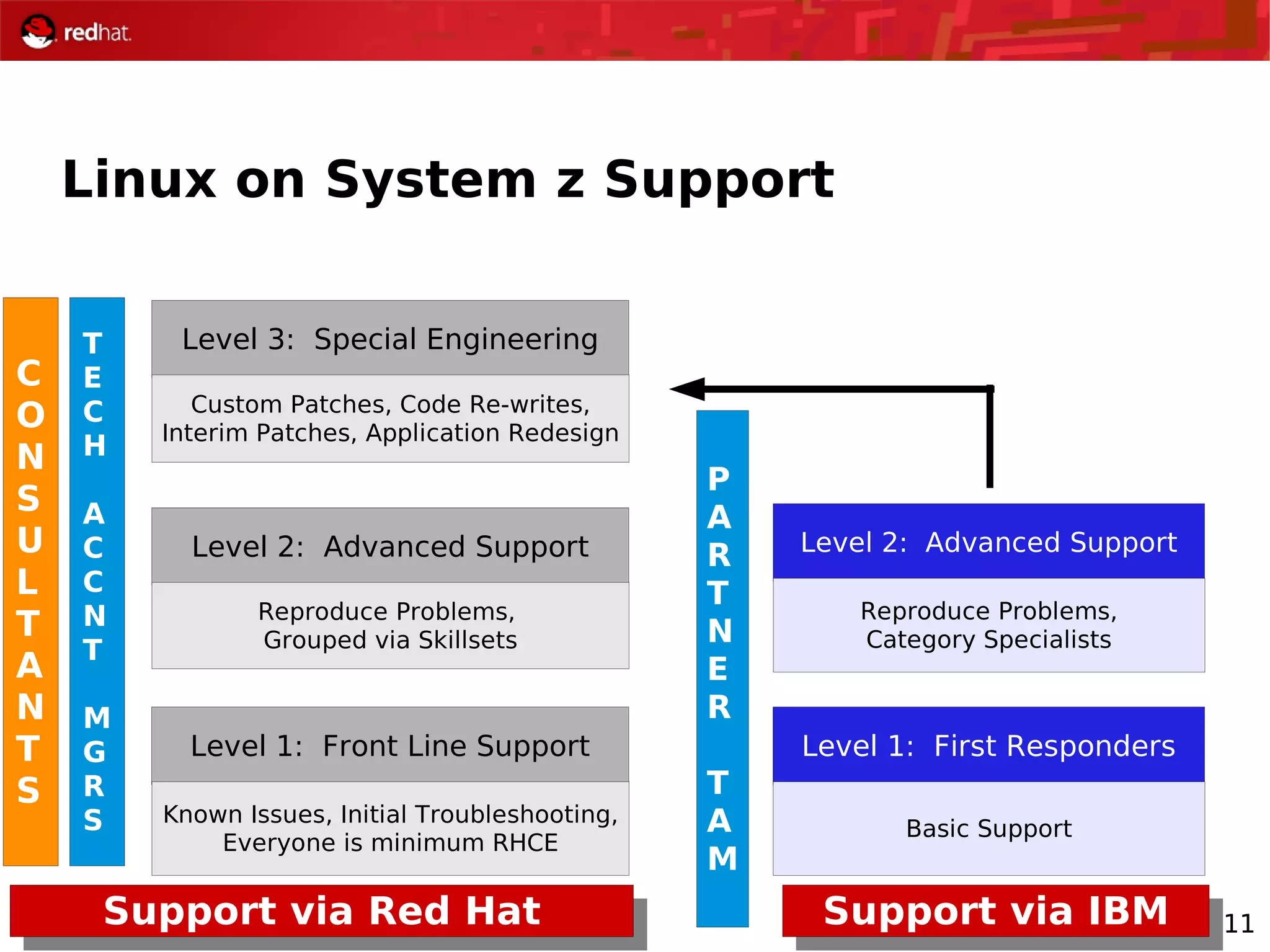
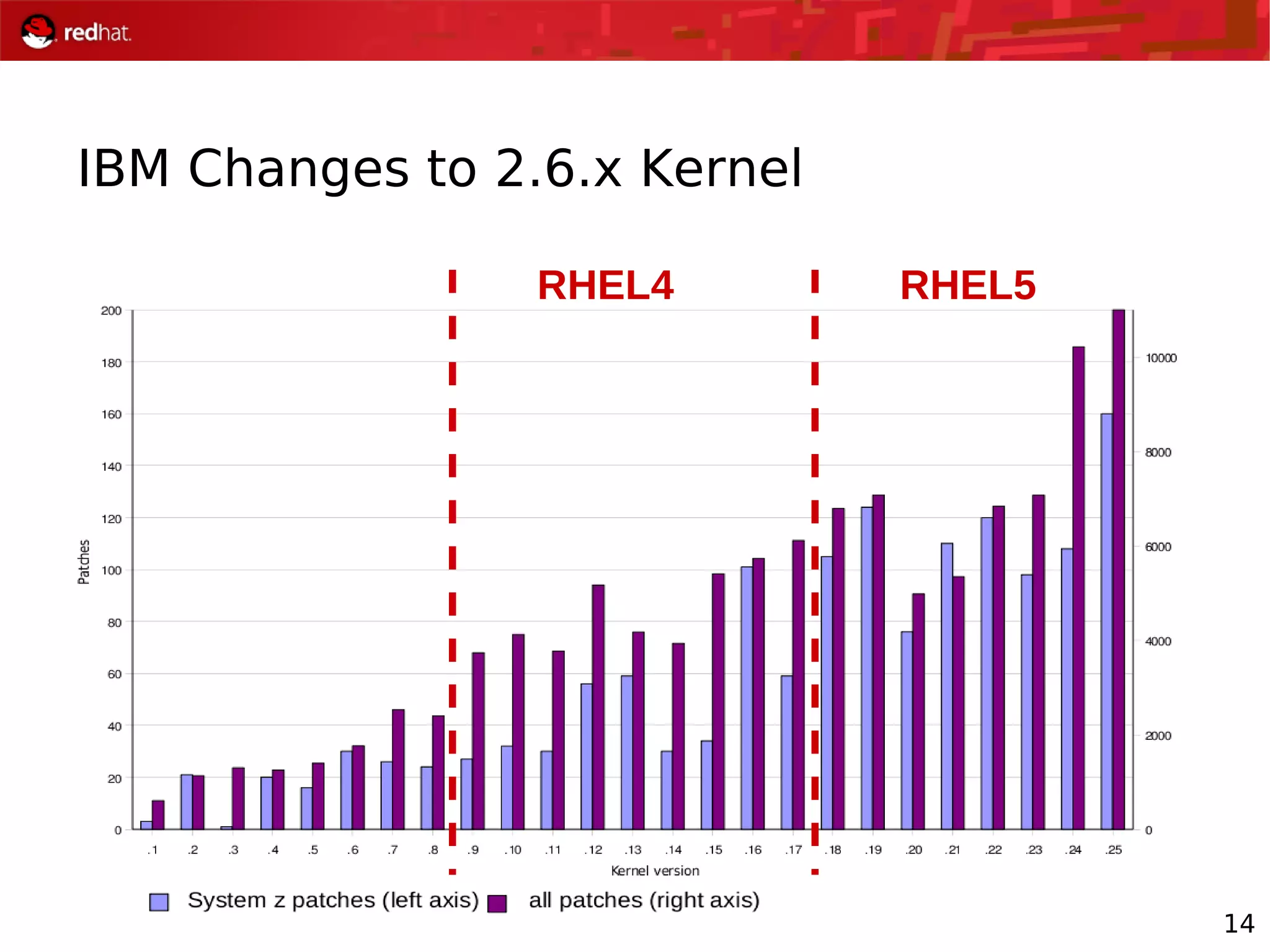
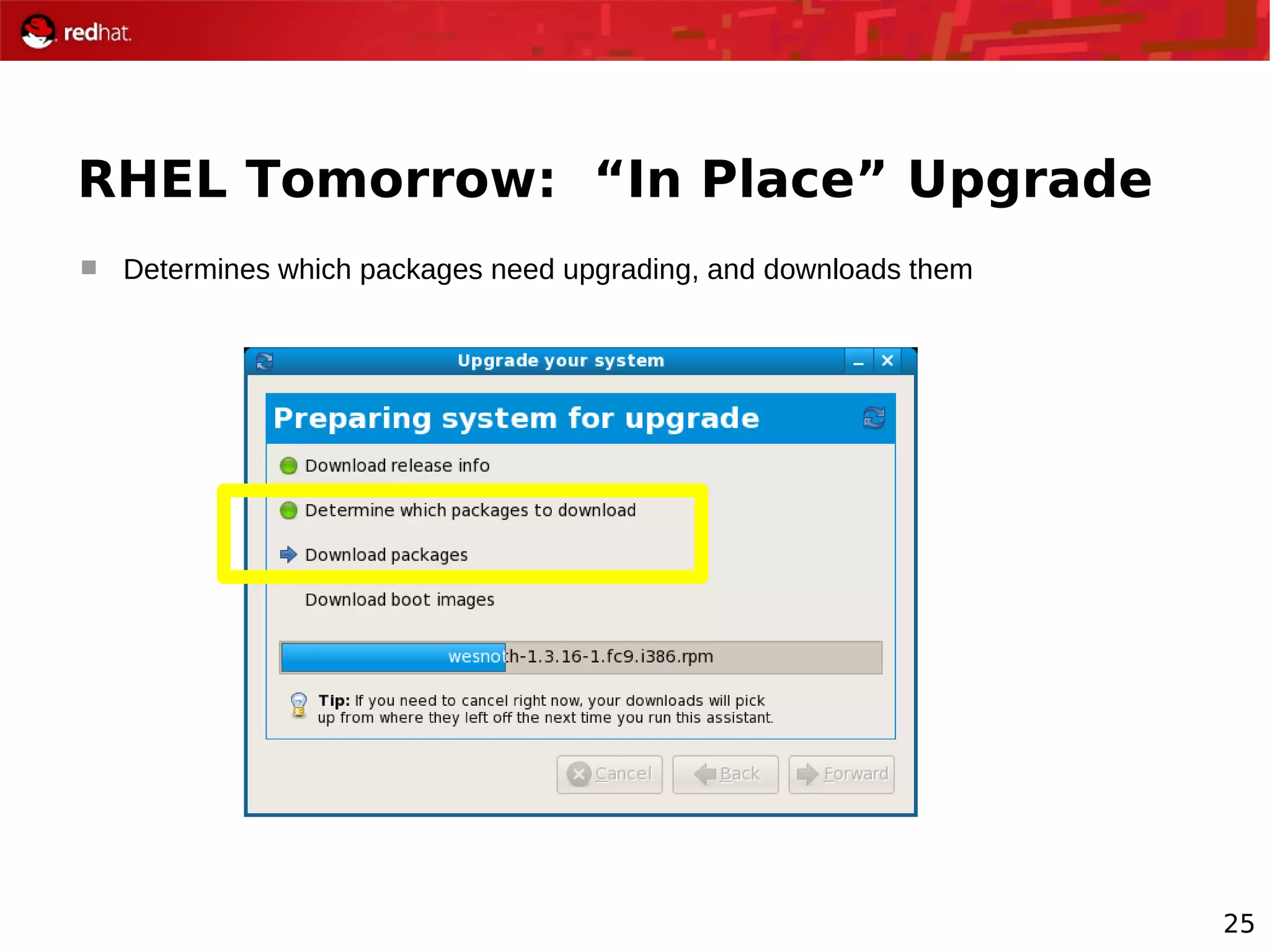
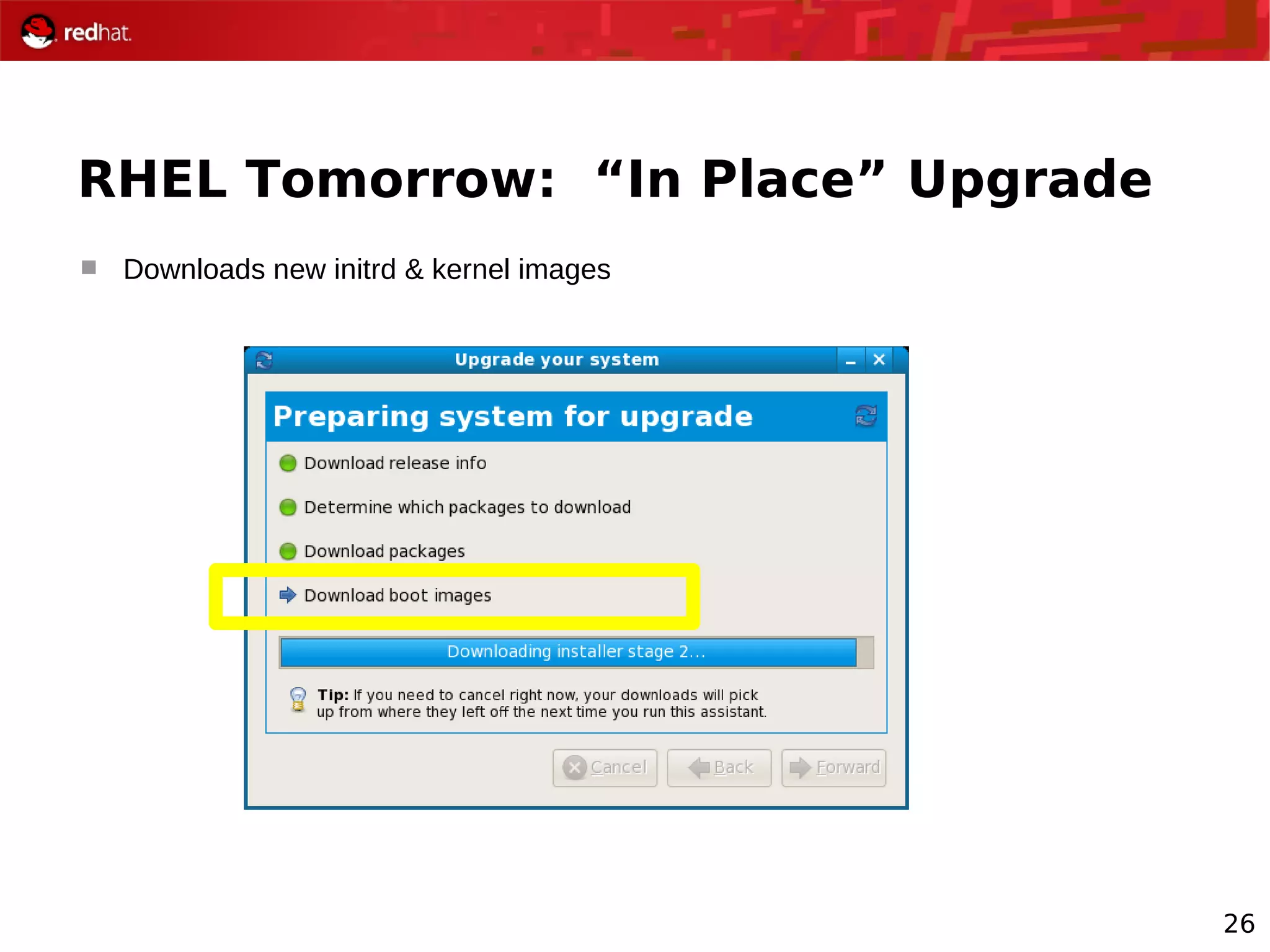
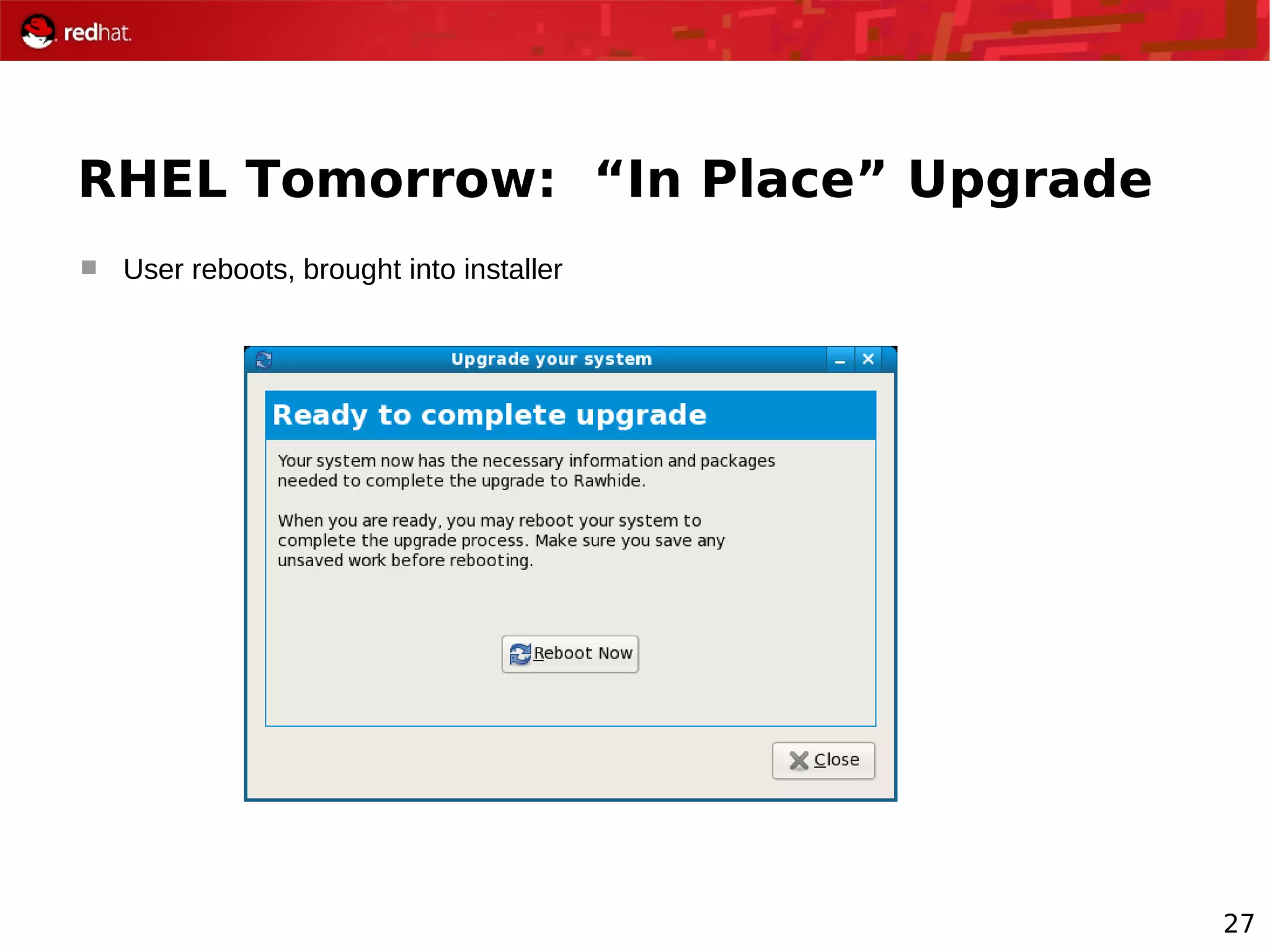
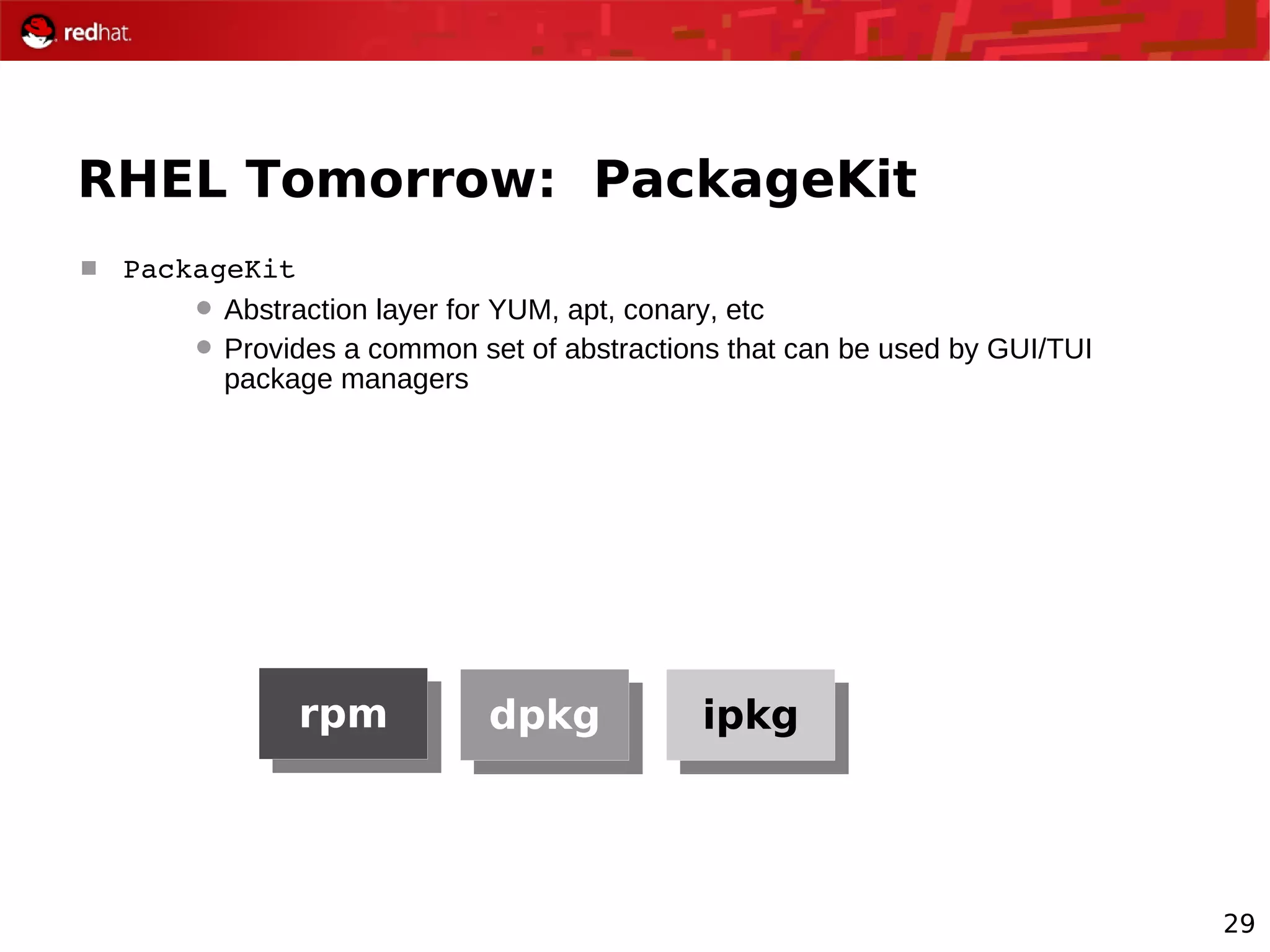
