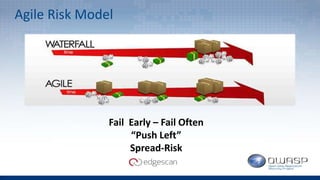
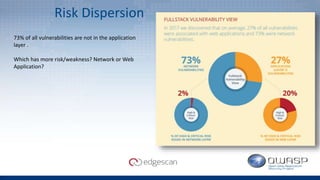
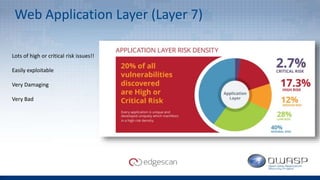
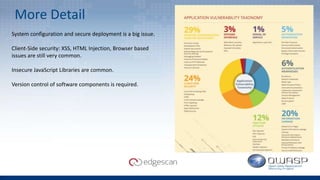
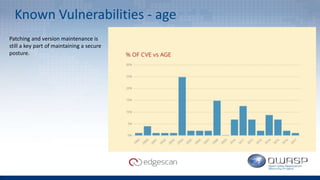
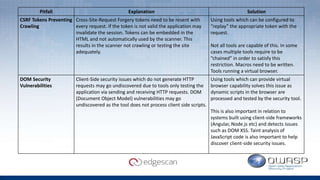
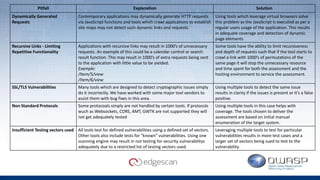
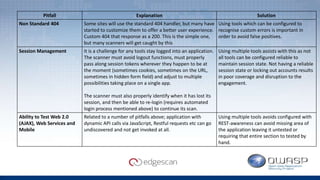
The document discusses Edgescan, a cloud-based vulnerability assessment tool that provides a full-stack view of security, emphasizing the prevalence of vulnerabilities in web applications over network layers. Key issues include the importance of proper patching, automation, and the challenges of testing dynamic elements in modern applications. The report suggests leveraging multiple tools for comprehensive security coverage and addresses common pitfalls in vulnerability scanning.