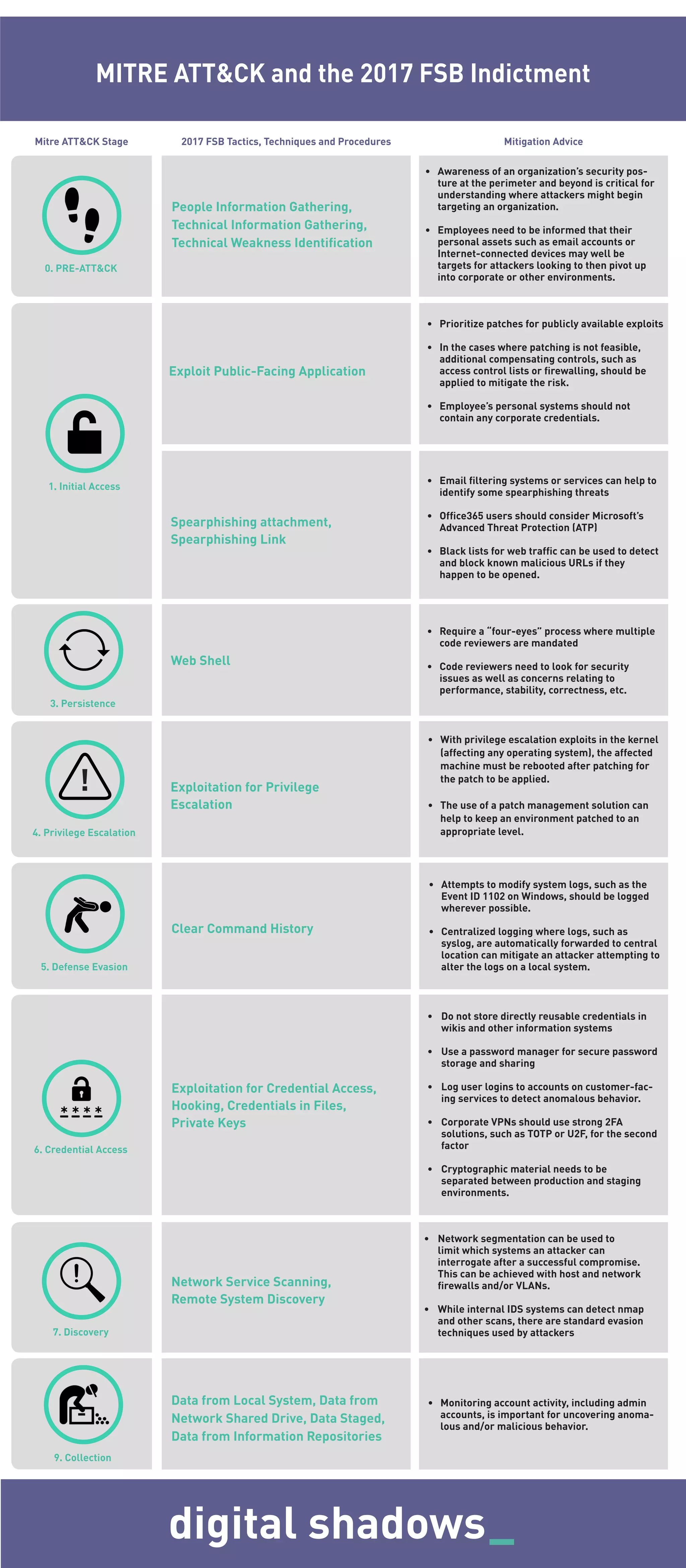
The document highlights critical security measures for organizations against potential attacker tactics, including awareness of personal asset vulnerabilities, prioritization of patching, and implementing compensating controls. It emphasizes the importance of secure coding practices, user login logging, and robust credential management while recommending network segmentation and centralized logging for effective threat detection. Additional recommendations include employing email filtering, utilizing advanced threat protection for services like Office365, and ensuring proper logging of any modifications to system logs.