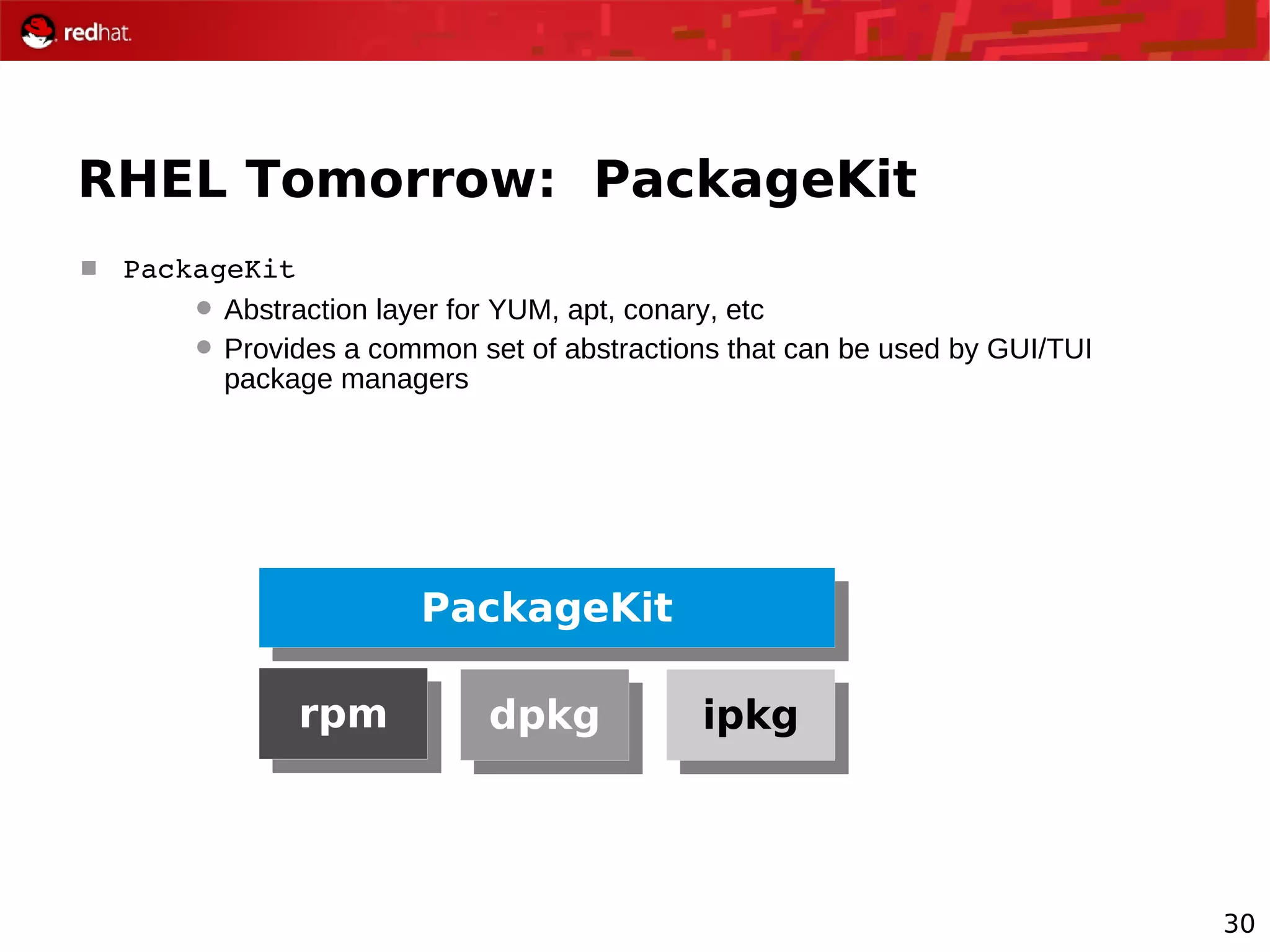
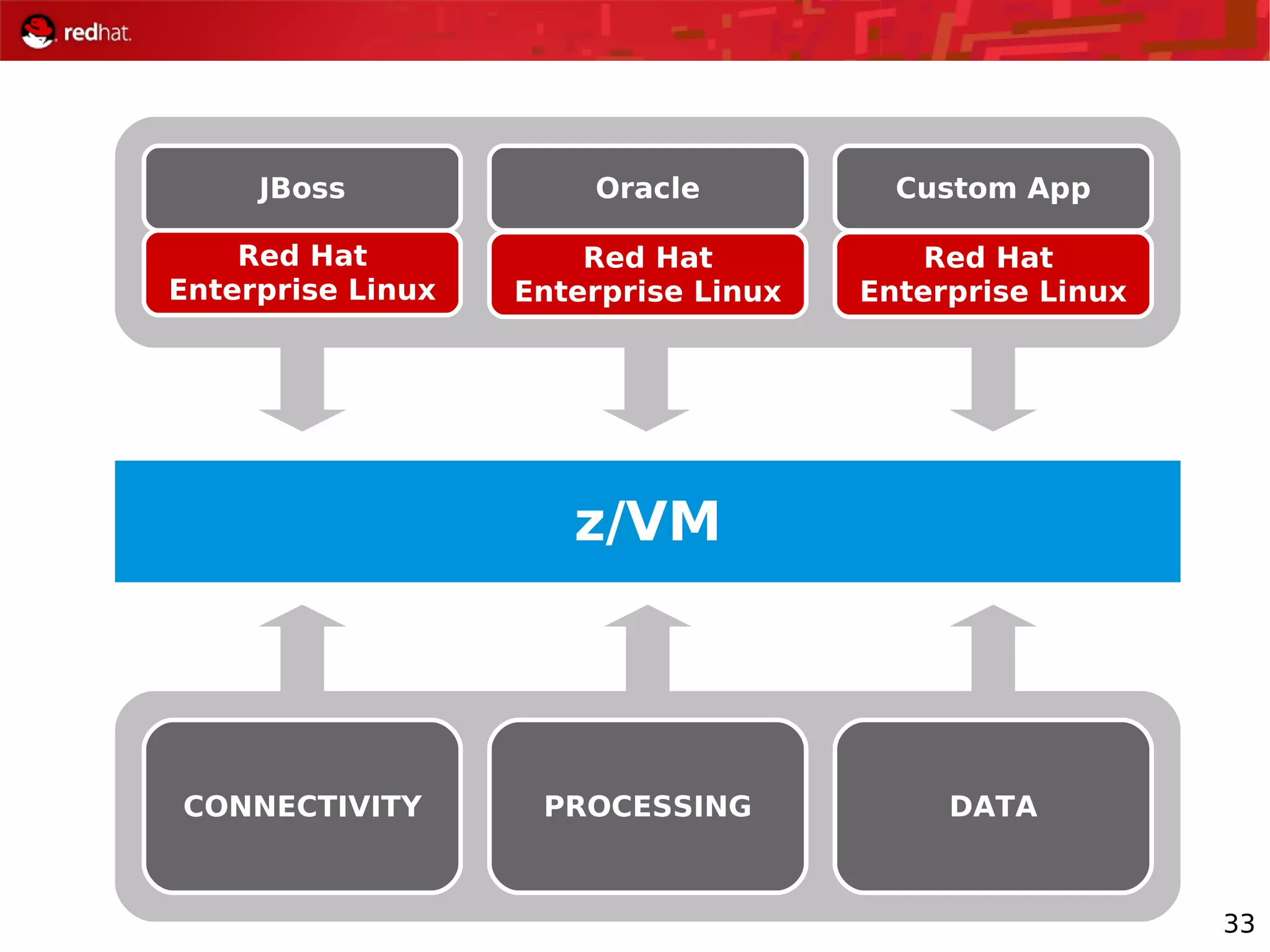
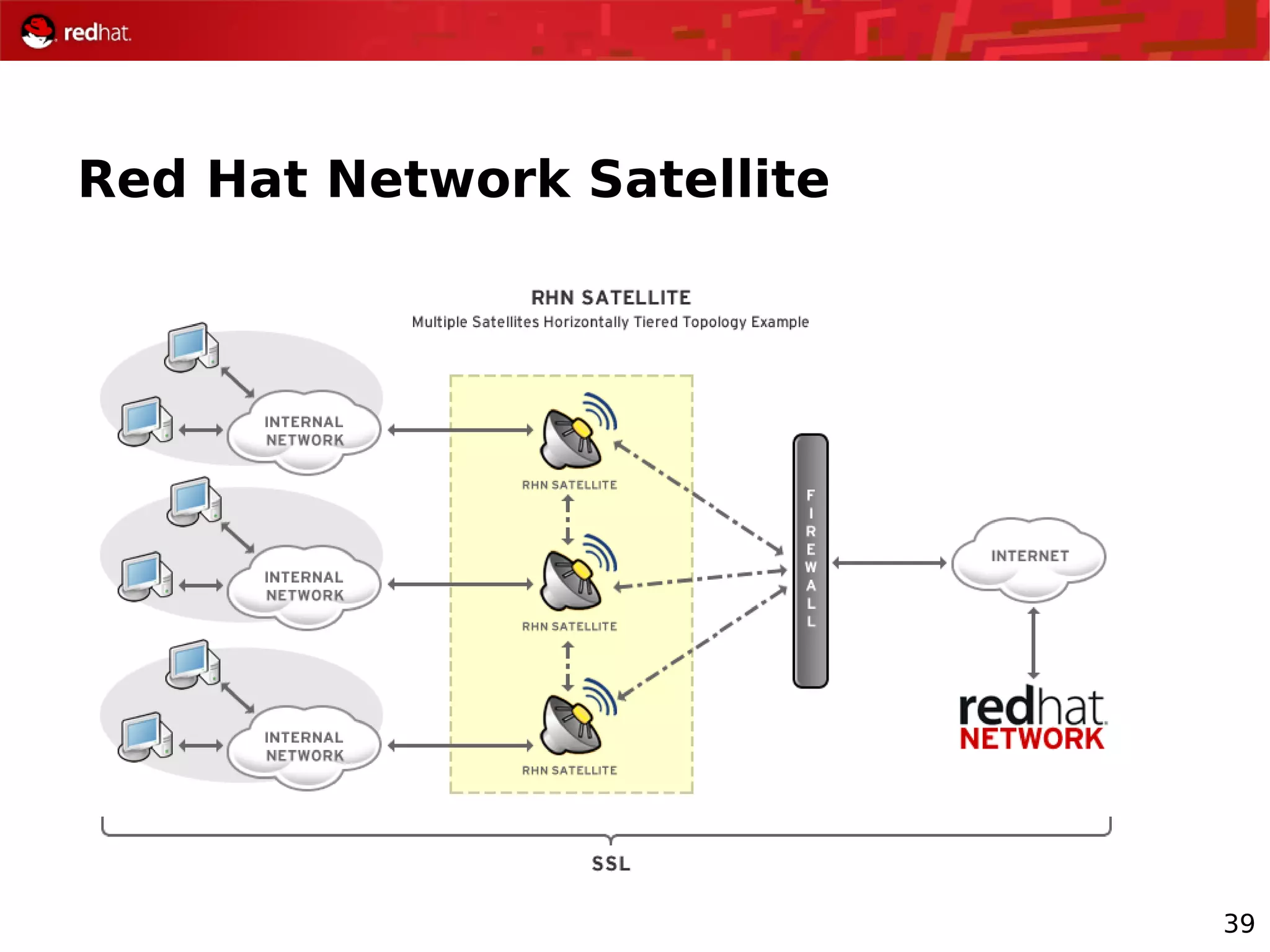
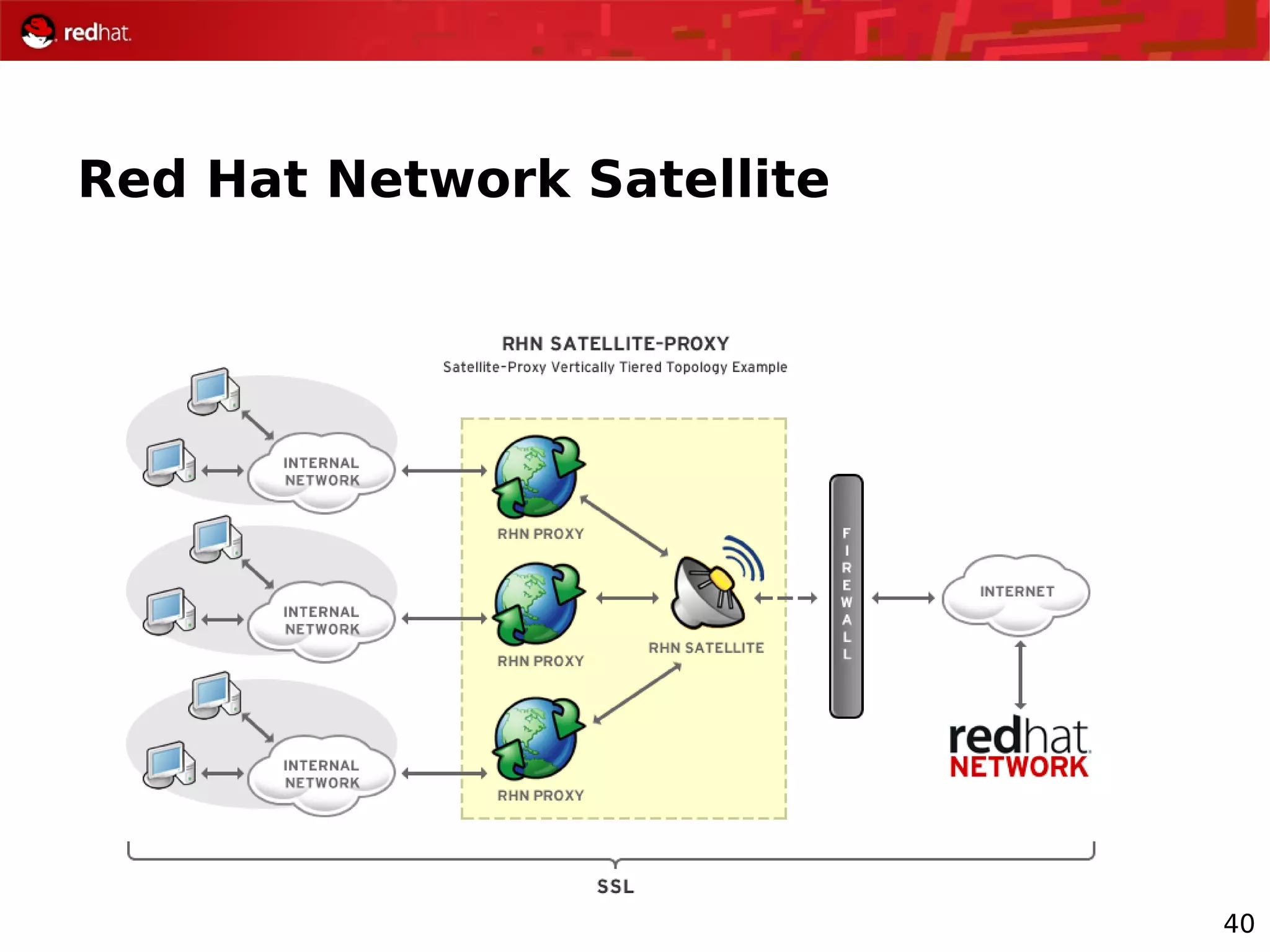
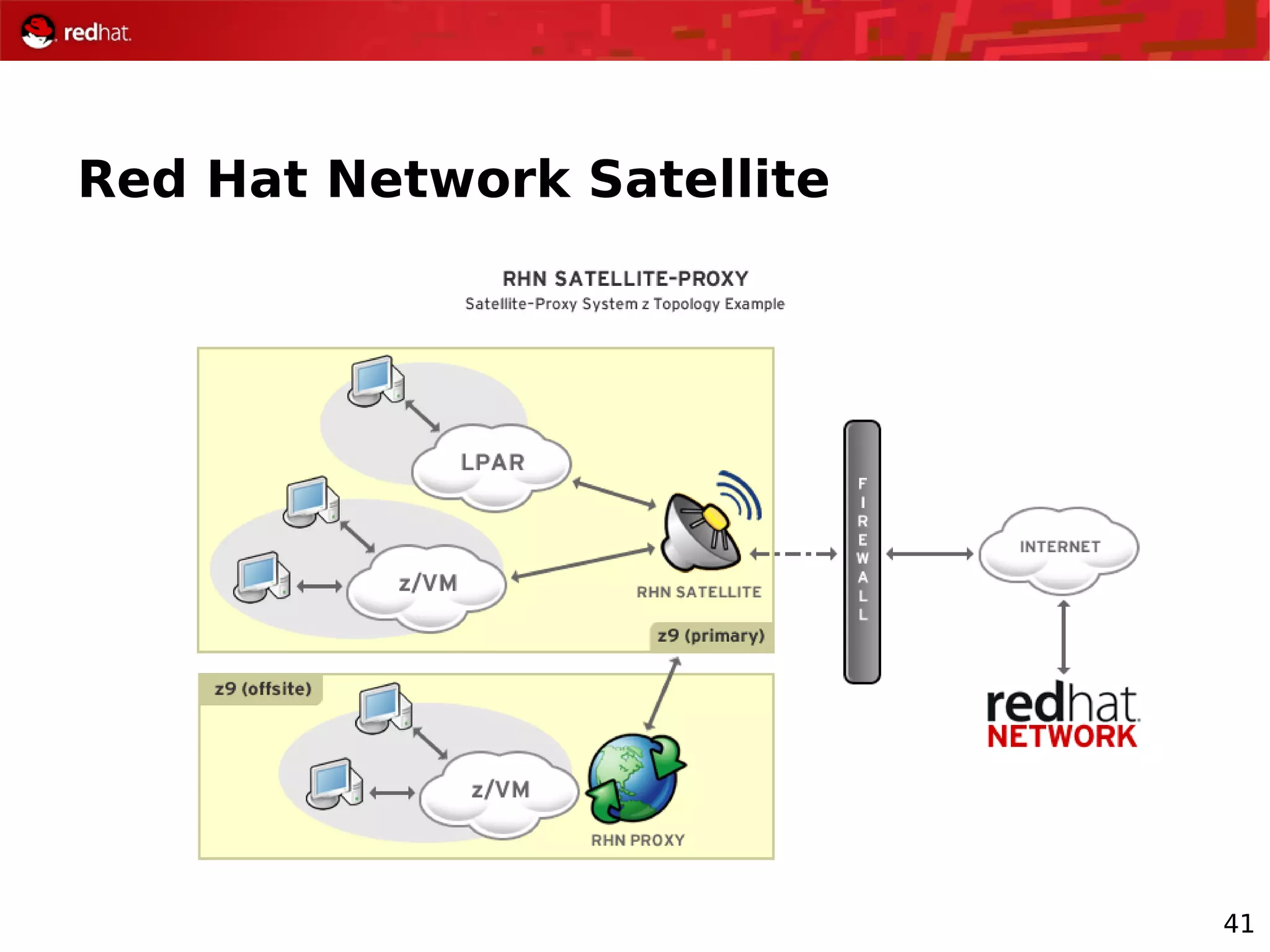
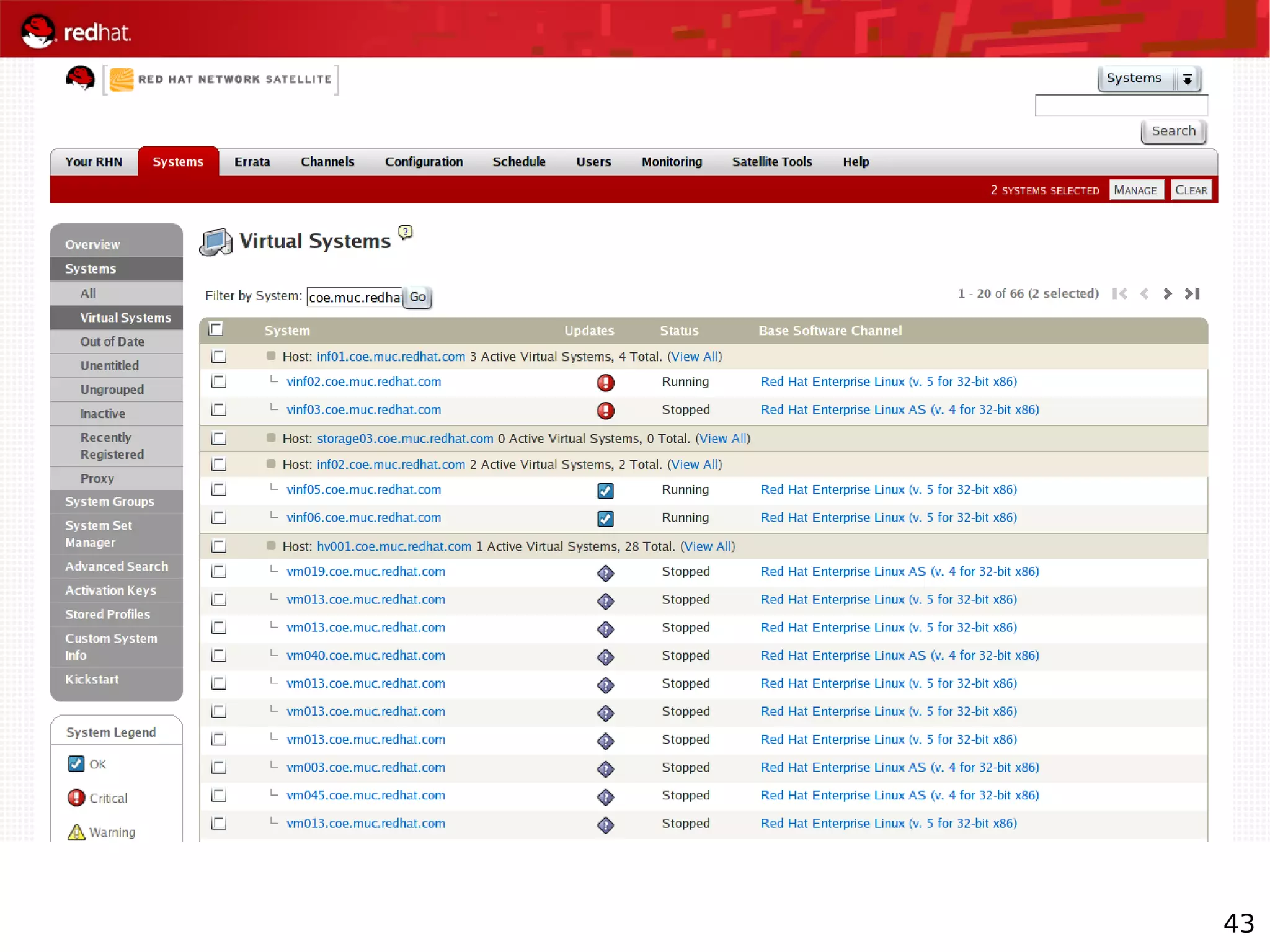
