UNIT-3 Complete PPT.pptx
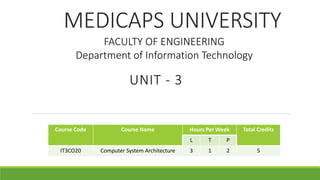
- 1. MEDICAPS UNIVERSITY UNIT - 3 Course Code Course Name Hours Per Week Total Credits L T P IT3CO20 Computer System Architecture 3 1 2 5 FACULTY OF ENGINEERING Department of Information Technology
- 2. Syllabus Information Representation, Floating Point Representation, Computer Arithmetic and Their Implementation; Fixed, Point Arithmetic: Addition, Subtraction, Multiplication and Division, Memory:-Static and Dynamic Memory, Random Access and Serial Access Memories, Cache Memory and Memory Hierarchy, Address Mapping, Cache Updation Schemes, Virtual Memory and Memory Management Unit.
- 3. Information Representation Computer does not understand human language. Any data, viz., letters, symbols, pictures, audio, videos, etc., fed to computer should be converted to machine language first. Number System We are introduced to concept of numbers from a very early age. To a computer, everything is a number, i.e., alphabets, pictures, sounds, etc., are numbers. Number system is categorized into four types − Binary number system consists of only two values, either 0 or 1 Octal number system represents values in 8 digits. Decimal number system represents values in 10 digits. Hexadecimal number system represents values in 16 digits.
- 4. Information Representation Bits and Bytes Bits − A bit is a smallest possible unit of data that a computer can recognize or use. Computer usually uses bits in groups. Bytes − group of eight bits is called a byte. Half a byte is called a nibble.
- 5. Information Representation Number System System Base Digits Binary 2 0 1 Octal 8 0 1 2 3 4 5 6 7 Decimal 10 0 1 2 3 4 5 6 7 8 9 Hexadecimal 16 0 1 2 3 4 5 6 7 8 9 A B C D E F
- 6. Information Representation The following table shows conversion of Bits and Bytes − Byte Value Bit Value 1 Byte 8 Bits 1024 Bytes 1 Kilobyte 1024 Kilobytes 1 Megabyte 1024 Megabytes 1 Gigabyte 1024 Gigabytes 1 Terabyte 1024 Terabytes 1 Petabyte 1024 Petabytes 1 Exabyte 1024 Exabytes 1 Zettabyte 1024 Zettabytes 1 Yottabyte 1024 Yottabytes 1 Brontobyte 1024 Brontobytes 1 Geopbytes
- 7. Information Representation Text Code Text code is format used commonly to represent alphabets, punctuation marks and other symbols. Four most popular text code systems are − EBCDIC ASCII Extended ASCII Unicode
- 8. Sign-Magnitude The sign-magnitude binary format is the simplest conceptual format. To represent a number in sign-magnitude, we simply use the leftmost bit to represent the sign. where 0 means positive, and the remaining bits to represent the magnitude (absolute value). A 8-bit sign-magnitude number would appear as follows: Sign Magnitude 7 6-0
- 9. Fixed Point Representation Addition and Subtraction with Signed-Magnitude Data • We designate the magnitude of two numbers by A and B. • There are eight different conditions when signed numbers are added and subtracted. • The algorithm for addition and subtraction are derived from the table. • When two equal numbers are subtracted, the result should be +0 not -0.
- 10. • When the signs of A and B are identical add the two magnitudes and attach the sign of A to the result. •When the signs of A and B are different compare the magnitudes and subtract the smaller from the larger. •If A>B, Sign of the result to be the same as A. •If A<B, Sign of the result to be complement of A. •If A=B, Subtract B from A and make the sign of result positive. Addition and Subtraction Algorithm
- 12. Hardware Implementation •Let A and B are two registers. (Hold Magnitudes of numbers) •As and Bs are two flipflops. (Hold corresponding signs) •Add Overflow Flip-flop.(Hold overflow bit when A and B Added) •The output carry transferred to flip-flop E. •The addition of A and B is done through the Parallel Adder. •The Sum (S) output of adder is applied to the input of A register.
