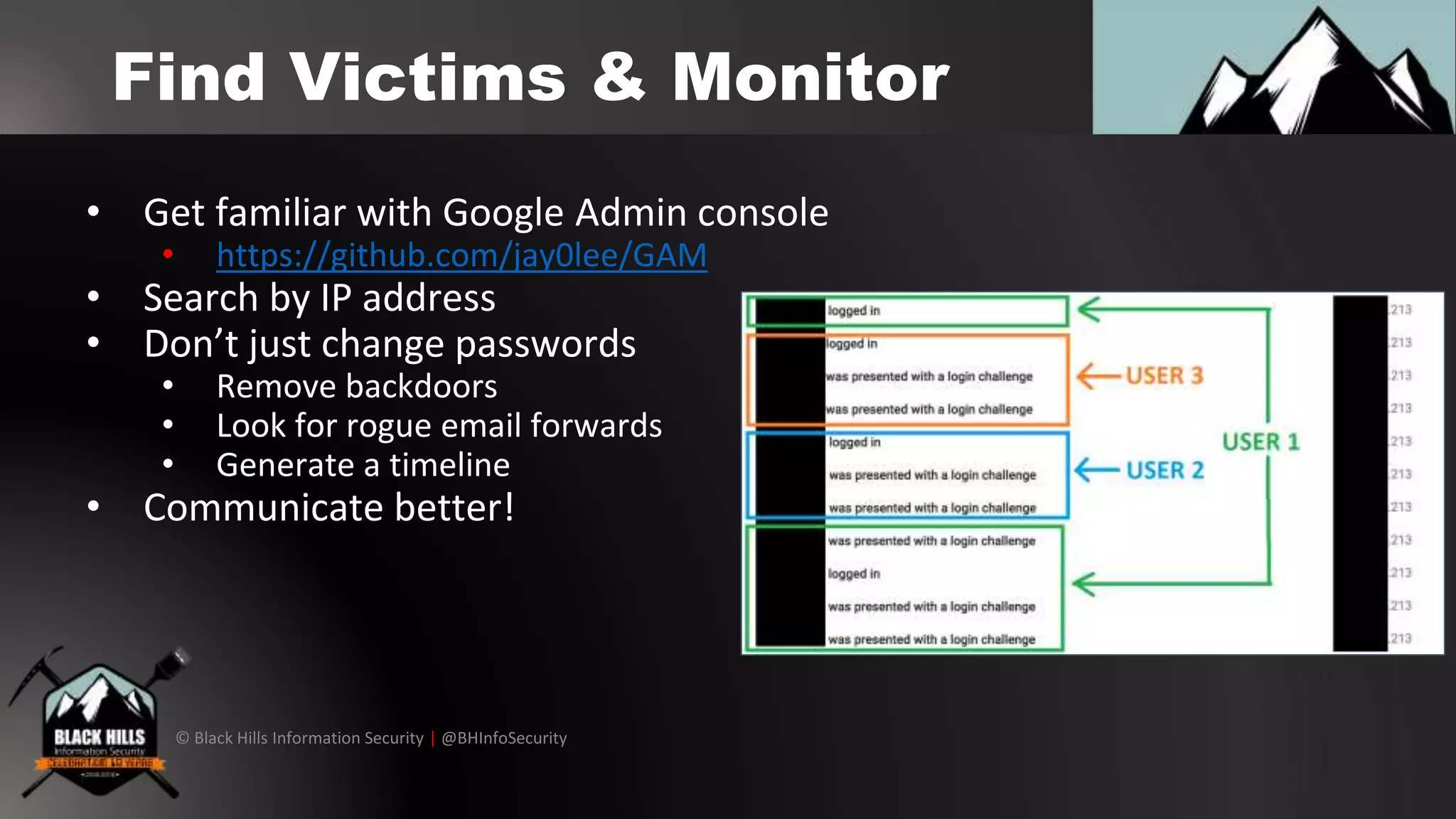
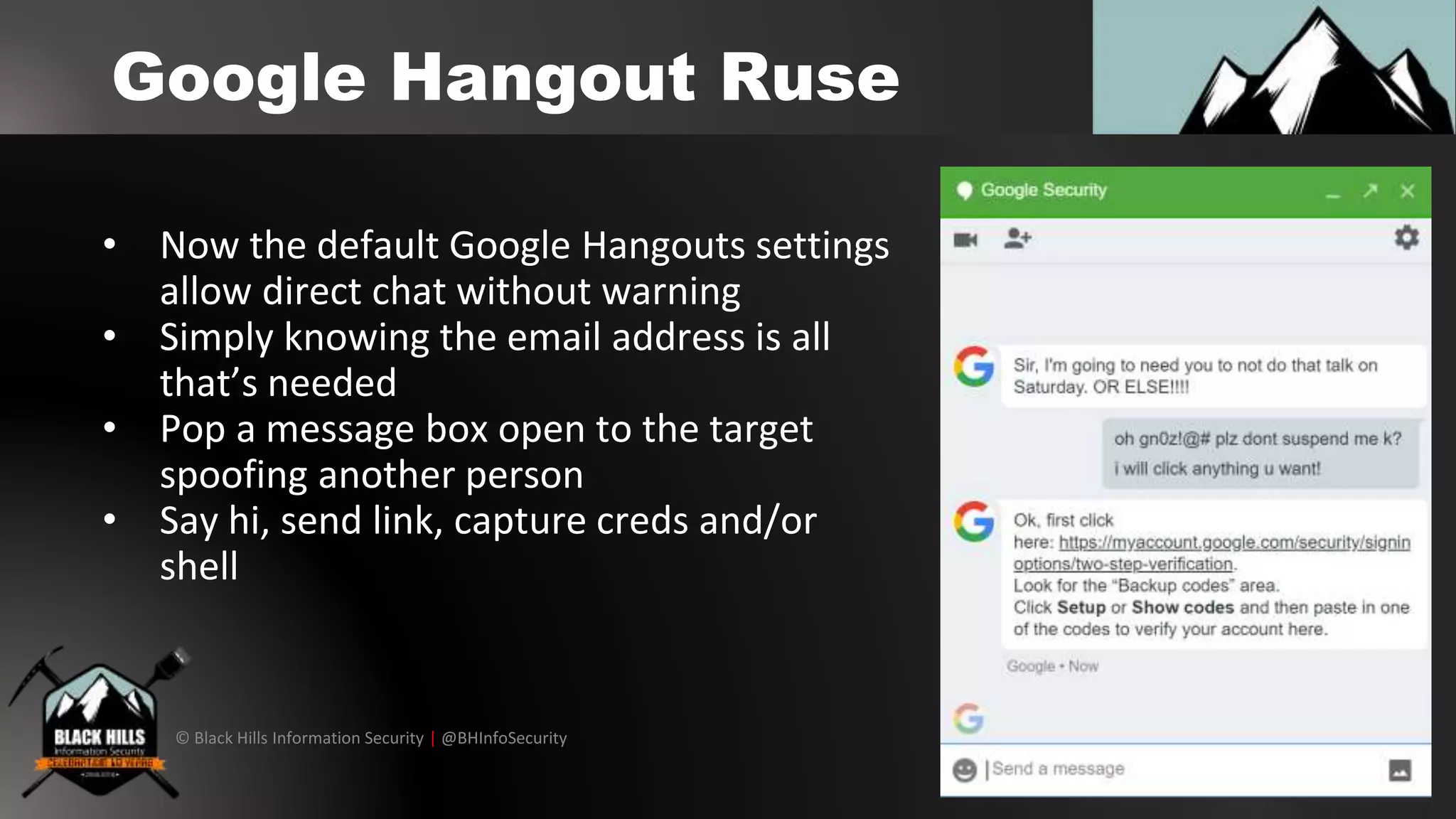
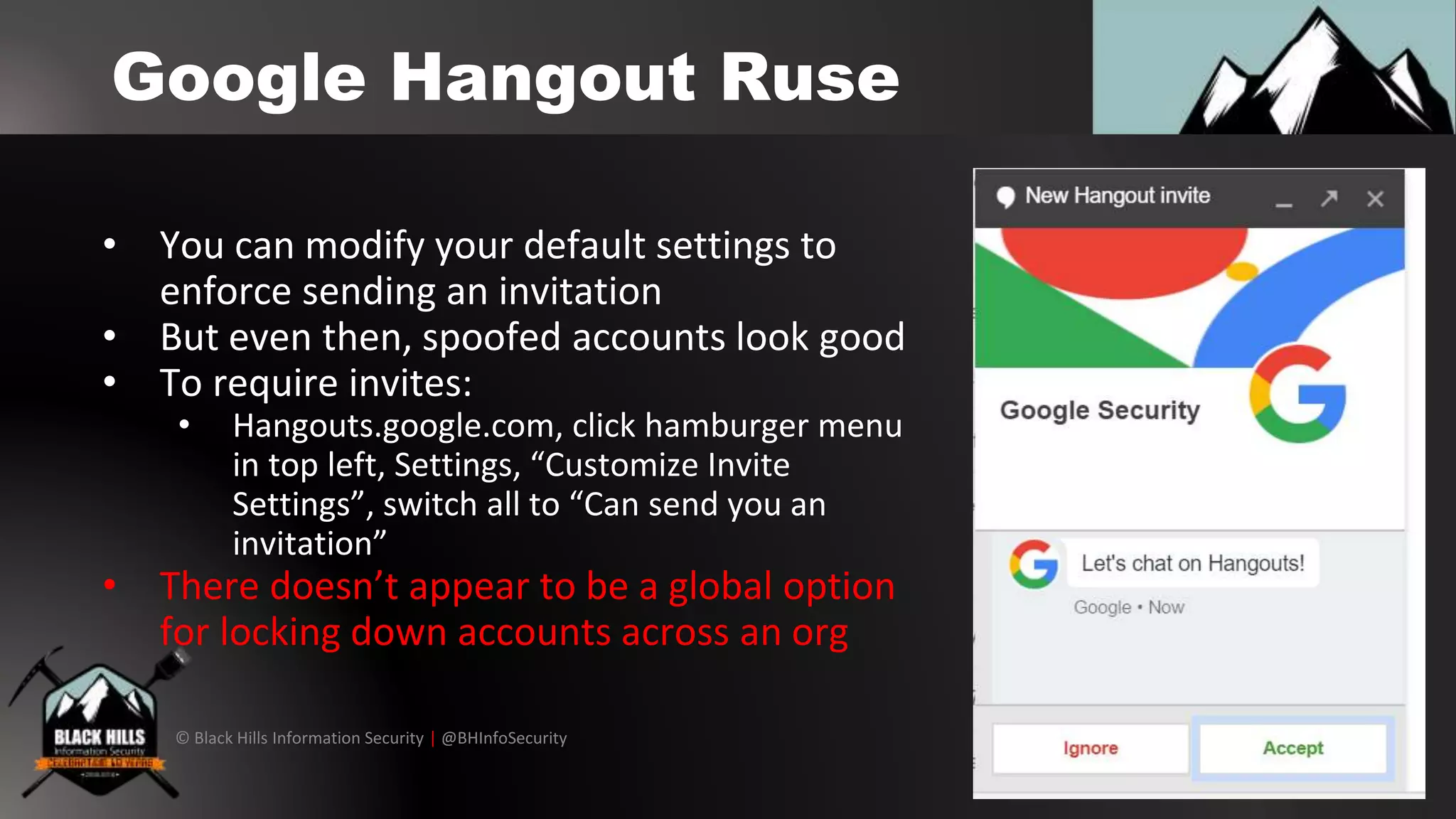
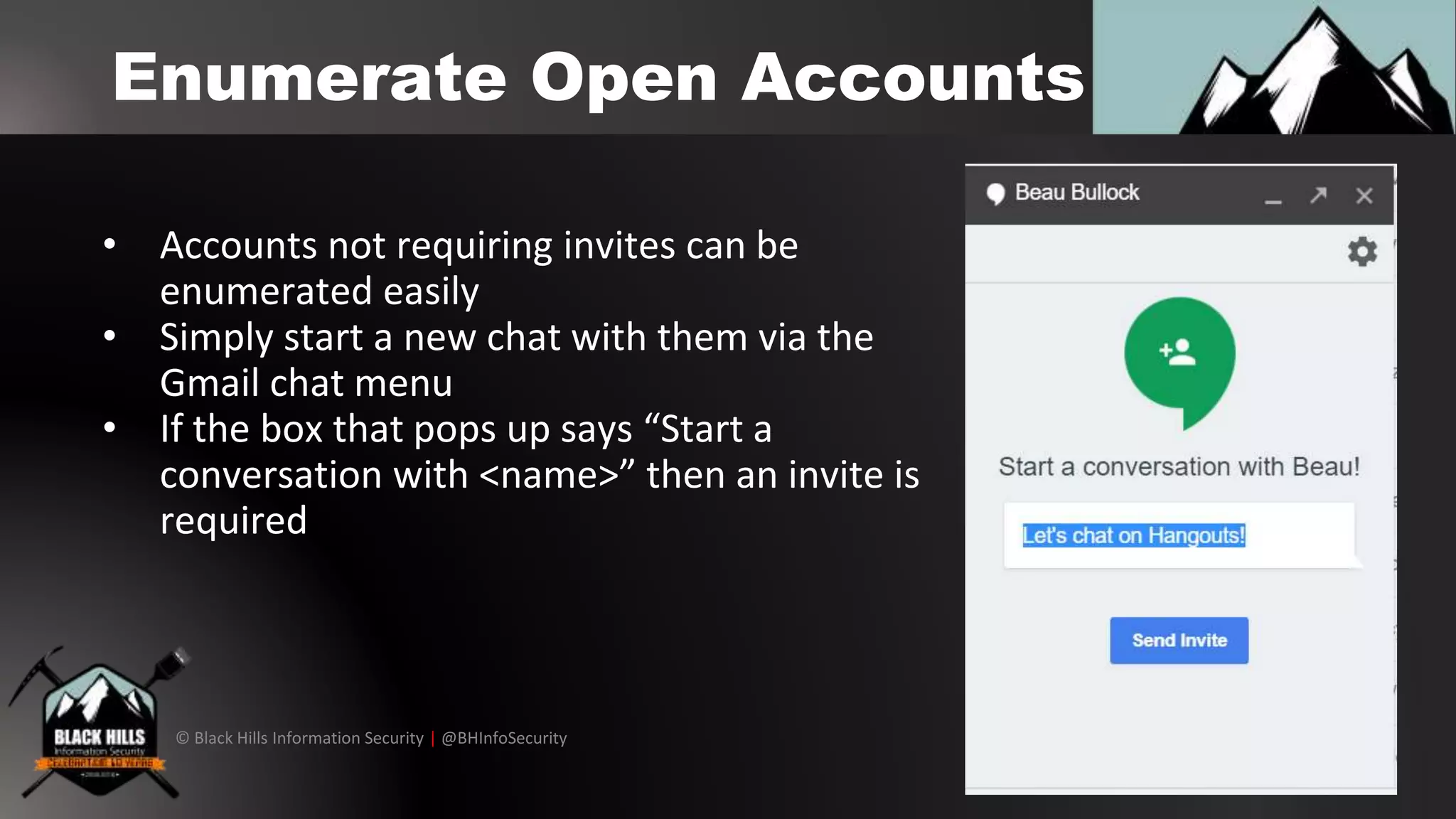
The document outlines techniques for conducting red team exercises against G Suite, focusing on areas such as operational security, perimeter cracking, social engineering, and internal security measures. It presents various attack methods like phishing via Google Docs, Google Hangouts, and calendar event injections, along with guidance on ensuring persistence within compromised accounts. The importance of user awareness, security audits, and proper incident response procedures are emphasized for defending against such attacks.














![© Black Hills Information Security | @BHInfoSecurity
Target Company Directory
• Create contacts group from directory
• Export all the contacts
• Tailor your target list..
• More technical, more access!
• Create a LinkedIn doppelganger
• Side note.. file transfers
don’t have [EXTERNAL] tags like email](https://image.slidesharecdn.com/okgooglehowdoiredteamgsuite-180408021633/75/OK-Google-How-Do-I-Red-Team-GSuite-41-2048.jpg)