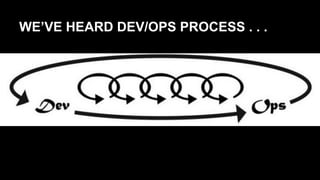
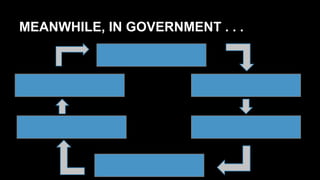
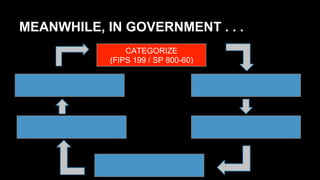
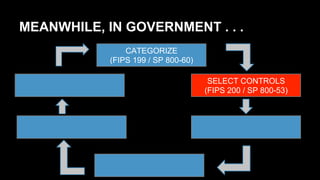
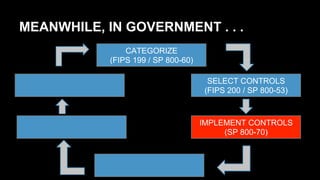
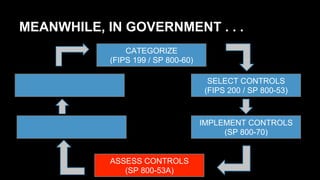
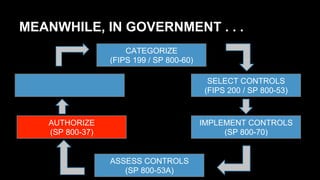
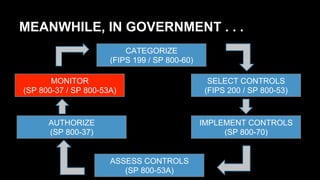
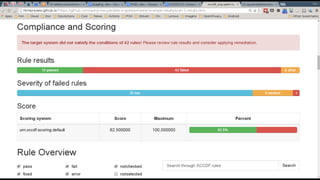
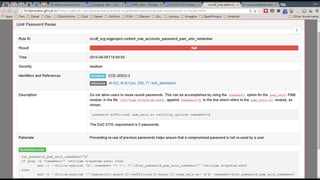
This document discusses the differences between DevOps practices in private industry and security practices in government. It notes that private companies can deploy code over 10,000 times per day, whereas government processes involve multiple standardized steps for categorizing, selecting, implementing, assessing, authorizing, and monitoring controls. The document proposes two initiatives - standardizing controls and configuration baselines across the government, and automating assessments using the Security Content Automation Protocol (SCAP). It provides information on engaging with the OpenSCAP community and learning more about SCAP.