- 13. Hardware Implementation •The Complementor provides output of B. (or Complement) •Complementer consist of EX-OR gate. •When Mode Control M=0 (Perform Addition) •In addition input carry is 0 and SUM=A+B. •When Mode Control M=1 (Perform Subtraction) •In Subtraction input carry is 1 and SUM=A+B+1. •This is equal A + two’s complement of B, SUM = A-B
- 15. Hardware Algorithm •As and Bs are two flipflops. (Hold corresponding signs) •As and Bs are compared by an Exclusive-OR gate. •If the output of gate=0 (Signs are identical) •If the output of gate=1 (Signs are different) •0 indicate positive sign. •1 indicate negative sign.
- 16. Hardware Algorithm •EA register combines E (carry) and A (register). •The value of E transferred to AVF. •No overflow can occur if the numbers are subtracted and hence AVF is cleared to zero. •E=1 indicates A>=B (Number in A is a correct result) •E=0 indicates A<B (A=A+1, As=As) •The final result found in register A and sign As.
- 23. Shift Micro-Operations •Shift micro-operations are those micro-operations that are used for serial transfer of information. These are also used in conjunction with arithmetic micro-operation, logic micro- operation, and other data-processing operations. •There are three types of shifts micro-operations: •1. Logical •2. Arithmetic •3. Circular
- 24. Shift Micro-Operations •1. Logical : •It transfers the 0 zero through the serial input. We use the symbols shl for logical shift-left and shr for shift-right. •Logical Shift Left – •In this shift one position moves each bit to the left one by one. The Empty least significant bit (LSB) is filled with zero (i.e, the serial input), and the most significant bit (MSB) is rejected.
- 26. Shift Micro-Operations •Right Logical Shift – •In this one position moves each bit to the right one by one and the least significant bit(LSB) is rejected and the empty MSB is filled with zero.
- 27. Shift Micro-Operations •2. Arithmetic : •This micro-operation shifts a signed binary number to the left or to the right position. In an arithmetic shift-left, it multiplies a signed binary number by 2 and In an arithmetic shift-right, it divides the number by 2. •Left Arithmetic Shift – •In this one position moves each bit to the left one by one. The empty least significant bit (LSB) is filled with zero and the most significant bit (MSB) is rejected. Same as the Left Logical Shift.
- 29. Shift Micro-Operations •Right Arithmetic Shift – •In this one position moves each bit to the right one by one and the least significant bit is rejected and the empty MSB is filled with the value of the previous MSB.
- 30. Shift Micro-Operations •3. Circular : •The circular shift circulates the bits in the sequence of the register around the both ends without any loss of information. •Left Circular Shift -
- 31. Shift Micro-Operations •Right Circular Shift –
- 32. Multiplication Algorithm •The process consists of looking at successive bits of the multiplier, least significant bit first. •If the multiplier bit is a 1, the multiplicand is copied down; otherwise, zeros are copied down. •The numbers copied down in successive lines are shifted one position to the left from the previous number. •Finally, the numbers are added and their sum forms the product. •The sign of the product is determined from the signs of the multiplicand and multiplier.
- 33. Multiplication Algorithm •If they are alike, the sign of the product is positive. •If they are unlike, the sign of the product is negative.
- 34. Hardware Implementation •The multiplicand is store in register B and the multiplier in Q. •As, Bs and Qs are flipflops. (Hold corresponding signs) • Qn is the rightmost bit of the multiplier. •The output carry transferred to flip-flop E. (Initial value of E=0) •A register initialize with 0. As denotes sign of partial product. •The sum of A and B forms a partial product which is transferred to the EA register.
- 35. Hardware Implementation •The multiplier is stored in the Q register and its sign in Qs. •The sequence counter SC is initially set to a number equal to the number of bits in the multiplier. •The counter is decremented by 1 after forming each partial product. •When the content of the counter reaches zero, the product is formed and the process stops. •EA register holds partial product , with carry in addition shifted to E. •AQ Contains the final product. A holding the MSB and Q holding the LSB.
