This document provides an overview of using the libpcap library to perform packet sniffing in C. It discusses installing libpcap on Linux and Windows, avoiding common C programming gotchas, the basic structure of a libpcap program including opening a live network interface and implementing a packet processing callback loop. It also covers reading the Ethernet, IP, and TCP/UDP headers of packets and using BPF filters to filter packets.







![9
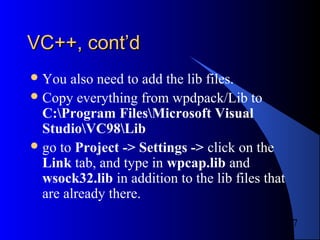
C cont’dC cont’d
Output is formatted.
char person[ ] = “baby”;
printf(“give me %d, %sn”, 5, person);
%d: int
%x: hex
%s: string
%f: double](https://image.slidesharecdn.com/libpcap-101122231040-phpapp01/85/Libpcap-9-320.jpg)
![10
Get to the point!Get to the point!
Pass by reference explicitly
- Pass-by-reference prototype
int doSomething( Thing *);
Choice 1:
Thing * t;
doSomething( t );
Choice 2:
Thing t;
doSomething( &t );
• Arrays are always in reference mode:
char * is like char[0]](https://image.slidesharecdn.com/libpcap-101122231040-phpapp01/85/Libpcap-10-320.jpg)



![14
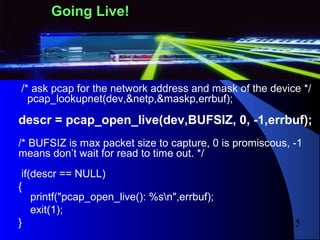
Getting onto the NICGetting onto the NIC
int main(int argc, char **argv) {
char *dev; /* name of the device to use */
pcap_t* descr; /* pointer to device descriptor */
struct pcap_pkthdr hdr; /* struct: packet header */
const u_char *packet; /* pointer to packet */
bpf_u_int32 maskp; /* subnet mask */
bpf_u_int32 netp; /* ip */
char errbuf[PCAP_ERRBUF_SIZE];
/* ask pcap to find a valid device to sniff */
dev = pcap_lookupdev(errbuf);
if(dev == NULL)
{ printf("%sn",errbuf); exit(1); }
printf("DEV: %sn",dev);](https://image.slidesharecdn.com/libpcap-101122231040-phpapp01/85/Libpcap-14-320.jpg)



![19
What is an ethernet header?What is an ethernet header?
From #include<netinet/if_ether.h>
struct ether_header {
u_int8_t ether_dhost[ETH_ALEN]; /* 6 bytes destination */
u_int8_t ether_shost[ETH_ALEN]; /* 6 bytes source addr */
u_int16_t ether_type; /* 2 bytes ID type */
} __attribute__ ((__packed__));
Some ID types:
#define ETHERTYPE_IP 0x0800 /* IP */
#define ETHERTYPE_ARP 0x0806 /* Address resolution */
Is this platform independent?](https://image.slidesharecdn.com/libpcap-101122231040-phpapp01/85/Libpcap-19-320.jpg)

![21
Filter – we don’t need to seeFilter – we don’t need to see
every packet!every packet!
Filters are strings. They get “compiled” into
“programs”
struct bpf_program fp; //where does it go?
Just before the event loop:
if (pcap_compile(descr,&fp,argv[1],0,netp) == -1)
{ fprintf(stderr,"Error calling pcap_compilen");
exit(1);
}
if (pcap_setfilter(descr,&fp) == -1) {
fprintf(stderr,"Error setting filtern");
exit(1);
}](https://image.slidesharecdn.com/libpcap-101122231040-phpapp01/85/Libpcap-21-320.jpg)