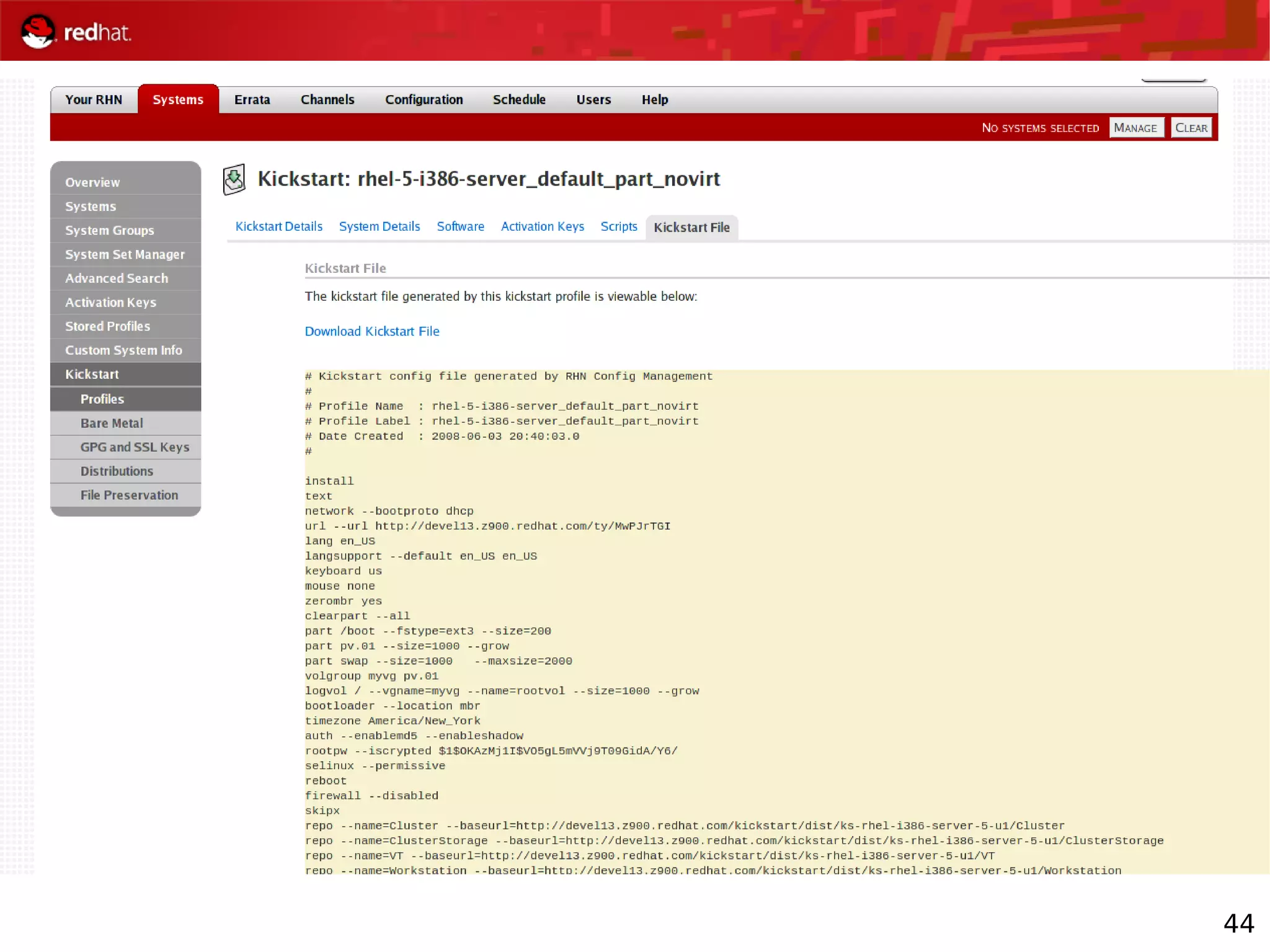
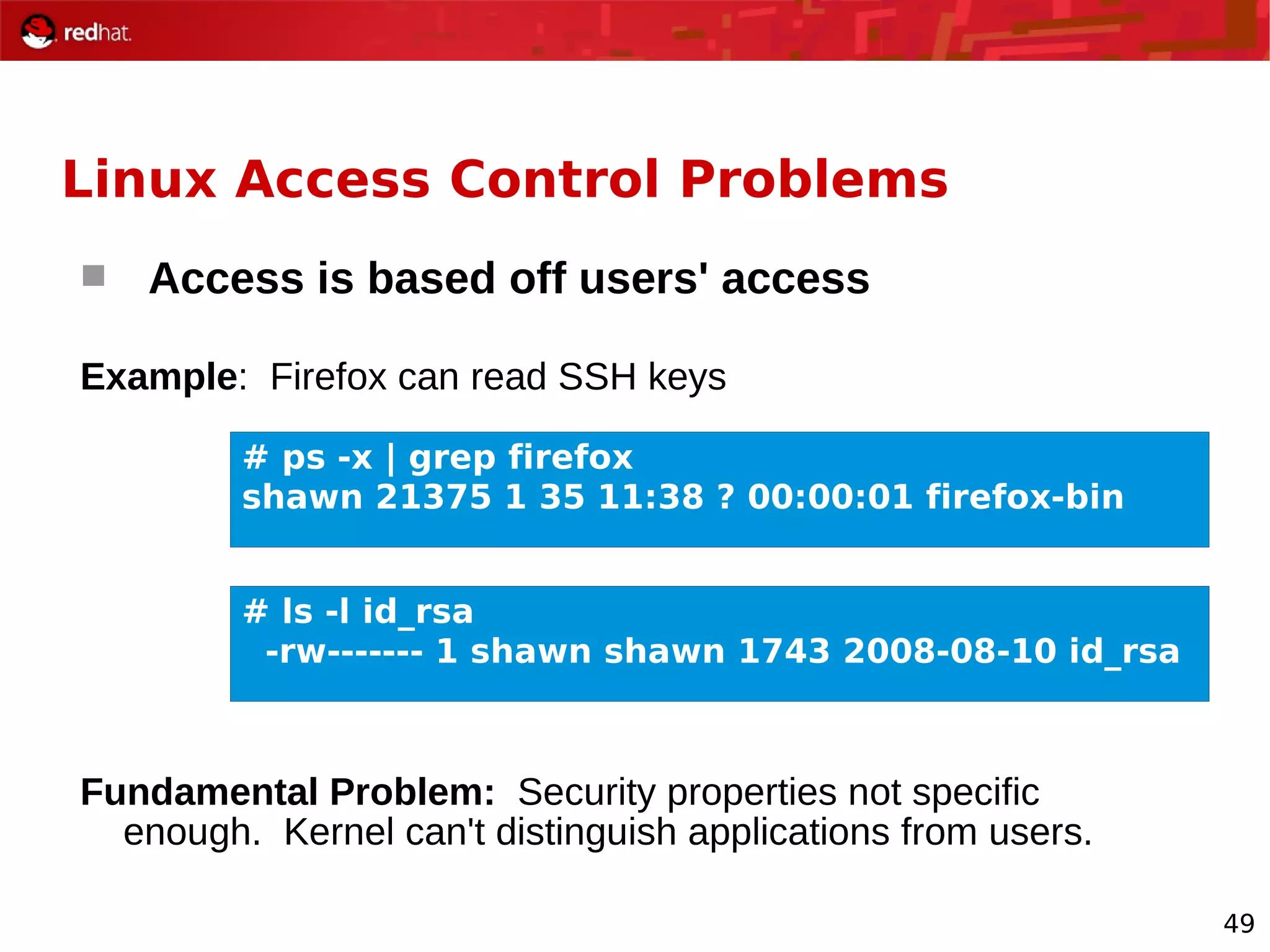
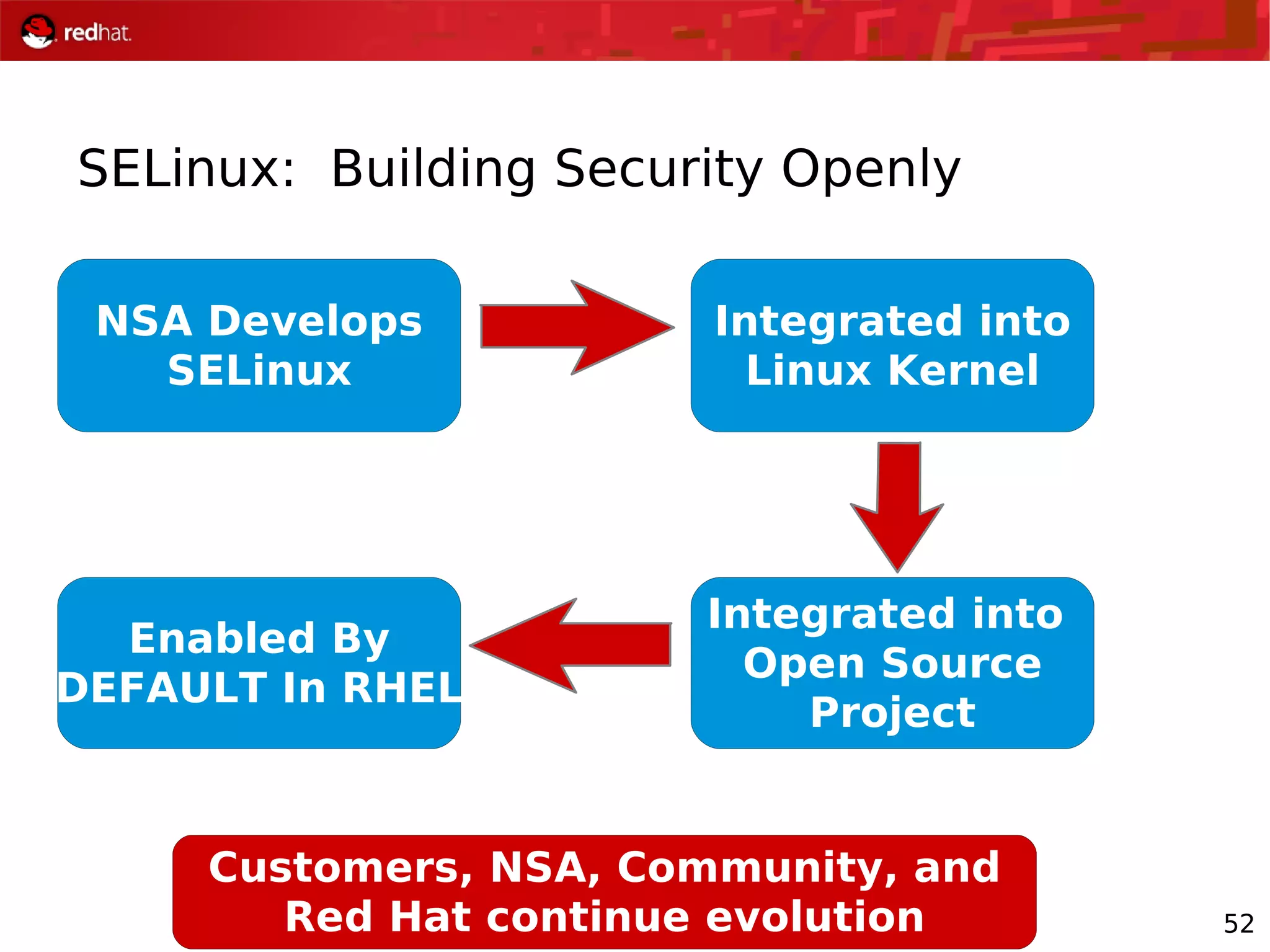
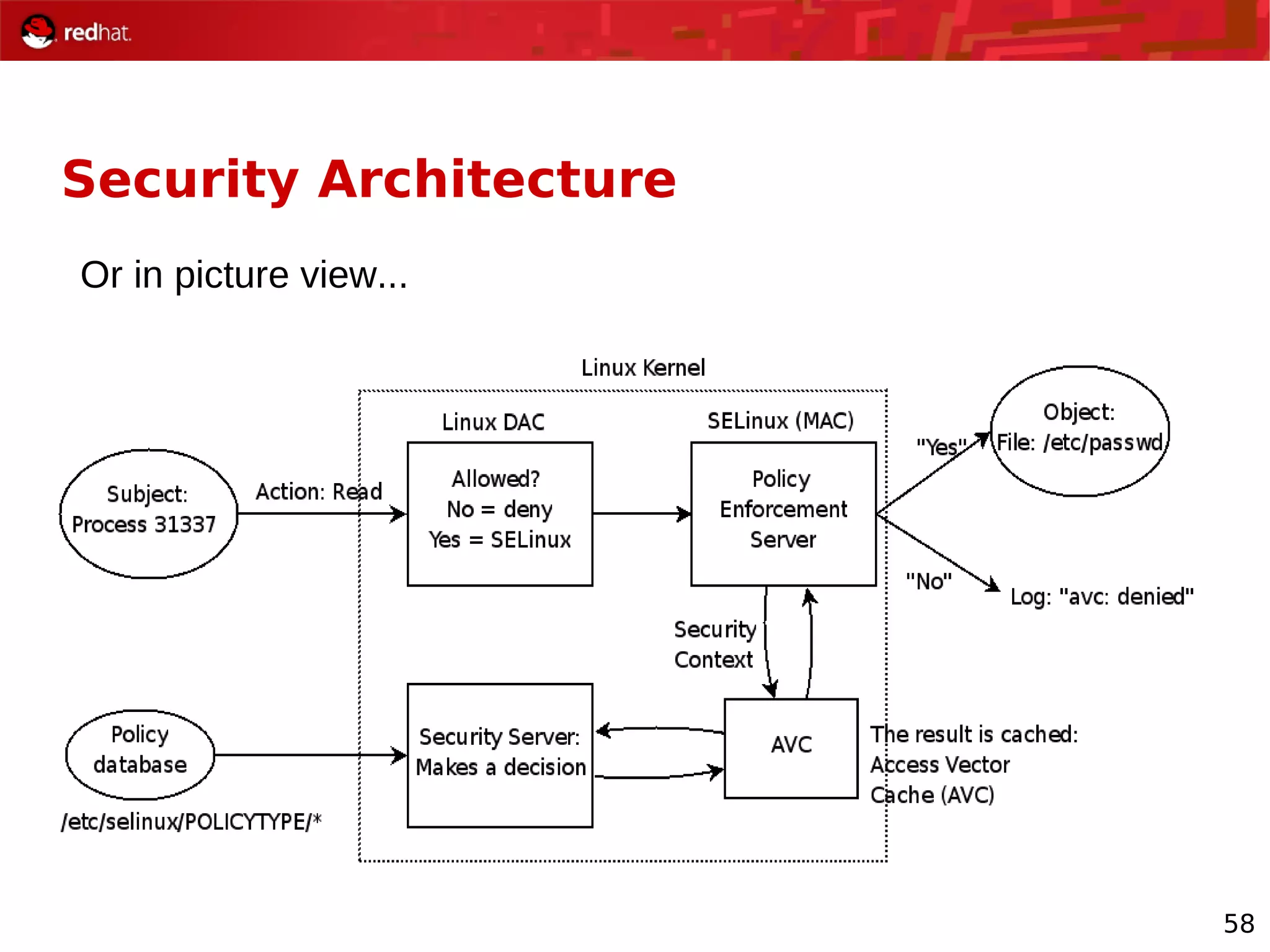
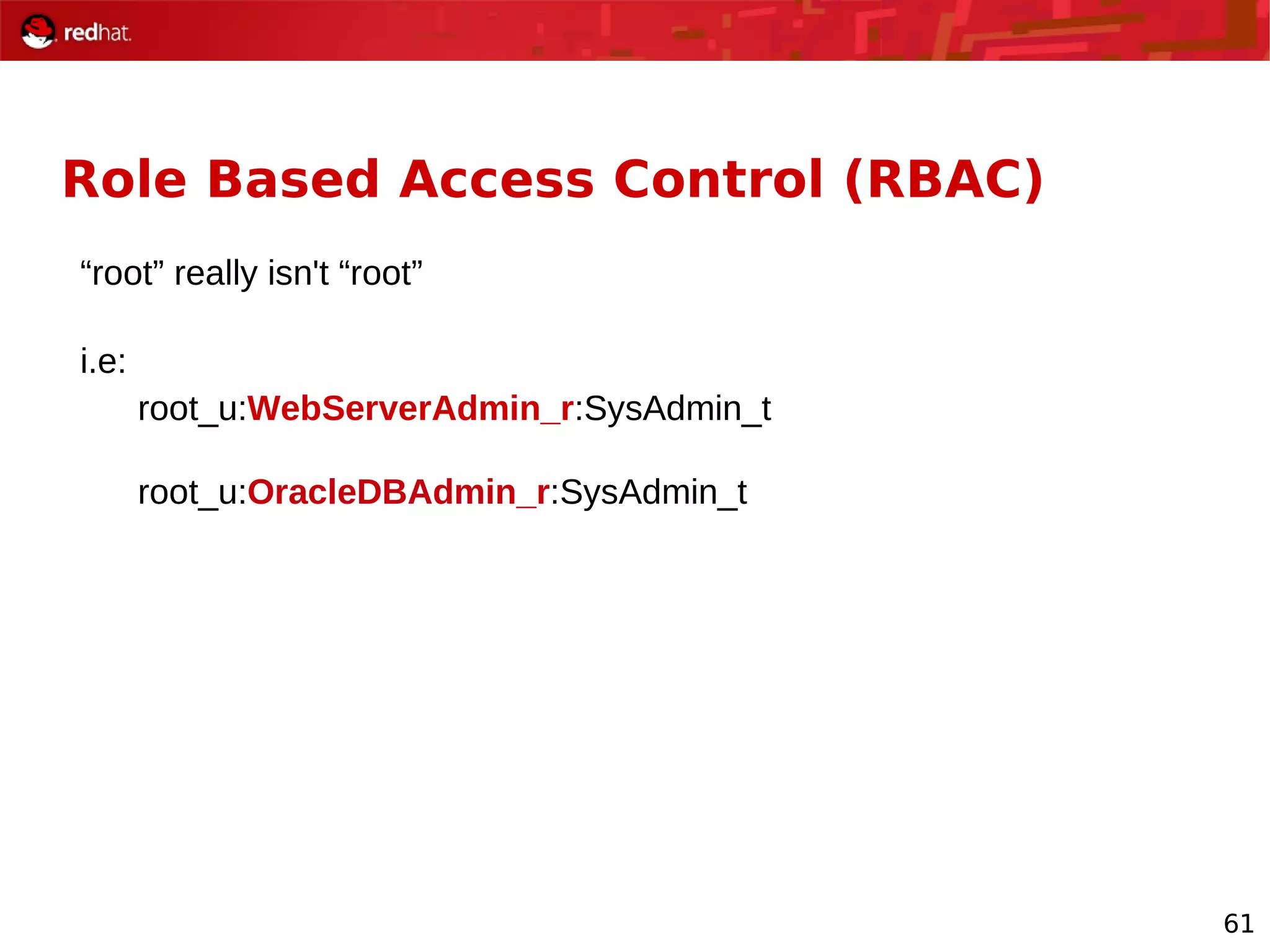
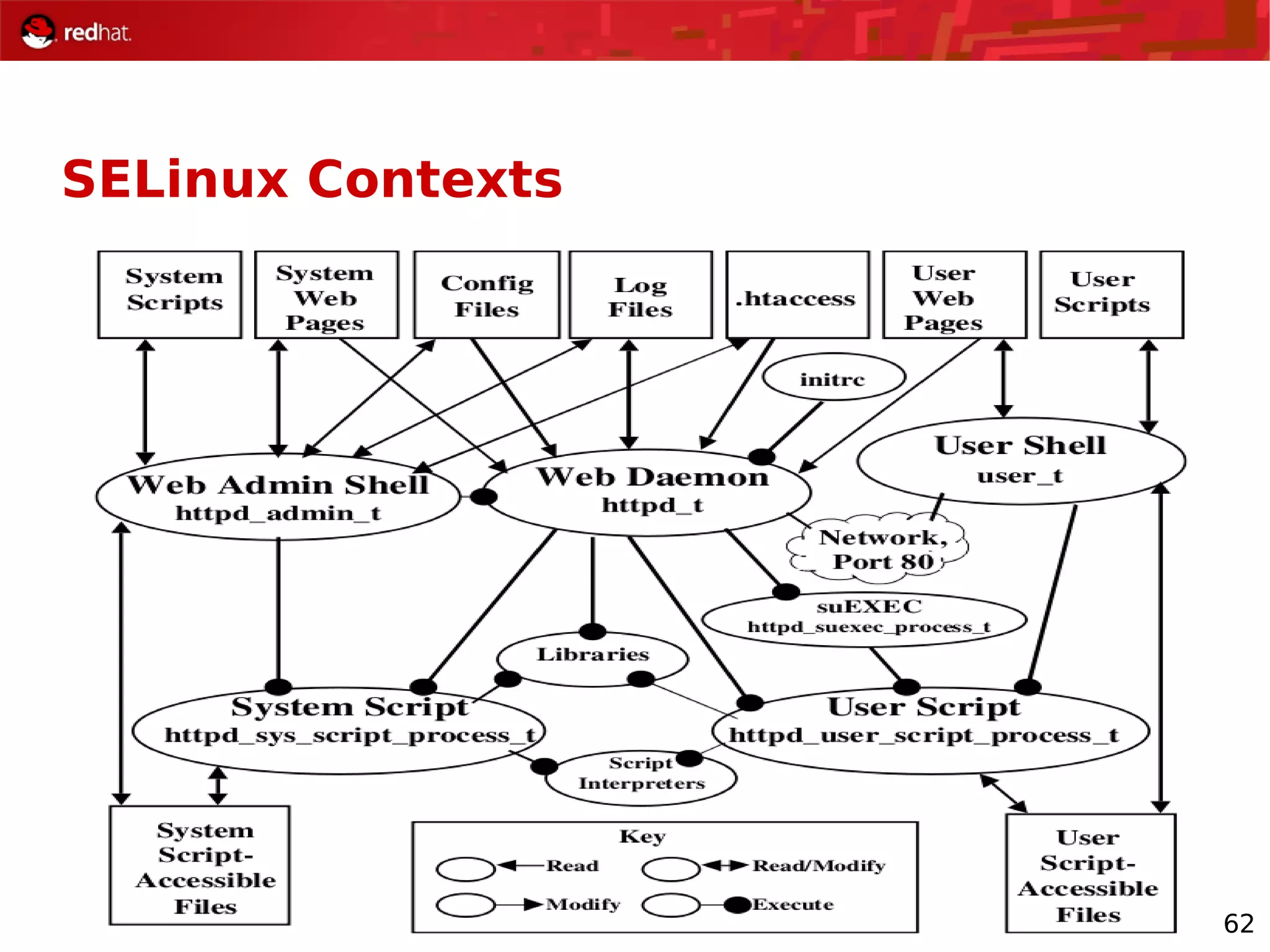
