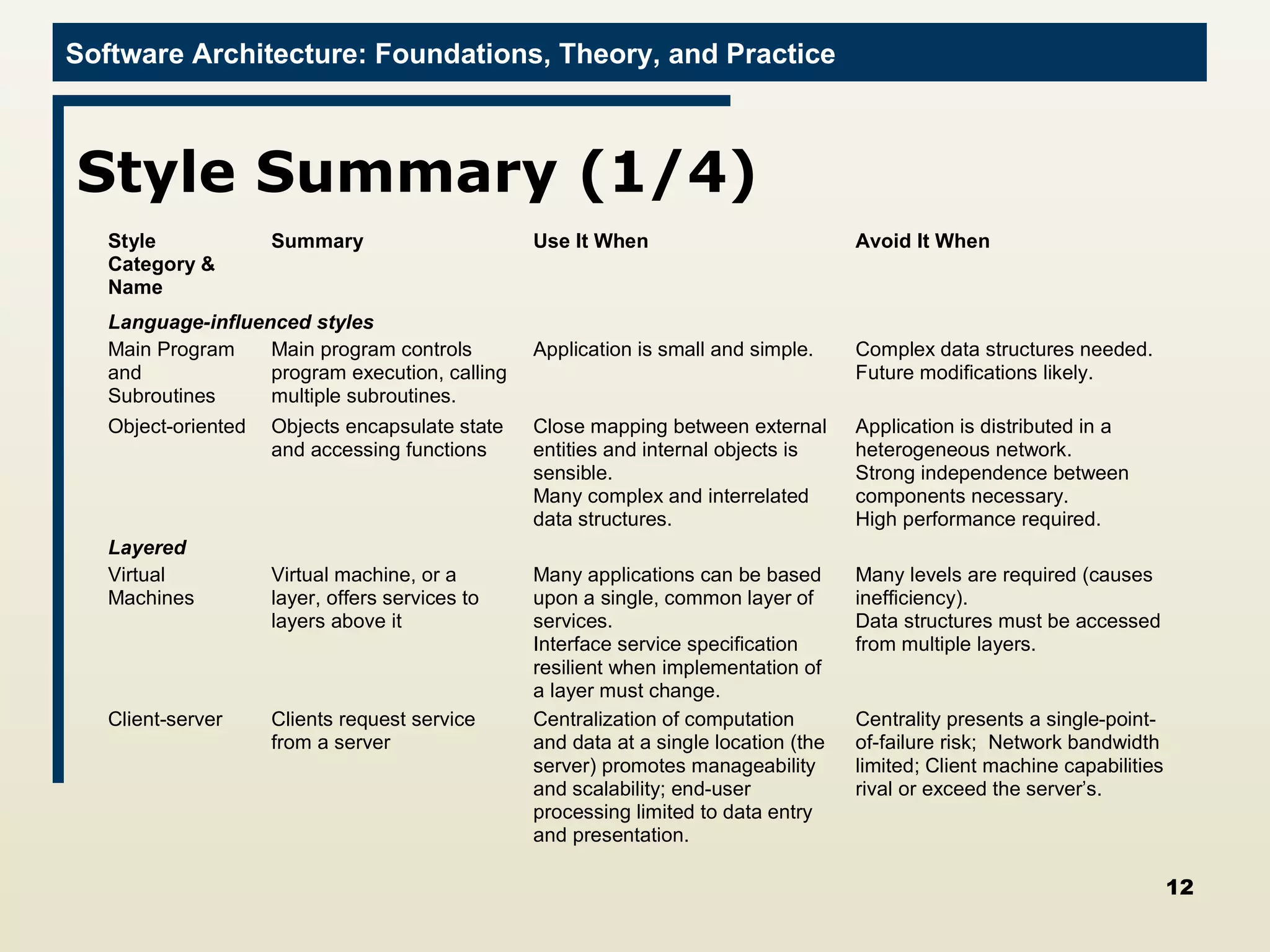
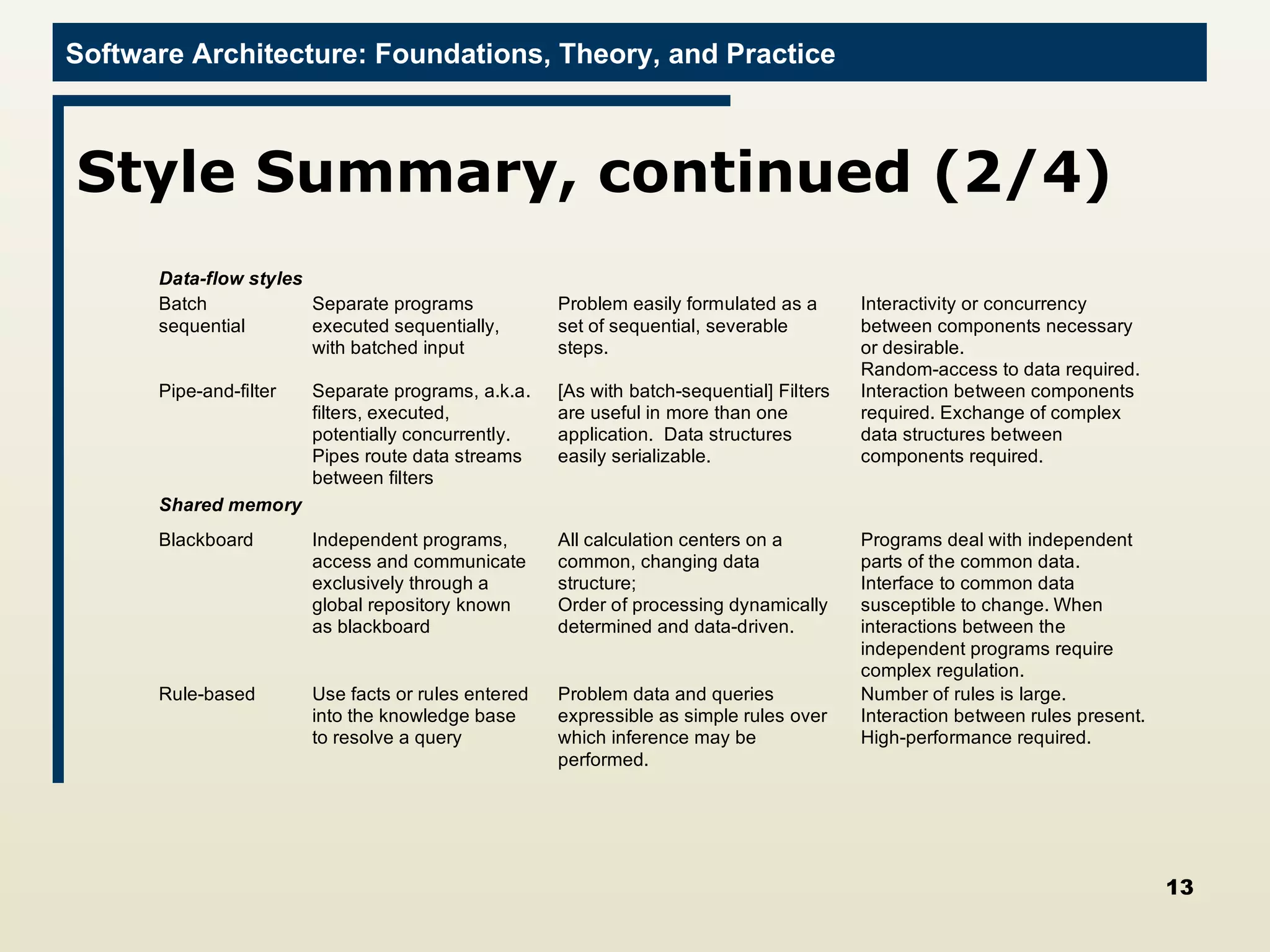
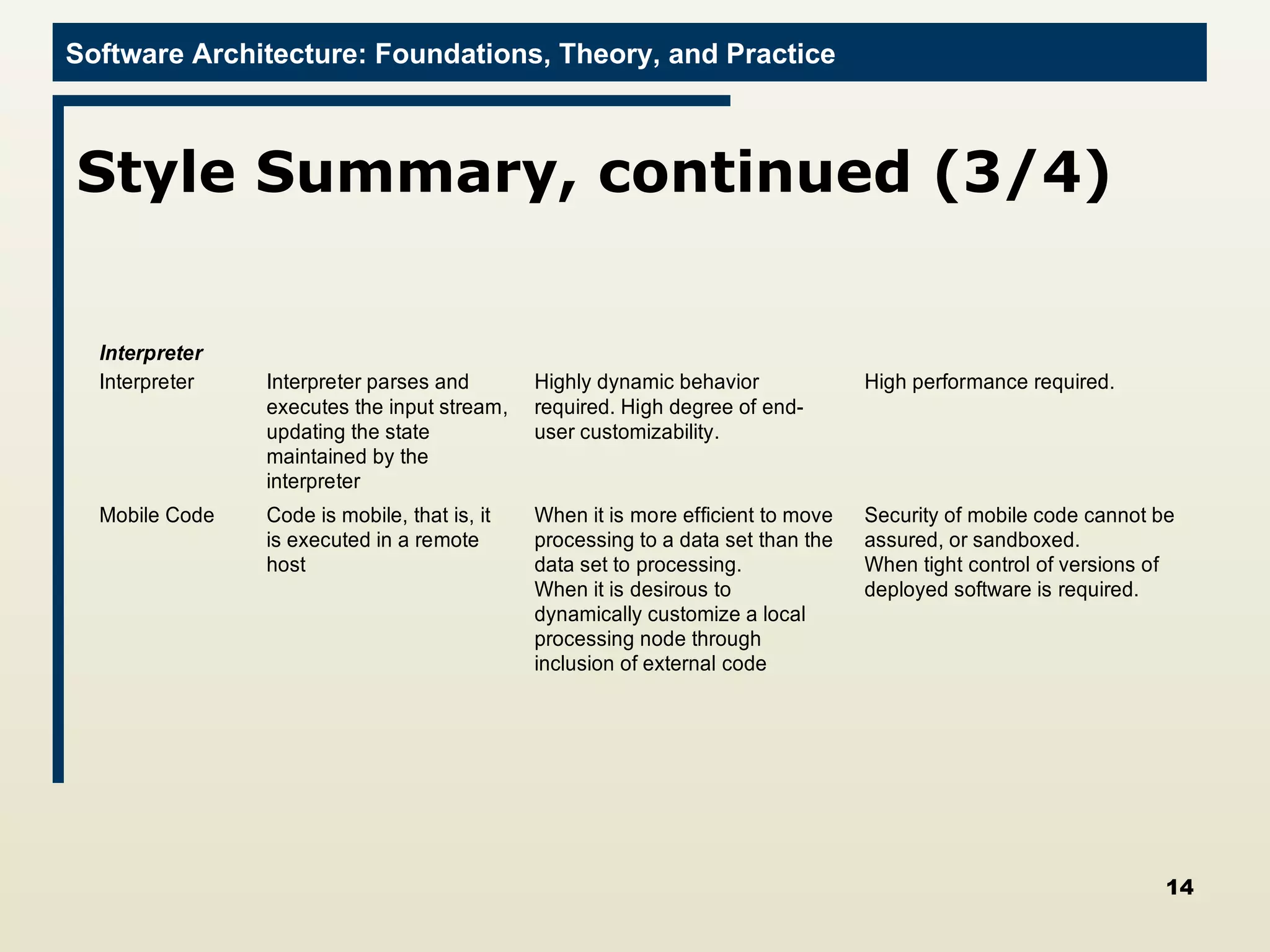
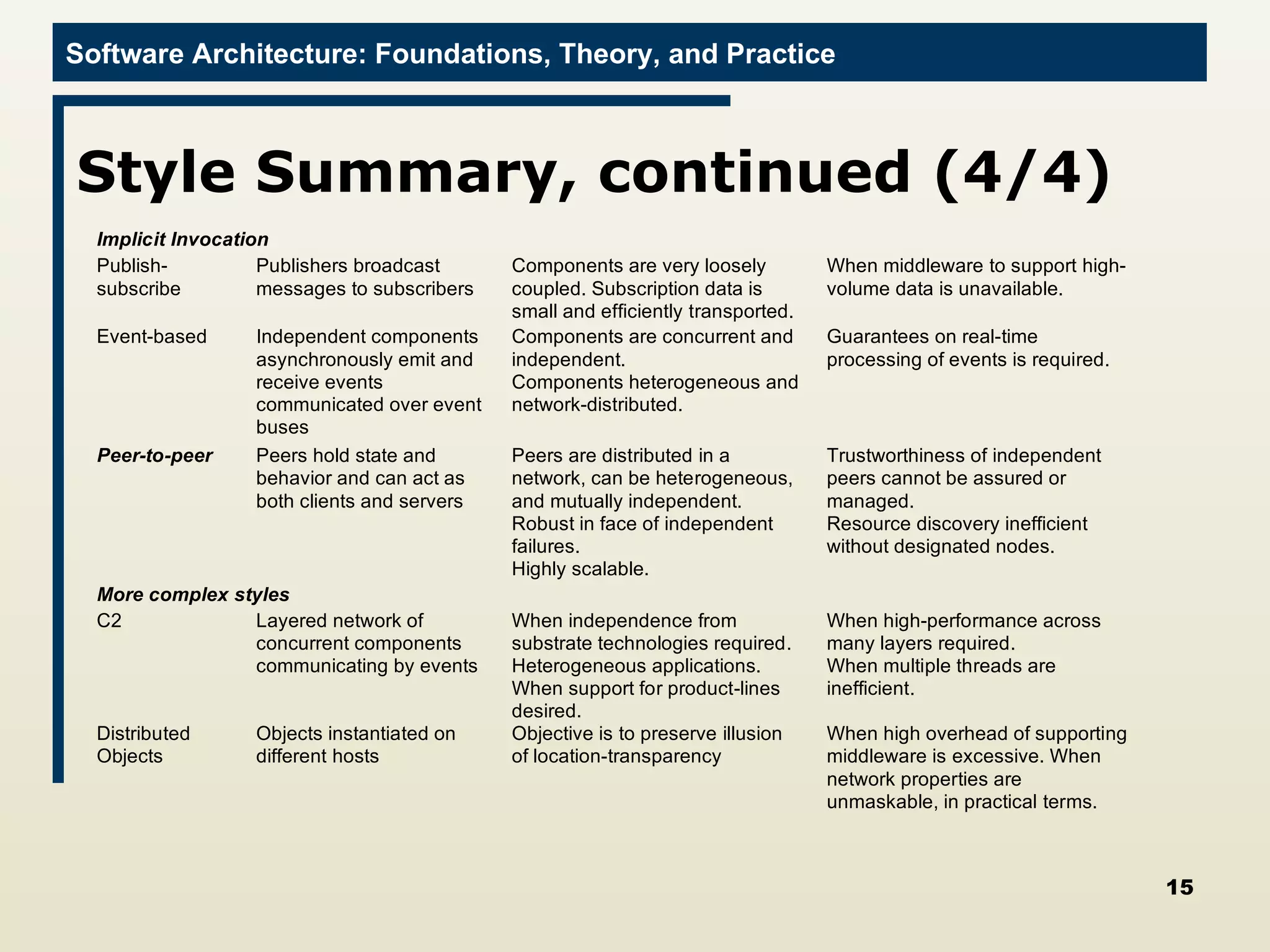
The document discusses several techniques for developing software architectures when no existing architecture exists to build upon. It describes strategies like analogy searching, brainstorming, literature searching, and morphological charts that can be used to generate novel ideas for the architecture. It also emphasizes controlling the design strategy through techniques like identifying critical decisions, relating costs to risks, and continually re-evaluating requirements and implementation constraints.