- 36. Hardware for Multiply operation
- 37. Hardware Algorithm for Multiplication •The multiplicand is in B and the multiplier in Q. •Their corresponding signs are in B, and Q., respectively. •The signs are compared, and both A and Q are set to correspond to the sign of the product since a double-length product will be stored in registers A and Q. •one bit of the word will be occupied by the sign and the magnitude will consist of n - 1 bits. •After the initialization, the low-order bit of the multiplier in Q, is tested.
- 38. Hardware Algorithm for Multiplication •If it is a 1, the multiplicand in B is added to the present partial product in A. If i t i s a 0, nothing is done. •Register EAQ is then shifted once to the right to form the new partial product. •The sequence counter is decremented by 1 and its new value checked. •If it is not equal to zero, the process is repeated and a new partial product is formed. •The process stops when SC = 0.
- 44. Booth’s Multiplication Algorithm •In Booth’s Algorithm sign bits are not separated from register. •Qr register contains the multiplier. •Qn represent LSB of the multiplier in Qr register. •Qn+1 is an extra flip-flop appended to Qr to facilitate a double bit inspection of the multiplier. •To show this difference, we rename registers A, B, and Q, as AC, BR, and QR, respectively.
- 45. Booth’s Multiplication Algorithm •Ac and Qn+1 are initially cleared to 0. •The sequence counter SC is set to a number n equal to the number of bits in the multiplier. •The two bits of the multiplier in Qn and Qn+1 are inspected. • If the two bits are equal to 10, it means that the first 1 in a string of 1' s has been encountered. •This requires a subtraction of the multiplicand from the partial product in AC.
- 47. Booth’s Multiplication Algorithm •Booth algorithm gives a procedure for multiplying binary integers in signed-2's complement representation. • As in all multiplication schemes, Booth algorithm requires examination of the multiplier bits and shifting of the partial product. •Prior to the shifting, the multiplicand may be added to the partial product, subtracted from the partial product, or left unchanged according to the following rules:
- 48. Booth’s Multiplication Algorithm •1. The multiplicand is subtracted from the partial product upon encountering the first least significant 1 in a string of 1's in the multiplier. (10) •2. The multiplicand is added to the partial product upon encountering the first 0 (provided that there was a previous 1) in a string of O's in the multiplier. (01) •3. The partial product does not change when the multiplier bit is identical to the previous multiplier bit. (00/11)
- 49. Booth’s Multiplication Algorithm •If the two bits are equal to 01, it means that the first 0 in a string of 0' s has been encountered. •This requires the addition of the multiplicand to the partial product in AC. •When the two bits are equal, the partial product does not change. •An overflow cannot occur because the addition and subtraction of the multiplicand follow each other.
- 50. Booth’s Multiplication Algorithm •The two numbers that are added always have opposite sign. •The next step is to shift right the partial product and the multiplier. •This is an arithmetic shift right (ashr) operation which shifts AC and QR to the right and leaves the sign bit in AC unchanged. •The sequence counter is decremented and the computational loop is repeated n times.
- 64. 2-bt by 2-bit Array Multiplier
- 65. 4-bit by 3-bit Array Multiplier
- 66. Division Algorithm •Division of two fixed-point binary numbers in signed-magnitude representation is done with paper and pencil by a process of successive compare, shift, and subtract operations. •The quotient digits are either 0 or 1 and there is no need to estimate how many times the dividend or partial remainder fits into the divisor. •The division process is illustrated by a numerical example
- 72. Hardware Algorithm •The dividend is in A and Q and the divisor in B. • The sign of the result is transferred into Qs to be part of the quotient. •A constant is set into the sequence counter SC to specify the number of bits in the quotient. •As in multiplication, we assume that operands are transferred to registers from a memory unit that has words of n bits. •an operand must be stored with its sign, one bit of the word will be occupied by the sign and the magnitude will consist of n -1 bits.
- 73. Hardware Algorithm •If the bit shifted into E is 1, B must be subtracted from EA and 1 inserted into Qn for the quotient bit. •If the shift-left operation inserts a 0 into E, the divisor is subtracted by adding its 2's complement value and the carry is transferred into E. •If E = 1, it signifies that A>=B; therefore, Qn is set to 1. •If E = 0, it signifies that A < B and the original number is restored by adding B to A. •The quotient sign is in Qs and the sign of the remainder in As is the same as the original sign of the dividend.