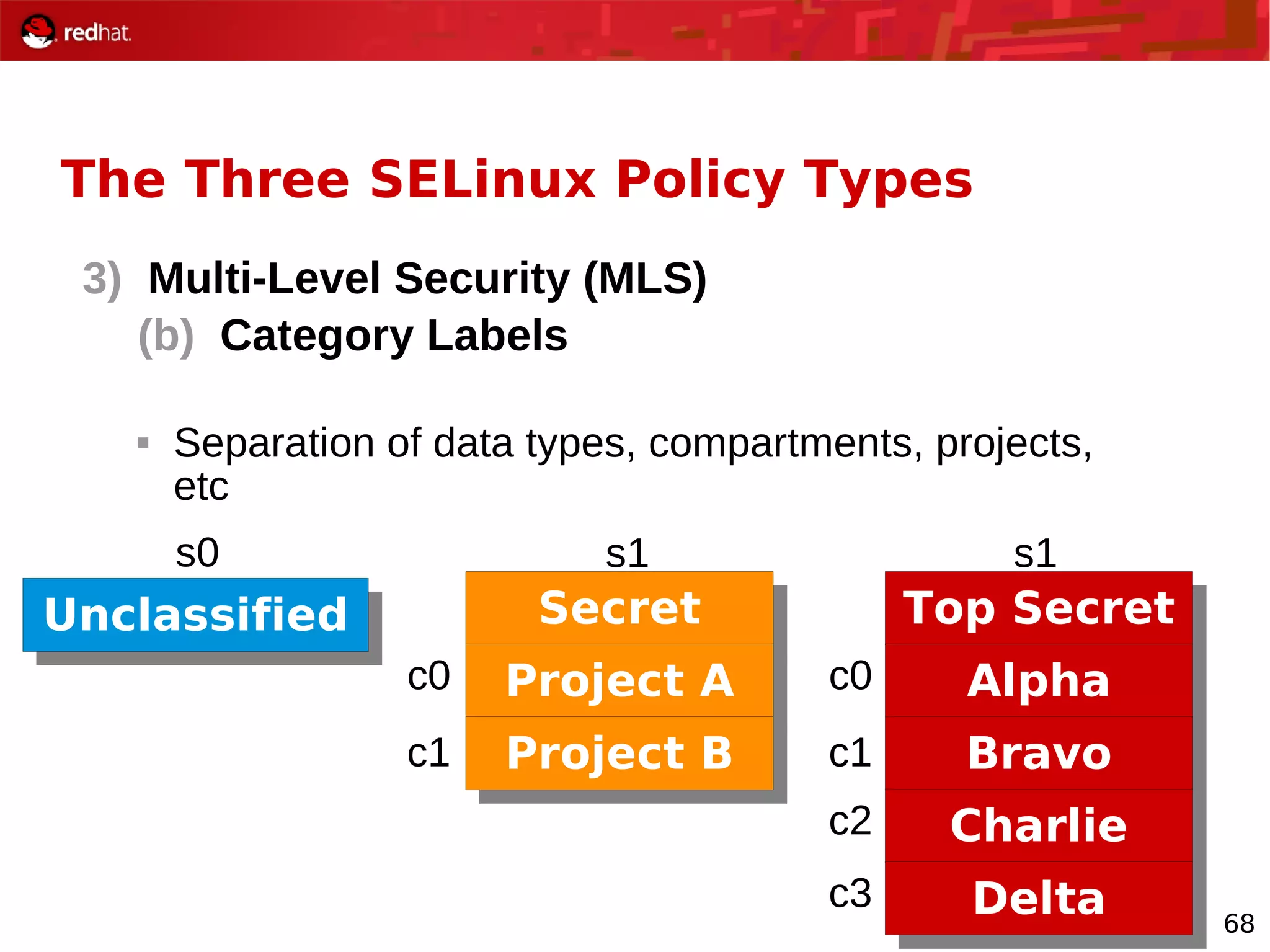
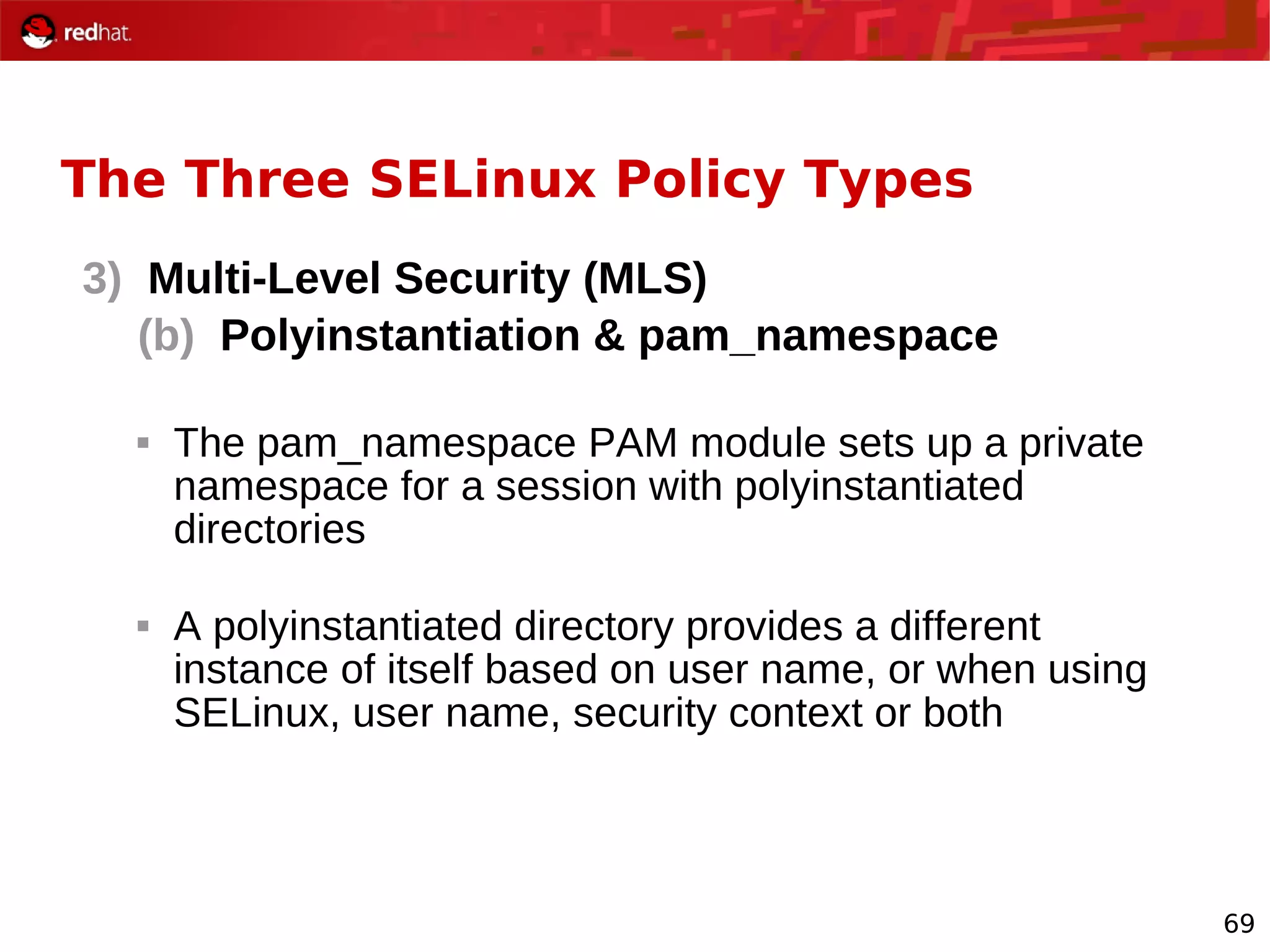
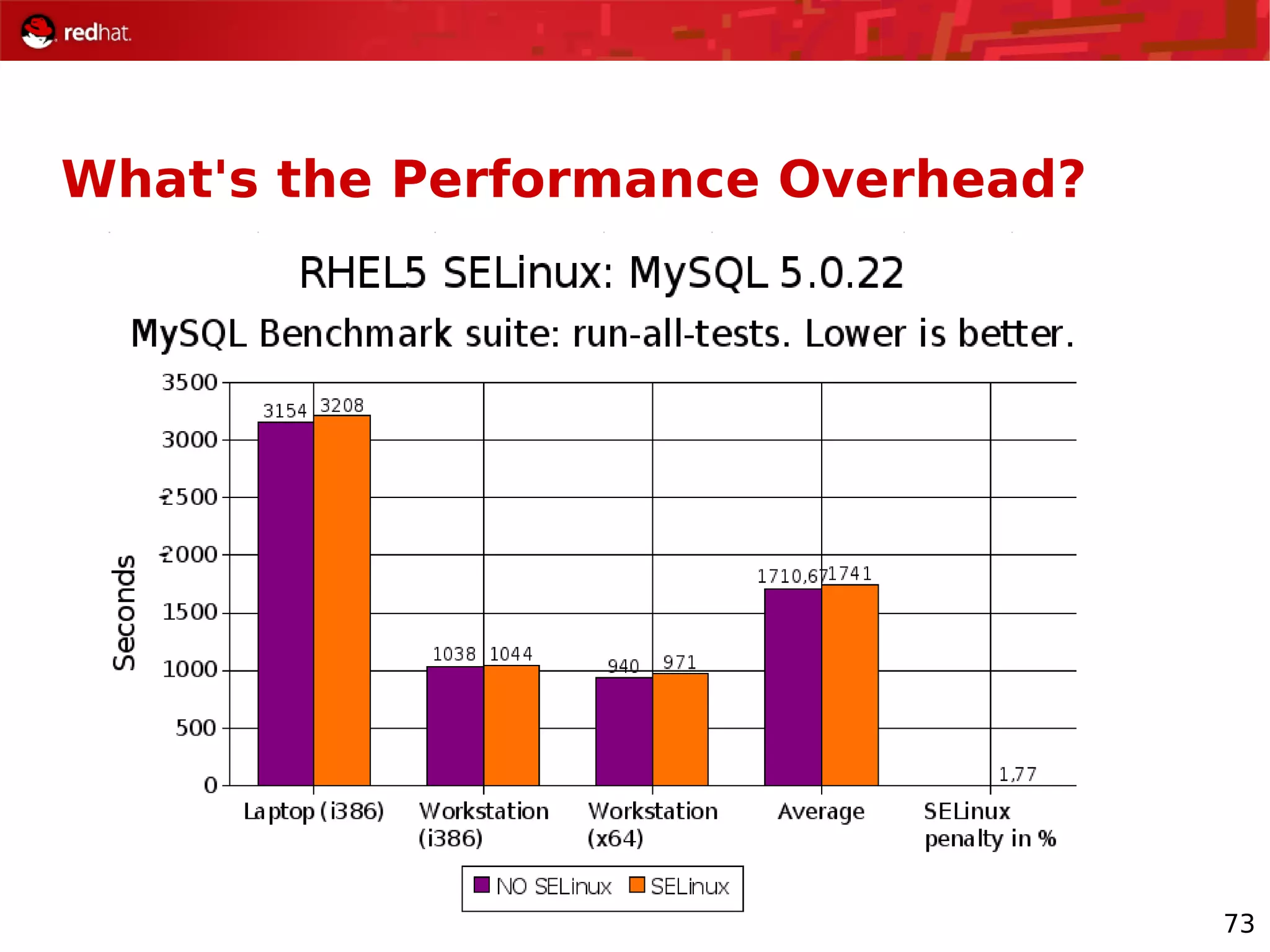
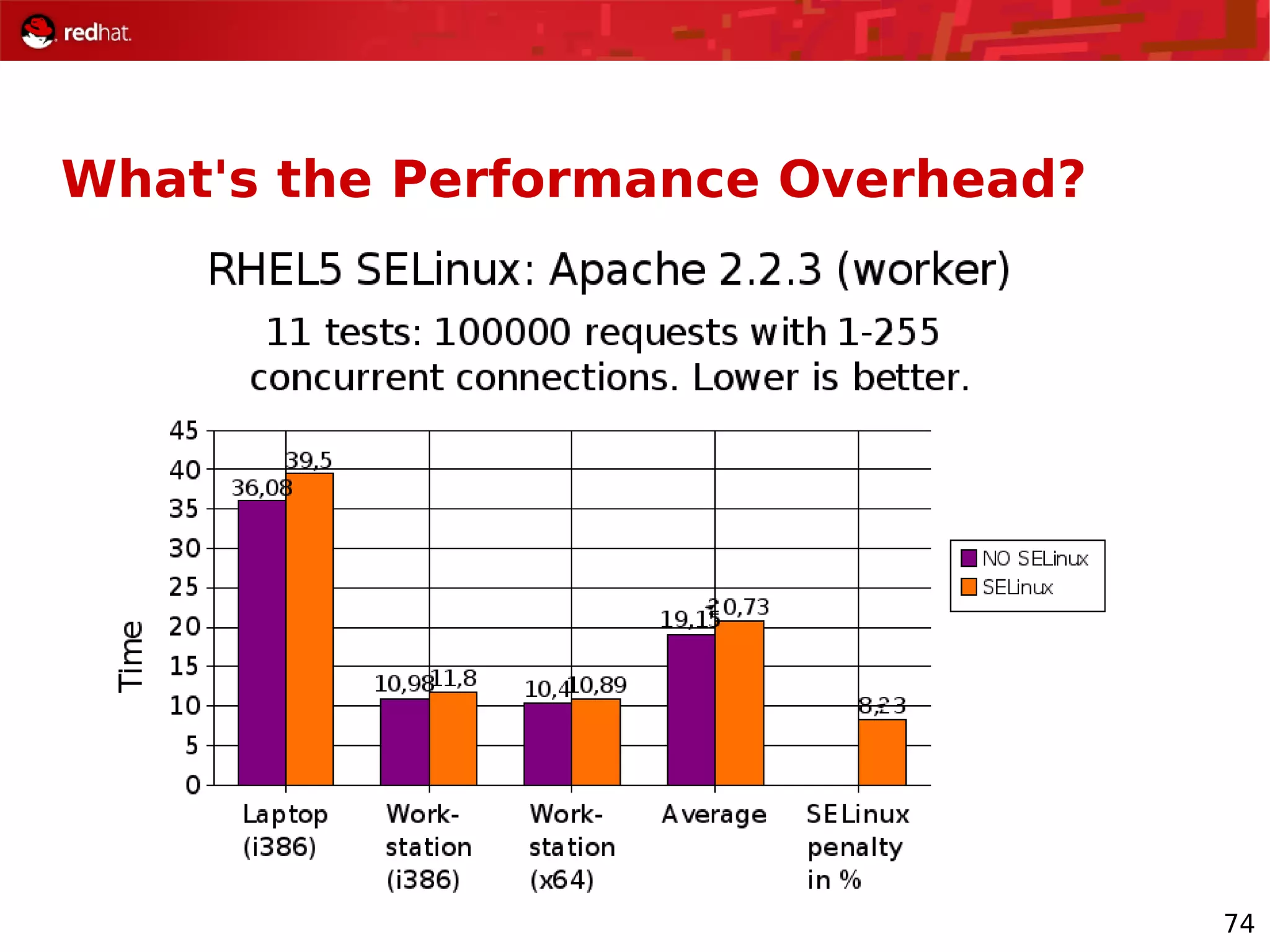
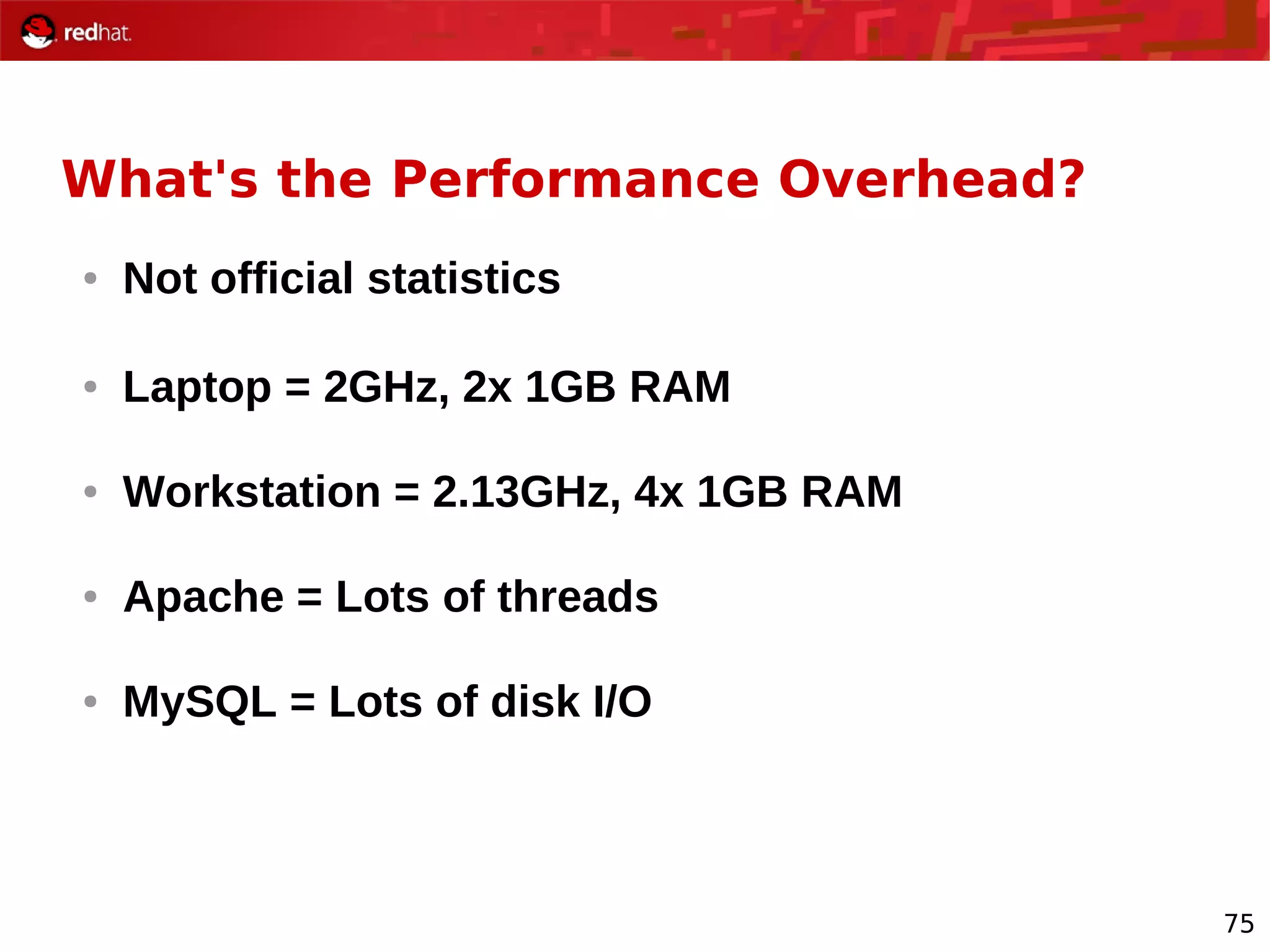
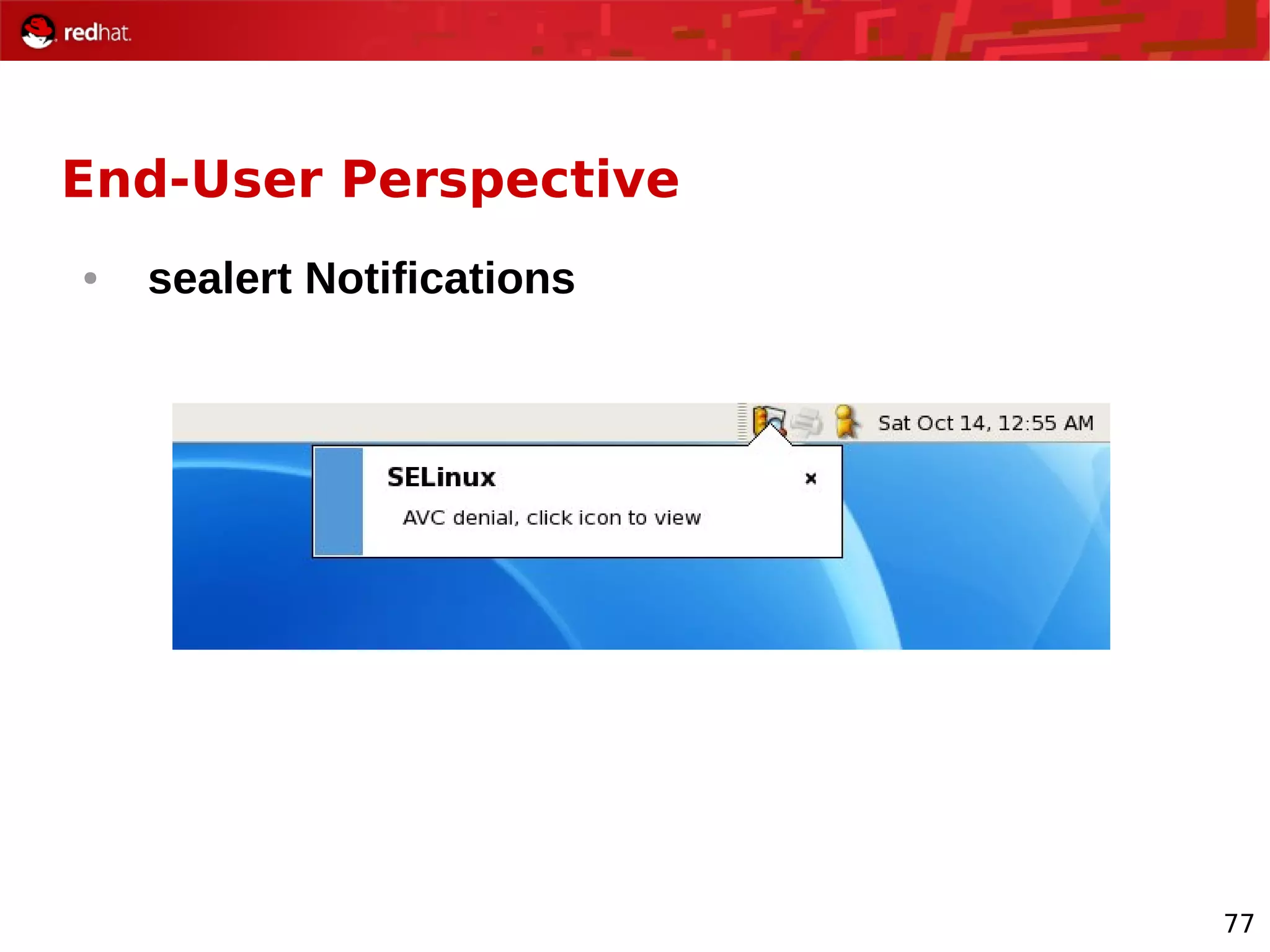
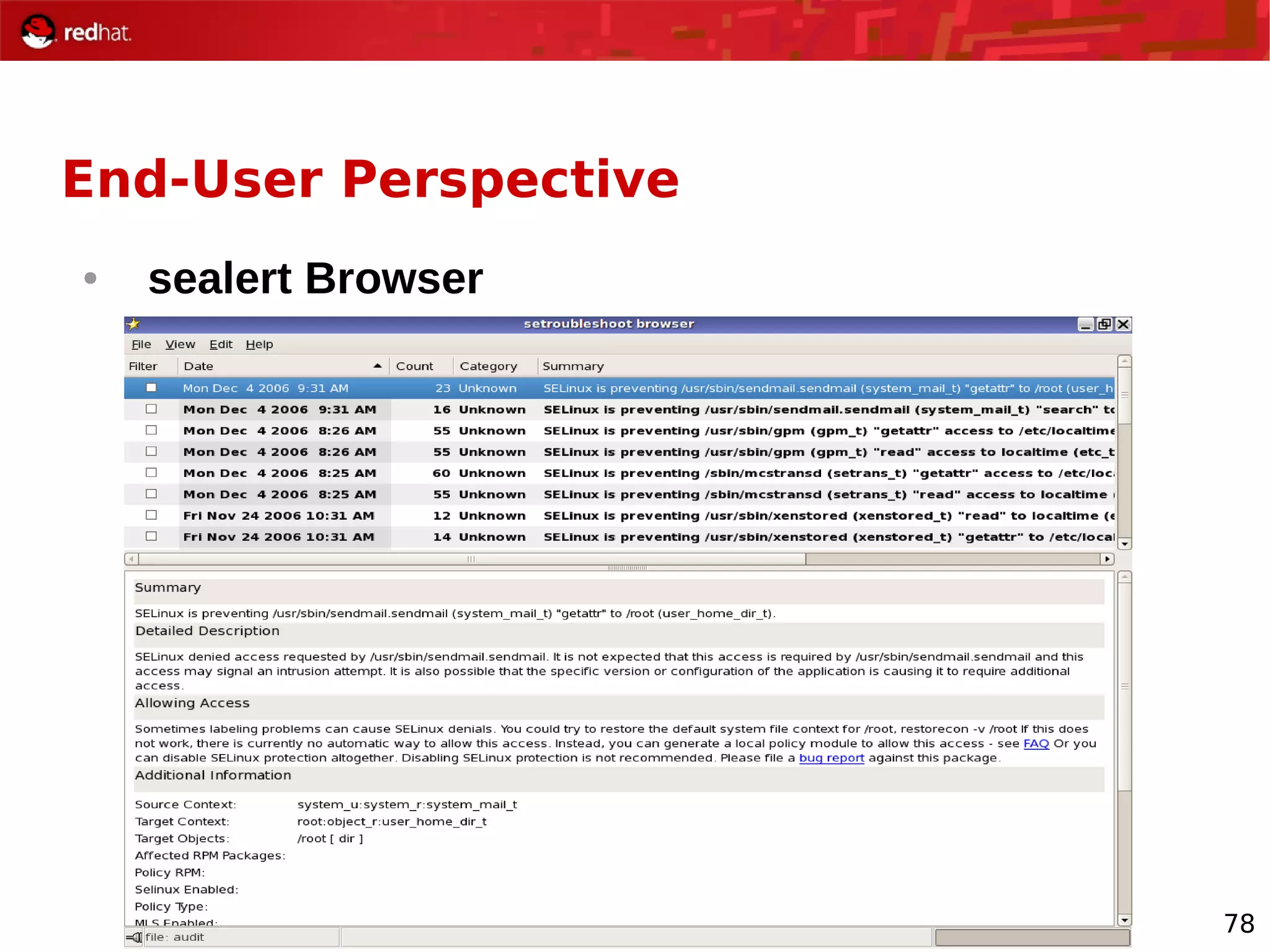
