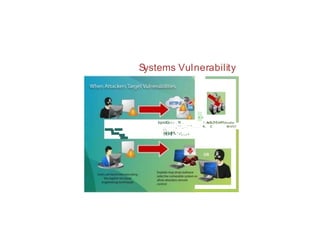
The document discusses systems vulnerability scanning and network vulnerability scanning. It provides an overview of vulnerability scanning concepts like open port identification, banner checking, traffic probing, and vulnerability probing. It also discusses vulnerability assessment tools like OpenVAS and Metasploit. The document defines computer security vulnerabilities and examines the causes and harms of vulnerabilities. It explores concepts like vulnerability management, vulnerability scanning, and why attackers scan for open ports.