- 88. Assignment for 1st Week [Unit-3 (I)] Q.1 Show the step-by-step multiplication process using Booth algorithm when the following binary numbers are multiplied. Assume 5-bit registers that hold signed numbers. The multiplicand in both cases is + 15. a. (+15) x (+13) b. (+15) X (-13) Q.2 Show the contents of registers E, A, Q, and SC during the process of multiplication of two binary numbers, 11111 (multiplicand) and 10101 (multiplier). The signs are not included. Q.3 Show the contents of registers E, A, Q, and SC during the process of division of (a) 10100011 by 1011; (b) 00001111 by 0011. (Use a dividend of eight bits.) Q.4 Show the step-by-step Addition/Subtraction process using Addition/Subtraction Algorithm A. 8-7 B. 6-7 C. 5+4 D. -5-4 Q.5 Represent 58.25 in IEEE 754 single precision floating point representation.
- 89. Memory •Memory unit is essential component of digital computer since it is needed for storing programs and data. •Memory unit that communicates directly with CPU is called Main memory. •Devices that provide backup storage is called auxiliary memory. •Only programs and data currently needed by processor reside in the main memory. •All other information is stored in auxiliary memory and transferred to main memory when needed.
- 90. Memory Hierarchy •The total memory capacity of a computer can be visualized as being a hierarchy of components. •Memory hierarchy system consist of all storage devices from auxiliary memory to main memory to cache memory •As one goes down the hierarchy : Cost per bit decreases. Capacity increases. Access time increases. Frequency of access by the processor decreases.
- 91. Levels of the Memory Hierarchy
- 92. Memory Hierarchy
- 93. Main Memory •It is the memory used to store programs and data during the computer operation. •The principal technology is based on semiconductor integrated circuits. •It consists of RAM and ROM chips. •RAM chips are available in two form static and dynamic.
- 94. RAM & ROM •RAM was used to refer to a random-access memory, but now it is used to designate a read/write memory to distinguish it from a read- only memory, although ROM is also random access. •RAM is used for storing the bulk of the programs and data that are subject to change. • ROM is used for storing programs that are permanently resident in the computer and for tables of constants that do not change in value once the production of the computer is completed. •The ROM portion of main memory is needed for storing an initial program called a bootstrap loader.
- 95. Bootstrap Loader •The bootstrap loader is a program whose function is to start the computer software operating when power is turned on. •Since RAM is volatile, its contents are destroyed when power is turned off. •The contents of ROM remain unchanged after power is turned off and on again. •The startup of a computer consists of turning the power on and starting the execution of an initial program. •The bootstrap program loads a portion of the operating system from disk to main memory and control is then transferred to the operating system, which prepares the computer for general use.
- 96. RAM and ROM Chips •A RAM chip is better suited for communication with the CPU if it has one or more control inputs that select the chip only when needed. •Another common feature is a bidirectional data bus that allows the transfer of data either from memory to CPU during a read operation, or from CPU to memory during a write operation. •The capacity of the memory is 128 words of eight bits (one byte) per word. This requires a 7-bit address and an 8-bit bidirectional data bus. •The read and write inputs specify the memory operation. • The two chips select (CS) control inputs are for enabling the chip only when it is selected by the microprocessor.
- 98. ROM •It is used for storing programs that are permanent and the tables of constants that do not change. •ROM store program called bootstrap loader whose function is to start the computer software when the power is turned on. •When the power is turned on, the hardware of the computer sets the program counter to the first address of the bootstrap loader. •For the same size chip it is possible to have more bits of ROM than of RAM, because the internal binary cells in ROM occupy less space than in RAM •For this reason the diagram specifies 512 byte ROM and 128 bytes RAM.
- 99. ROM •A ROM can only read, the data bus can only be in an output mode. •The nine address lines in the ROM chip specify any one of the 512 bytes stored in it. •The two chip select inputs must be CS1 = 1 and CS2 = 0 for the unit to operate. Otherwise, the data bus is in a high-impedance state. •There is no need for a read or write control because the unit can only read. Thus when the chip is enabled by the two select inputs, the byte selected by the address lines appears on the data bus.