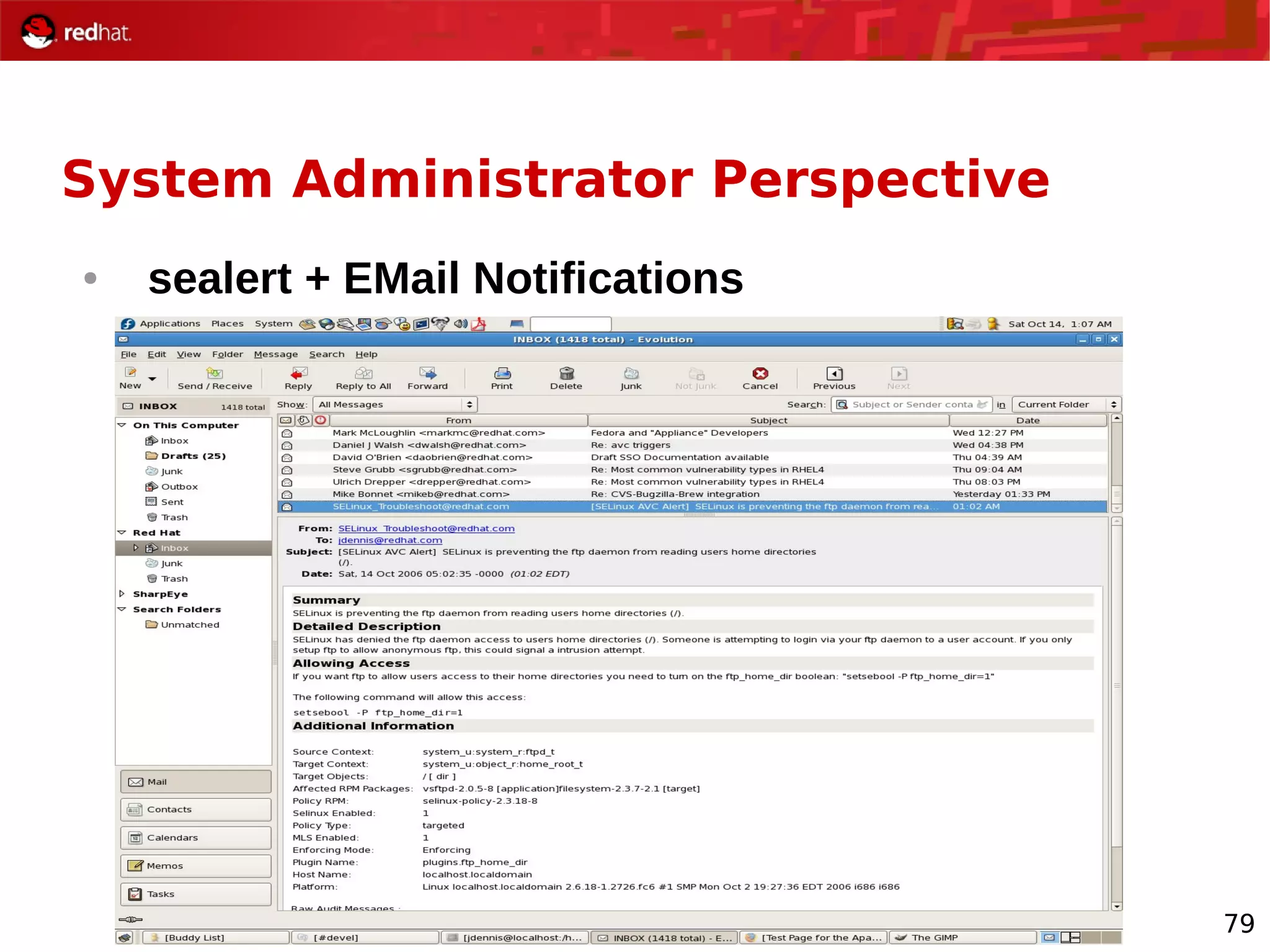
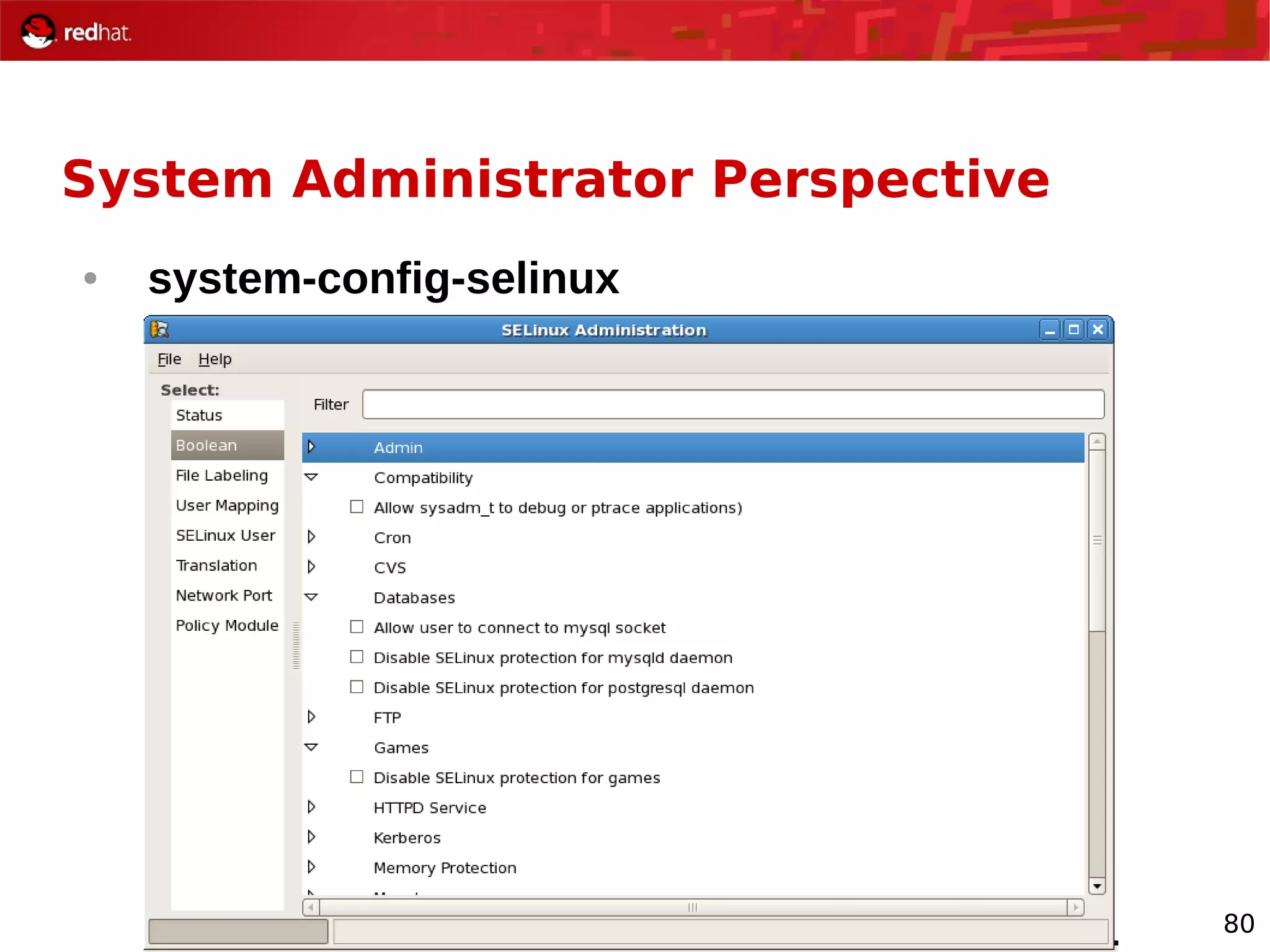
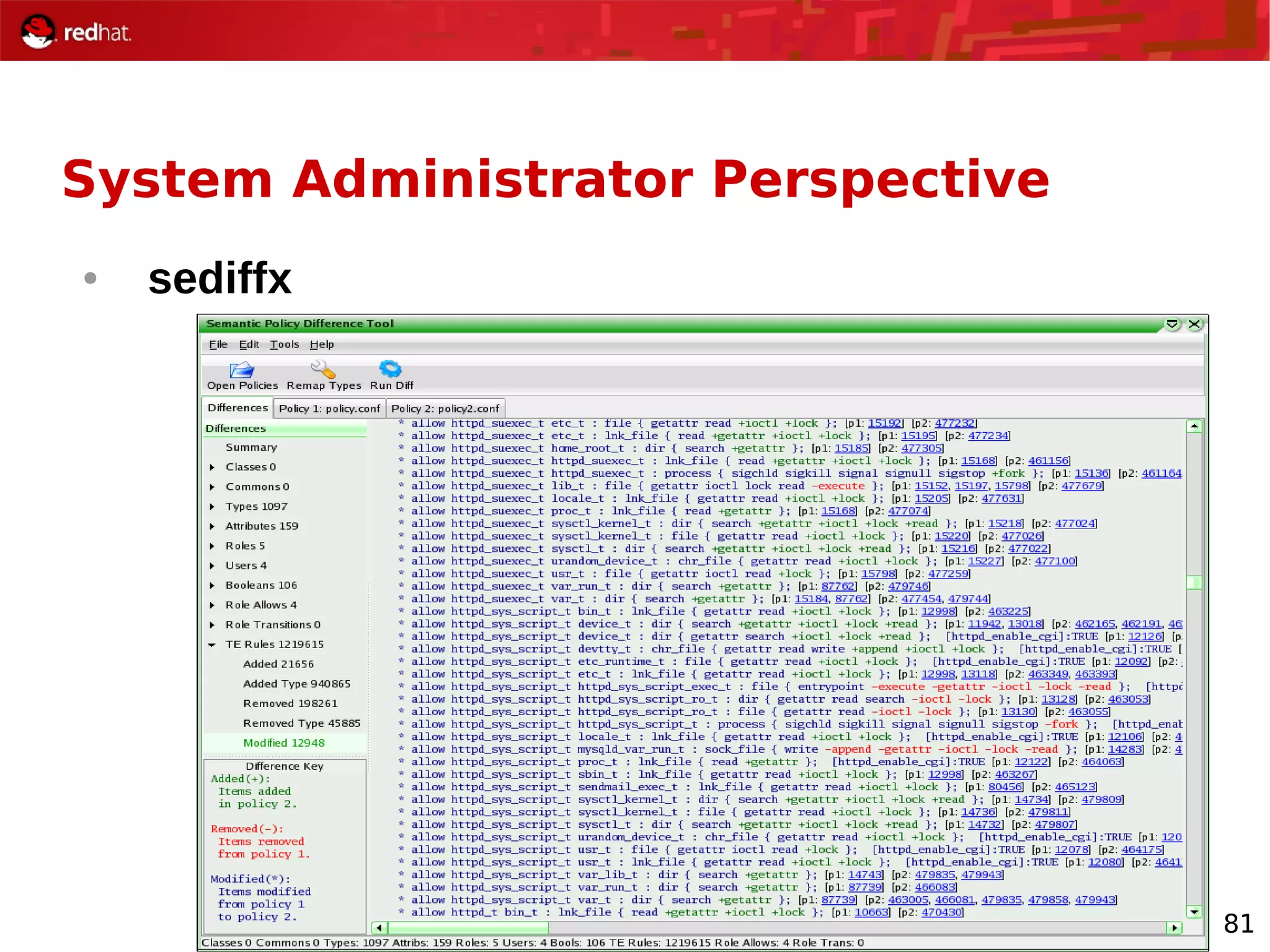
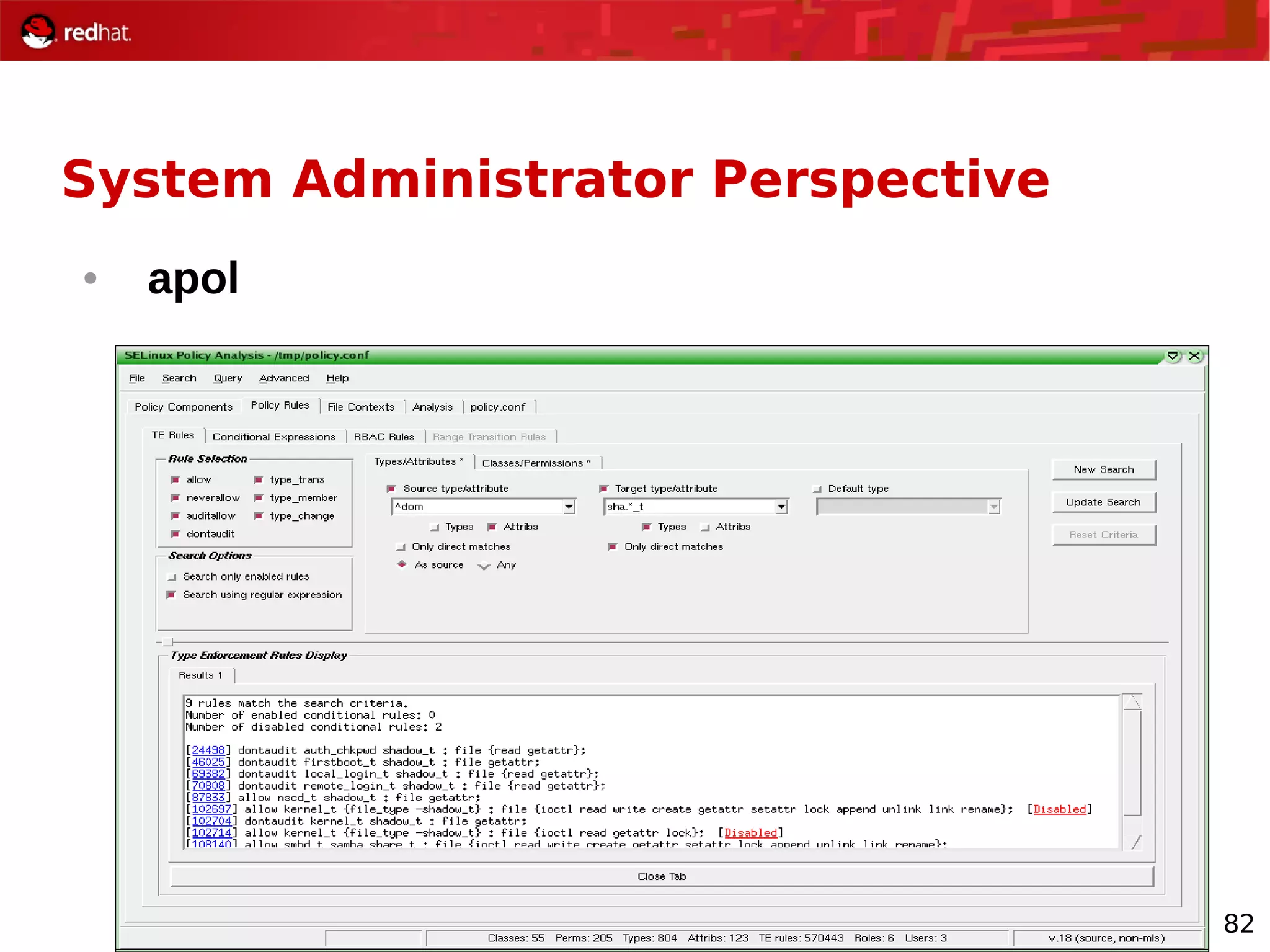
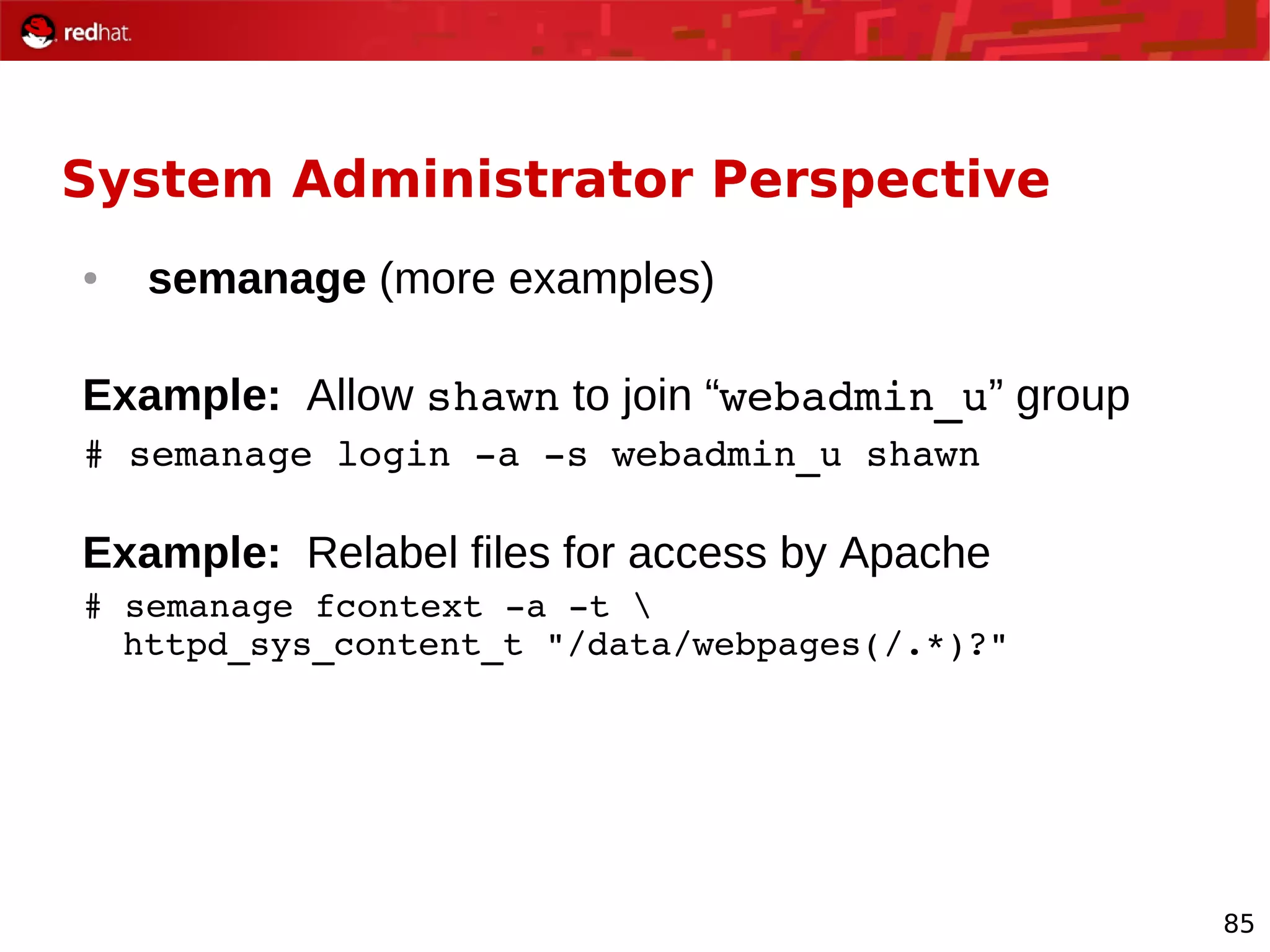
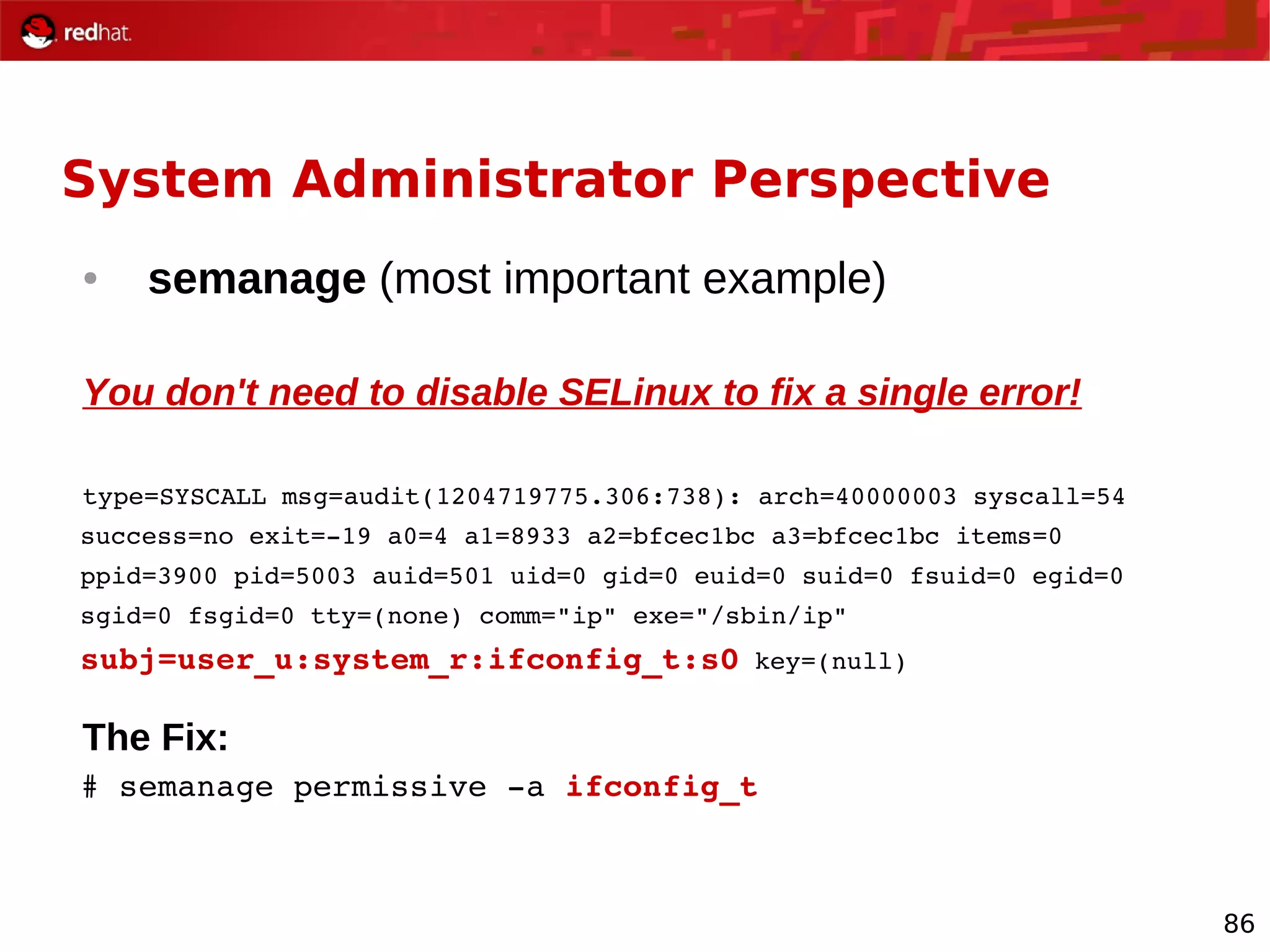
