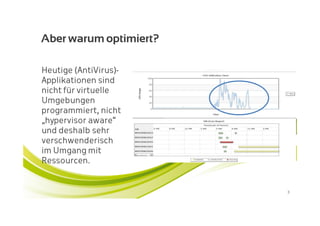
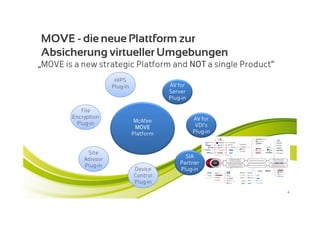
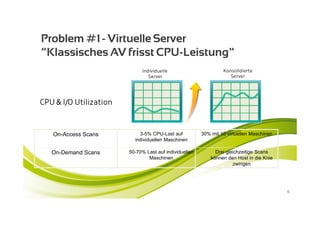
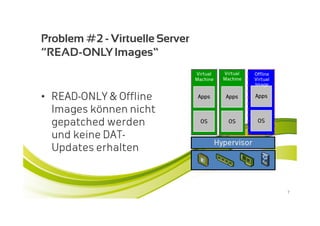
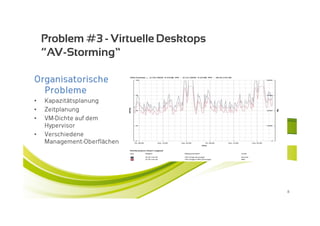
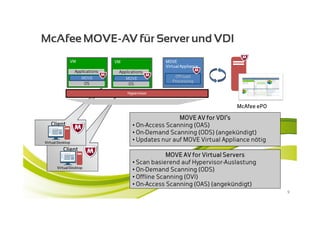
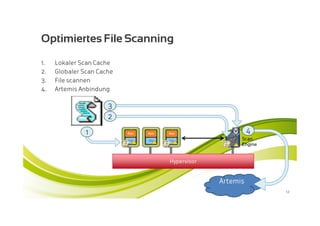
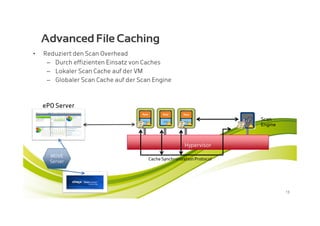
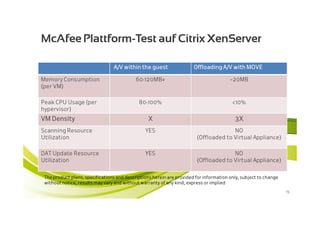
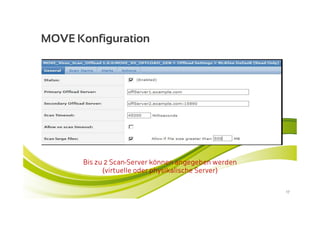
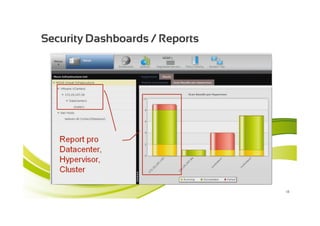
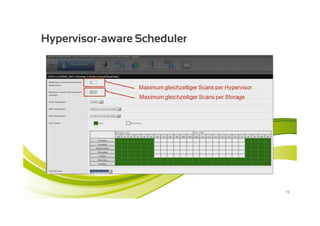
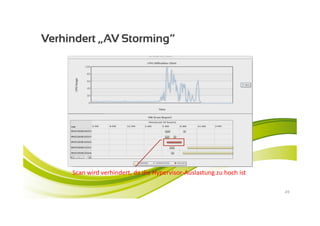
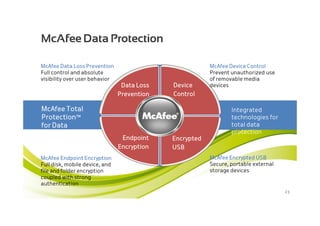
McAfee MOVE provides a new strategic platform for securing virtual environments, addressing inefficiencies of traditional antivirus applications that aren't optimized for virtualization. It enables effective security management, reduces resource consumption, and enhances performance during high VM densities. McAfee Endpoint Encryption further protects corporate data on mobile devices through full disk and file encryption, providing robust safeguards against data loss and theft.