- 100. Typical ROM Chip
- 101. Memory Address Map •The designer of a computer system must calculate the amount of memory required for the particular application and assign it to either RAM or ROM. •The addressing of the memory is then established by means of table called memory address map that specifies the memory address assign to each chip. •To demonstrate with a particular example, assume that a computer system needs 512 bytes of RAM and 512 bytes of ROM.
- 103. Memory Address Map •Although there are 16 lines in the address bus, the table shows only 10 lines because the other 6 are not used in this example and are assumed to be zero. •The small x's under the address bus lines designate those lines that must be connected to the address inputs in each chip. •The RAM chips have 128 bytes and need seven address lines. •The ROM chip has 512 bytes and needs 9 address lines. •The x's are always assigned to the low-order bus lines: lines 1 through 7 for the RAM and lines 1 through 9 for the ROM.
- 104. Memory Address Map •It is now necessary to distinguish between four RAM chips by assigning to each a different address. •For this particular example we choose bus lines 8 and 9 to represent four distinct binary combinations. •Note that any other pair of unused bus lines can be chosen for this purpose. •The distinction between a RAM and ROM address is done with another bus line. When line 10 is 0, the CPU selects a RAM, and when this line is equal to 1, it selects the ROM
- 105. Memory Address Map for Microprocessor
- 111. Sr.No. SRAM DRAM 1. Transistors are used to store information in SRAM. Capacitors are used to store data in DRAM. 2. Capacitors are not used hence no refreshing is required. To store information for a longer time, contents of the capacitor needs to be refreshed periodically. 3. SRAM is faster as compared to DRAM. DRAM provides slow access speeds. 4. These are expensive. These are cheaper. 5. SRAMs are low density devices. DRAMs are high density devices. 6. These are used in cache memories. These are used in main memories.
- 112. Auxiliary Memory •The most common auxiliary memory devices used in computer systems are magnetic disks and magnetic tapes. •Other components used, but not as frequently, are magnetic drums, magnetic bubble memory, and optical disks. •The important characteristics of any device are its access mode, access time, transfer rate, capacity, and cost. •The average time required to reach a storage location in memory and obtain its contents is called the access time.
- 113. Auxiliary Memory •Transfer time required to transfer data to or from the device. •The seek time is usually much longer than the transfer time. •Auxiliary storage is organized in records or blocks. •A record is a specified number of characters or words. •Reading or writing is always done on entire records. •The transfer rate is the number of characters or words that the device can transfer per second, after it has been positioned at the beginning of the record.
- 114. Magnetic Disk •A magnetic disk is a circular plate constructed of metal or plastic coated with magnetized material. •Often both sides of the disk are used and several disks may be stacked on one spindle with read/write heads available on each surface. •All disks rotate together at high speed and are not stopped or started for access purposes. •Bits are stored in the magnetized surface in spots along concentric circles called tracks.
- 115. Magnetic Disk •The tracks are commonly divided into sections called sectors. •The minimum quantity of information which can be transferred is a sector. •Some units use a single read/write head for each disk surface. •In other disk systems, separate read/write heads are provided for each track in each surface.
- 117. Magnetic Tape •Magnetic tape is a strip of plastic coated with a magnetic recording medium. • It is a Sequential Storage Medium used for data collection, backups and archiving. •The major drawbacks of tape is its sequential format locating a specific records requires reading every record in front of it. •Magnetic tape provides a compact, economical means of preserving & reproducing varied forms of information.
- 118. Magnetic Tape •Recording on tape can be played back immediately & are easily erased, permitting the tape to be reused many times without a loss in quality of recording. •Bits are recorded as magnetic spots on tape along several tracks. •Usually 7 or 9 bits are recorded simultaneously to forma character together with a parity bit. •Read/write heads are mounted one in each track so that data can be recorded and read as a sequence of characters. •Magnetic tape units can be stopped, started to move forward or in reverse, or can be rewound.
- 119. Magnetic Tape •Information is recorded in blocks referred to as records. •Each record on tape has an identification bit pattern at the beginning and end. •By reading the bit pattern at the beginning, the tape control identifies the record number. By reading the bit pattern at the end of the record, the control recognizes the beginning of a gap. • A tape unit is addressed by specifying the record number and the number of characters in the record. •Records may be of fixed or variable length.