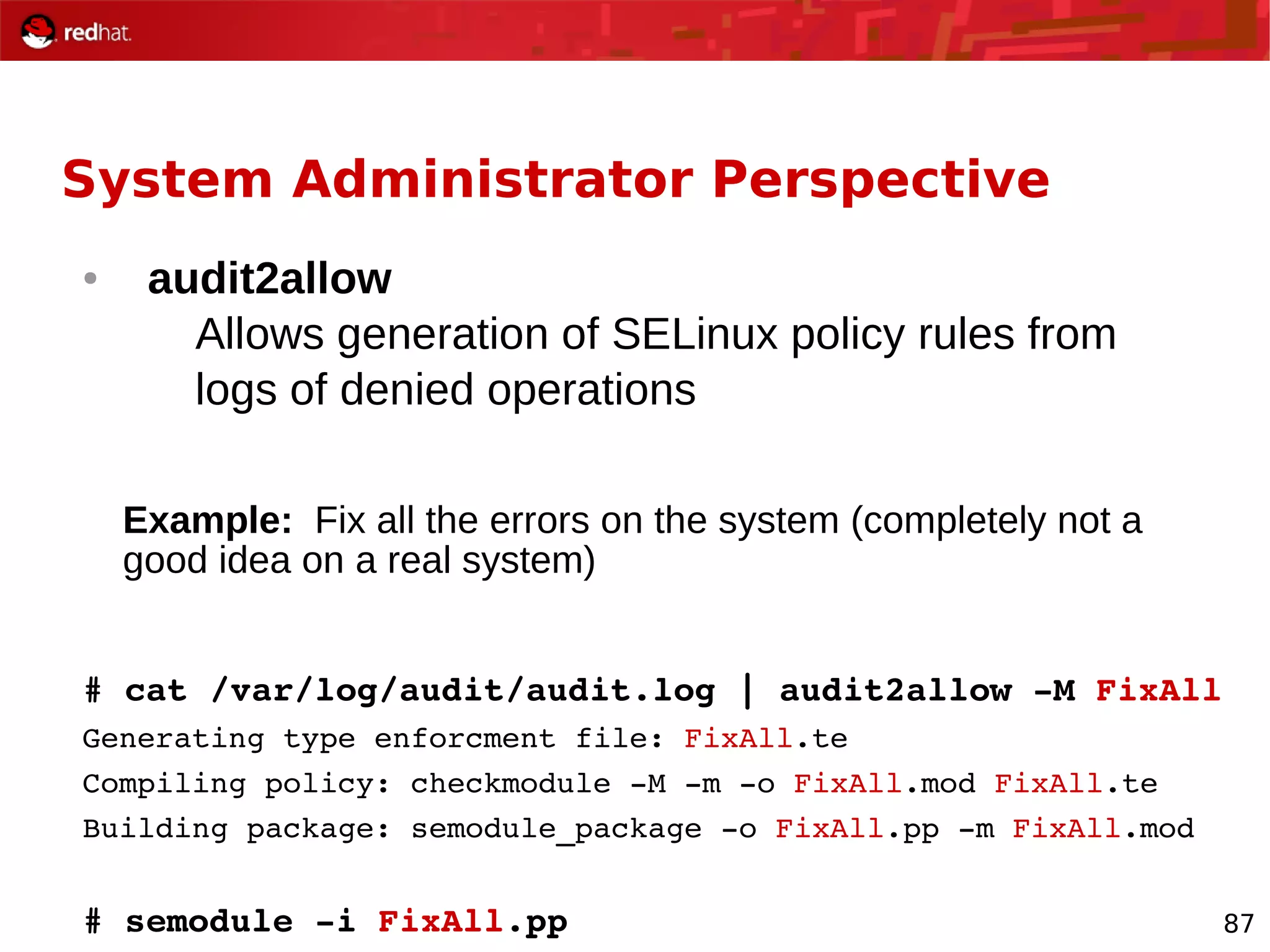
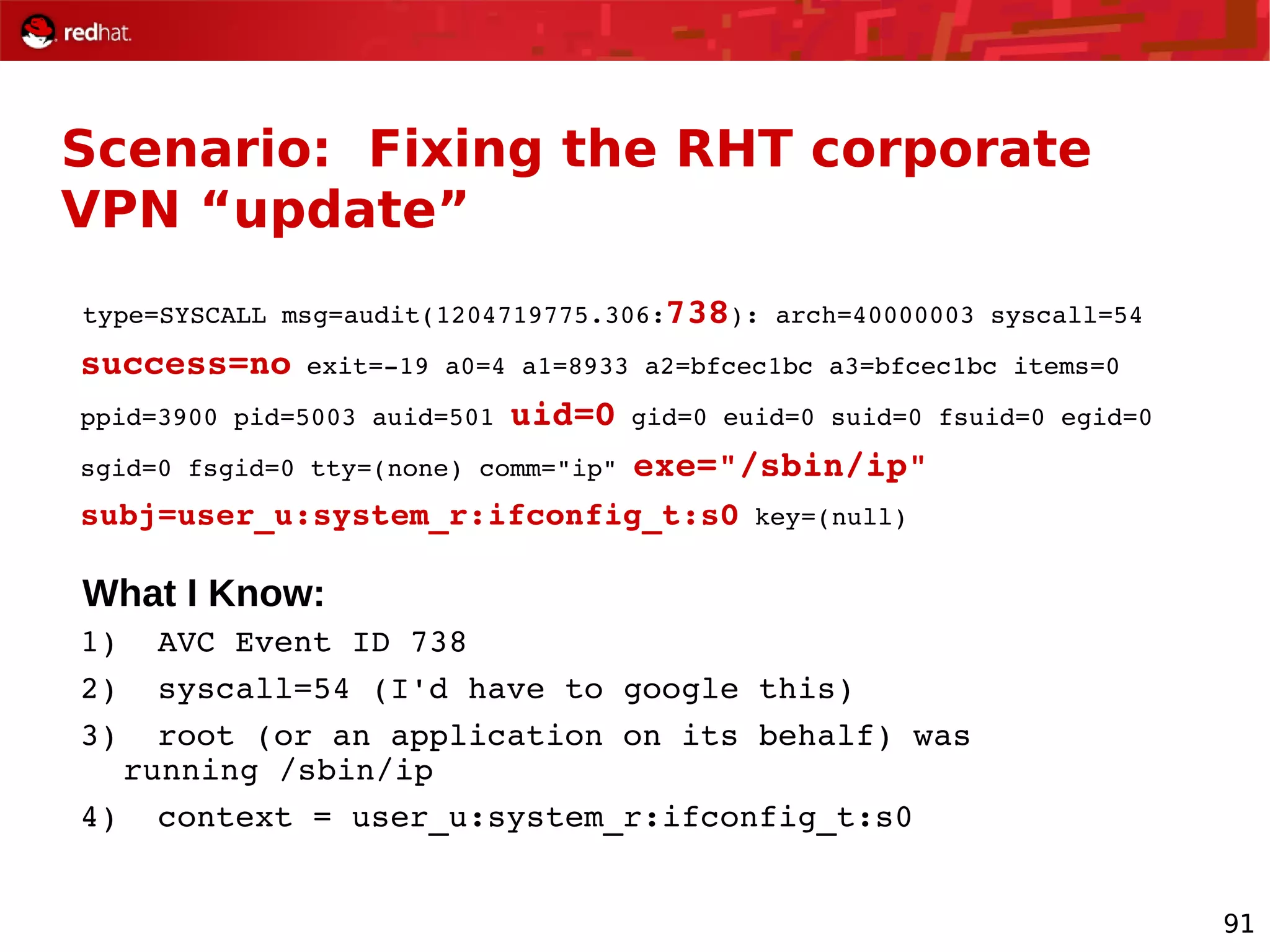
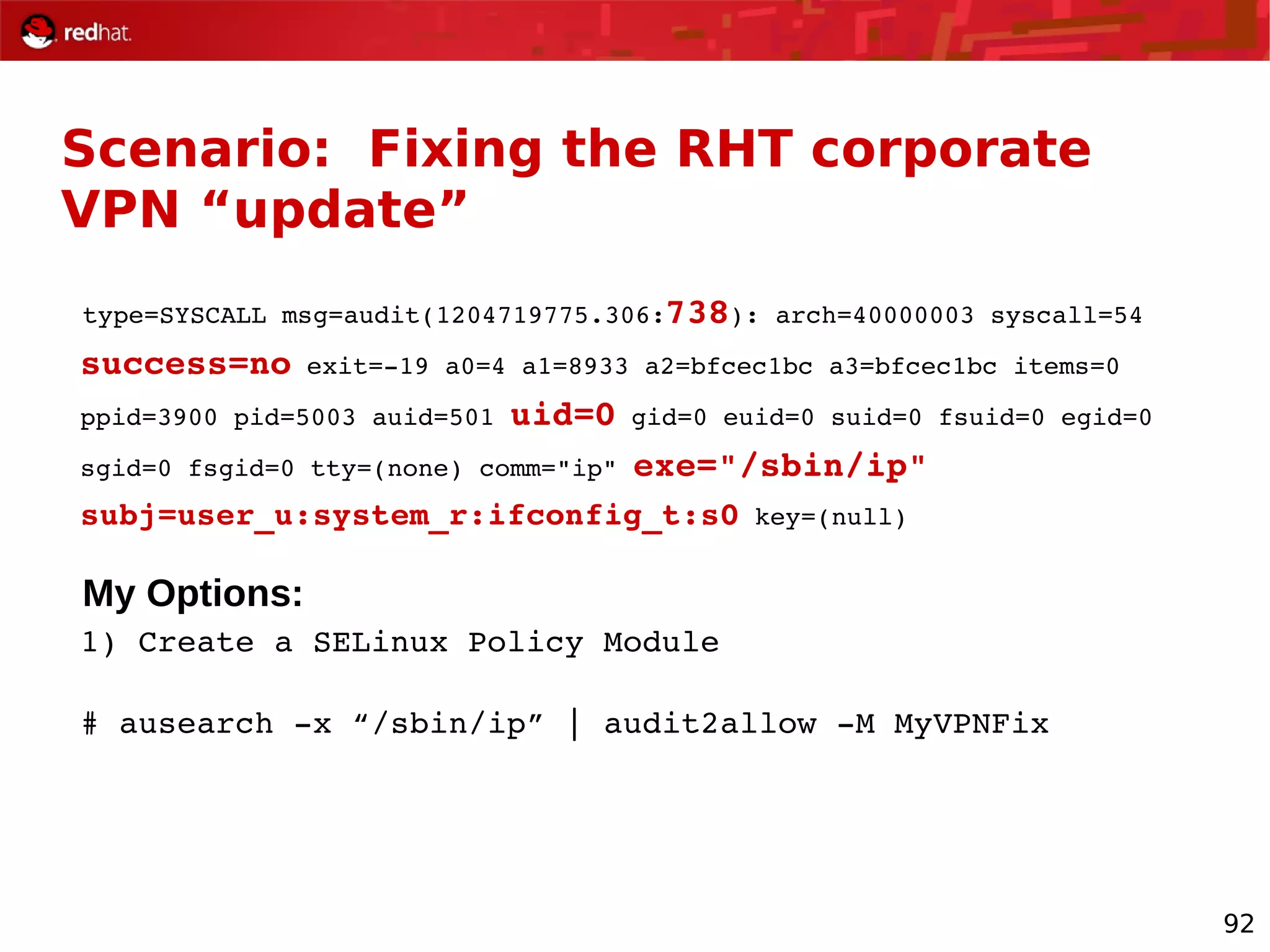
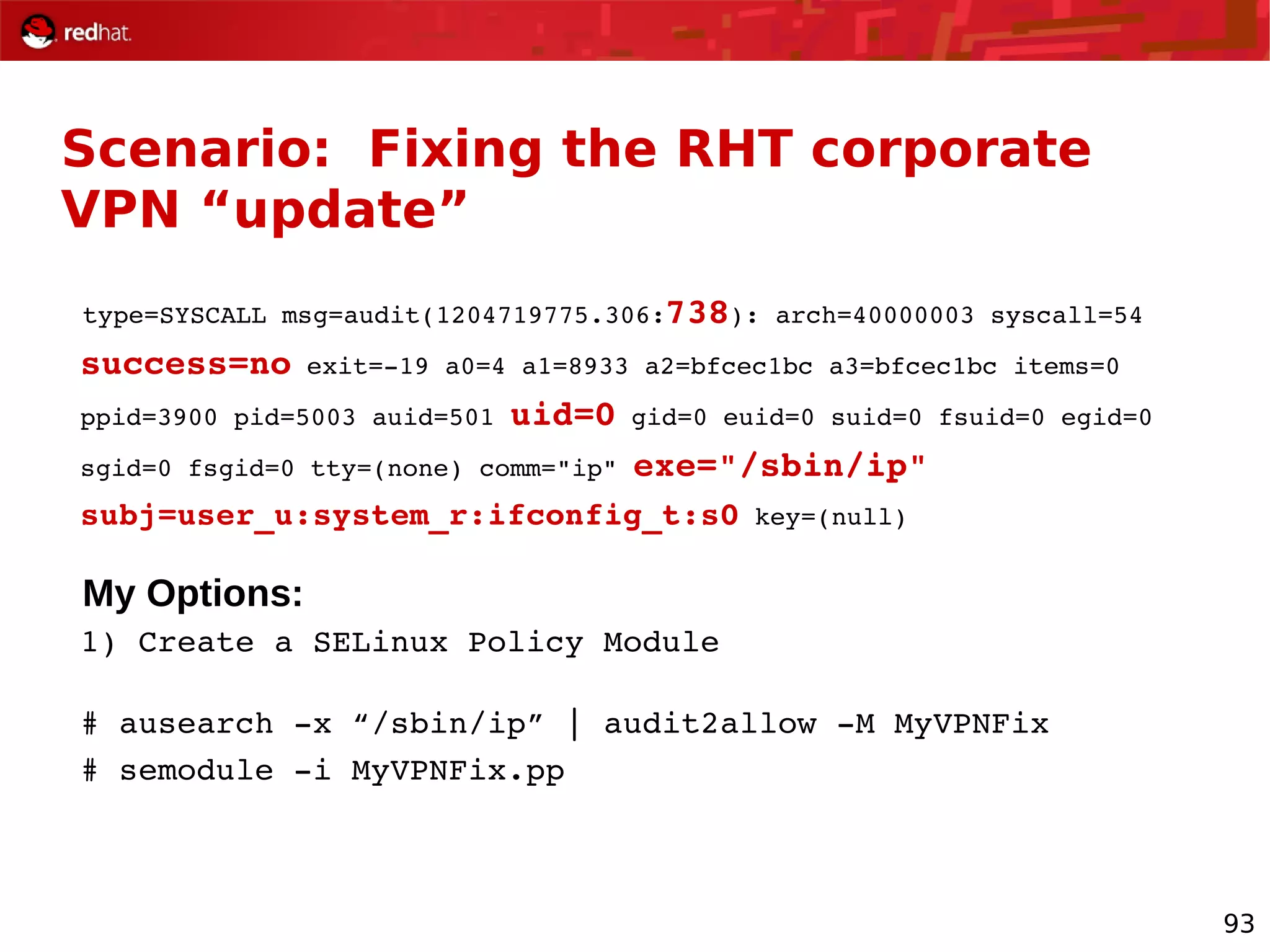
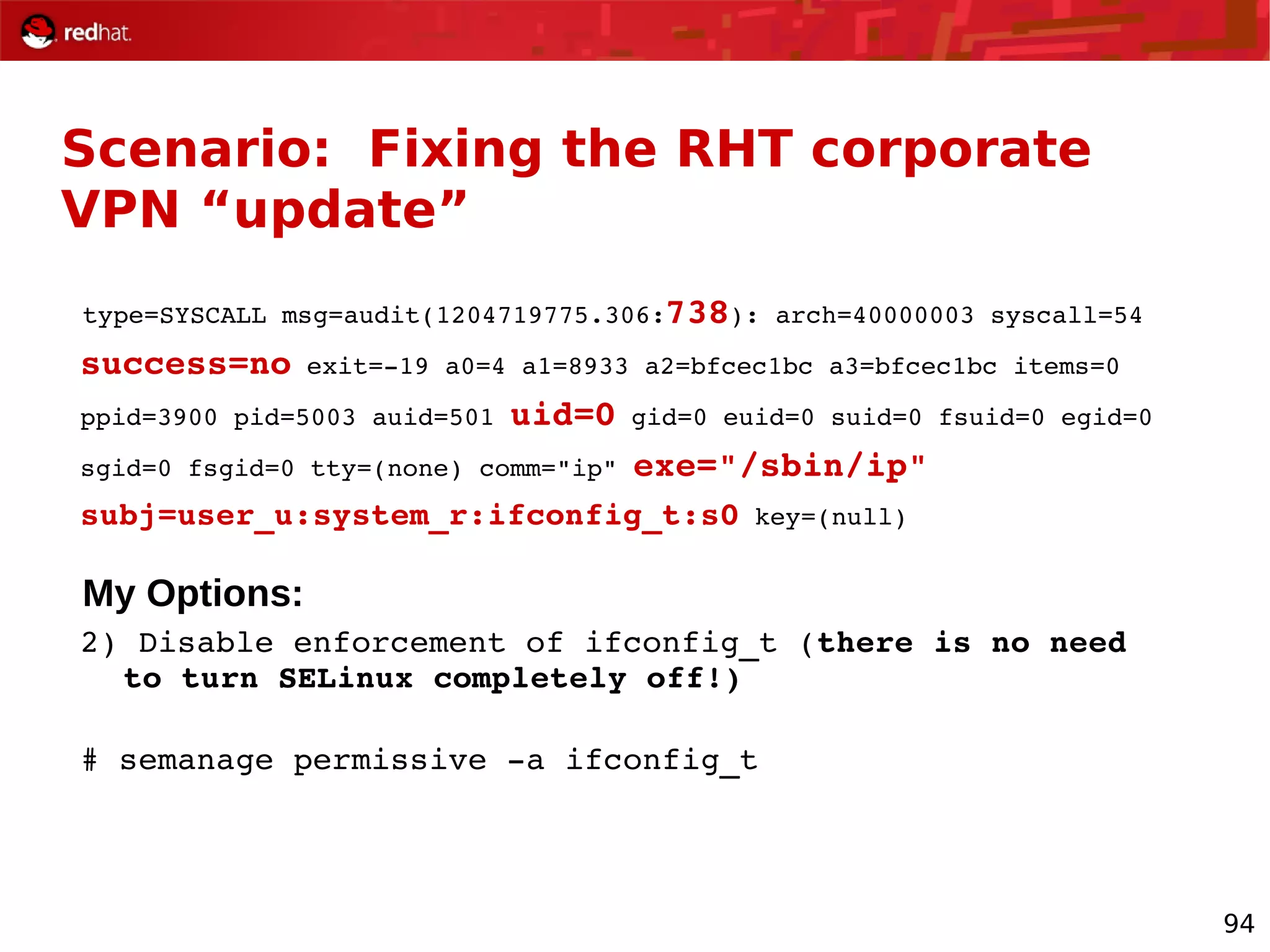
The document provides an overview of Red Hat's Deep Dive sessions focusing on Linux on System z, detailing the development process, current and future releases of Red Hat Enterprise Linux (RHEL), support structures, and the importance of SELinux for security. Key elements discussed include RHEL's development roadmap, subscription models, lifecycle support, and features implemented in versions 5.2 and 5.3. The document also highlights the significance of Fedora as a testing ground for new technologies that influence future RHEL releases.