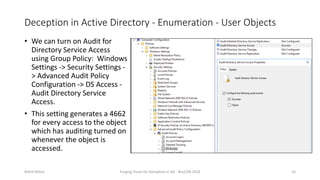
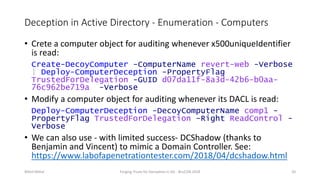
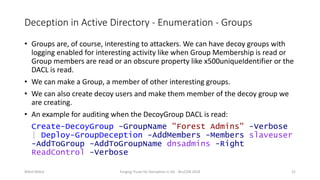
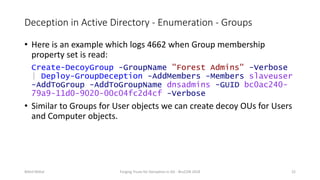
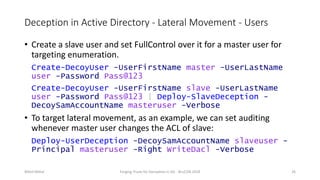
Nikhil Mittal discusses techniques for deploying deception in Active Directory to detect adversaries. This includes creating decoy user, computer and group objects with interesting attributes and enabling detailed auditing. When adversaries interact with or enumerate these decoy objects, alerts will be generated. The presentation also covers automating this process using a PowerShell module. Deception can target both the enumeration and lateral movement phases of an attack.