- 123. Cache Memory •Cache Memory is a special very high-speed memory. • It is used to speed up and synchronizing with high-speed CPU. •Cache memory is costlier than main memory or disk memory but economical than CPU registers. •Cache memory is an extremely fast memory type that acts as a buffer between RAM and the CPU. •It holds frequently requested data and instructions so that they are immediately available to the CPU when needed.
- 124. Cache Memory •Cache memory is used to reduce the average time to access data from the Main memory. •The cache is a smaller and faster memory which stores copies of the data from frequently used main memory locations. •There are various different independent caches in a CPU, which store instructions and data. •The cache memory access time is less than the access time of main memory by a factor of 5 to 10.
- 126. Cache Memory •When the CPU needs to access memory, the cache is examined. •If the word is found in the cache, it is read from the fast memory. •If the word addressed by the CPU is not found in the cache, the main memory is accessed to read the word. •A block of words containing the one just accessed is then transferred from main memory to cache memory. •The block size may vary from one word (the one just accessed) to about 16 words.
- 127. Cache Memory •Some data are transferred to cache so that future references to memory find the required words in the fast cache memory. •The performance of cache memory is frequently measured in terms of a quantity called hit ratio . •When the CPU refers to memory and finds the word in cache, it is said to produce a hit. •If the word is not found in cache, it is in main memory and it counts as a miss. •The ratio of the number of hits divided by the total CPU references to memory (hits plus misses) is the hit ratio.
- 128. Cache Memory •The hit ratio is best measured experimentally by running representative programs in the computer and measuring the number of hits and misses during a given time. •The basic characteristic of cache memory is its fast access time. •The transformation of data from main memory to cache memory is referred to as a mapping process. •Three types of mapping procedures are of practical interest when considering the organization of cache memory: •1. Direct mapping 2. Associative mapping 3. Set-associative mapping
- 145. Locality of Reference •1. Spatial Locality (Space) •2. Temporal Locality (Time) •If a word is accessed now then the word adjacent to it will be accessed next. •Keeping more words in a block affects spatial locality. (block size) •If a word is referenced now then the same word will be reference again in future. •LRU is used in temporal locality.
- 146. Associative Memory •A memory unit accessed by content is called an associative memory or Content Addressable Memory (CAM). •This type of memory is accessed simultaneously and in parallel on the basis of data content rather than by specific address or location. •When a word is written in an associative memory, no address is given. •The memory is capable of finding an empty unused location to store the word.
- 147. Associative Memory •When a word is to be read from an associative memory, the content of the word, or part of the word, is specified. •The memory locates all words which match the specified content and marks them for reading. •The time required to find an item stored in memory can be reduced considerably if stored data can be identified for access by the content of the data itself rather than by an address. •Because of its organization, the associative memory is uniquely suited to do parallel searches by data association.
- 148. Associative Memory •Searches can be done on an entire word or on a specific field within a word. •An associative memory is more expensive than a random access memory because each cell must have storage capability as well as logic circuits for matching its content with an external argument. •For this reason, associative memories are used in applications where the search time is very critical and must be very short.
- 149. How associative memory works? •Data is stored at the very first empty location found in memory. •In associative memory when data is stored at a particular location then no address is stored along with it. •When the stored data need to be searched then only the key (i.e. data or part of data) is provided. •A sequential search is performed in the memory using the specified key to find out the matching key from the memory. •If the data content is found then it is set for the next reading by the memory.
- 150. Associative Memory •It consists of a memory array and logic for m words with n bits per word. •The argument register A and key register K each have n bits, one for each bit of a word. •The match register M has m bits, one for each memory word. •Each word in memory is compared in parallel with the content of the argument register. •The key register provides a mask for choosing a particular field or key in the argument word.
- 152. Associative Memory •The entire argument is compared with each memory word if the key register contains all l' s. •Otherwise, only those bits in the argument that have l's in their corresponding position of the key register are compared.
