Using the grades mechanism to differentiate the users in VANET
- 1. Using the Grades Mechanism to Differentiate the Users in Vehicular Ad hoc Network (VANET) Dr I.A.Sumra
- 2. End user is the key module of a future vehicular network and safety and non safety applications mostly focuses on the user’s safety and comfortable during the journey. Security of these applications are very significant and these life saving messages cannot be altered by any attacker. In this slide, the role of the end user in a vehicular network will be discussed in detail and three levels of trust grades for users will be proposed. It is necessary for secure vehicular communication that the user’s role in the network should be in a positive direction, and other users should take more benefits from this new future technology. 2
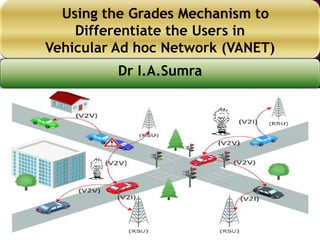
- 3. Vehicular ad-hoc network is a special kind of network in which nodes (Vehicles) can communicate with each other on the road and with its Infrastructure. 3
- 4. Safety Applications Non Safety Applications Work in Progress Plz! use Alt. route Work Zone Warning:!!! Work Zone Warning:!!! Shopping MALL Parking Slot Available!!! RSU Parking Slot Available!!! 4
- 5. Role of end user is most important in VANET and objective of VANET applications to serve the users and reduces the death rate due to road accident. Car manufacturers provide smart vehicles while government agencies provide the basic infrastructure needed to implement applications and serve the users. VANET applications and smart vehicles are major modules and users directly communicate with them and send and receive safety and non safety messages. 5
- 6. 6
- 7. User is the main entity in vehicular work and objective of this new technology is to serve users and safe their lives from road accidents. Safety and non safety VANET applications meet the all users requirement during their journey like send or receive safety message to other vehicles and use the entertainment services. 7
- 8. 8
- 10. Users are important entities in a network and the purpose of VANET applications to serve the end user and provide safety on the highway. Applications serve the end users when these applications are secured and user should be trusted, otherwise these applications create more problems for users of the network. Good or bad user always remains part of the network and it is difficult to predict his/her behavior on the road due to the dynamic topology of the network. Therefore, trust grades for vehicular users have been proposed and objective of these grades to differentiate between good users and malicious users in a network. The Figure.3 shows the Trust grades for End Users. 10
- 11. 11
- 12. Zero Trusted User (ZTU) (Attackers) – Trust Grade (0) Zero Trusted Users (ZTUs) are those users that do not possess the trusted credentials and could potentially be the kind of attackers who create problems for legitimate users by launching some type of attack. In the vehicular network, their role is more prominent because they can potentially change the life critical information on the road. All types of attackers which we have discussed in related work is also considered in zero trusted users. 12
- 13. Zero Trusted Users (ZTUs)- [Trust Grade-0] 13
- 14. These people are not attackers, but their behavior indirectly effects the main functionality of network. These are the factors that change the behavior of the users and assign weak trusted users. The Figure 6 describes weak users’ type and we have assigned the one grade to these types of users. Weak Trusted User (WTU) – [Trust Grade-1] 14
- 15. Strong Trusted Users (STUs) are those people who perform their tasks properly and achieve the security requirements in the network. Security requirements are important factor for all components of vehicular network, so every module should be secured and work properly to serve the users. Applications and other modules should be fulfilling the maximum levels of security requirements. Strong Trusted User (STU) – [Trust Grade-2] 15
- 16. End users require more safety on the road in future vehicular networks and this could be possible by the successful implementing of VANET in real environment with its potential applications. Vehicular applications must be secured; if non-trusted users (attackers) change the content of safety applications then other users are directly effected. Attackers change their attacking behavior and they launch different attacks at different times. The proposed trust grades of attackers are expected to be helpful to identify and understand the behavior of different types of users. The Implementation of this future human life saving network could be easy if users play their positive roles and make secure communications. 16
- 17. This is journal research paper and please download complete research paper from research gate. 17
- 18. 18