- 154. Associative Memory •Advantages of associative memory •Advantages of associative memory is given below: •Associative memory searching process is fast. •Associative memory is suitable for parallel searches. •Disadvantages of associative memory •Disadvantages of associative memory is given below: •Associative memory is expensive than RAM
- 155. Difference between RAM and CAM Sr. No. Key RAM [MM] CAM [AM] 1 Definition RAM stands for Random Access Memory. CAM stands for Content Addressable Memory. 2 Operation User supplies an address and RAM returns the word present at that location. User supplies a word and CAM returns the links where word is present. 3 Cost RAM is cheaper than associative memory. CAM is costlier. 4 Application RAM is used to run programs and to store their data during execution. CAM is primary used in database management systems. 5 Suitability RAM is suitable for PRAM (Paraller RAM) algorithm. CAM is suitable for parallel access.
- 156. VIRTUAL MEMORY •In a memory hierarchy system, programs and data are first stored in auxiliary memory. •Portions of a program or data are brought into main memory as they are needed by the CPU. •The term virtual memory refers to something which appears to be present but actually it is not. •The virtual memory is the concept that gives the illusion to the user to use more memory of program than the real memory of computer.
- 157. VIRTUAL MEMORY •Virtual memory is used to give programmers the illusion that they have a very large memory at their disposal, even though the computer actually has a relatively small main memory. •An address used by a programmer will be called a virtual address, and the set of such addresses the address space. •An address in main memory is called a location or physical address. The set of such locations is called the memory space. •Virtual Memory is simulated memory that is written to a file on a hard drive. This file is called page file or swap file.
- 158. VIRTUAL MEMORY •It is used by operating system to simulate physical RAM by using hard disk space. •In windows 1.0, 2.0 version there was no virtual memory. So we were not able to run a number of application due to run out of RAM space. •However from windows 3.0 concept of virtual memory was introduced. •To implement it, a portion of hard drive is reserved by the system. This portion can be either a file or a separate portion.
- 159. VIRTUAL MEMORY •In Windows, it is called pagefile.sys and in Linux, a separate partition is used for virtual memory. •When the system needs more memory it maps some of its memory address out to the hard disk drive. •The extra memory does not actually exist in the RAM, it is the storage space on disk drive. •The more RAM (main memory) your computer has, the faster your program run. •If lack of RAM is slowing our computer, then we can increase virtual memory to compensate.
- 160. VIRTUAL MEMORY •Virtual Address (Logical Address):- Each Address in Virtual Memory is called virtual Address. •Address Space:- Set of all Virtual Address is called virtual address. •Memory Address (Physical Address):- Each Address in main memory is called physical address. •Memory Space:- Set of all Memory Address is called Memory Sapce.
- 161. VIRTUAL MEMORY •Swapping:- Swapping is a mechanism in which a process temporarily moved out from main memory to secondary storage is called swap out and another process moved in from secondary storage to main memory is called swap in. •After sometime first process again brought to main memory. •Address Mapping:- Address mapping specify how to convert virtual address to memory address. •Virtual Memory Implementation :- •1) Paging 2)Segmented Paging
- 162. Address Mapping using PAGING •Page:- Virtual memory is divided into equal size of group. Each group is called page. •Each page consists of number of words called page size. •The term ‘Page Frame’ is sometimes used to denote a block. •The physical memory is broken down into groups of equal size called block.
- 166. Memory Management Unit •A memory management system is a collection of hardware and software procedures for managing the various programs residing in memory. •The memory management software is part of an overall operating system available in many computers. •Here we are concerned with the hardware unit associated with the memory management system.
- 167. Memory Management Unit •The basic components of a memory management unit are: • 1. A facility for dynamic storage relocation that maps logical memory references into physical memory addresses. • 2. A provision for sharing common programs stored in memory by different users. •3. Protection of information against unauthorized access between users and preventing users from changing operating system functions
- 168. Memory Management Unit •It is more convenient to divide programs and data into logical parts called segments. •A segment is a set of logically related instructions or data elements associated with a given name. •Segments may be generated by the programmer or by the operating system. •Examples of segments are a subroutine, an array of data, a table of symbols, or a user's program.
- 169. Segment page mapping •In this the virtual memory is first divided into segments, which are further divided into pages, pages are further divided into words. •Each segment s a group of pages. •Each page is group of words.